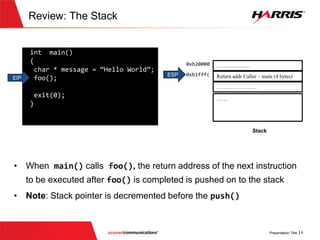
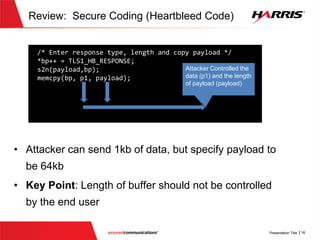
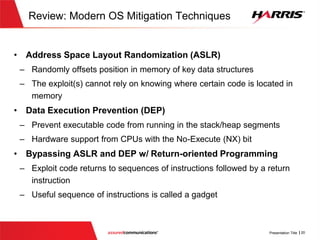
The document discusses offensive cybersecurity, particularly focusing on exploiting vulnerabilities in software written in C/C++. It illustrates the concept of 'smashing the stack', detailing the steps and coding practices that lead to potential exploits, including case studies like Heartbleed. The presentation emphasizes the importance of understanding offensive techniques to improve defensive coding practices and includes a section on leveraging Python for exploitation after gaining unauthorized access.















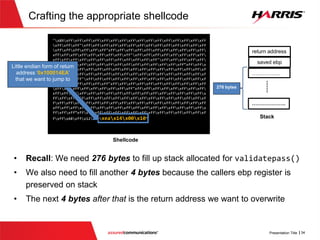
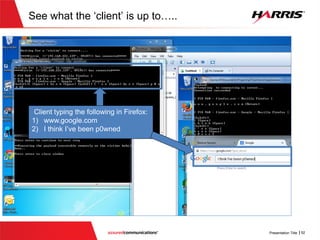
![Smashing the Stack (Vulnerable Sever)
validpassword=validatePassword(usercredential_buff,password_len,username_len);
if(validpassword)
{
printf("Determining if user is rootn");
char * username =strtok(usercredential_buff, DELIMETER);
if (strcmp(username,"root")==0)
{
message = "Administrative access to system shell granted.";
send(new_socket , message , strlen(message) , 0);
while(1)
{
message = "Enter command to execute:";
send(new_socket , message , strlen(message) , 0);
//Receiving command
valread= recv( new_socket , command_buff, MAXRECV, 0);
if(valread <=0) {break; }
command_buff[valread] = NULL;
//Executing command
int retval = system(command_buff);
}
}
}
Executes a
command provided
by remote user
Appears that this
region can be
accessed only
with appropriate
credentials](https://image.slidesharecdn.com/offensivecybersecuritysmashingthestackfinal-150728114644-lva1-app6891/85/Offensive-cyber-security-Smashing-the-stack-with-Python-22-320.jpg)

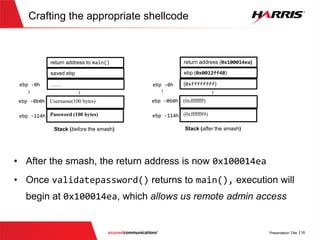
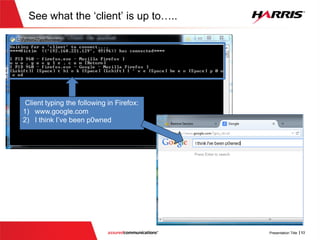
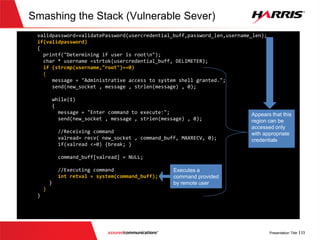
![Smashing the Stack (Vulnerable Code)
v
bool validatePassword(char * usercredential, int password_len, int username_len)
{
char username[100];
char password[100];
//Get username
memcpy(username, usercredential,username_len);
char *p_password = usercredential+ username_len +1;
//Get password
memcpy(password, p_password,password_len);
if(strcmp(username,"root")==0)
{
if (strcmp(password,"route66")==0)
{
return true;
}
}else if (strcmp(username,"someuser")==0)
{
if (strcmp(password,"password")==0)
{
return true;
}
}
return false;
}
No check to make sure that the
password length does not exceed the
local buffer size of ‘100’
Password buffer has
length of 100](https://image.slidesharecdn.com/offensivecybersecuritysmashingthestackfinal-150728114644-lva1-app6891/85/Offensive-cyber-security-Smashing-the-stack-with-Python-24-320.jpg)

