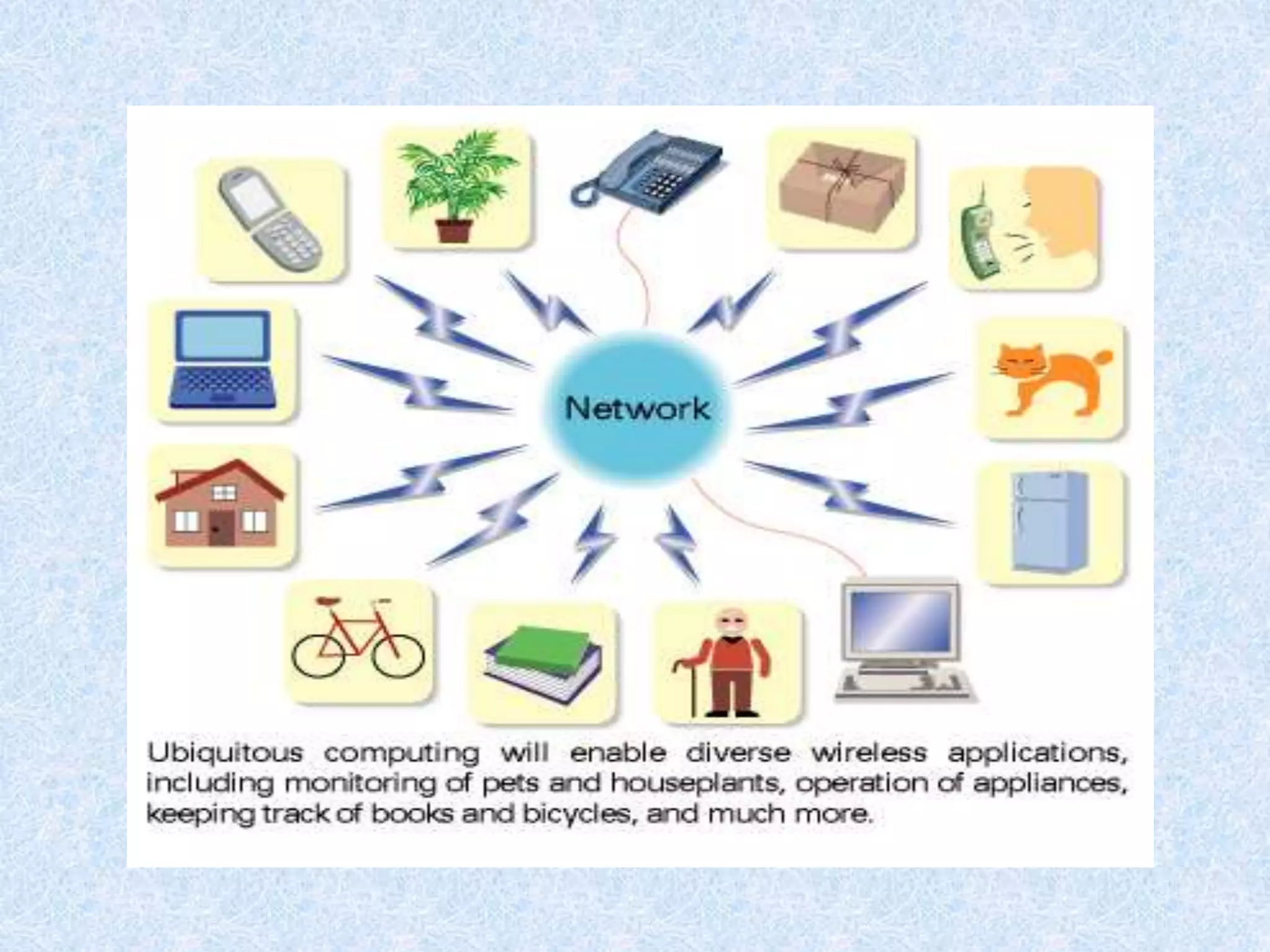
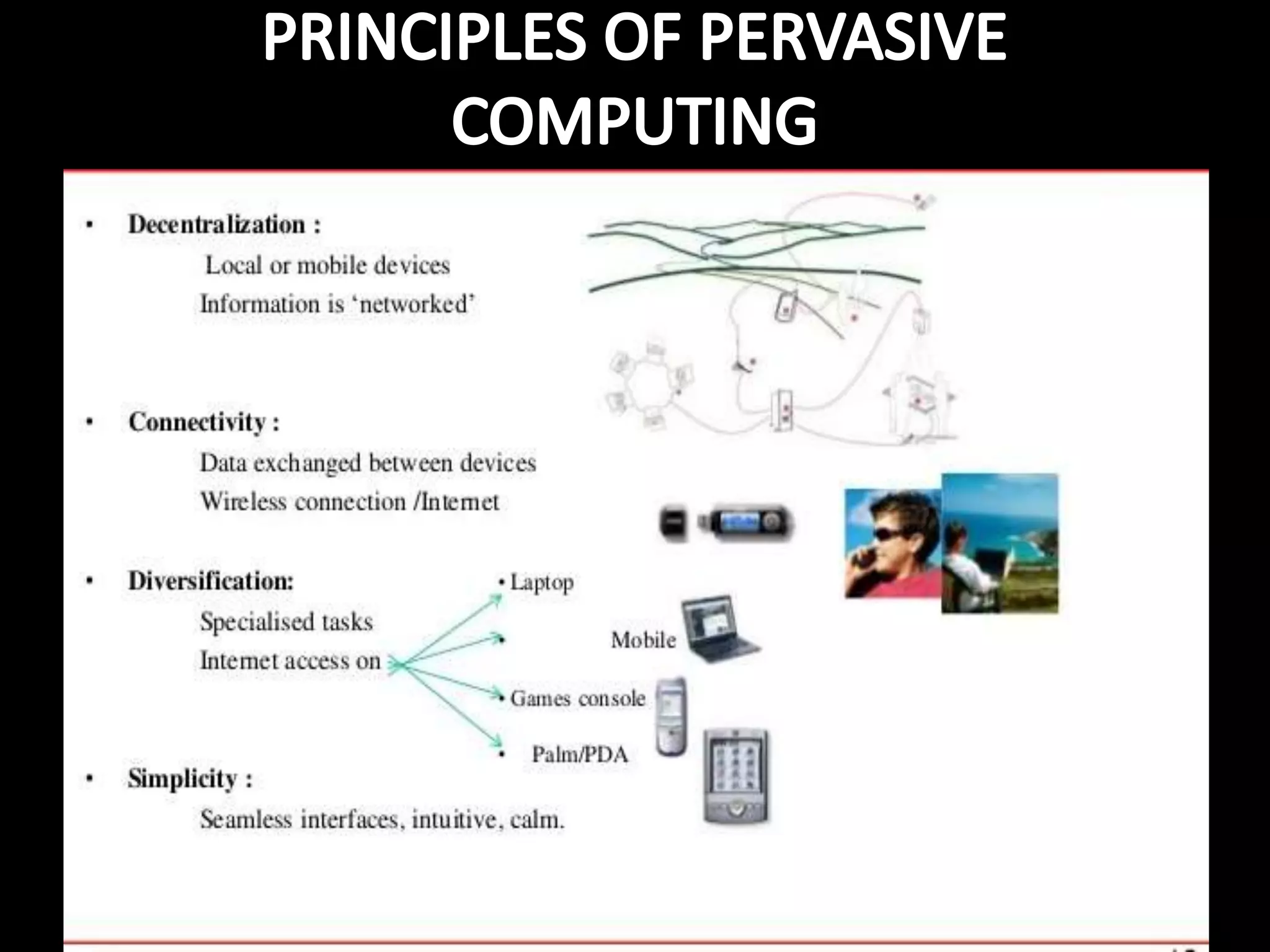
Pervasive/ubiquitous computing refers to embedding microprocessors in everyday objects to communicate information and connect devices. The goal is for connectivity to be unobtrusive and always available. Key aspects include wireless technologies, advanced electronics, and the internet connecting smart products. Challenges include creating seamless integration between technology and users.