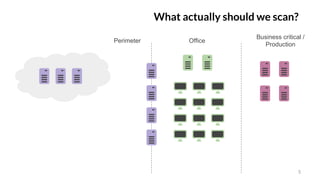
The document discusses the complexities of enterprise vulnerability management, emphasizing the discrepancies between vendor marketing and real-world challenges faced by security analysts. It outlines the typical environments, asset management difficulties, and issues like unexplored vulnerabilities and patching inefficiencies. The author advocates for the practical use of vulnerability scanners while highlighting the necessity for customized automation to manage vulnerabilities effectively.