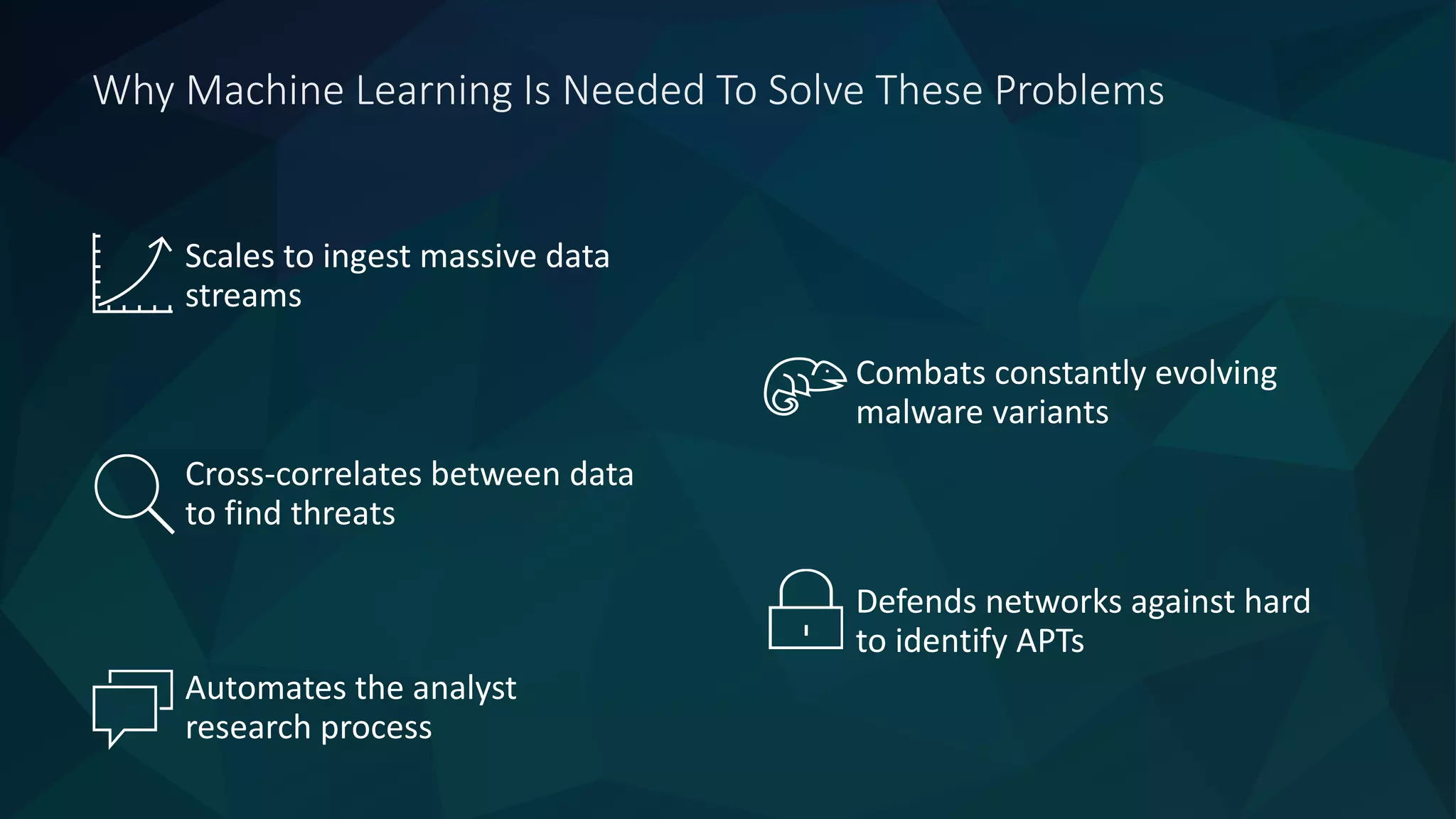
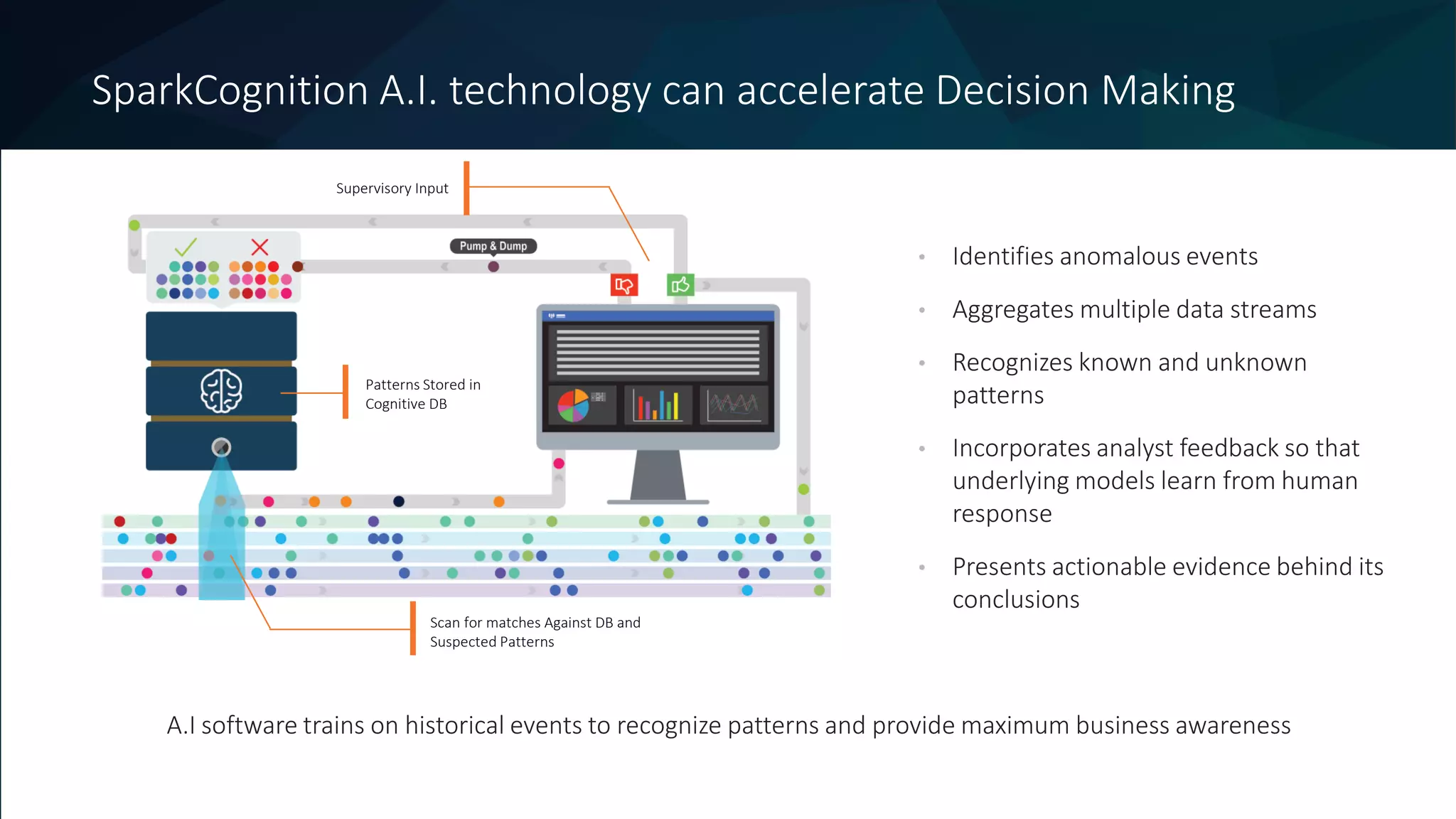
