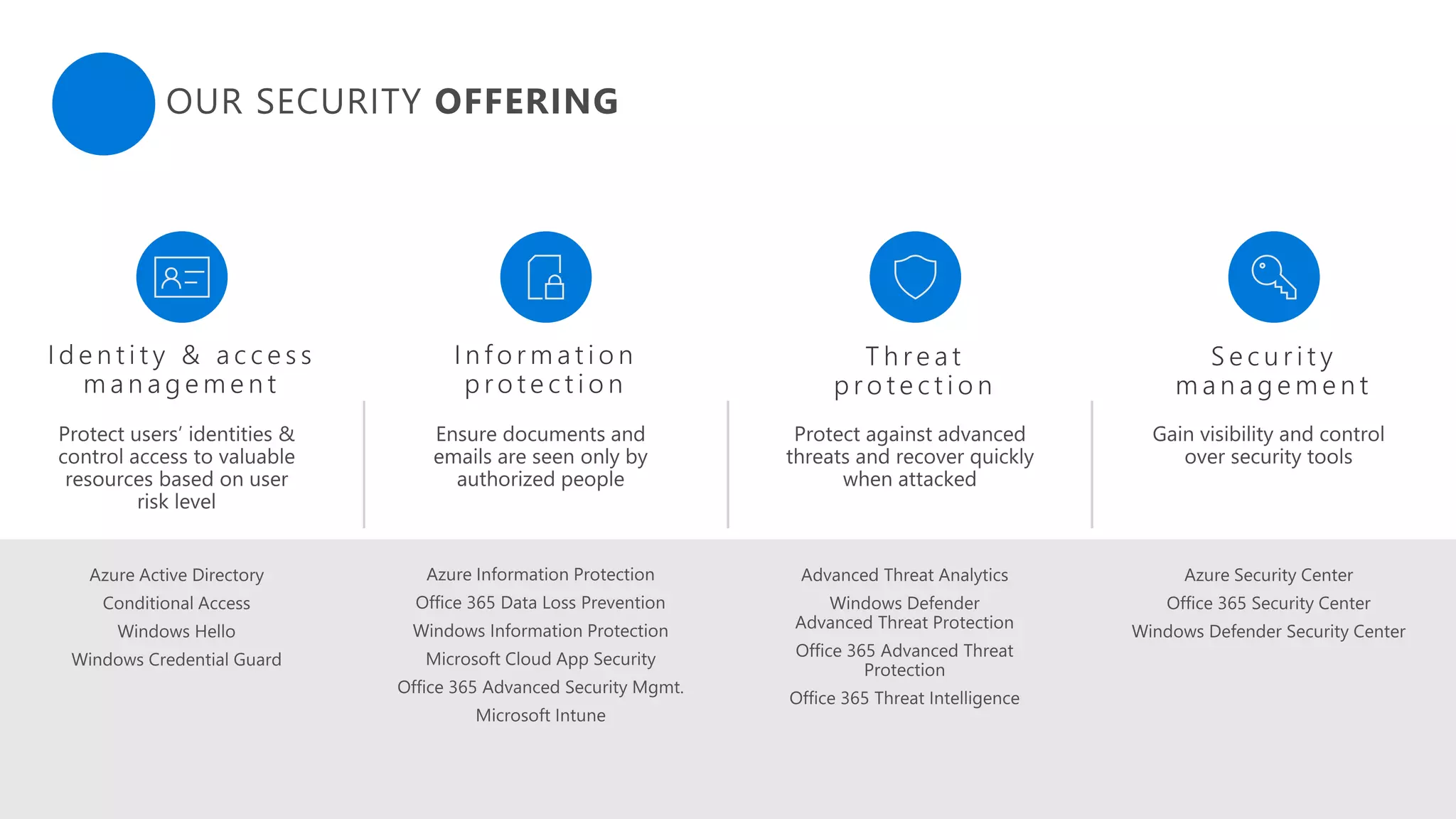
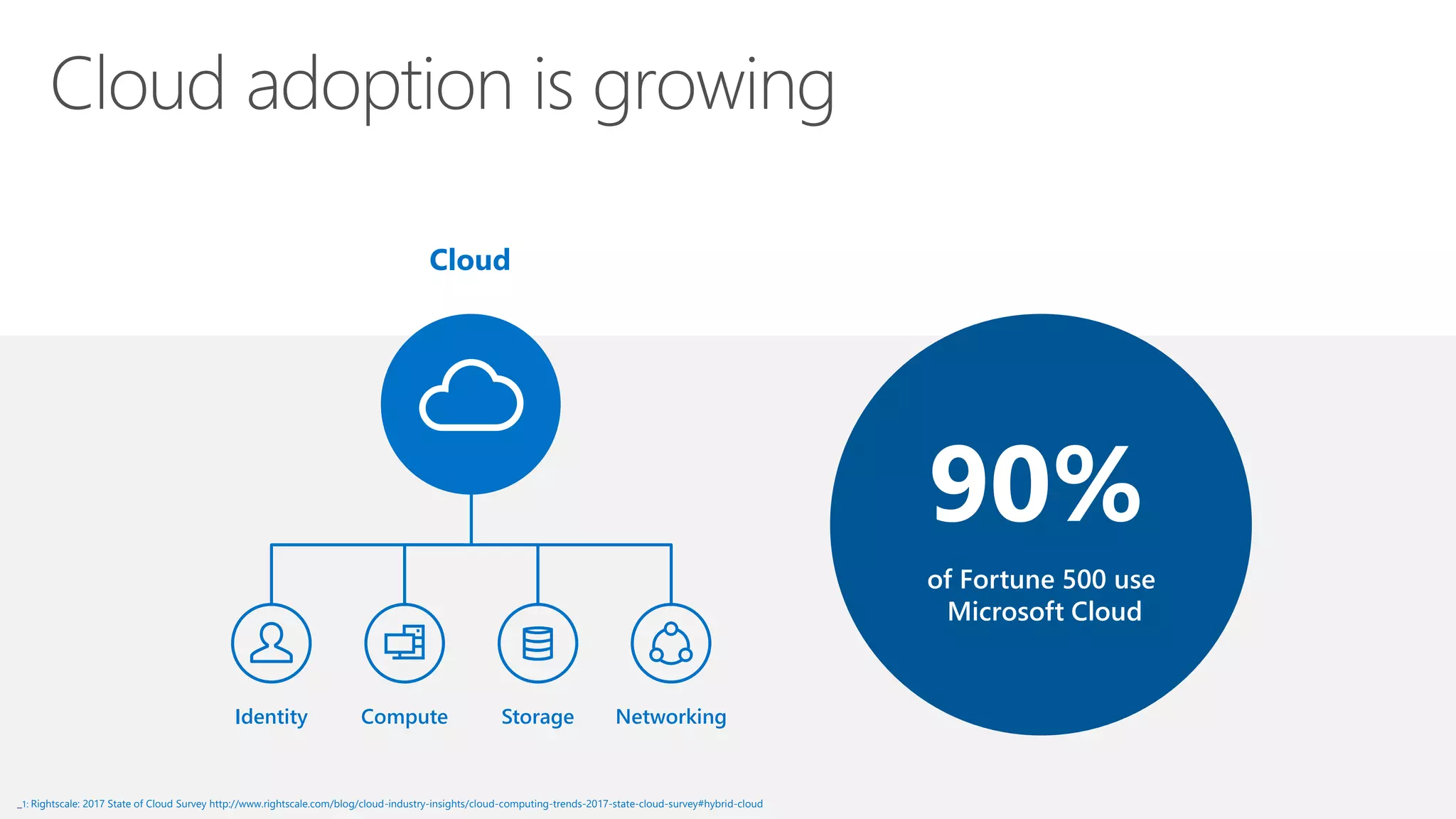
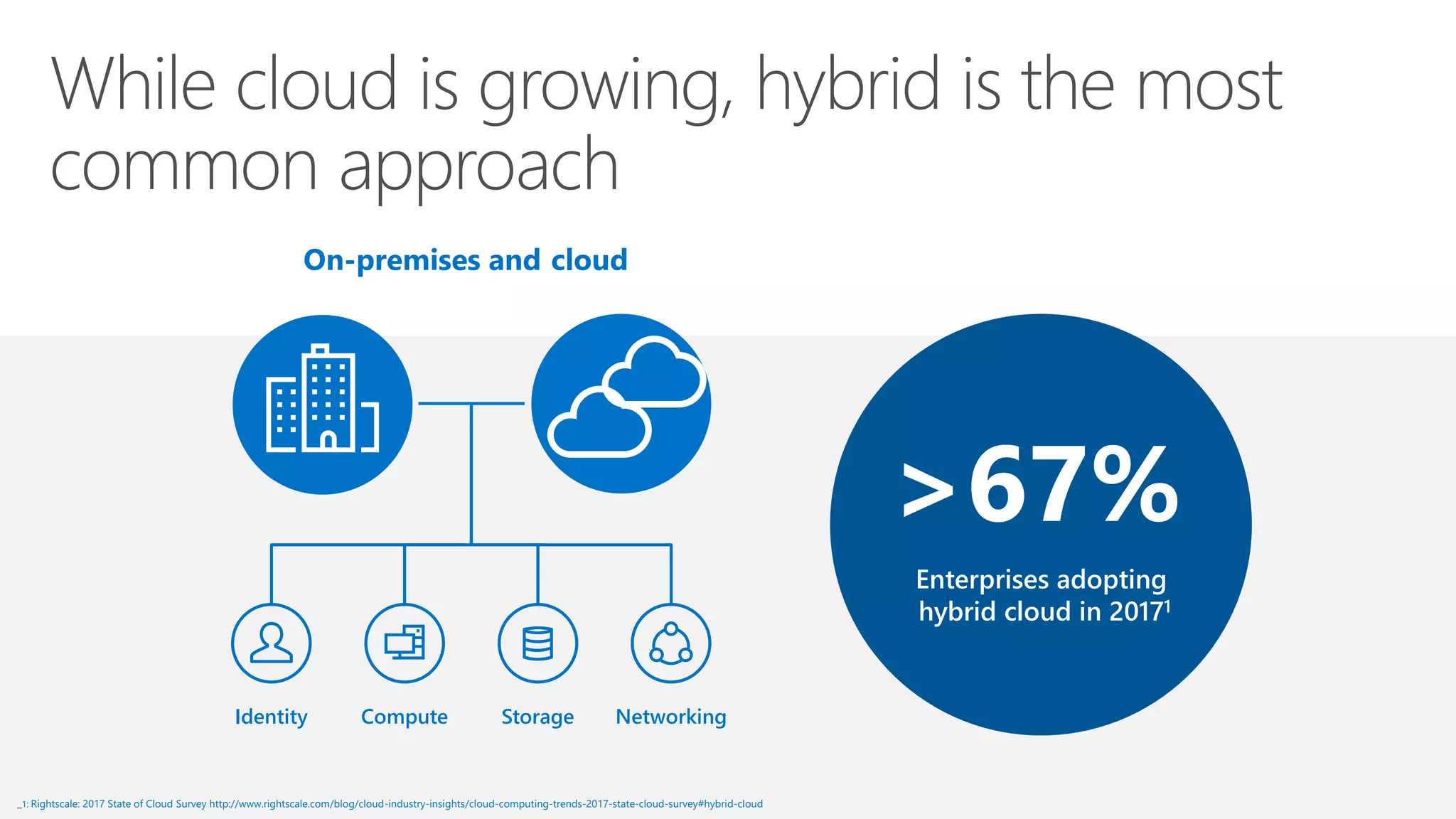
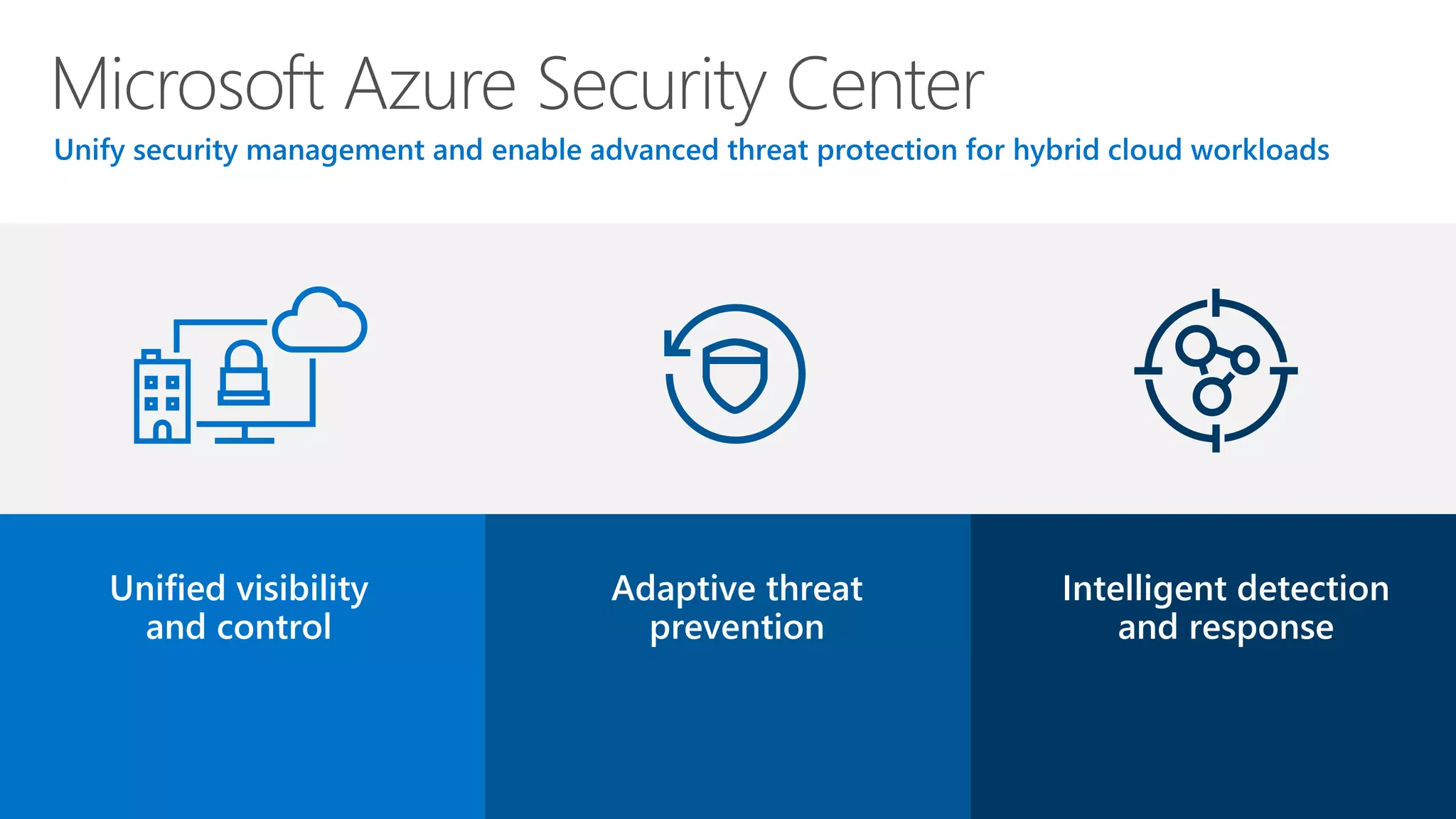
