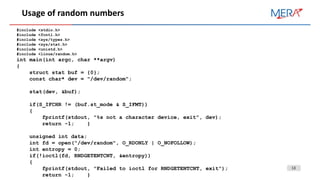
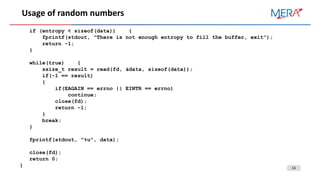
This document discusses secure coding practices related to timing attacks, random number generation, and string security. It provides examples of vulnerabilities in Java timing attacks, OpenSSL and .NET random number generation, and recommendations for using cryptographically secure random number generators and constant time comparisons to mitigate timing attacks.


![3
Timing attack: Java vulnerability
• Site-channel attack, implementation attack
• Attacker analyses a system reaction time for different input parameters and looks for ways to compromise the system
• CVE-2016-6210: OpenSSH uses BLOWFISH as hash for non-existing users and SHA256/SHA512 for existing. It is
exploitable with number of inputs more than 10K.
• Java bug Bug # 6863503 (Jul 2009) in java.security.MessageDigest Java 6.0 Update 15
public static boolean isEqual(byte digesta[], byte digestb[]) {
if (digesta.length != digestb.length)
return false;
for (int i = 0; i < digesta.length; i++) {
if (digesta[i] != digestb[i]) {
return false;
}
}
return true;
}](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-3-320.jpg)

![5
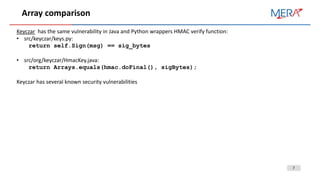
Array comparison
Opportunities And Limits Of Remote Timing Attacks:
• WWW Remote timing difference: 20 µs per 1000 attempts.
• Lan: 100ns per 1000 attempts.
• Side-channel amplification to slow down the website
public static boolean isEqual(byte[] a, byte[] b) {
int result = 0;
result = a.length ^ b.length;
for (int i = 0; i < a.length && I < b.length; i++) {
result |= a[i] ^ b[i];
}
return result == 0;
}
Bug was fixed in Java SE 6 Update 17 (Dec 2009) “SECURITY: MessageDigest.isEqual introduces timing attack
vulnerabilities”](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-5-320.jpg)







![21
Intel Secure Key
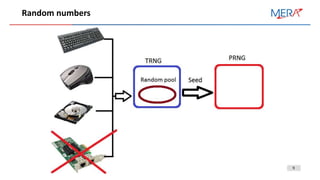
Intel developed it’s own PRNG and starting from Ivy Bridge all CPUs have it.
• RDSEED: Generates seed
• RDRAND: provides pseudo number results
Implemented as AES in AES-CBC-MAC mode.
drivers/char/random.c: extract buf
for (i = 0; i < LONGS(EXTRACT_SIZE); i++)
{
unsigned long v; // arch_get_random is RDRAND.
if (!arch_get_random_long(&v)) break;
hash.l[i] ^= v;
}
Potential vulnerability is when CPU-generated random numbers could reverse existing hash and make it constant
(e.x. 0)
Also applications that use RDRAND directly are vulnerable to secret key that used for AES](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-21-320.jpg)
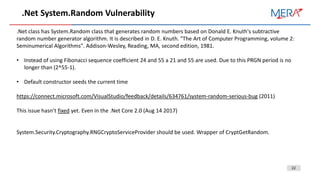
![23
C++ example
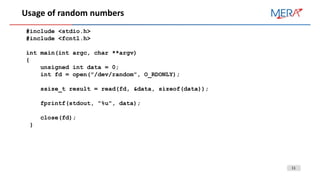
On Linux, /dev/urandom is used
On Windows, RtlGenRandom (not CryptGenRandom to save resources for CryptoAPI) is used
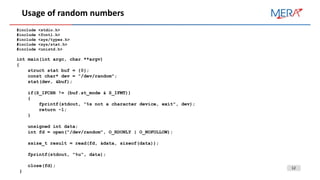
libSodium example:
#include "sodium.h"
int main(int argc, char** argv)
{
unsigned char data[32];
uint32_t rnd;
//Fill array with 32 bytes not null-terminated
randombytes_buf(data, 32);
//Random number between 0 and 9
rnd = randombytes_uniform(10);
}](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-23-320.jpg)
![24
Strings Security
Security problems of usage string in programming languages:
• Store unencrypted data in memory
• Non-obvious memory coping and reallocation
• Object destruction actually doesn’t clear memory data, especially important for memory-managed
languages like Java, C#.
• Strings in String Pool is immutable and every modification create new string
• Common way to work aroud the issues is to use char[]](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-24-320.jpg)
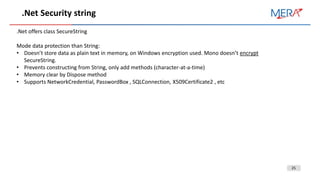
![26
Java Security string
In SWING getPassword() returns char[]/
• Java Cryptography Architecture (JCA) Reference Guide recommends to use char[] for sensitive data
• Secure Coding Guidelines for Java SE recommends the same in other words](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-26-320.jpg)


![29
Strings Security: EFBFBD issue
Some Android applications faced with password entropy issue: entropy seriously reduced:
Before: B7B0F88D603466CF7BF26C24E2B2AA576AAFC5E90C6BD4EECCC576B9D7F1E9C3
After:
EFBFBDEFBFBDEFBFBD603466EFBFBD7BEFBFBD6C24E2B2AA576AEFBFBDEFBFBDEFBFBD0C6BEFBFBDEF
BFBDEFBFBDEFBFBD76EFBFBDEFBFBDEFBFBDEFBFBDEFBFBD
What wrong with this code:
privateString generateRandomPassword() {
byte[] arr = newbyte[42];
newSecureRandom().nextBytes(arr);
return new String(arr);
}](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-29-320.jpg)

![31
Strings Security: EFBFBD issue
How to fix the issue:
• Avoid bytes to String conversion. See “How to Use Password Fields” from “The Java™ Tutorials” for
details
• Use base64 encoding:
• private String generateRandomPassword() {
byte[] arr = newbyte[42];
return Base64.encodeToString(arr, 0);
}](https://image.slidesharecdn.com/securecodingp-180318121746/85/Secure-coding-for-developers-31-320.jpg)


