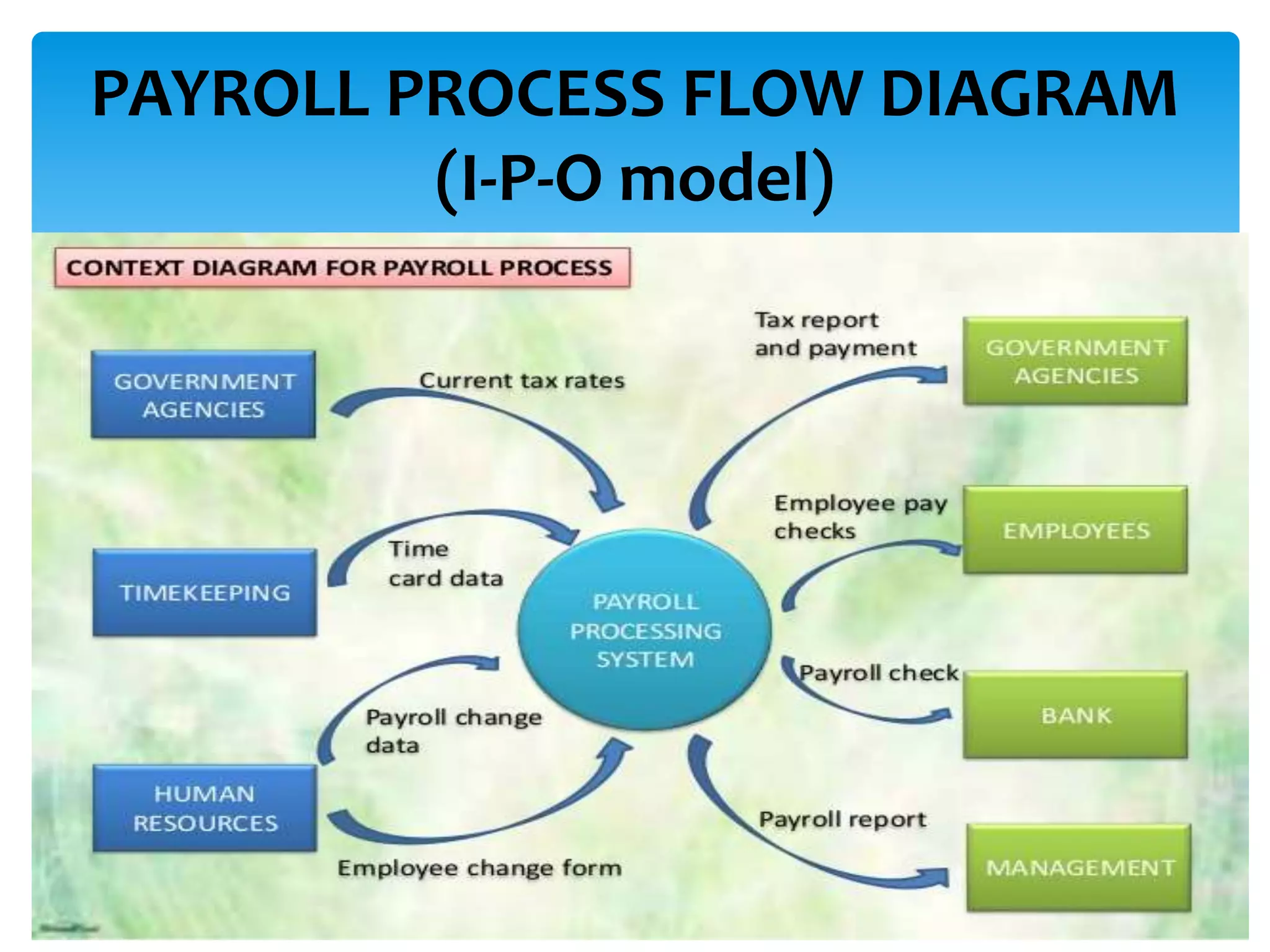
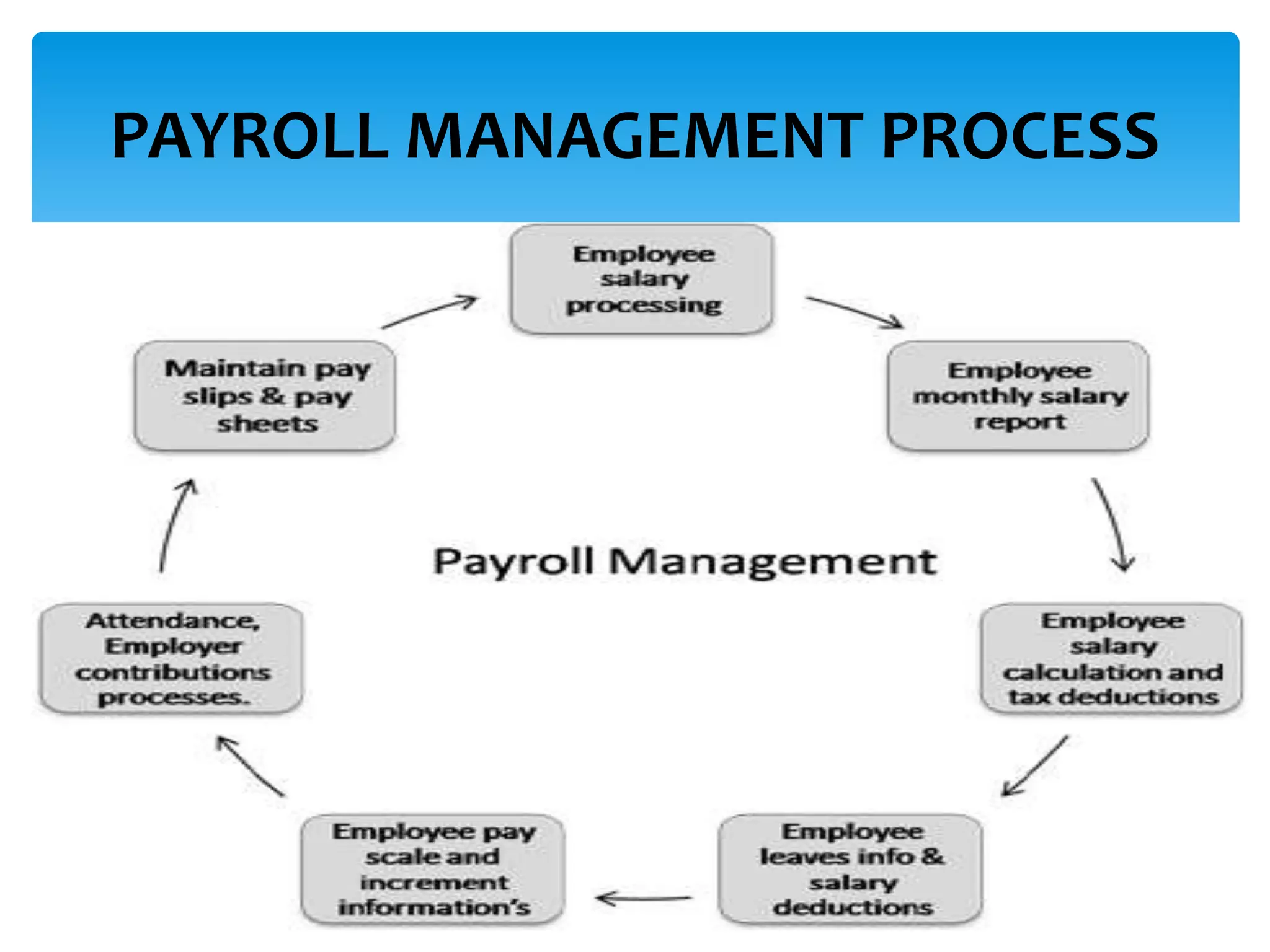
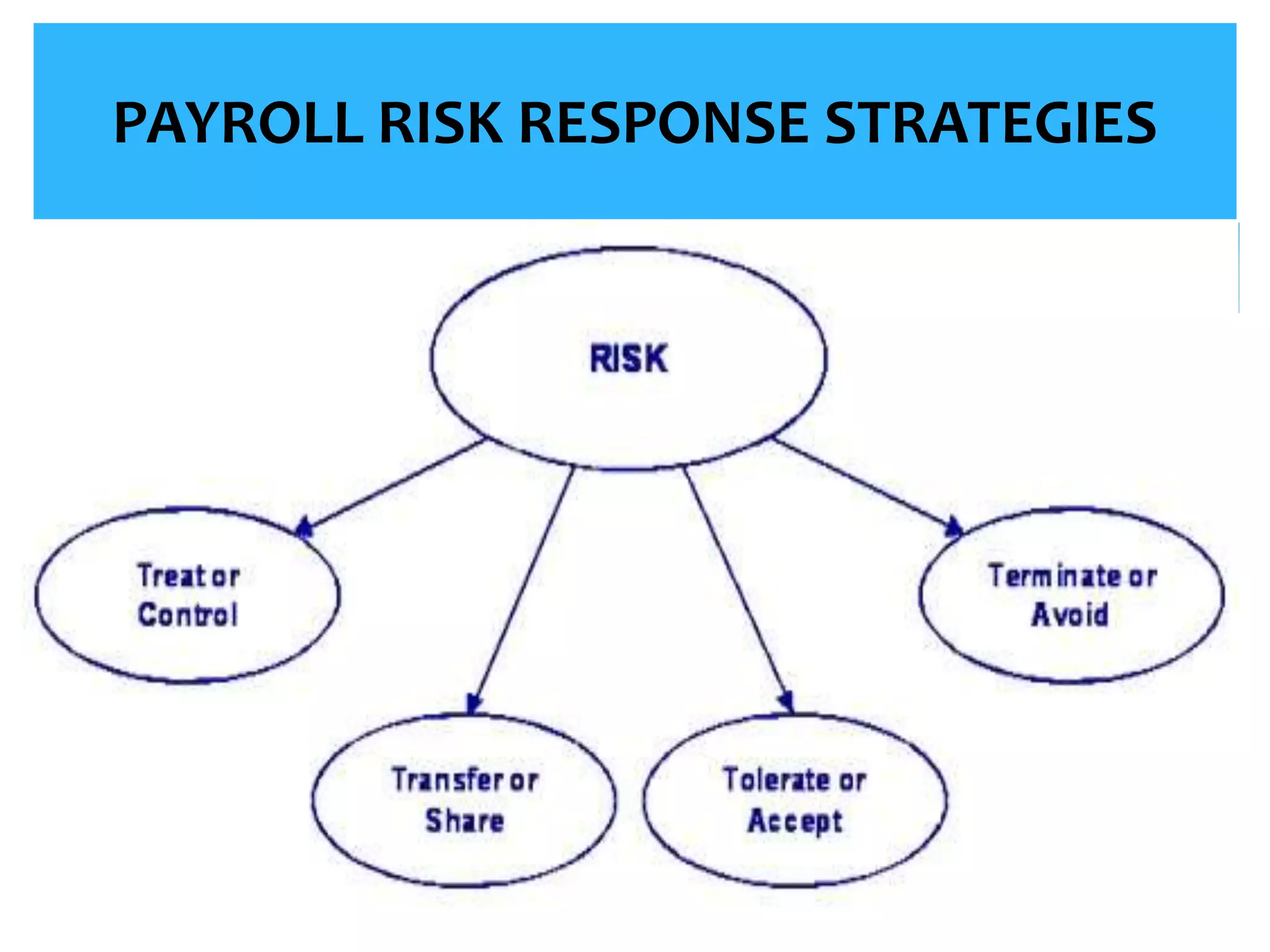
