This document outlines key aspects of pervasive computing including:
1. It discusses the evolution of computing from mainframes to personal computers to the emerging era of pervasive computing.
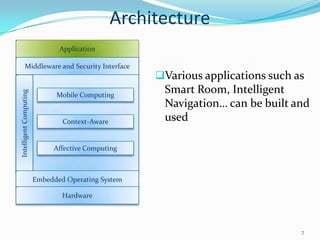
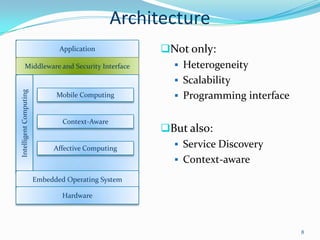
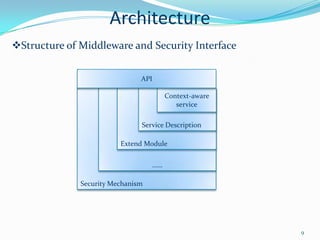
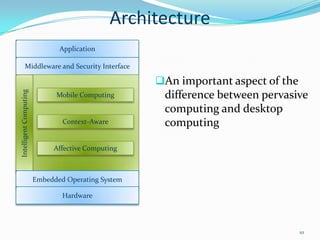
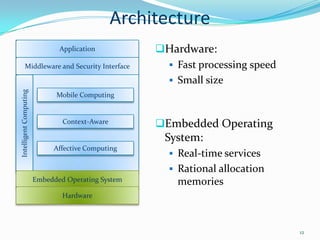
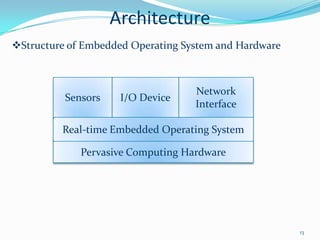
2. It describes the architecture of pervasive computing including applications, middleware, intelligent computing, mobile computing, context-awareness and affective computing components.
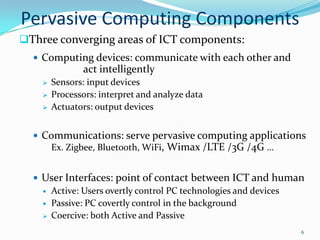
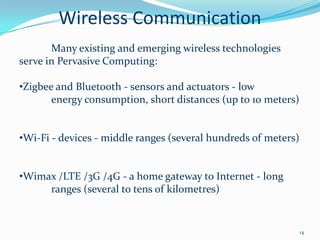
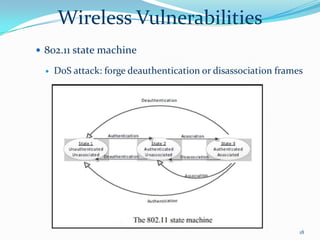
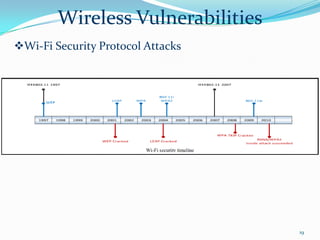
3. It examines wireless communication technologies used in pervasive computing like Zigbee, Bluetooth, WiFi and discusses security issues with vulnerabilities in these wireless systems including denial of service attacks, eavesdropping and message injection.