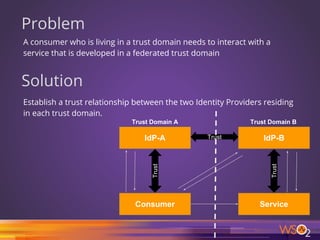
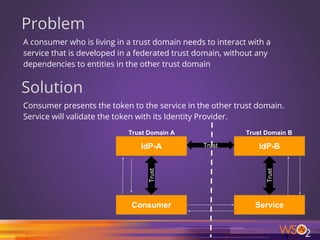
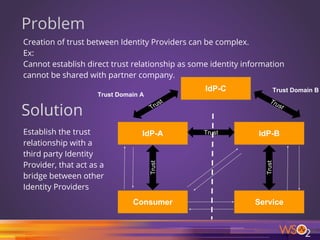
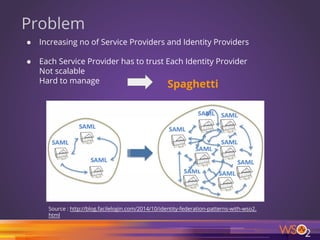
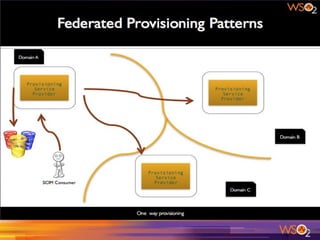
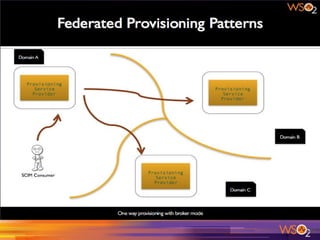
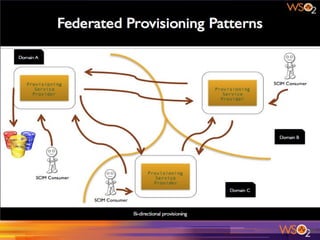
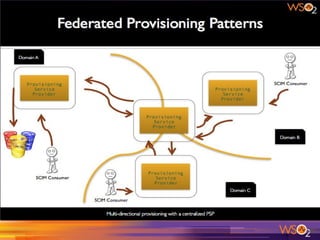
The document discusses various patterns and antipatterns related to identity and access management in enterprise security, with a focus on practical solutions for common problems such as user integration, authentication, and security management. It outlines several strategies, including identity brokers, federated authentication, multi-factor authentication, and secure information exchange methods, detailing their benefits and limitations. Additionally, the document highlights the importance of effective governance and modular design in maintaining secure and scalable identity management systems.



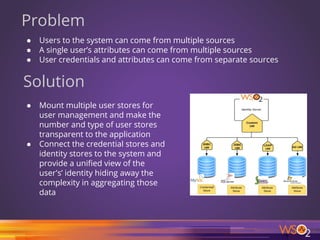

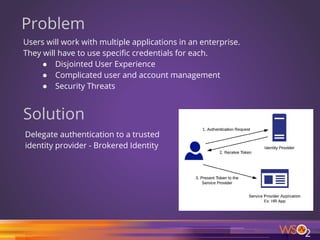


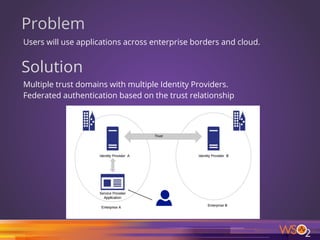































![66
References
[1] https://msdn.microsoft.com/en-us/library/
[2] http://soapatterns.org/
[3] https://medium.facilelogin.com/thirty-solution-patterns-with-the-wso2-identity-server-
16f9fd0c0389#.1f3slrjnt
[4] http://wso2.com/library/blog-post/2014/10/blog-post-identity-anti-patterns-federation-silos-
and-spaghetti-identity/
[5] http://wso2.com/library/webinars/identity-server/
[6] M. Schumacher, E. Fernandez-Buglioni and D. Hybertson, Security Patterns: Integrating
Security and Systems Engineering. 2005.](https://image.slidesharecdn.com/enterprisesecuritypatternsanti-patterns-160601085750/85/Patterns-and-Antipatterns-in-Enterprise-Security-66-320.jpg)
