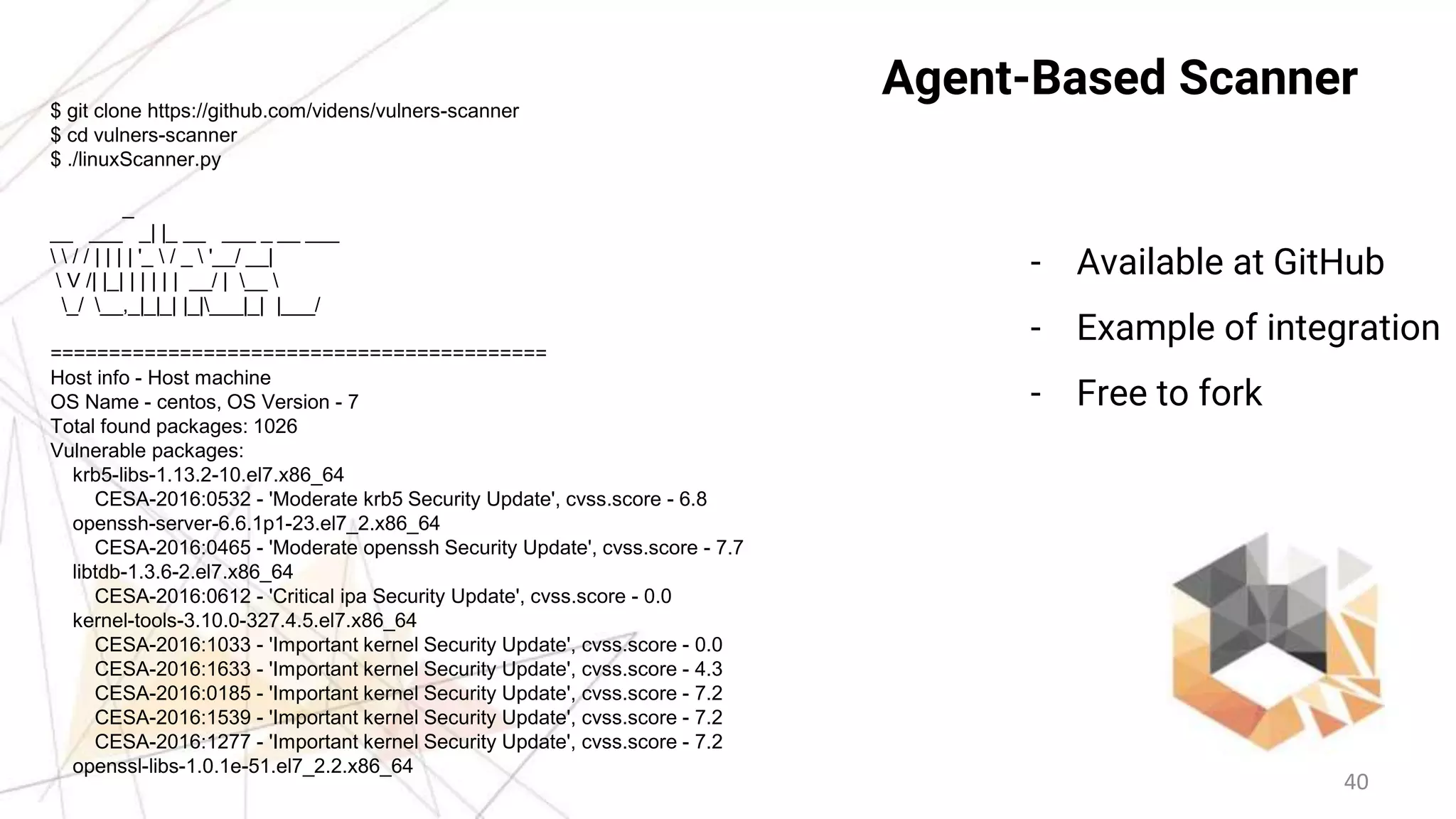
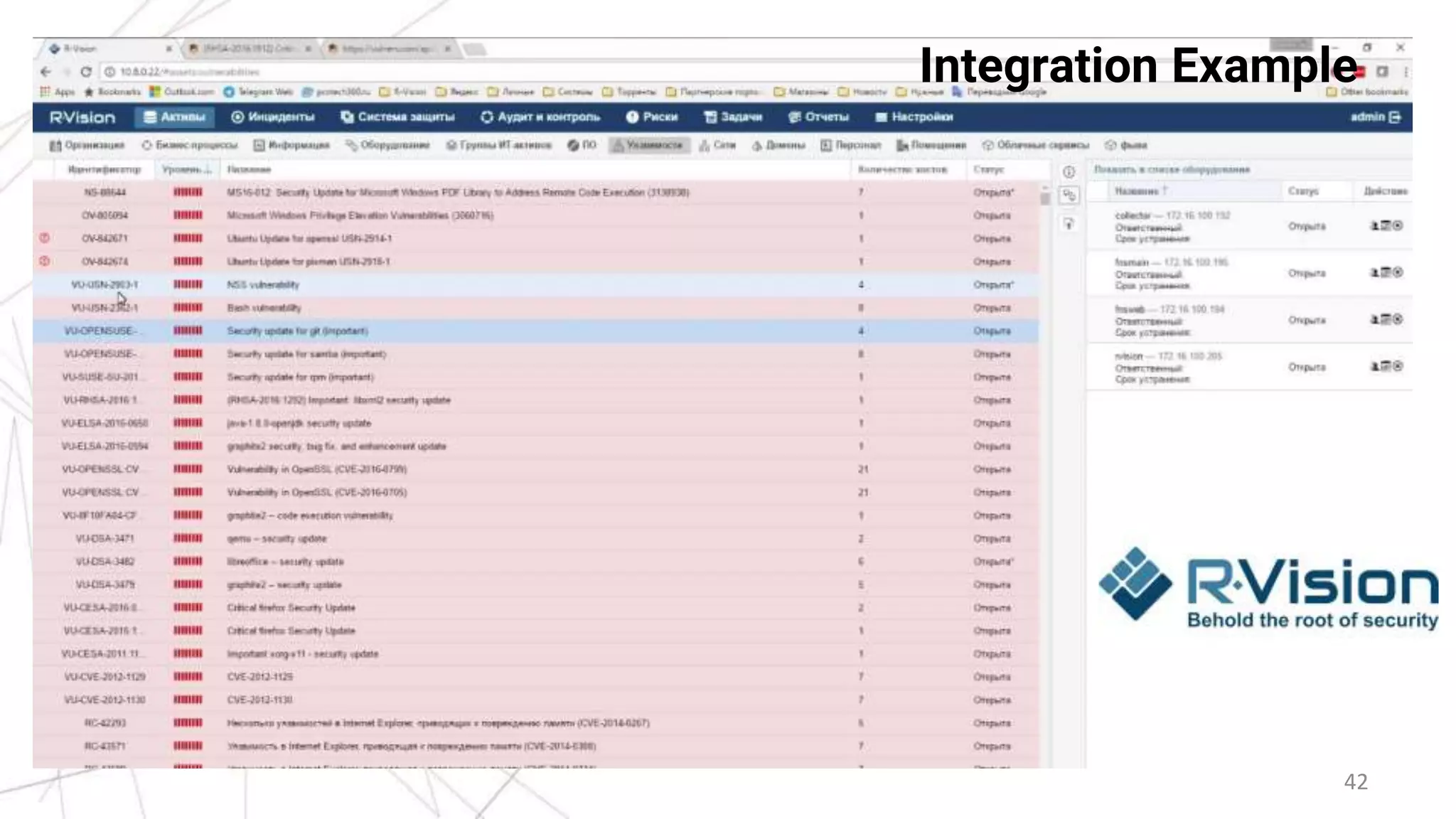
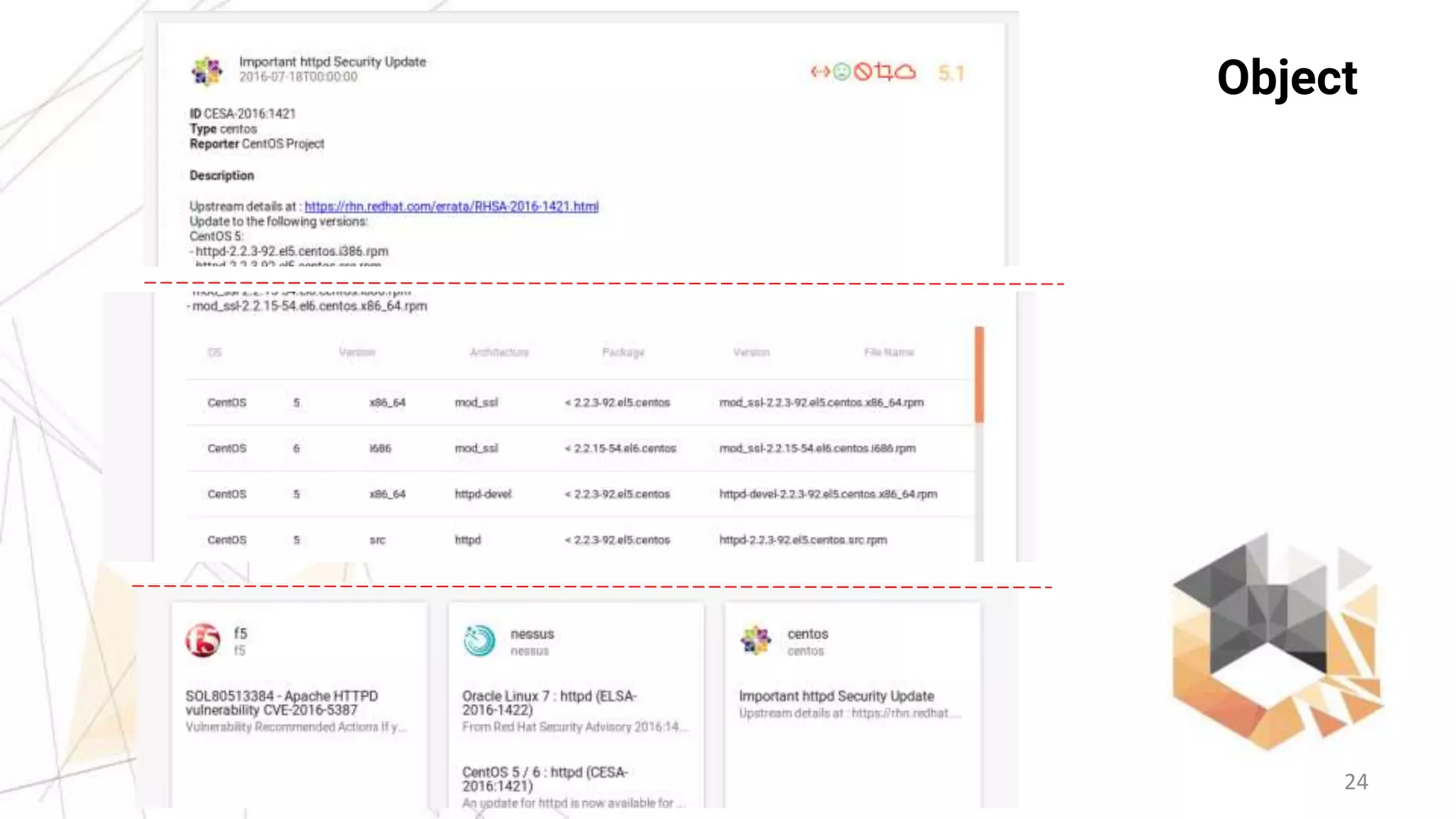
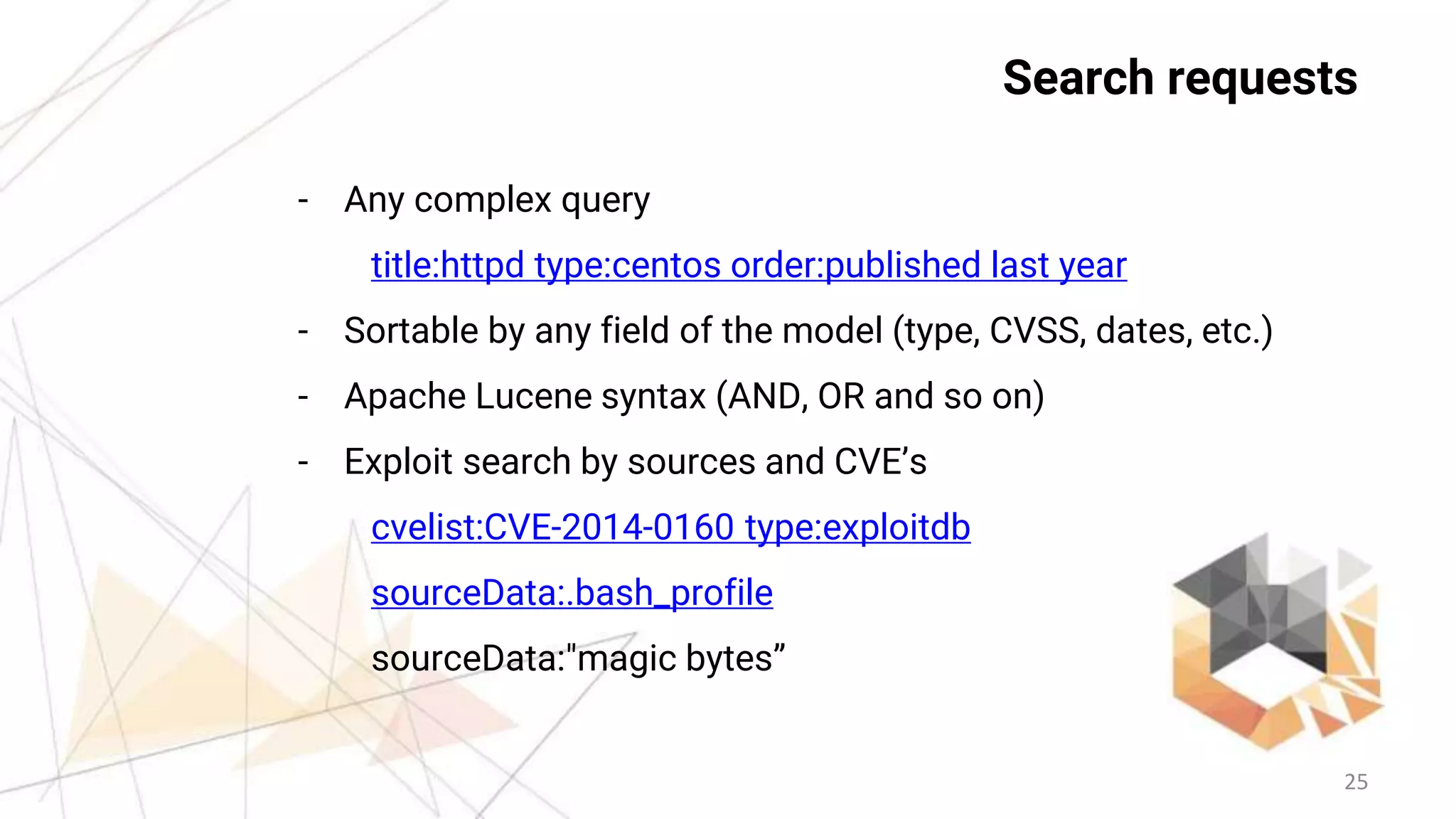
This document provides an overview of the Vulners Project, which aggregates vulnerability data from multiple sources to provide a comprehensive and machine-readable database. It describes Vulners' goals of being a centralized vulnerability search engine and