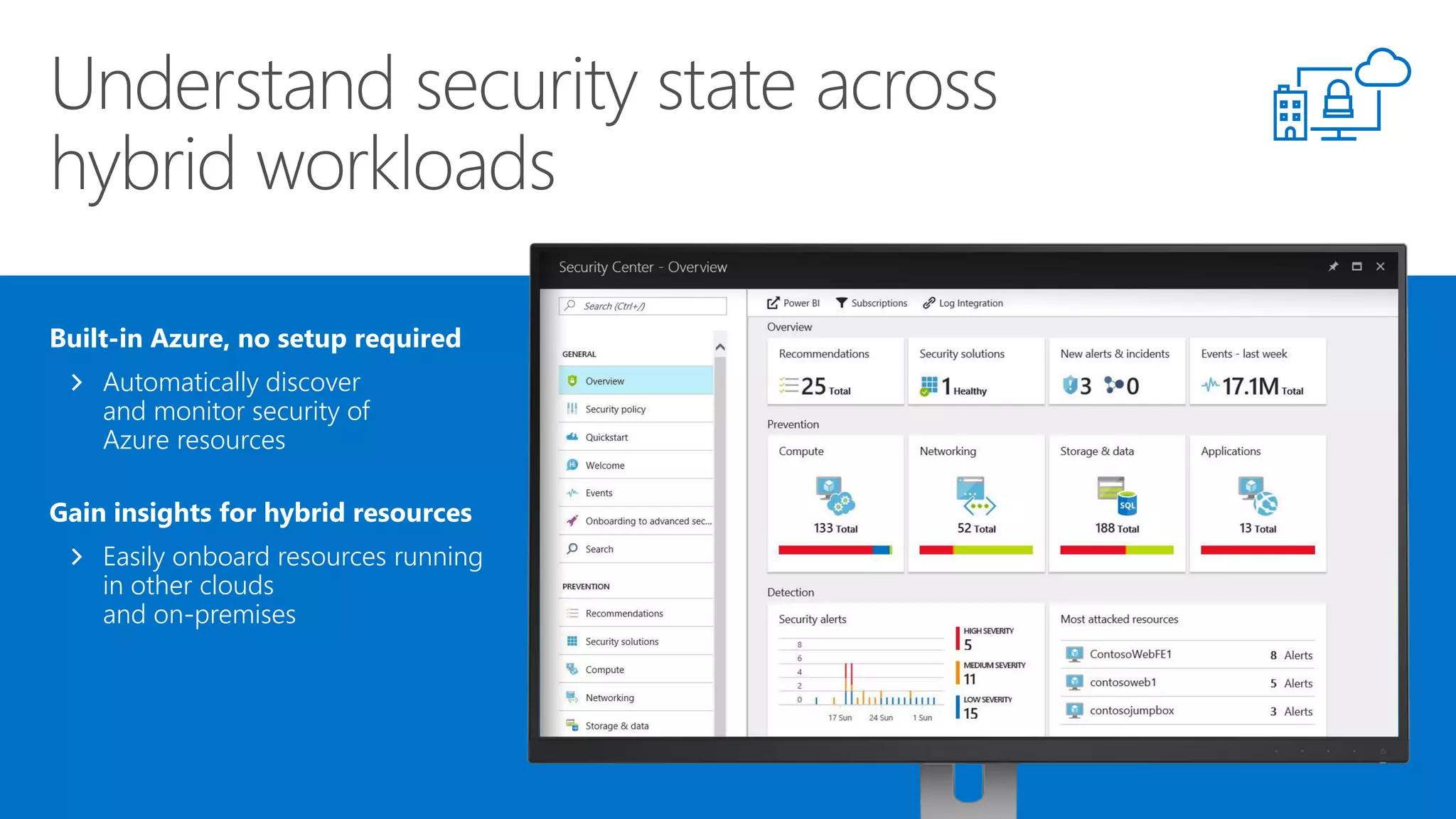
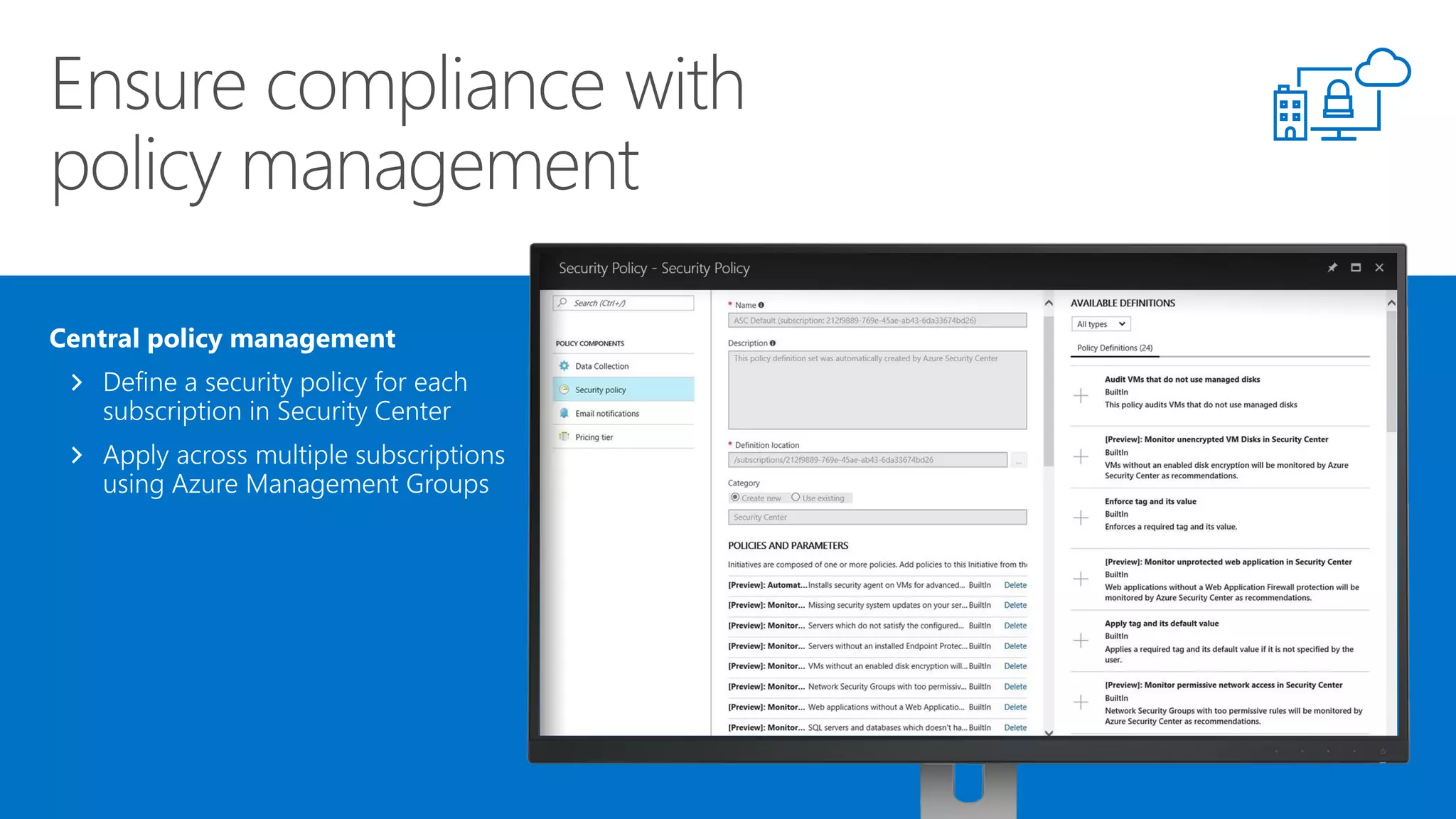
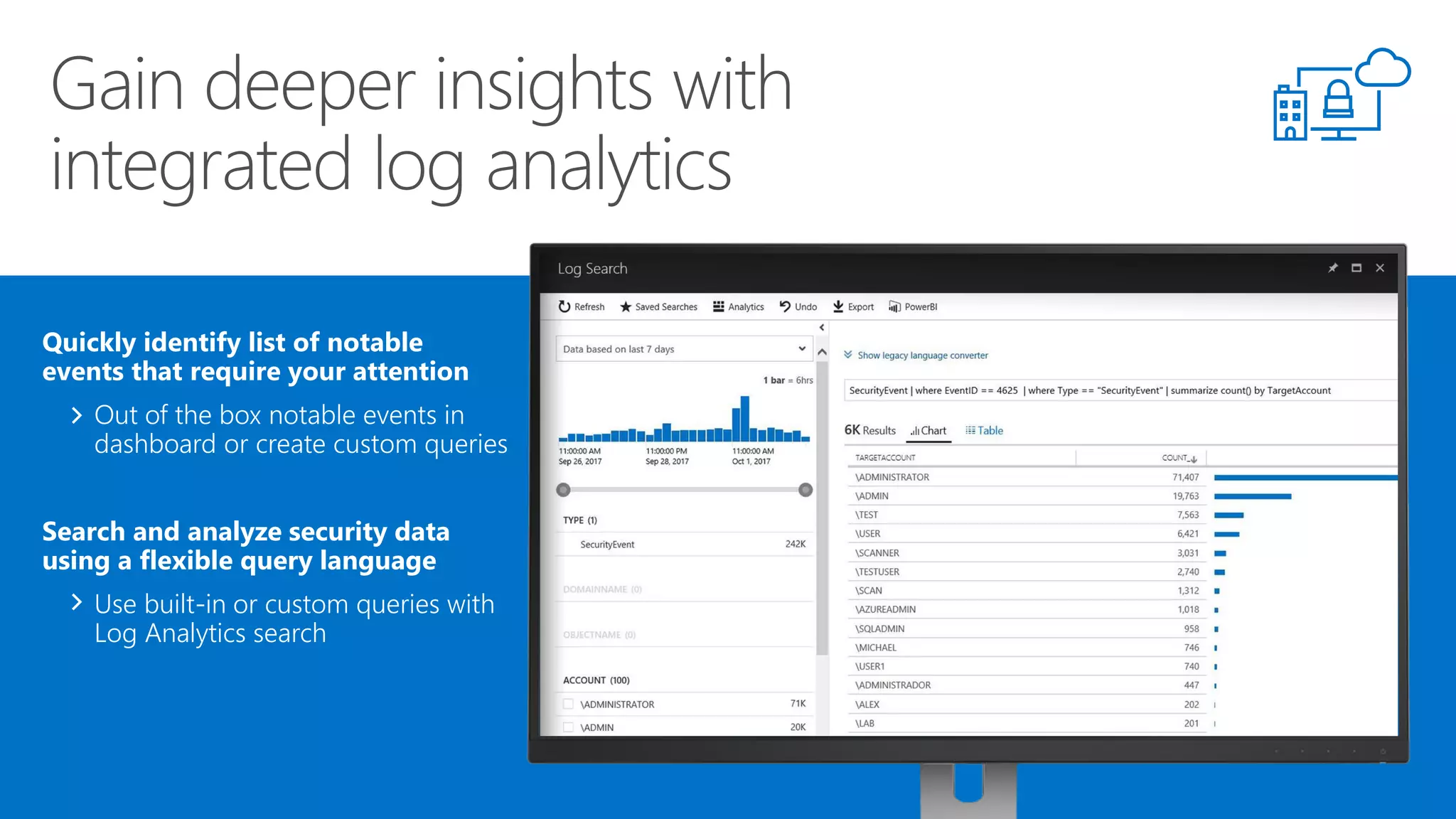
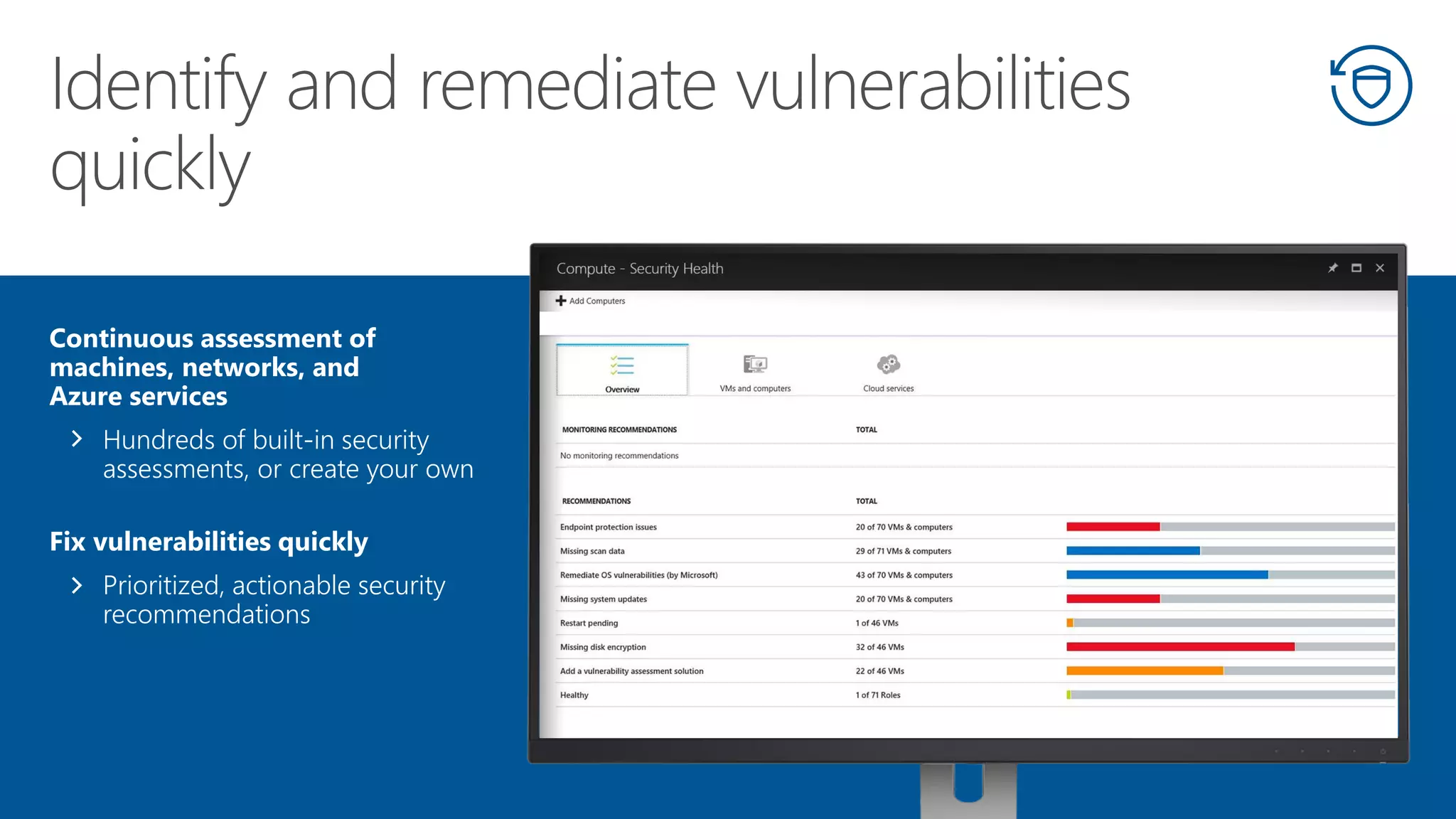