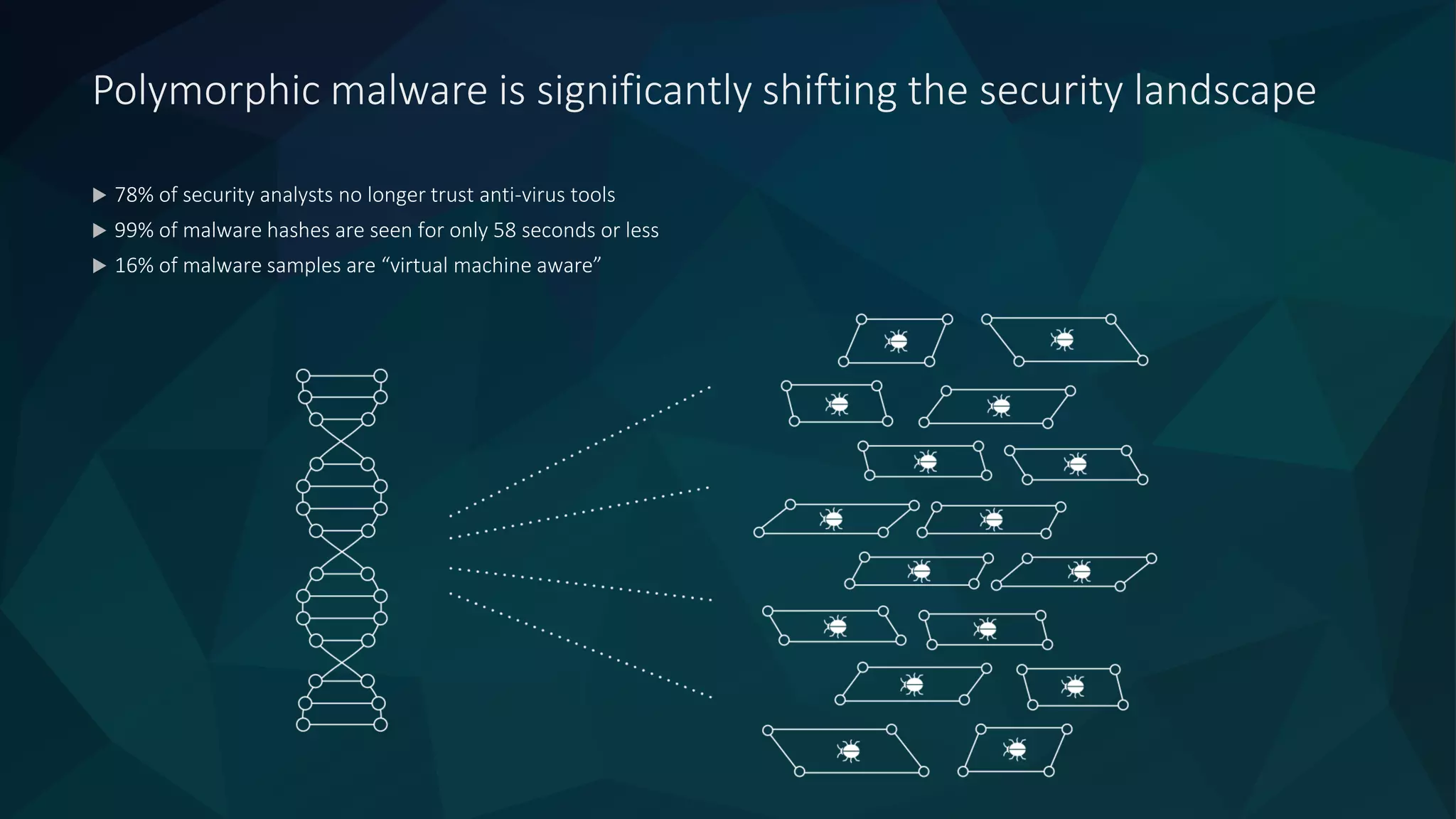
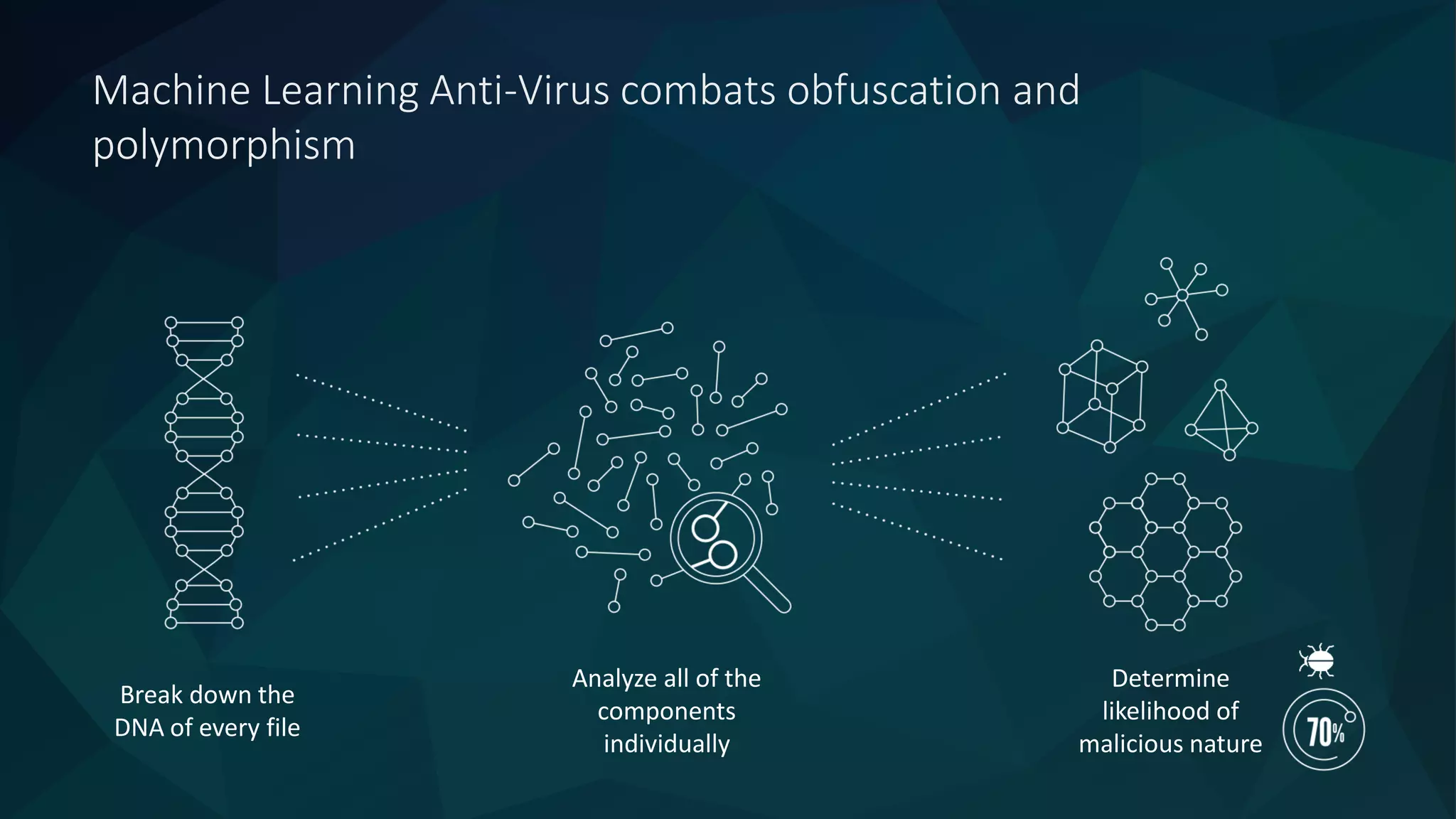
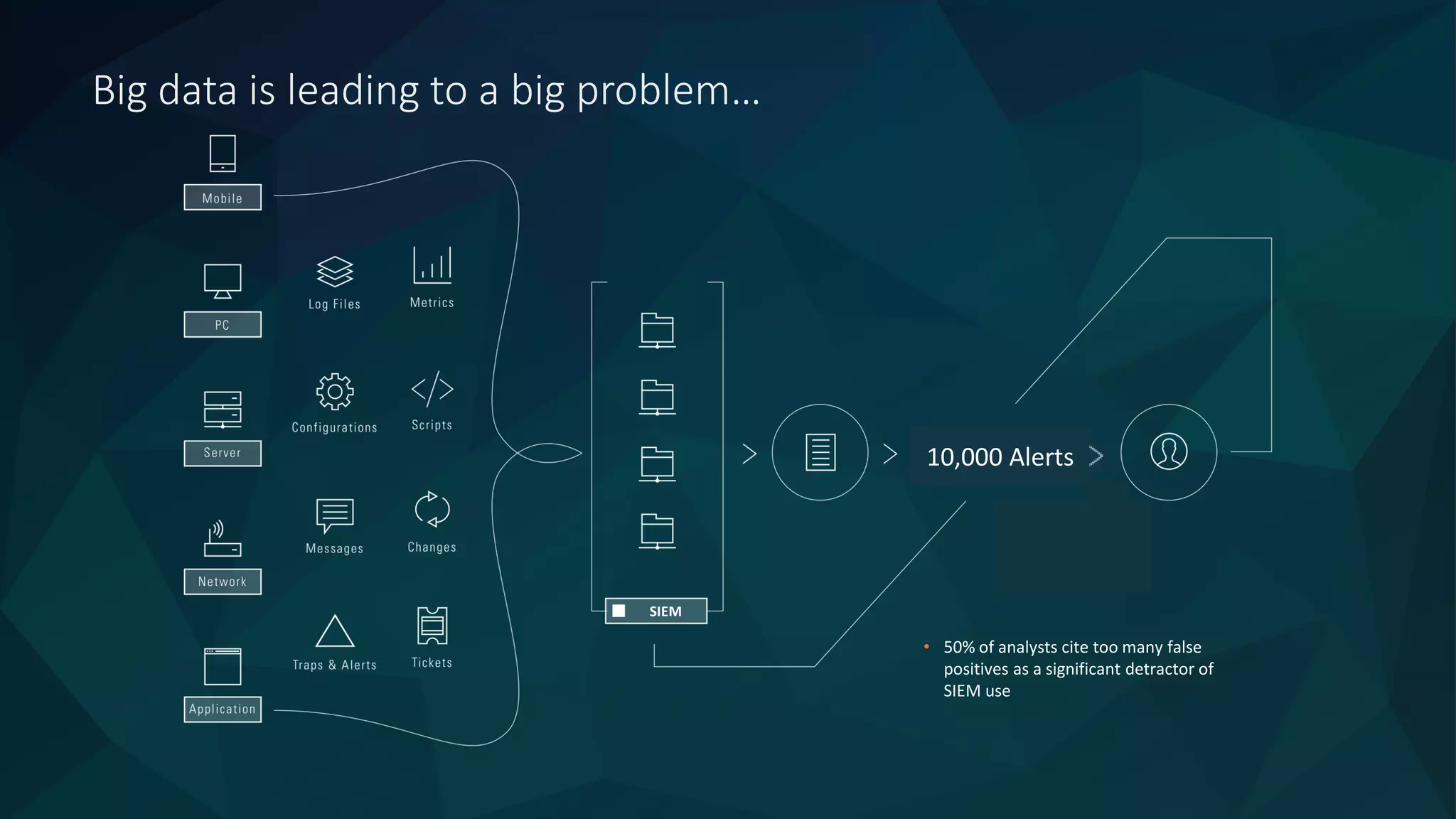
