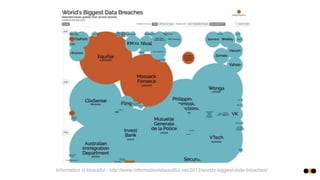
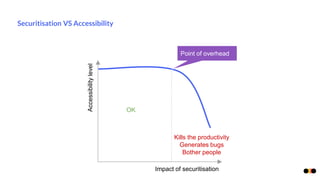
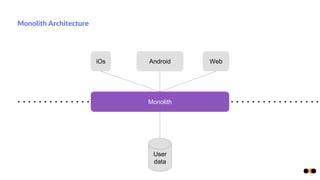
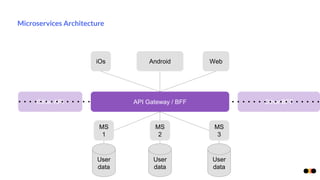
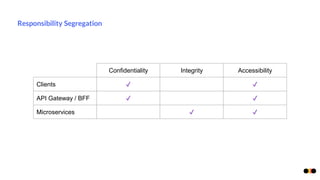
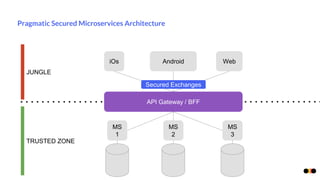
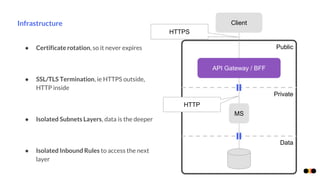
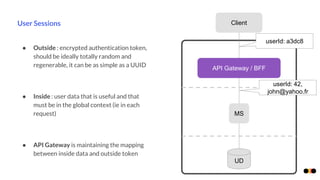
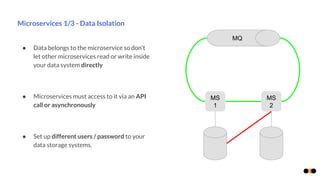
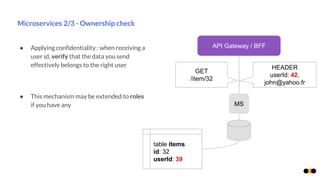
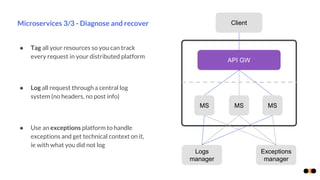
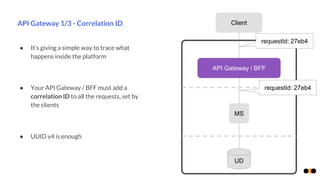
The document discusses security in microservices architectures, emphasizing that security is a continuous process rather than a one-time setup. It outlines essential pillars of IT security including confidentiality, integrity, and availability, while detailing best practices such as data isolation, ownership checks, and traffic pattern detection. The importance of API gateways in maintaining secure communications and preventing threats like DDoS attacks and brute force logins is highlighted.