information security "Google". Key features highlighted include a fast search engine, API, RSS feeds, email subscriptions, and tools for vulnerability scanning and auditing Linux systems. The document encourages integration of Vulners' data and using their free services for applications like security scanners and threat intelligence.











![26
Requests
- CentOS bulletins with remotely exploited vulnerabilities:
(type:centos AND (title:"Critical" OR title:"Important") AND
cvss.vector:"AV:NETWORK") order:published
- Important CVE vulnerabilities in Microsoft software:
(type:cve AND cvss.score:[6 TO 10] AND description:"Microsoft")
order:published
Search requests](https://image.slidesharecdn.com/vulnerspentestit-161022110511/75/Vulnerability-Intelligence-and-Assessment-with-vulners-com-26-2048.jpg)
![27
Search requests
- Nessus plugins for remotely exploited vulnerabilities; exclude
Windows:
type:nessus AND cvss.score:[6 TO 10] AND
cvss.vector:"AV:NETWORK" AND (NOT naslFamily:"Local" AND
NOT naslFamily:"Windows : Microsoft Bulletins" AND NOT
naslFamily:"Windows") order:published
- OpenSSL and OpenSSH vulnerabilities:
(type:openssl OR ( type:cve AND cpe:*openssh* ) )
order:published](https://image.slidesharecdn.com/vulnerspentestit-161022110511/75/