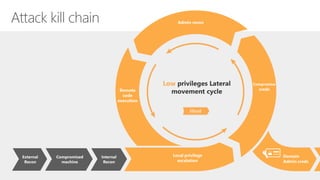
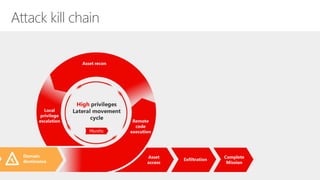
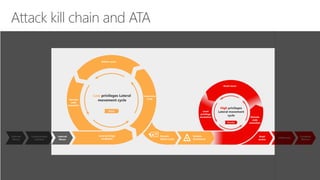
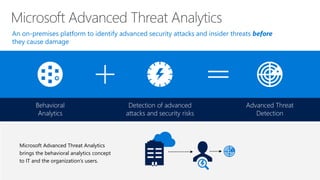
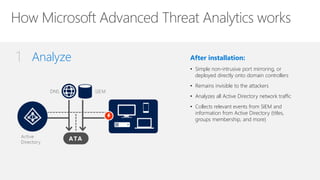
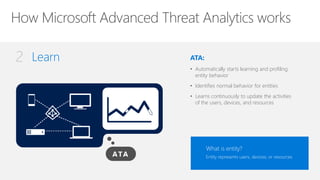
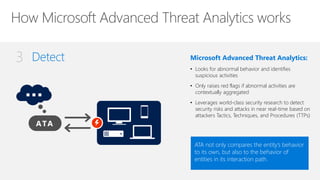
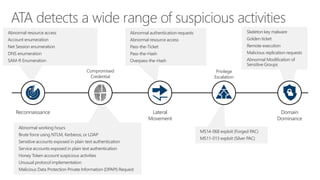
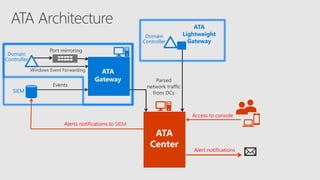
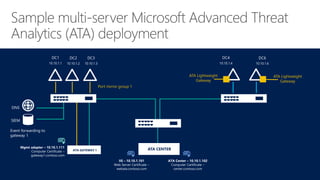
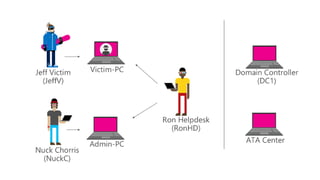
Microsoft Advanced Threat Analytics (ATA) is a behavioral analytics platform that detects advanced security threats and insider threats in enterprise networks. It analyzes Active Directory network traffic and events using machine learning to establish normal user behavior and detect anomalies. When installed, ATA automatically starts learning and profiling entities. It identifies normal behavior and looks for abnormal activities that could indicate security risks or attacks based on tactics used by attackers. Any suspicious activities are presented on a timeline with details on who was involved, what happened, when, and how to investigate and respond. ATA helps enterprises detect threats that evade other security tools and prioritize responses.