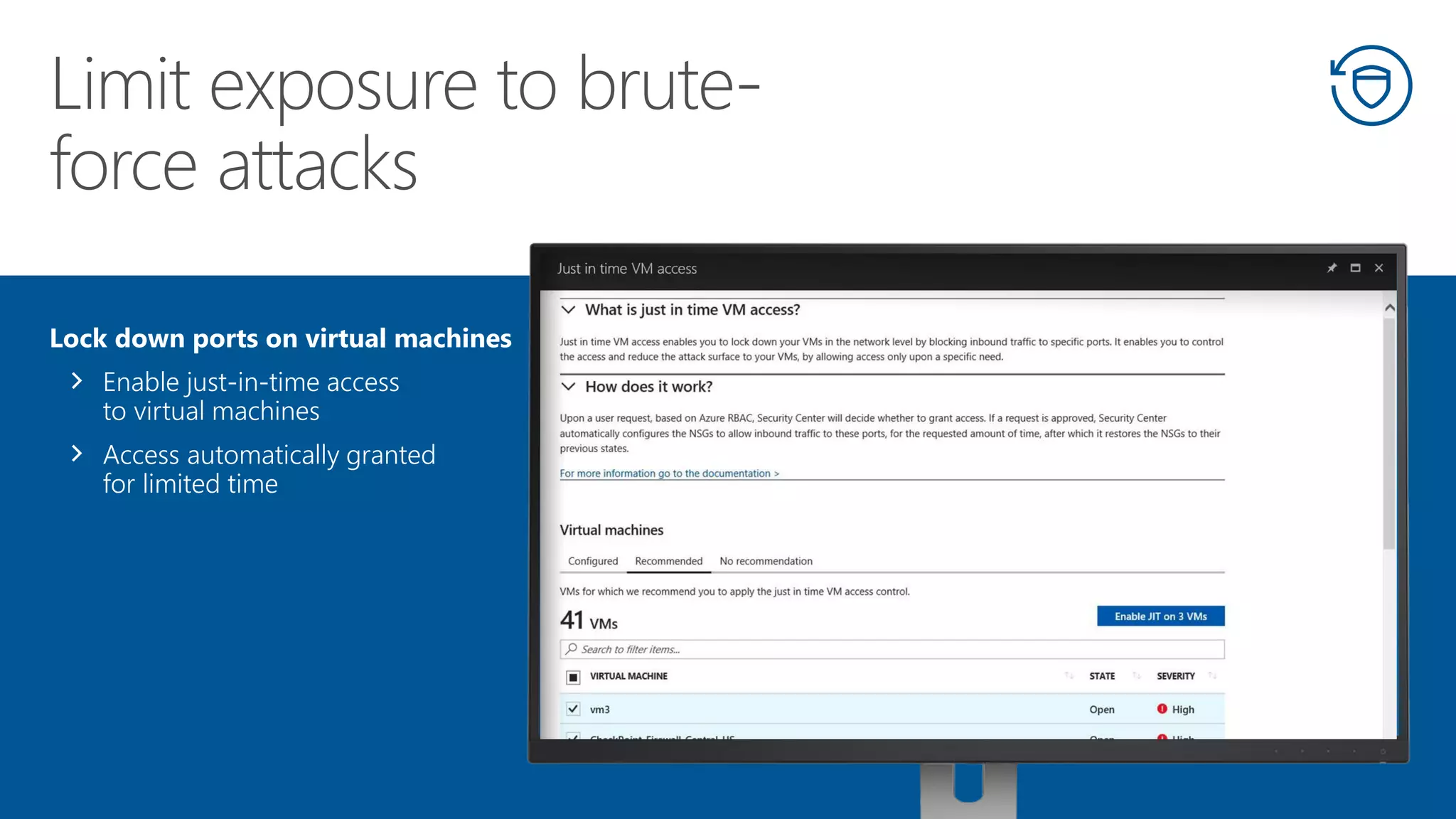
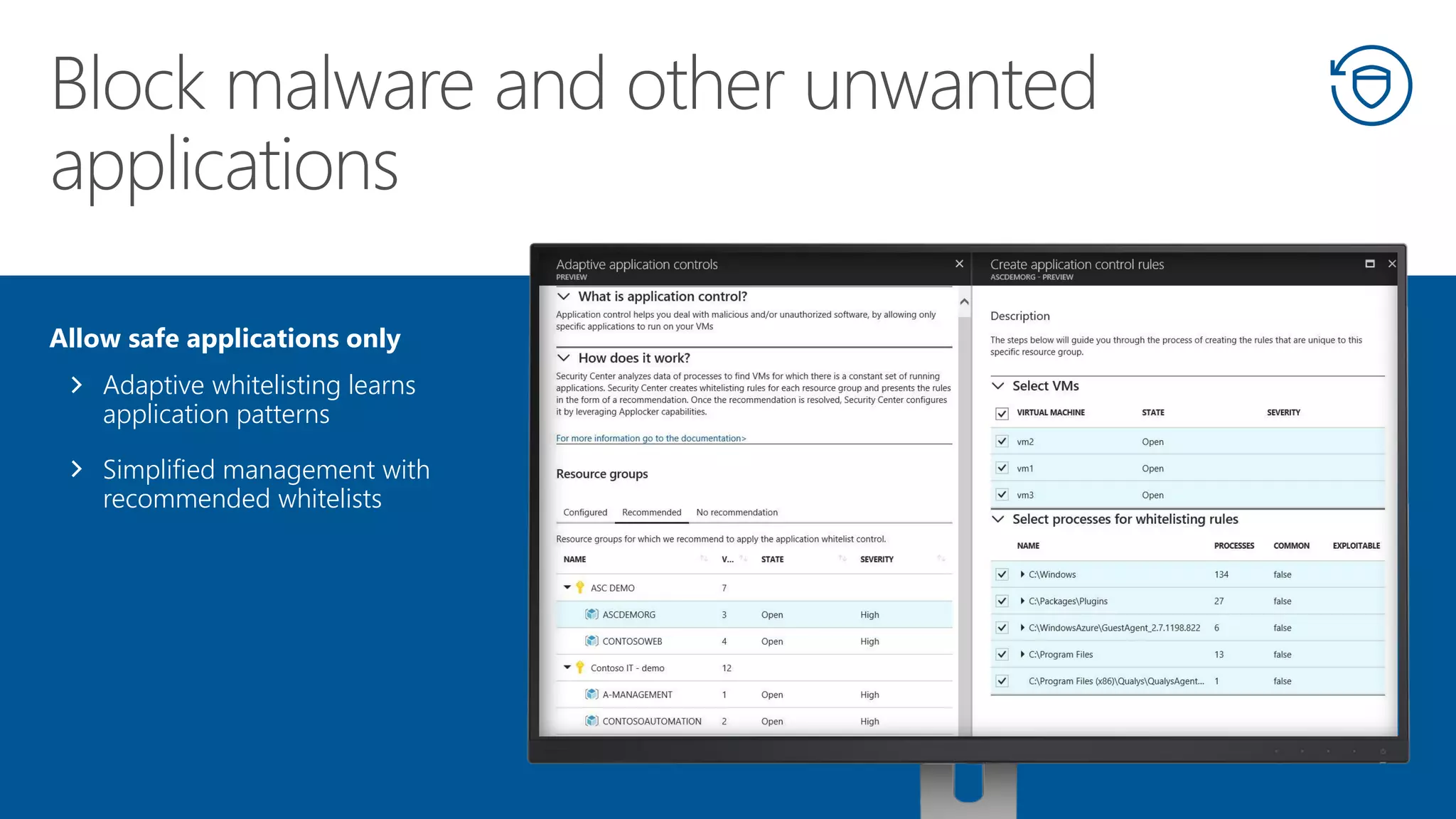
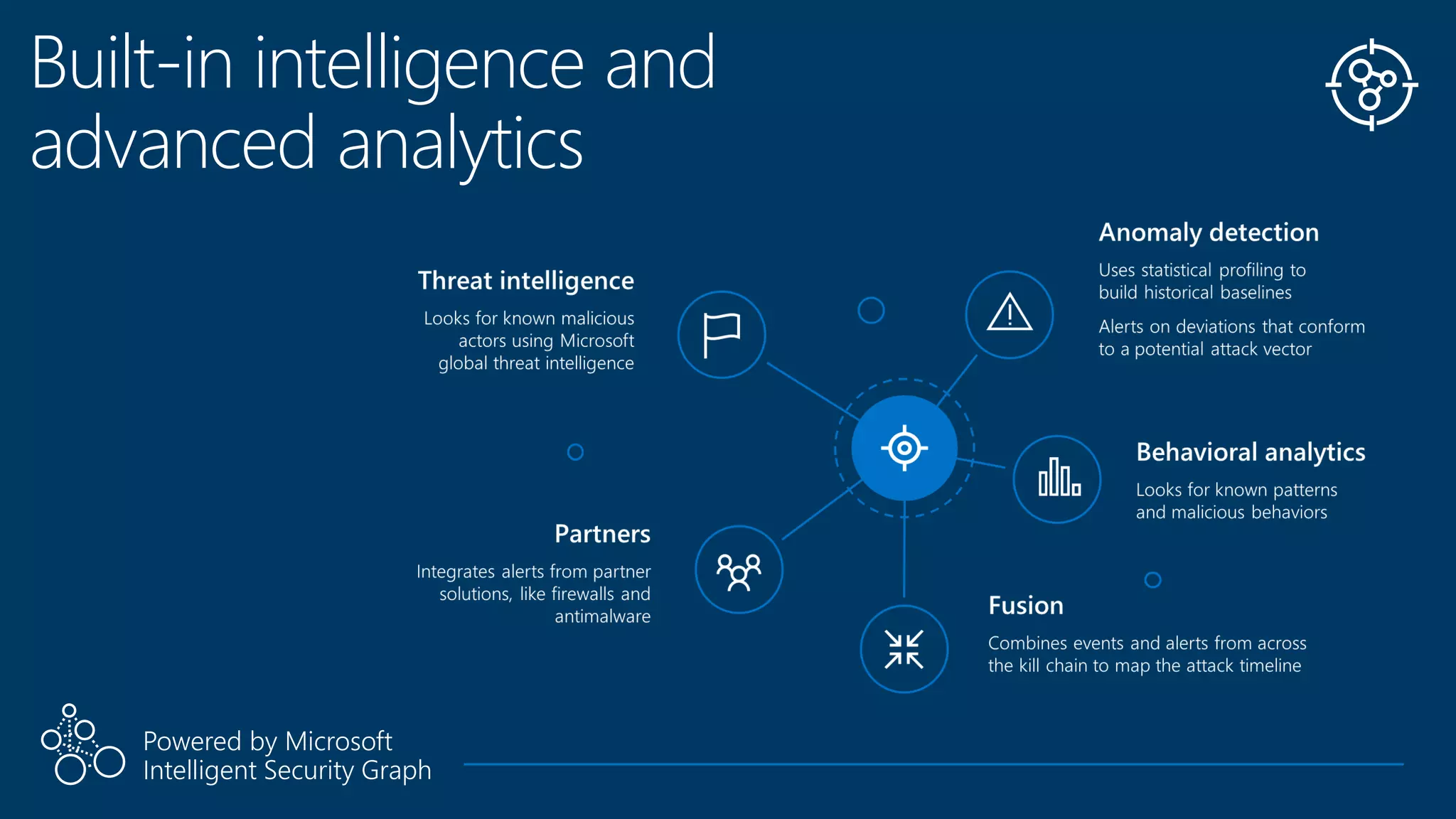
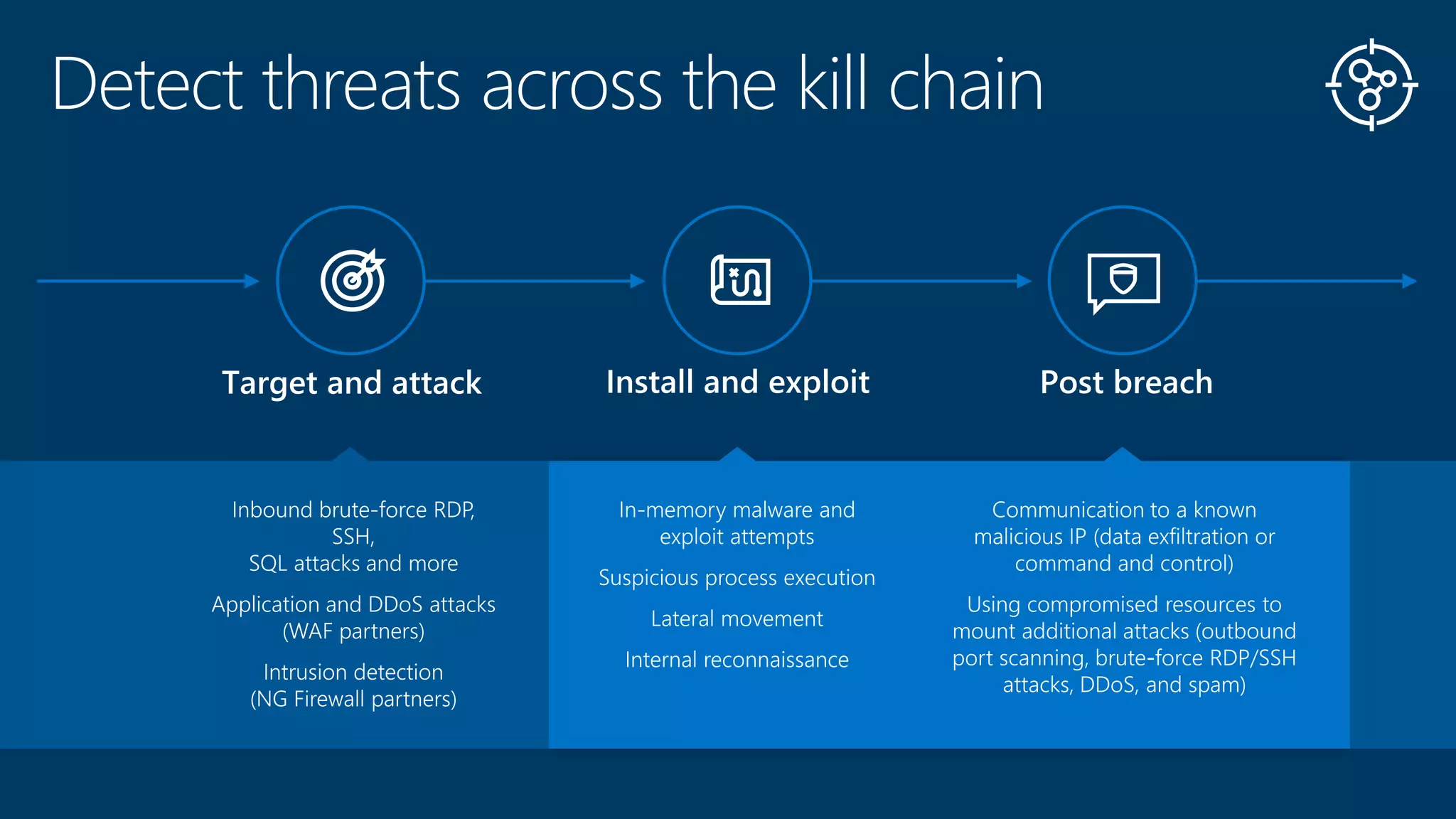