Vulnerability-Intelligence-and-Assessment-with-vulners-com-27-2048.jpg)
![29
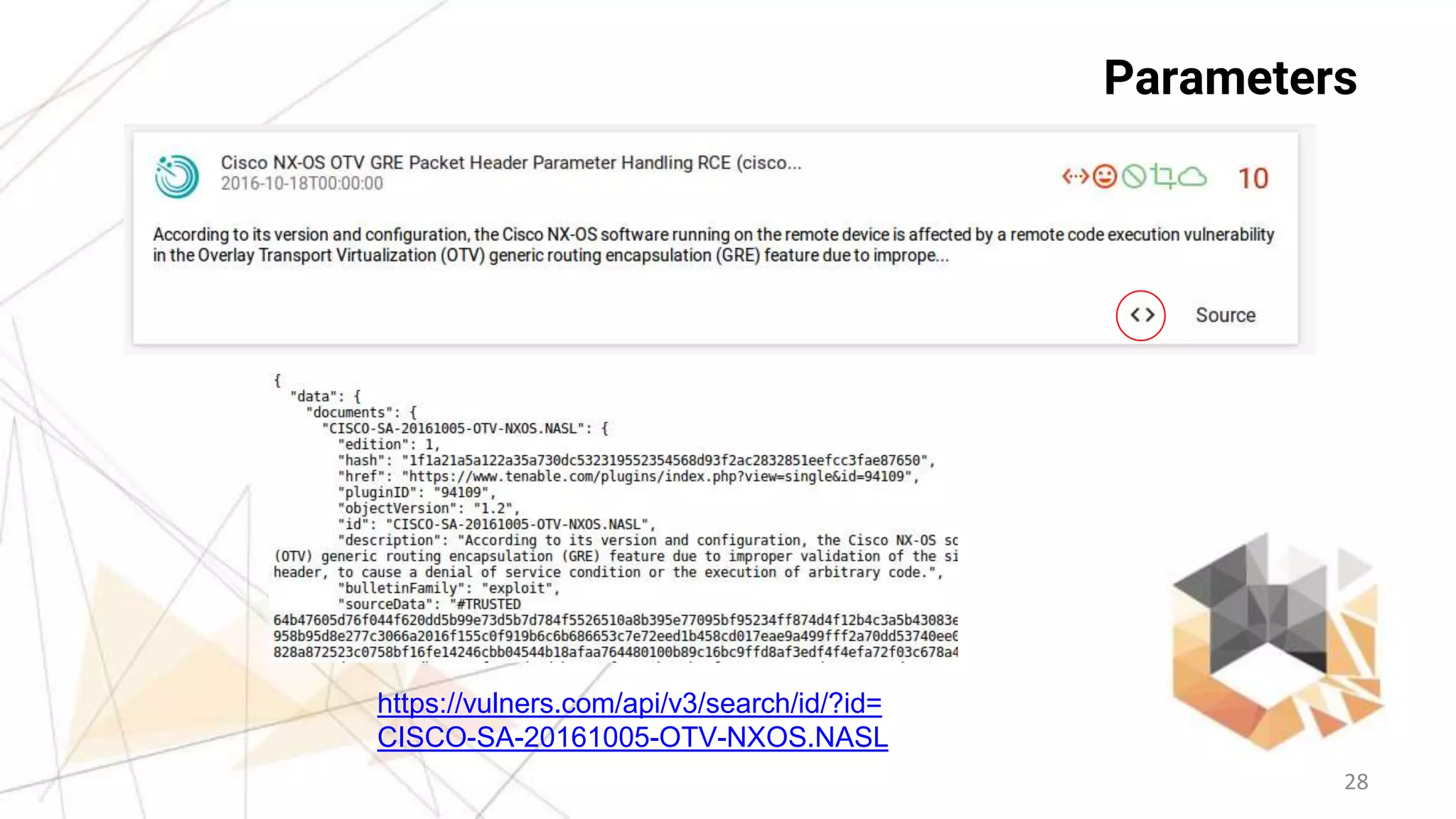
Search API
- GET/POST REST API with JSON output
- Search
https://vulners.com/api/v3/search/lucene/?query=type:centos%2
0cvss.score:[8%20TO%2010]%20order:published
- Information
https://vulners.com/api/v3/search/id?id=CESA-2016:1237
&references=true
- Export
https://vulners.com/api/v3/archive/collection?
