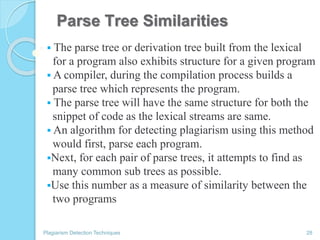
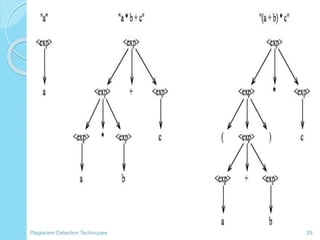
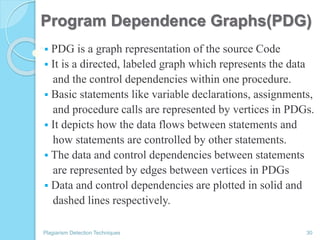
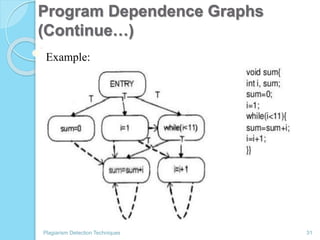
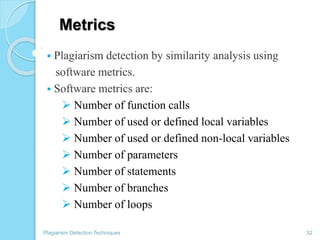
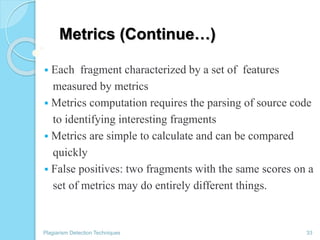
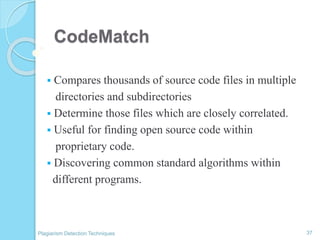
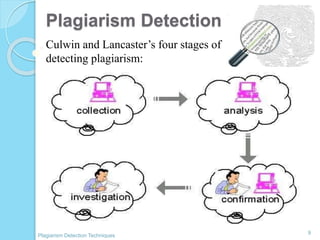
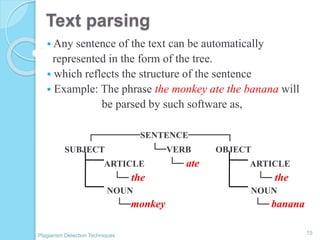
The document discusses various techniques for detecting plagiarism in text and source code. It defines plagiarism and describes how to avoid it through prevention and detection. For text, it covers substring matching, keyword similarity, fingerprint matching, and text parsing techniques. For source code, it discusses lexical similarities, parse trees, program dependence graphs, and metrics. It also provides examples of tools used for each type of plagiarism detection like PlagAware, MOSS, and JPlag.



















![Lexical Similarities (Continue…)
Consider the following two snippets of Java Code:
Plagiarism Detection Techniques 26
int[] A = {1,2,3,4};
for(int i = 0; i < A.length; i++)
{
A[i] = A[i] + 1;
}
int[] B = {1, 2, 3, 4};
for(int j = 0; j < B.length; j++)
{
B[j] = B[j] + 1;
}](https://image.slidesharecdn.com/13mca11030-160415174315/85/plagiarism-detection-tools-and-techniques-27-320.jpg)