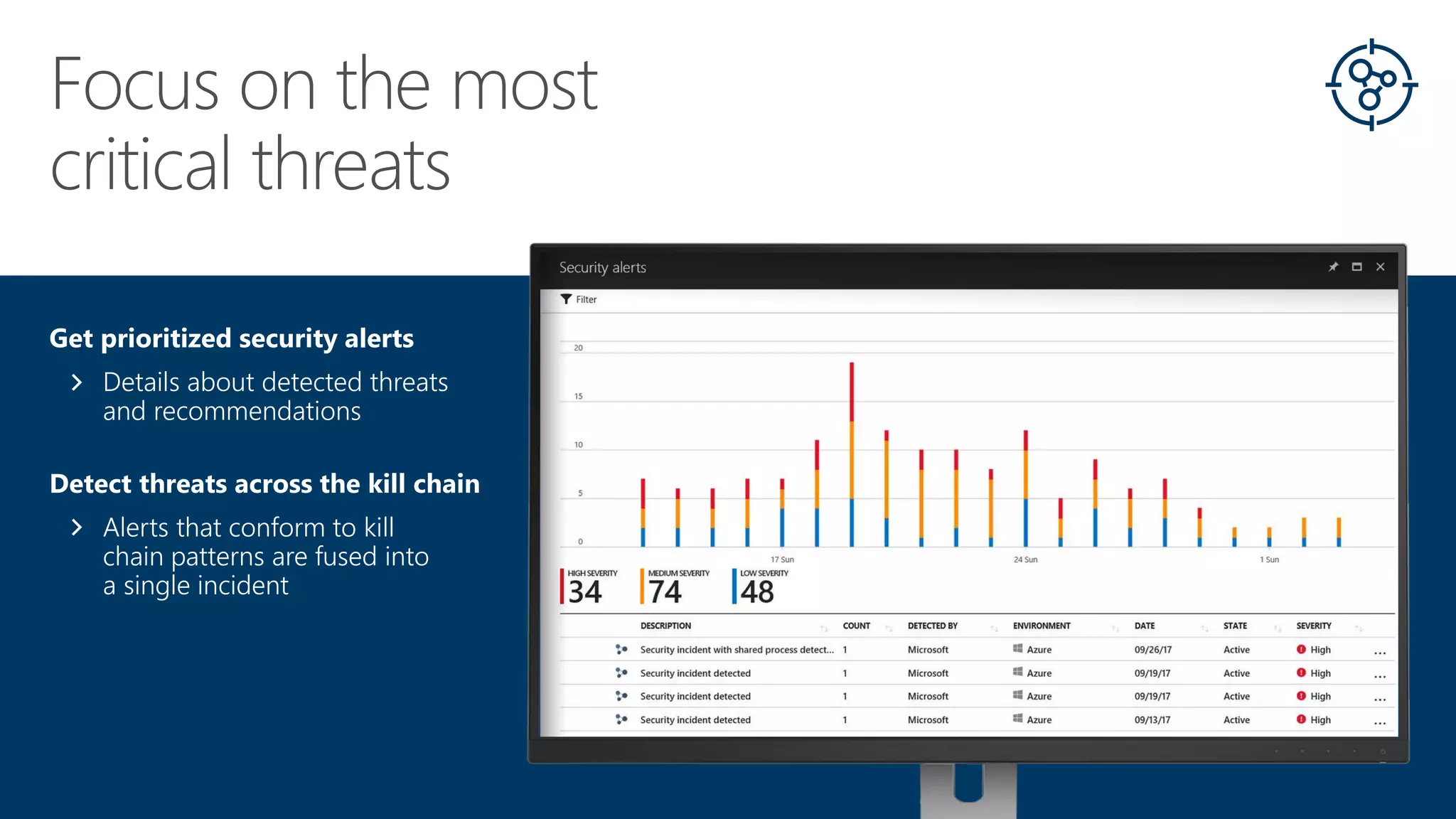
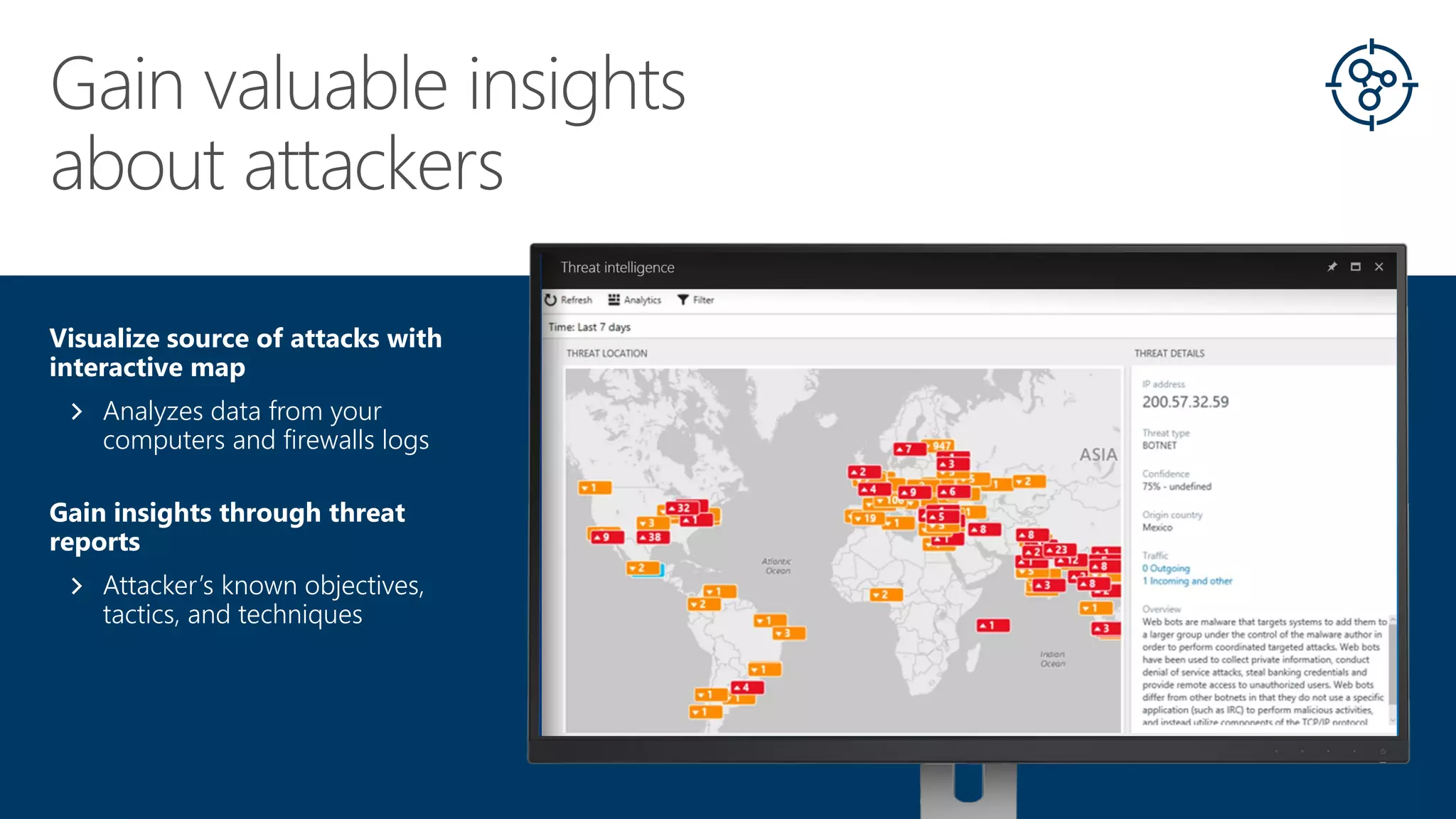
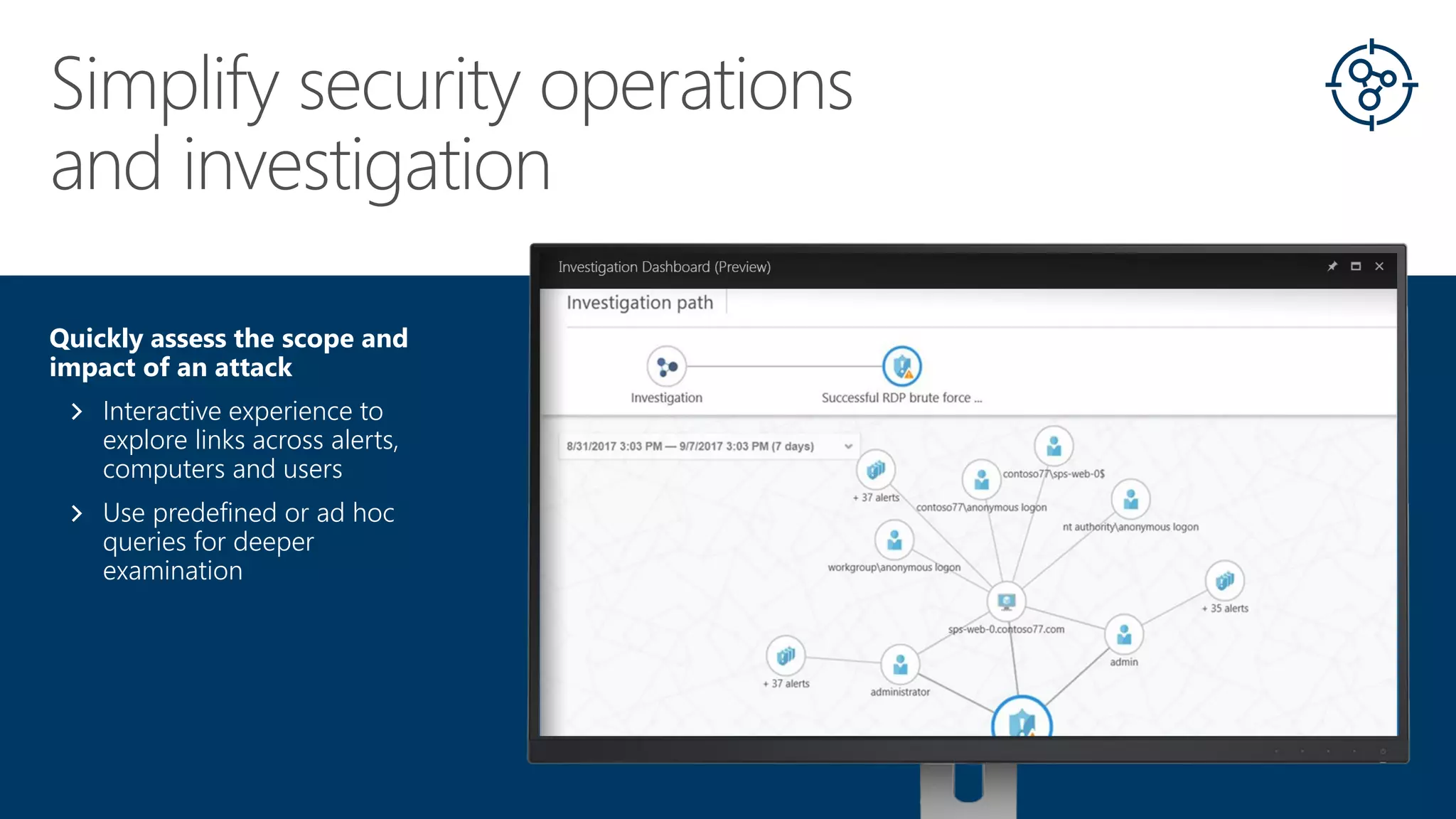
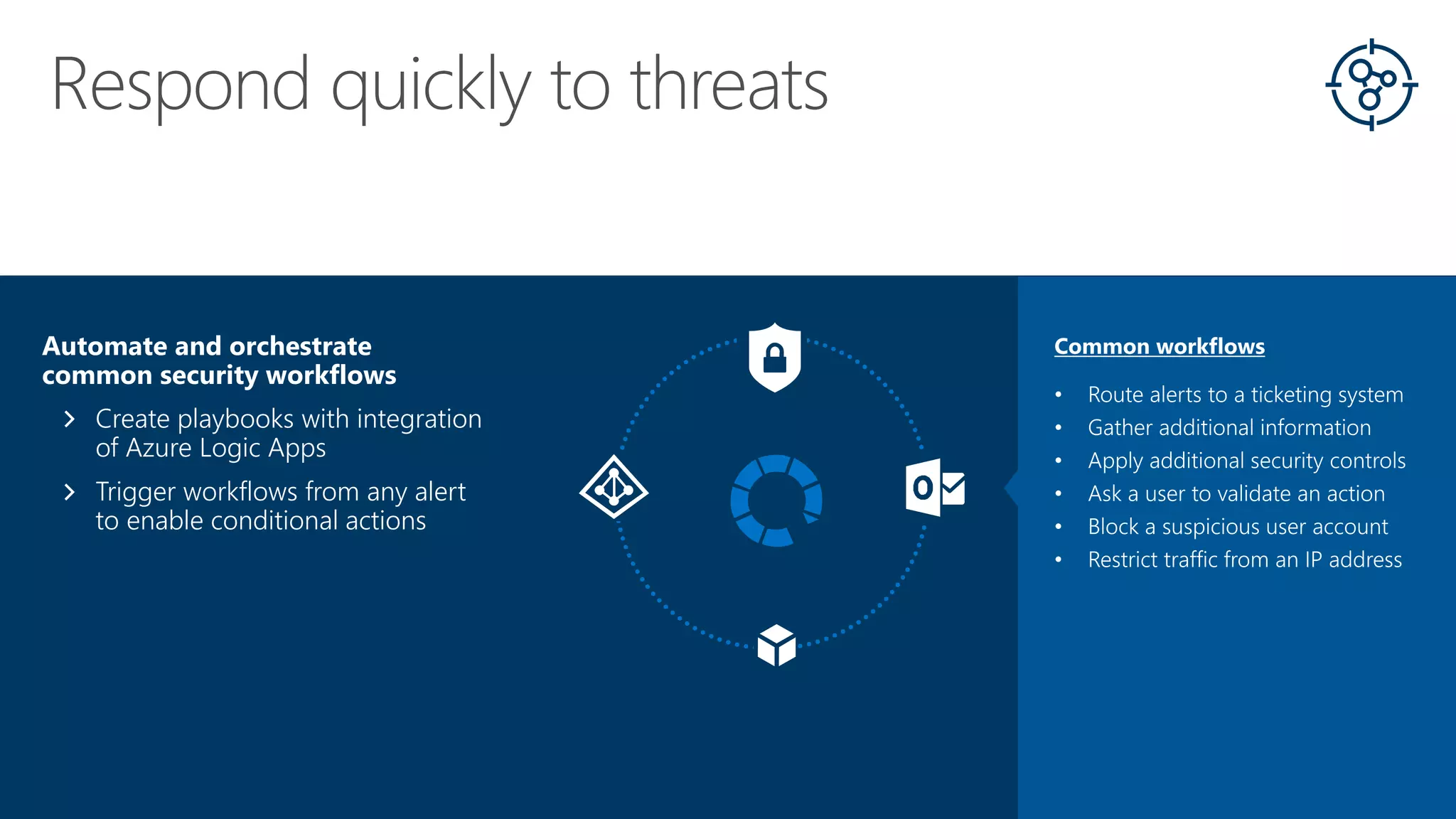
