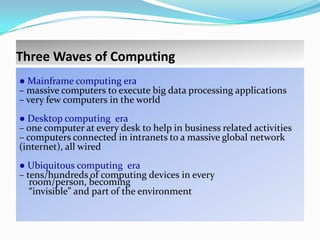
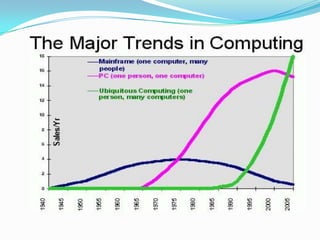
Ubiquitous computing is an advanced computing paradigm where numerous embedded computers seamlessly integrate into everyday environments, enhancing user interaction while remaining largely invisible. Key drivers include advancements in processing, storage, networking, and sensor technology, enabling pervasive and context-aware applications. Despite the challenges of integration and security, ubiquitous computing envisions a future where computational power is omnipresent, improving the quality of life through enhanced technology.