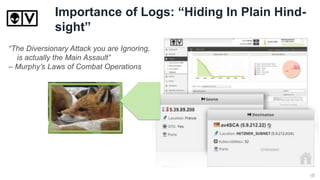
The document serves as a guide for organizations preparing for a security breach, emphasizing the inevitability of such incidents and the importance of readiness. Key recommendations include implementing monitoring technologies, fostering collaboration across departments, and maintaining effective communication channels. Ultimately, it stresses the significance of process and practice in managing a breach efficiently.