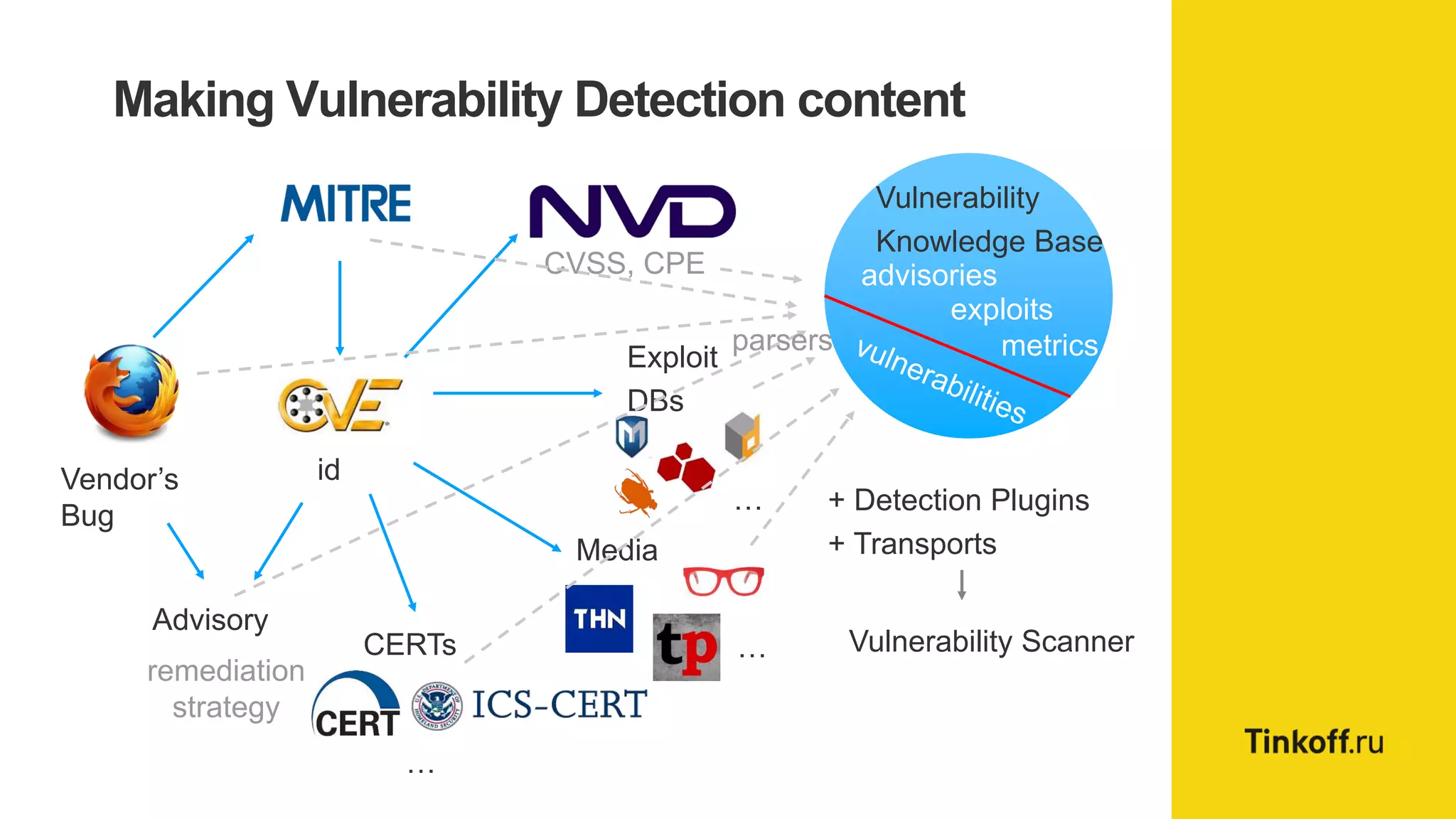
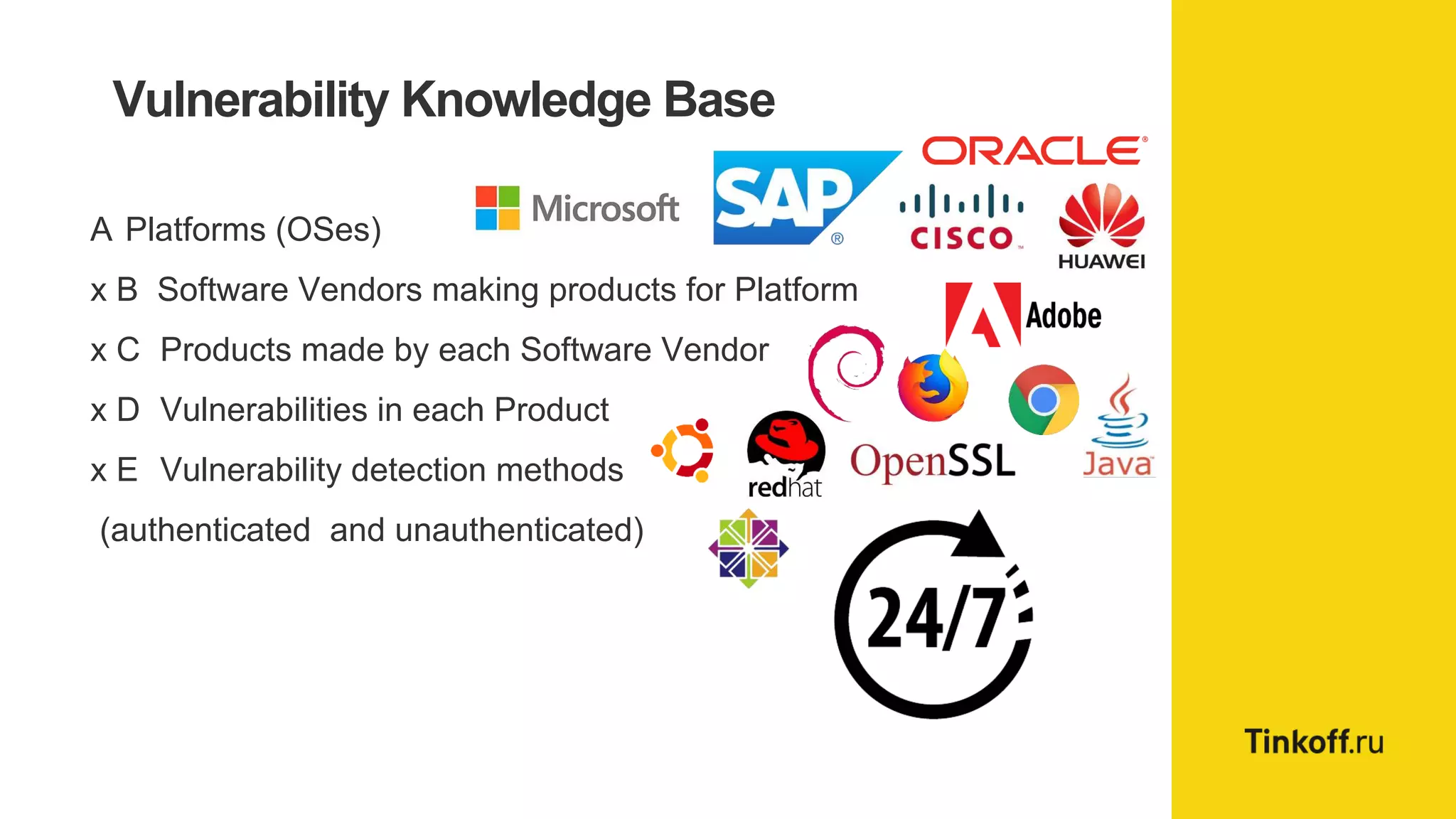
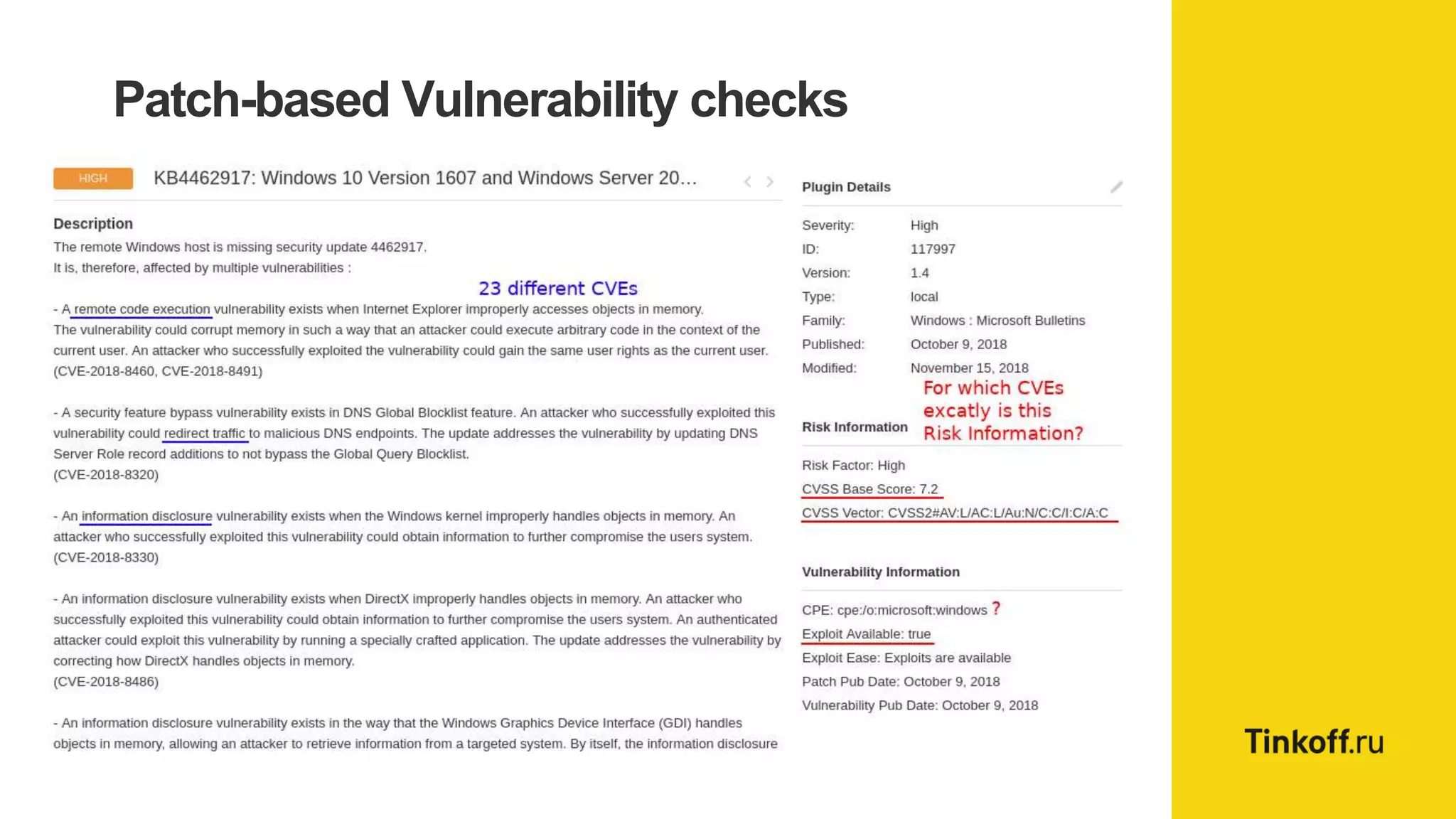