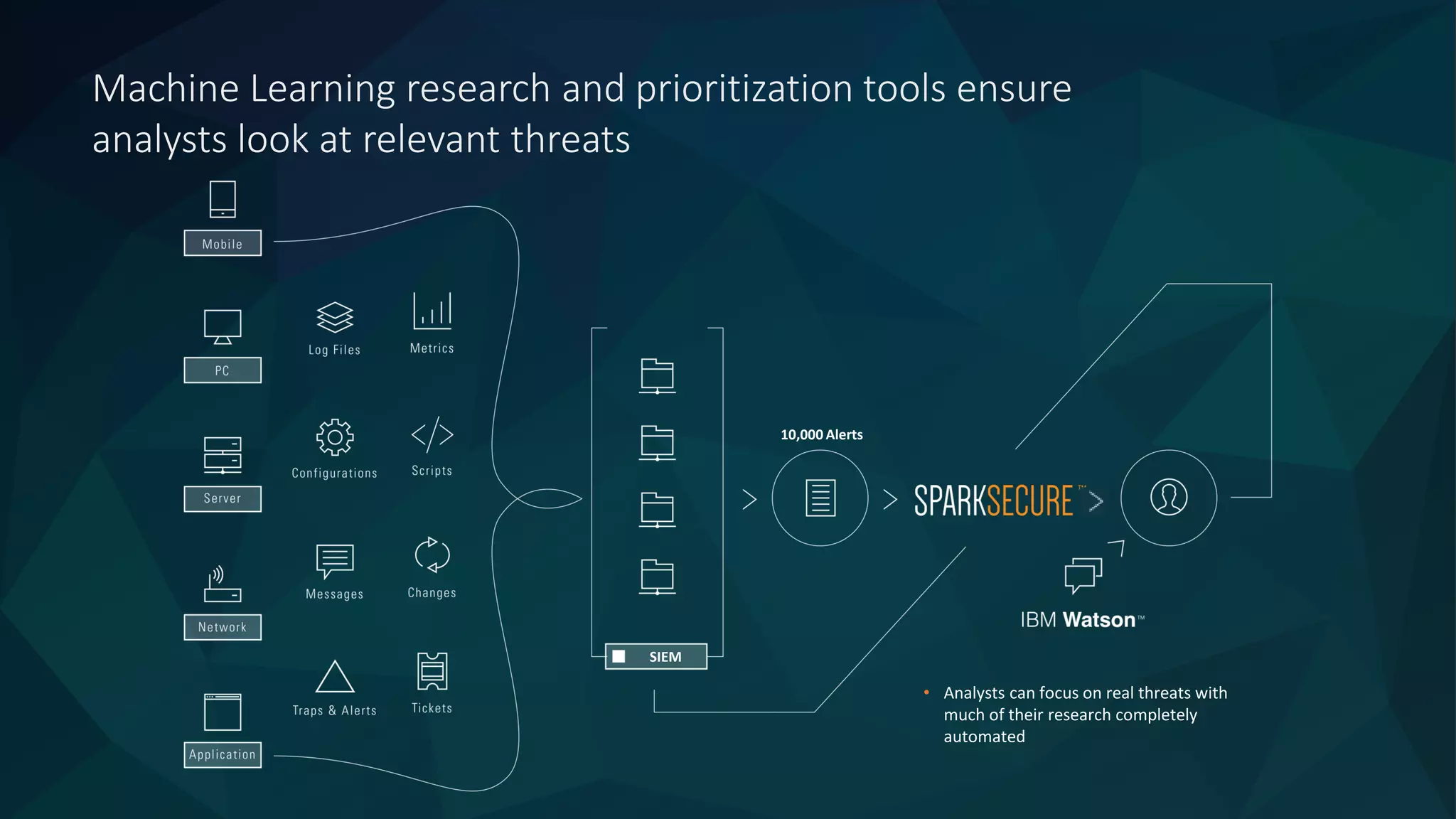
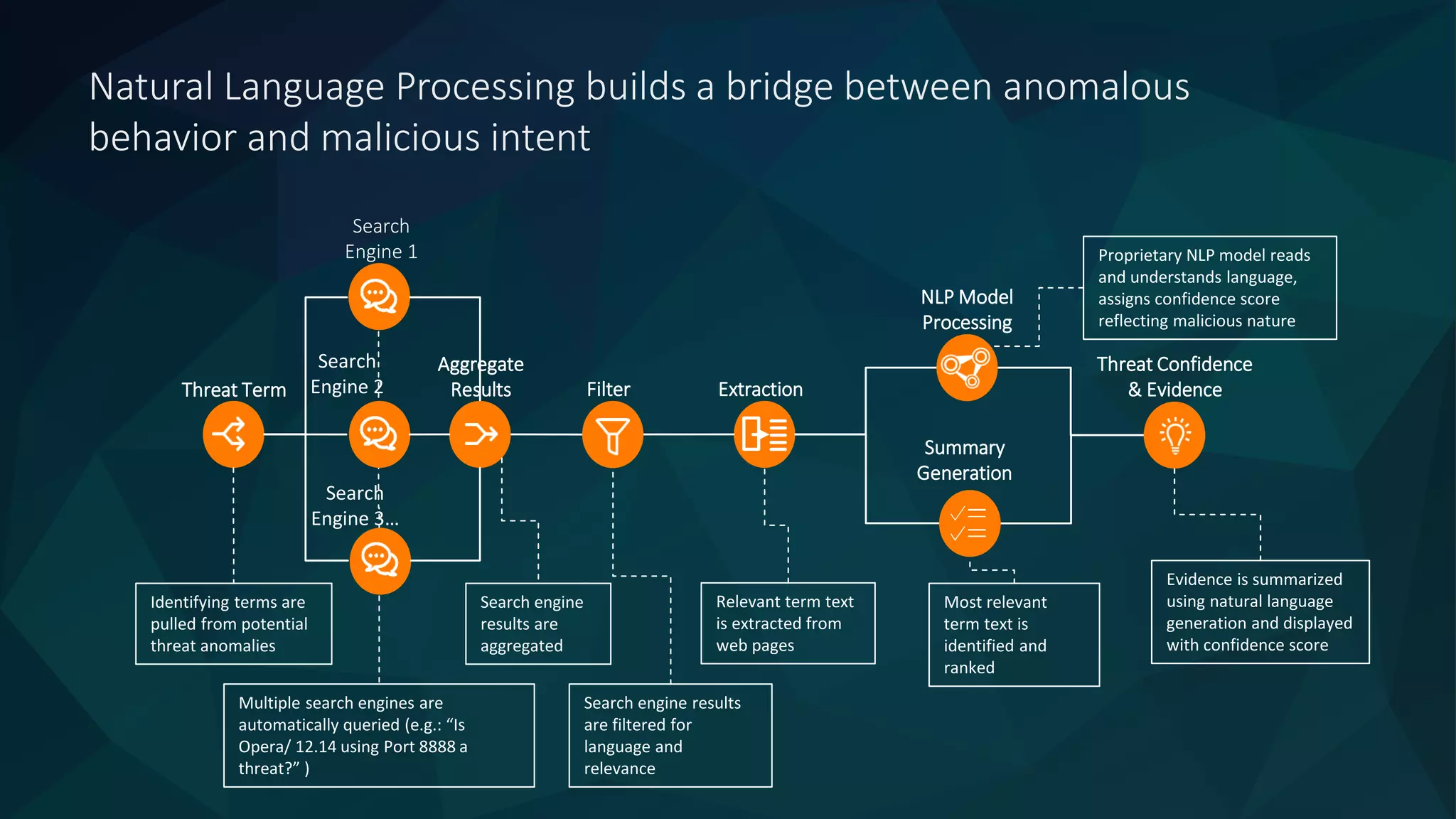