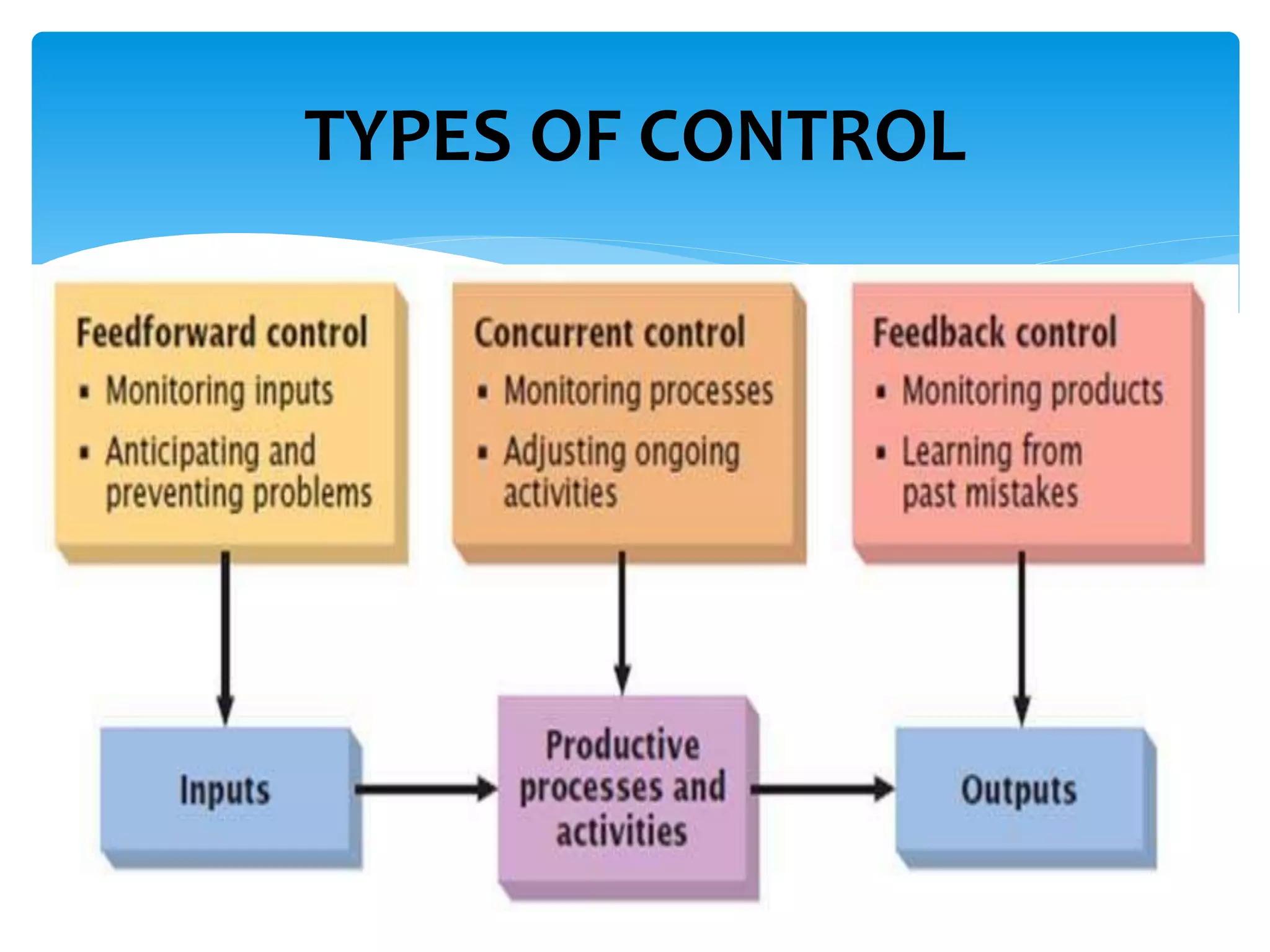
The presentation covered effective payroll controls, risk management, and fraud prevention strategies. It discussed applying the payroll risk management process in 5 steps, implementing internal controls, and analyzing payroll fraud prevention techniques and case studies. Common types of payroll fraud like ghost workers and tips for detection were also reviewed.