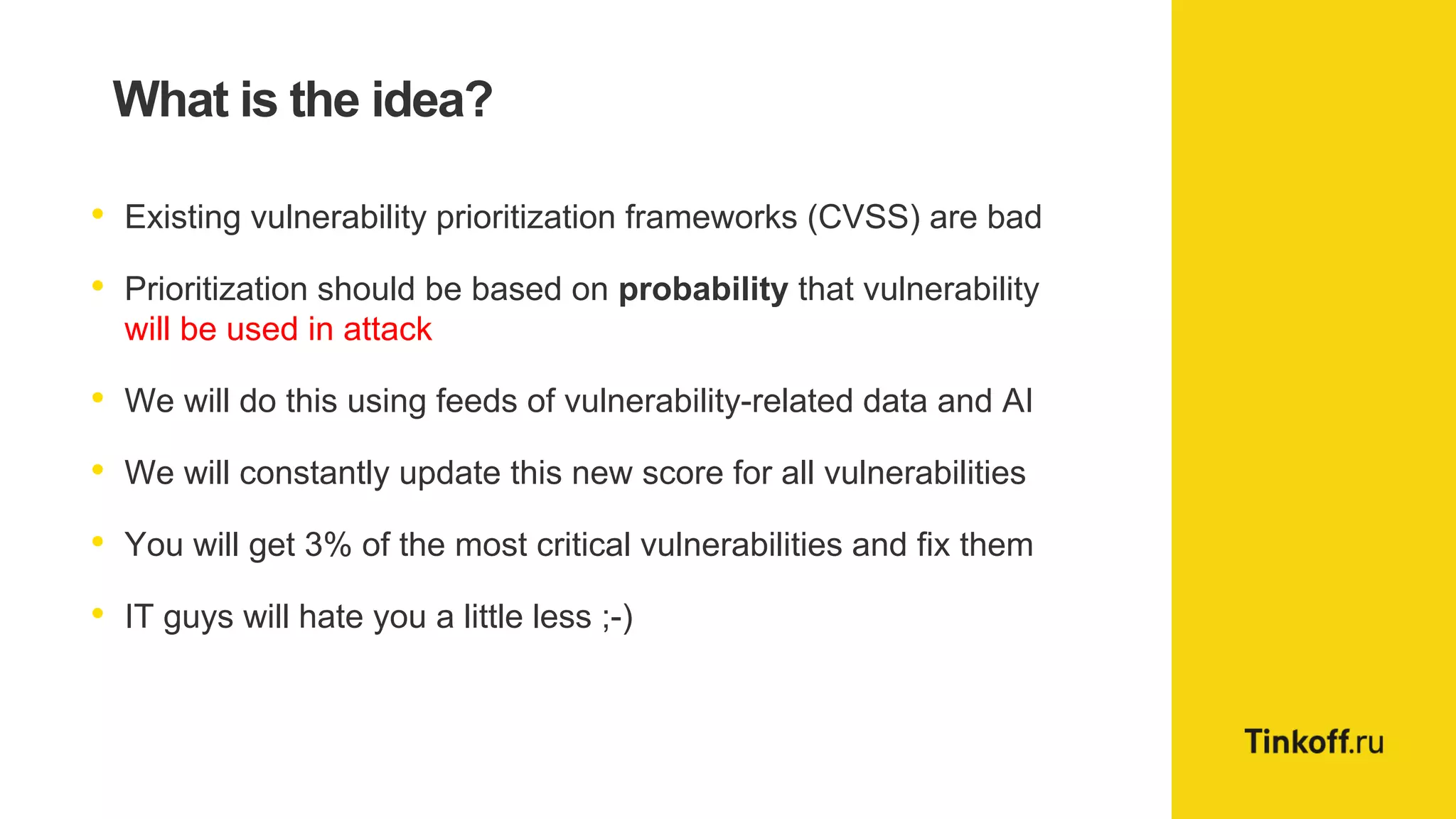
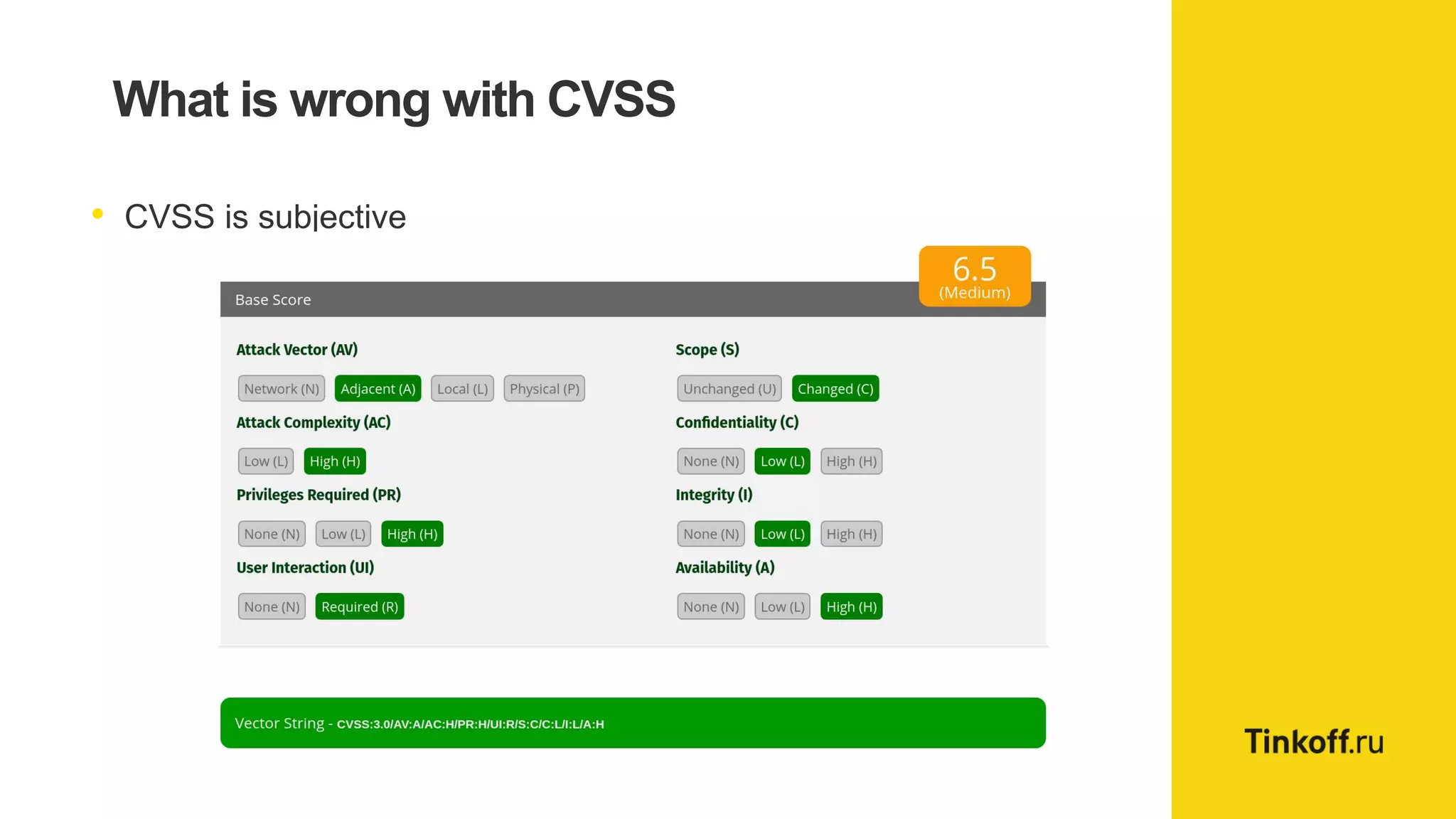
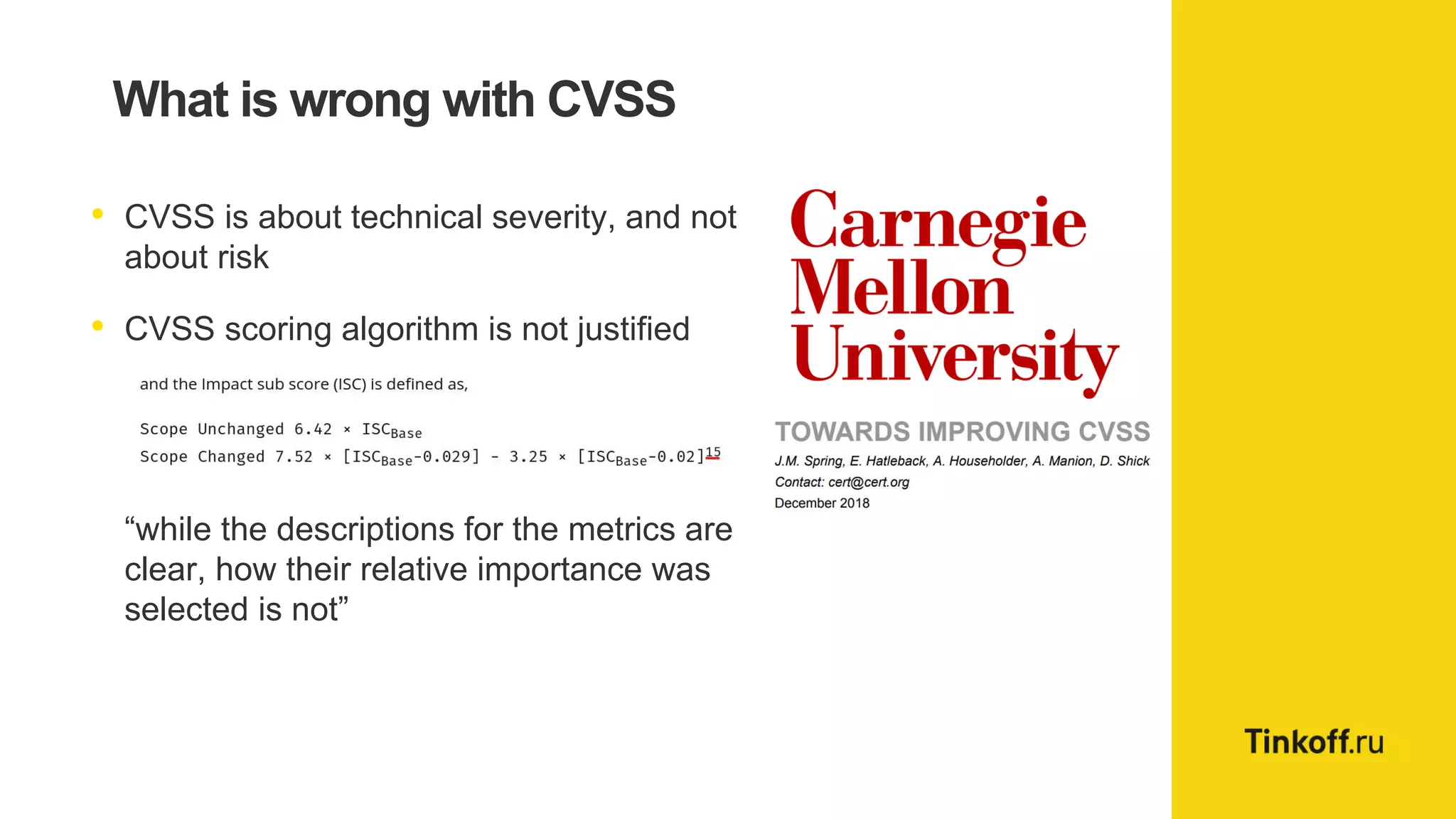