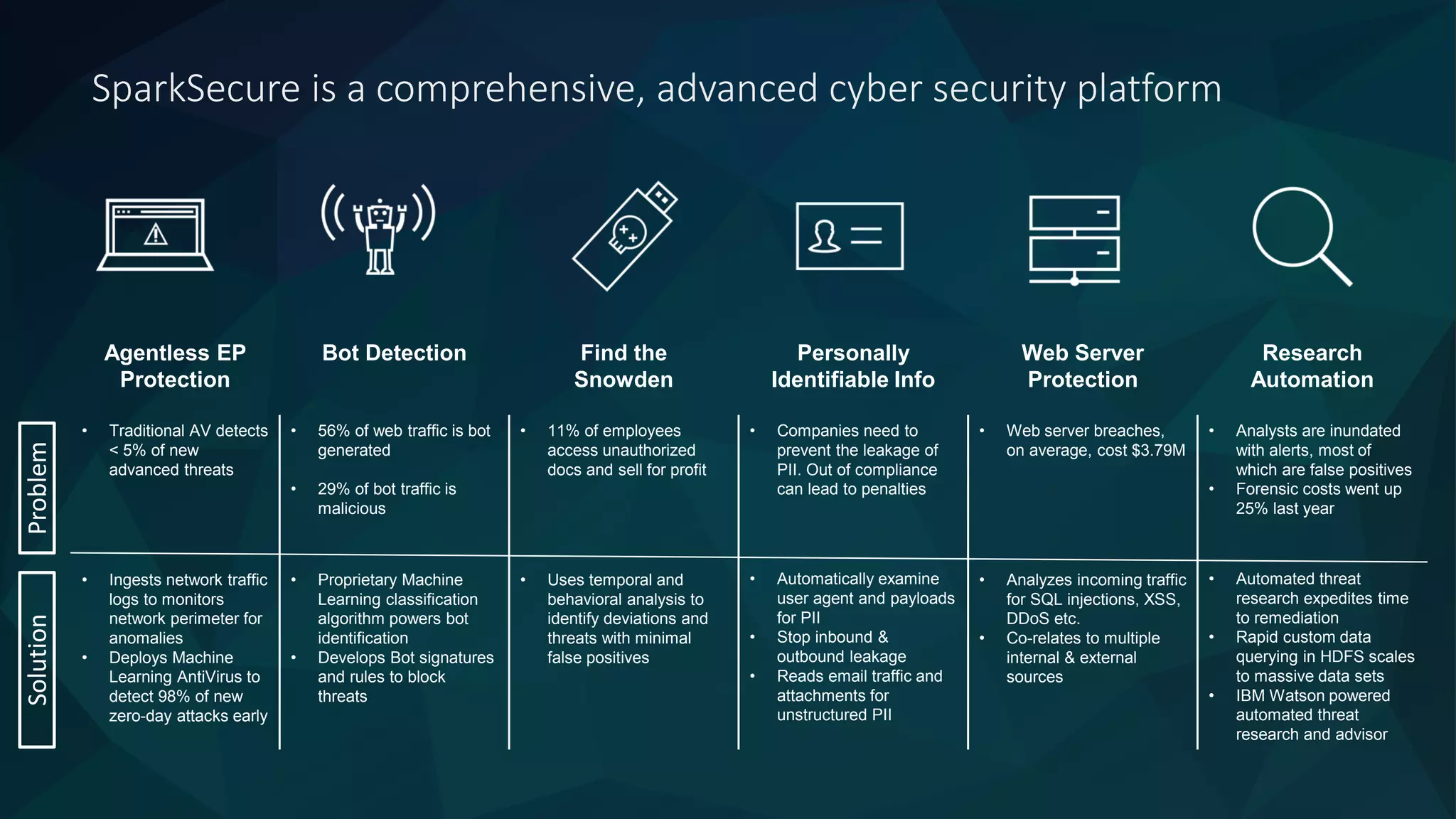
The document discusses the role of machine learning in enhancing cybersecurity, highlighting its capabilities in automating the analysis process, identifying threats, and reducing false positives. It emphasizes how SparkCognition's technology can combat evolving malware and improve operational efficiency for analysts. The platform leverages natural language processing and machine learning to provide actionable insights and effectively address various cybersecurity challenges.