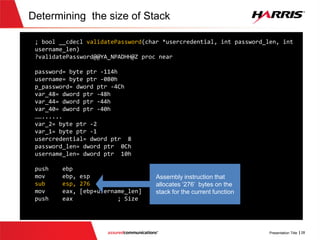
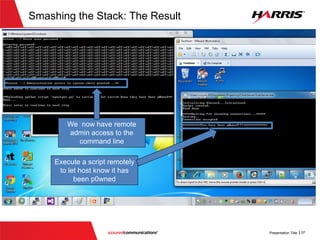
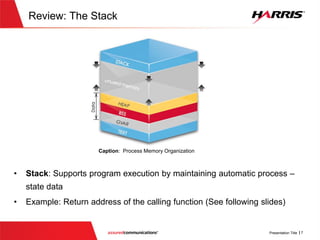
![Determining the size of Stack
v
; bool __cdecl validatePassword(char *usercredential, int password_len, int
username_len)
?validatePassword@@YA_NPADHH@Z proc near
password= byte ptr -114h
username= byte ptr -0B0h
p_password= dword ptr -4Ch
var_48= dword ptr -48h
var_44= dword ptr -44h
var_40= dword ptr -40h
……......
var_2= byte ptr -2
var_1= byte ptr -1
usercredential= dword ptr 8
password_len= dword ptr 0Ch
username_len= dword ptr 10h
push ebp
mov ebp, esp
sub esp, 276
mov eax, [ebp+username_len]
push eax ; Size
Assembly instruction that
allocates ‘276’ bytes on the
stack for the current function](https://image.slidesharecdn.com/offensivecybersecuritysmashingthestackfinal-150728114644-lva1-app6891/85/Offensive-cyber-security-Smashing-the-stack-with-Python-27-320.jpg)
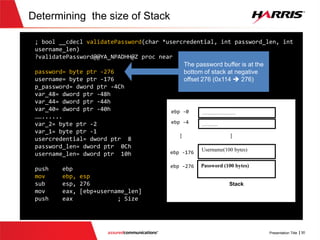
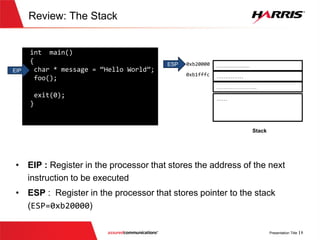
![v
Figure out position of password buffer
; bool __cdecl validatePassword(char *usercredential, int password_len, int
username_len)
?validatePassword@@YA_NPADHH@Z proc near
password= byte ptr -276
username= byte ptr -176
p_password= dword ptr -4Ch
var_48= dword ptr -48h
var_44= dword ptr -44h
var_40= dword ptr -40h
……......
var_2= byte ptr -2
var_1= byte ptr -1
usercredential= dword ptr 8
password_len= dword ptr 0Ch
username_len= dword ptr 10h
push ebp
mov ebp, esp
sub esp, 276
mov eax, [ebp+username_len]
push eax ; Size
The password buffer is at the
bottom of stack at negative
offset 276 (0x114 276)
……………….
………
Password (100 bytes)
ebp -0
Stack
ebp -4
Username(100 bytes)
ebp -176
ebp -276
...
...](https://image.slidesharecdn.com/offensivecybersecuritysmashingthestackfinal-150728114644-lva1-app6891/85/Offensive-cyber-security-Smashing-the-stack-with-Python-29-320.jpg)

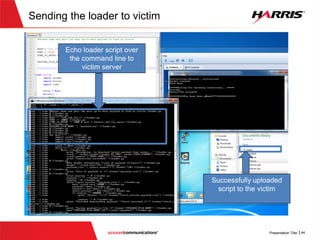
![v
Determining target return address
int main(int argc , char *argv[])
{
10001200 push ebp
.........................................{
printf("Determining if user is rootn");
100014DC push 100022BCh
100014E1 call dword ptr ds:[10002030h]
100014E7 add esp,4
char * username
=strtok(usercredential_buff, DELIMETER);
100014EA push 100022DCh
100014EF lea ecx,[usercredential_buff]
100014F5 push ecx
100014F6 call dword ptr ds:[1000203Ch]
100014FC add esp,8
100014FF mov dword ptr [ebp-7Ch],eax
v
int main(int argc , char *argv[])
{
.........................................
validpassword=validatePassword(……);
if(validpassword)
{
printf("Determining if user rootn");
char * username = strtok(…)
if (strcmp(username,"root")==0)
{
message = "Administrative access to
system shell granted...";
send(new_socket , message ,
strlen(message) , 0);
}
....................
}Jumping to address ‘0x100014EA’
allows us to bypass the if statement
that checks if password is valid
Goal is to bypass
this check](https://image.slidesharecdn.com/offensivecybersecuritysmashingthestackfinal-150728114644-lva1-app6891/85/Offensive-cyber-security-Smashing-the-stack-with-Python-31-320.jpg)