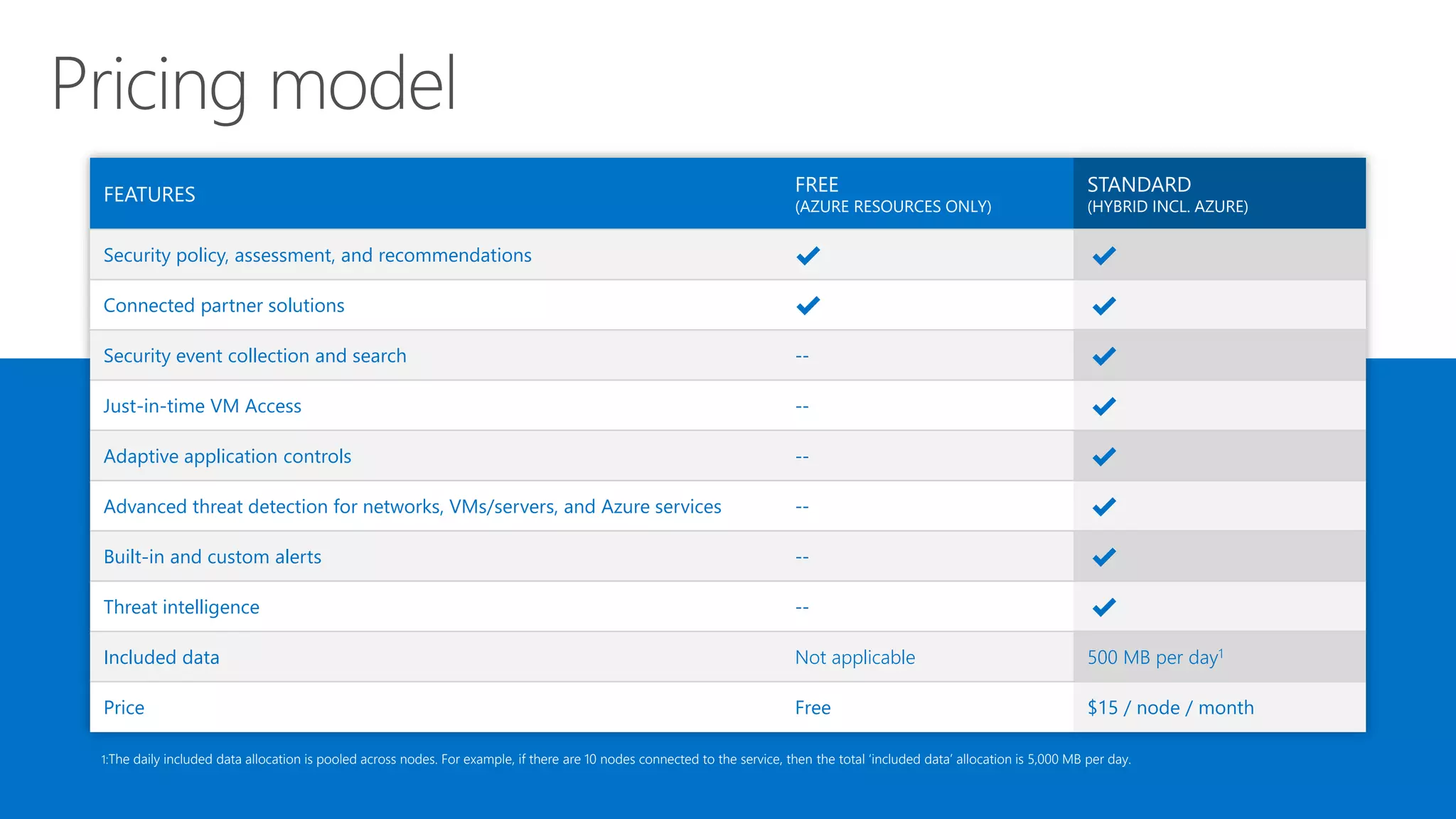
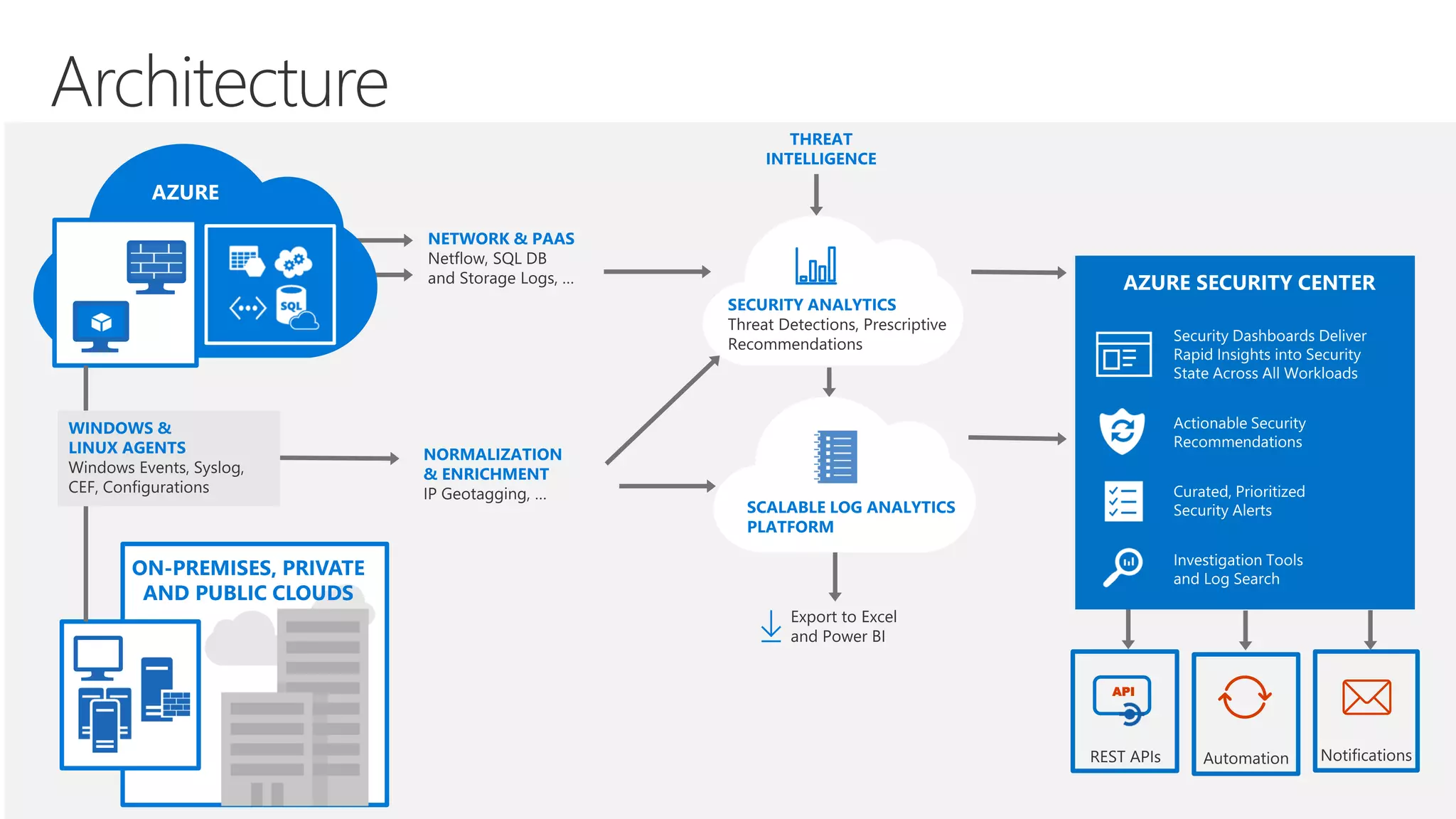
This document summarizes Azure Security Center, a service that provides unified visibility and control of security across hybrid cloud workloads. It dynamically discovers resources, enables adaptive threat prevention through assessments and recommendations, and provides intelligent detection and response using advanced analytics and Microsoft's Intelligent Security Graph. Customers gain insights through centralized security management and save time on security tasks. Azure Security Center is available in free and standard tiers that differ in features and pricing.