type=exploitdb](https://image.slidesharecdn.com/vulnerspentestit-161022110511/75/Vulnerability-Intelligence-and-Assessment-with-vulners-com-29-2048.jpg)
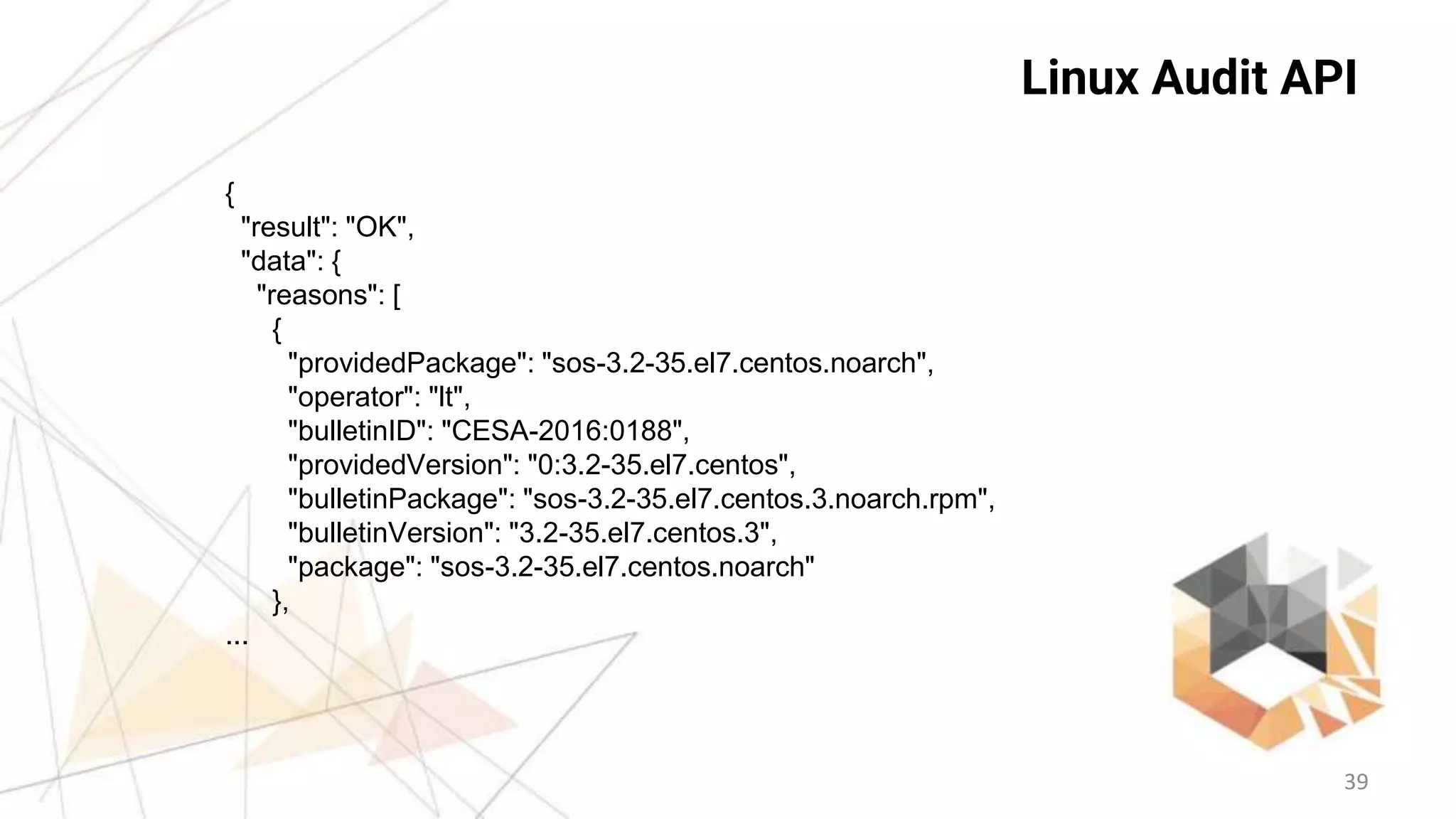
![37
Linux Audit API
curl -H "Accept: application/json" -H "Content-Type: application/json" -X POST -d
'{"os":"centos","package":["pcre-8.32-15.el7.x86_64", "samba-common-4.2.3-
11.el7_2.noarch", "gnu-free-fonts-common-20120503-8.el7.noarch", "libreport-centos-
2.1.11-32.el7.centos.x86_64", "libacl-2.2.51-12.el7.x86_64"],"version":"7"}'
https://vulners.com/api/v3/audit/audit/](https://image.slidesharecdn.com/vulnerspentestit-161022110511/75/Vulnerability-Intelligence-and-Assessment-with-vulners-com-37-2048.jpg)