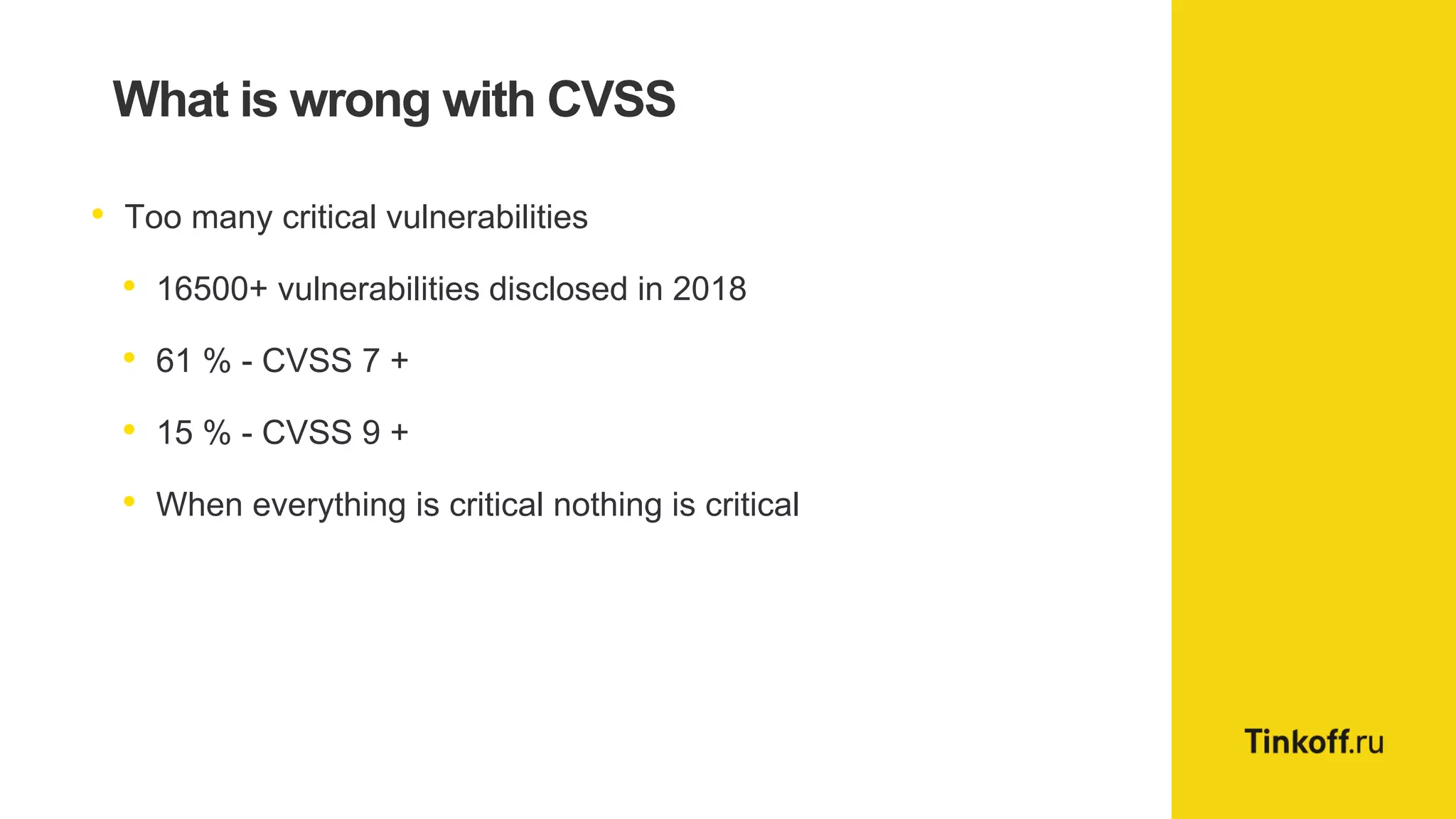
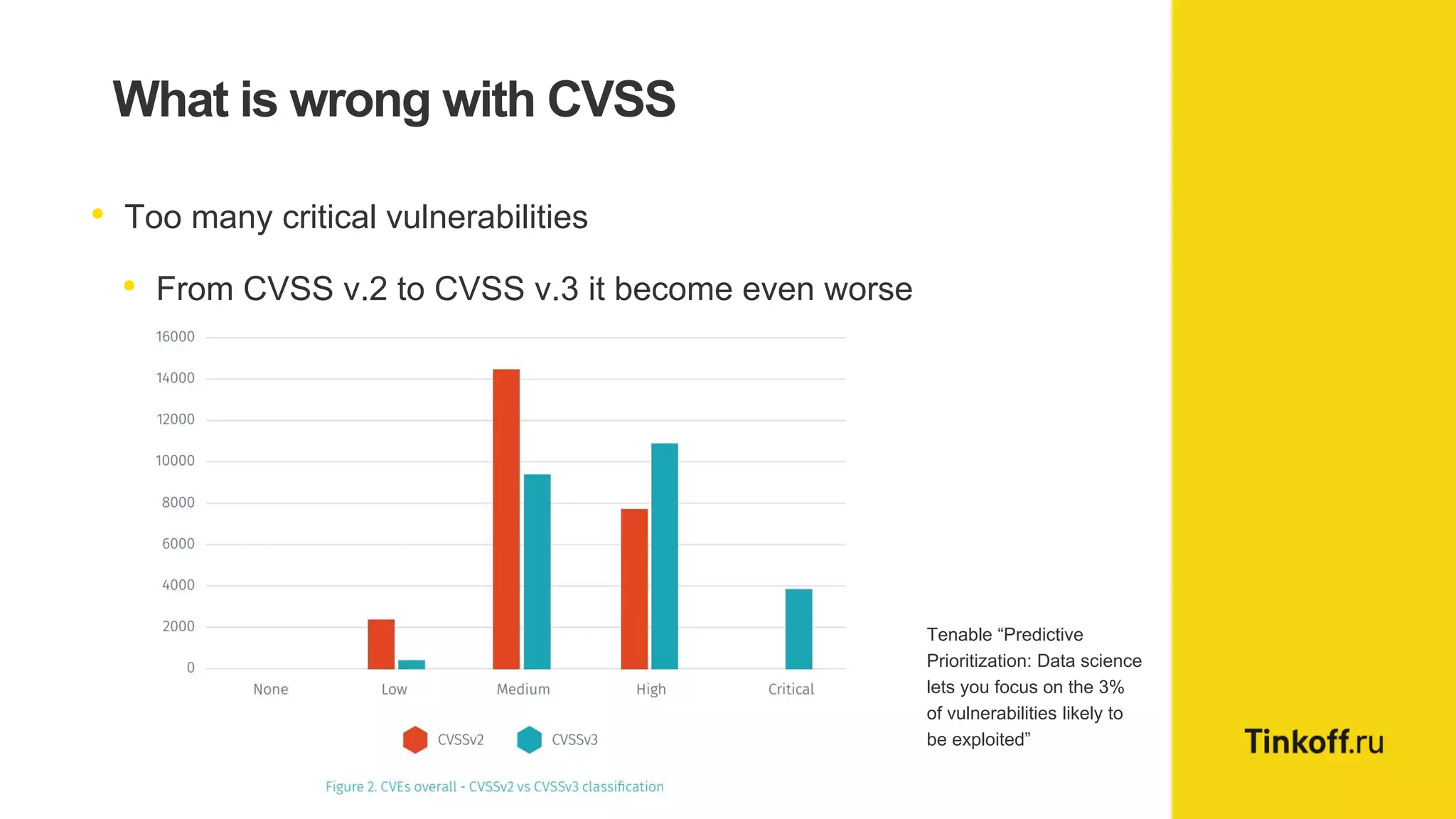
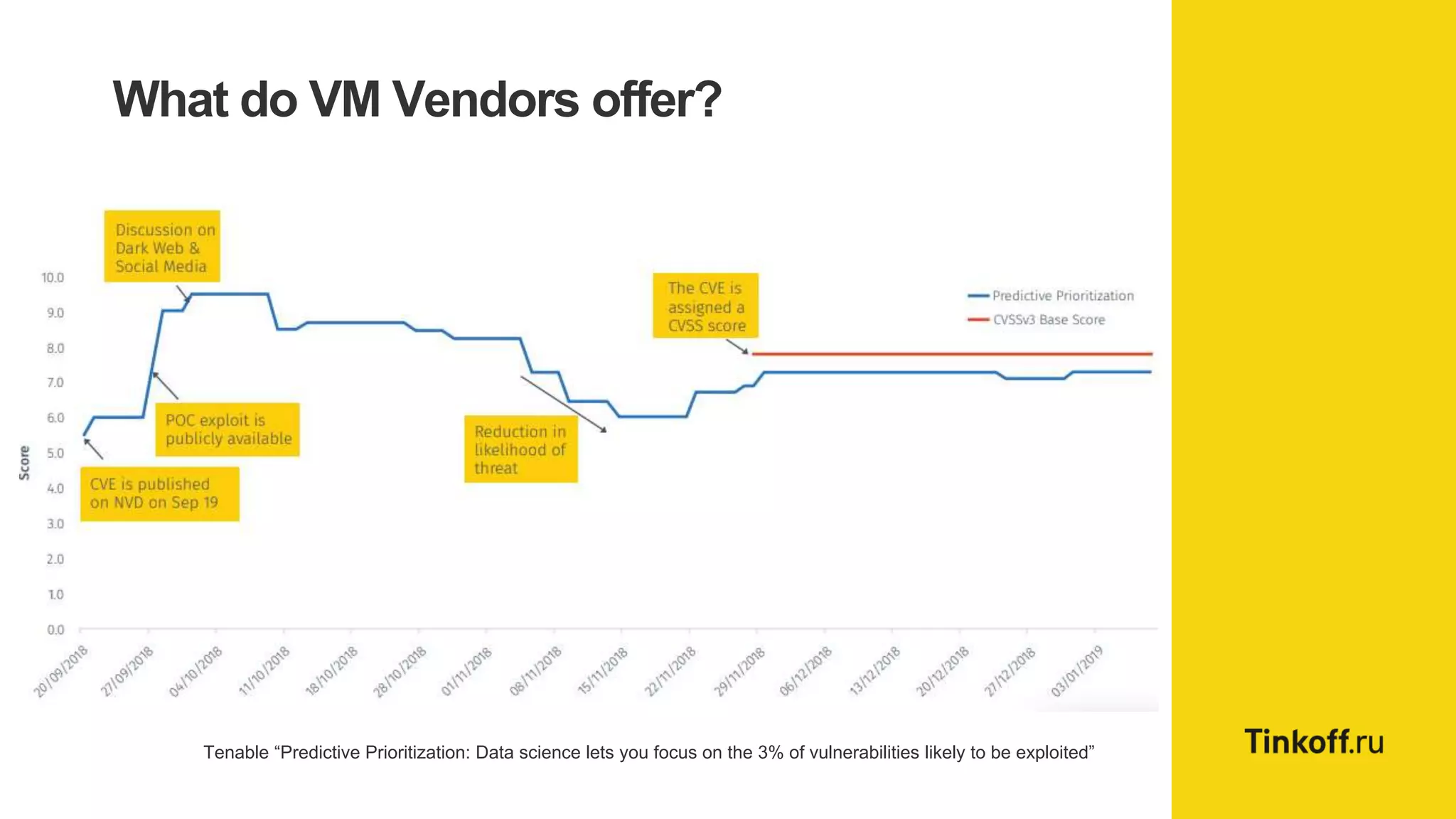
