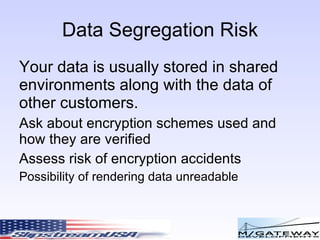
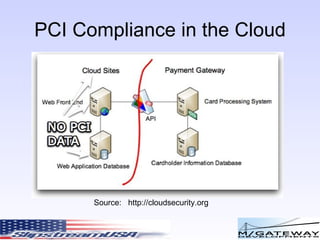
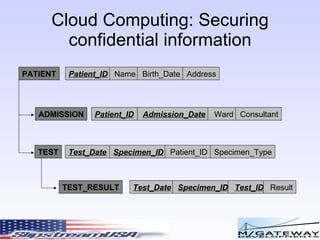
The document discusses various risks and security considerations related to cloud computing. It covers assessing risks from real world, corporate, and technical perspectives. Key risks include user access, data location, recovery risks, and ensuring regulatory compliance. The document also provides an overview of security standards like PCI compliance and approaches to securing confidential data and applications in the cloud.