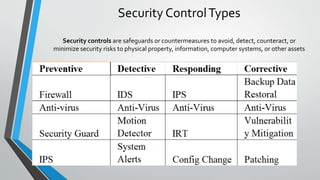
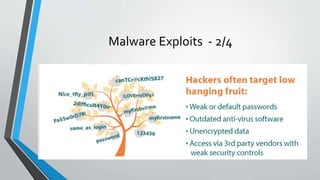
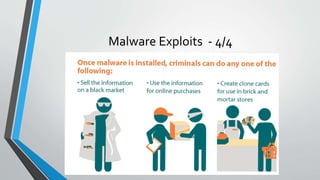
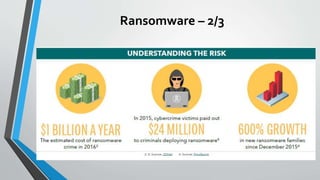
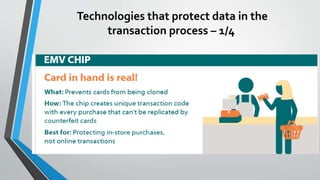
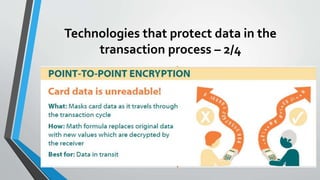
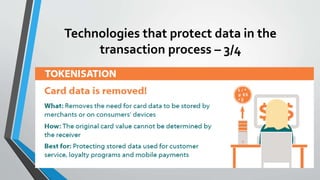
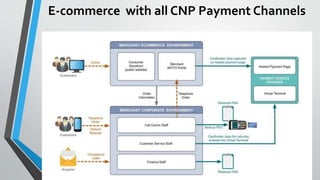
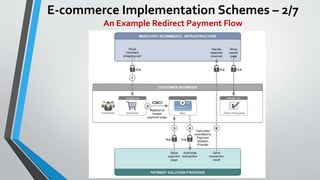
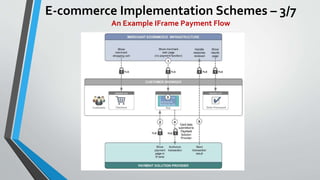
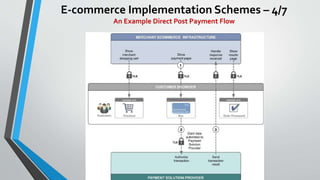
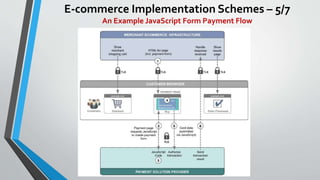
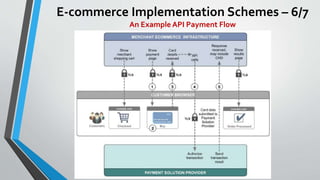
The document discusses cybersecurity issues in the payment card industry, focusing on vulnerabilities, common attack vectors, and the impact of transitioning to chip card technology. It emphasizes the importance of adhering to Payment Card Industry Data Security Standards and outlines strategies for preventing data breaches, including the use of EMV chips and effective phishing defenses. The document also recommends best practices for businesses to protect themselves and their customers from increasing cyber threats.