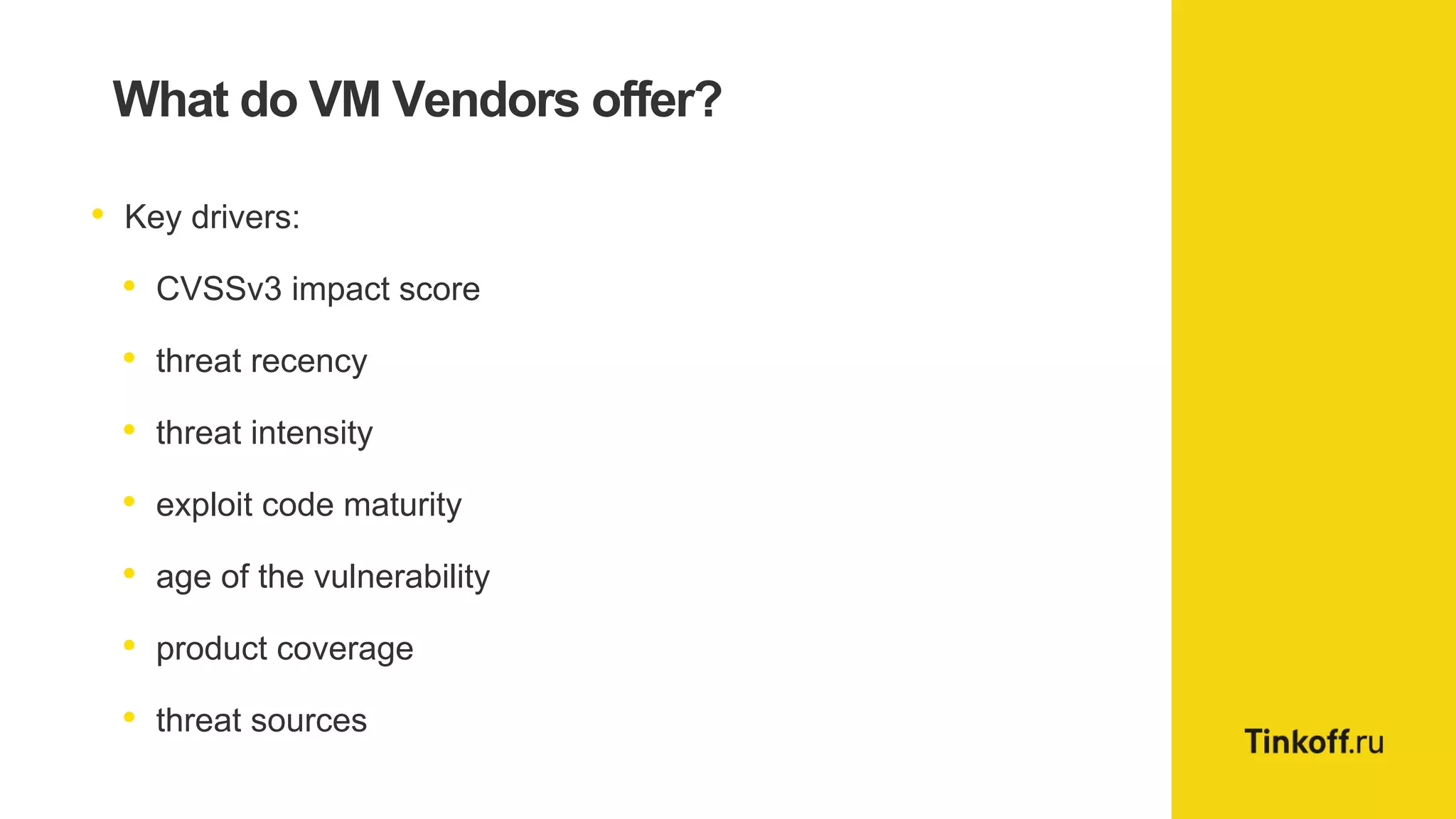
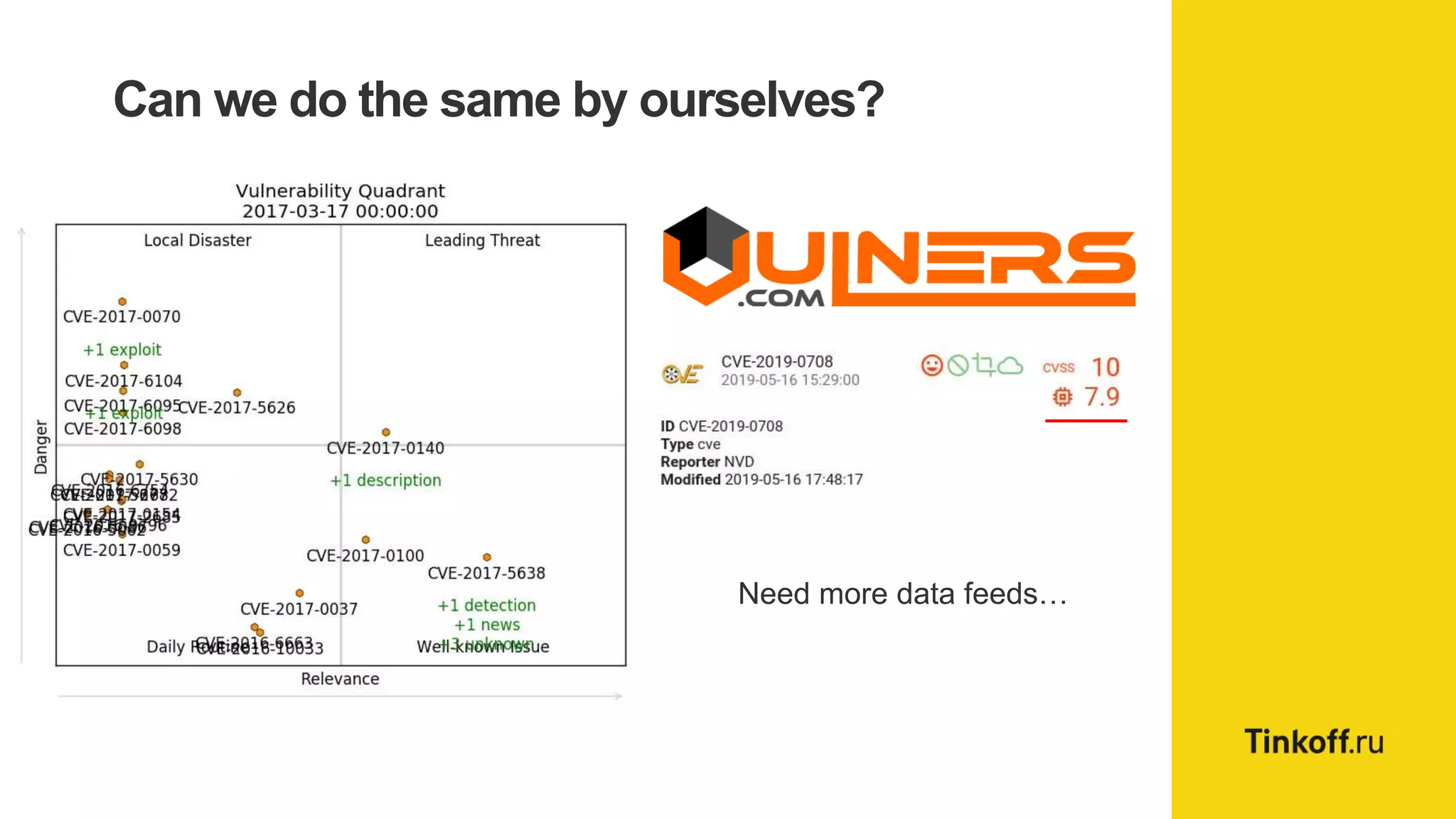
Alexander Leonov discusses the shortcomings of current vulnerability prioritization methods, particularly the CVSS framework, which fails to effectively assess the risk of vulnerabilities in the context of potential exploitation. He proposes a new approach to prioritization using predictive intelligence and data science to focus on the 3% of vulnerabilities most likely to be exploited. This method aims to provide more accurate prioritization by incorporating various data sources and continuously updating vulnerability scores.