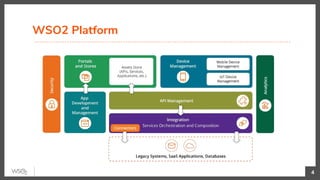
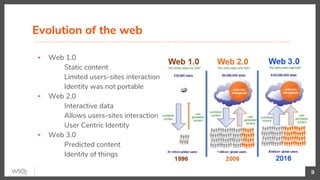
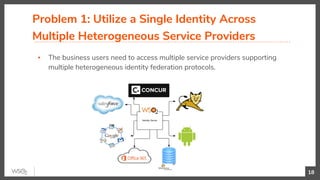
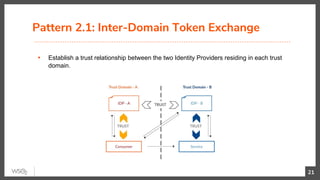
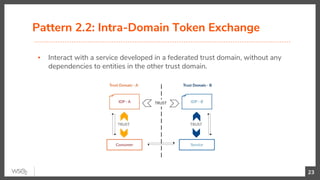
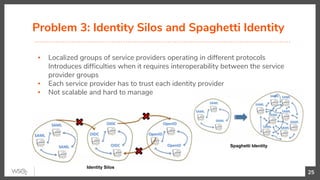
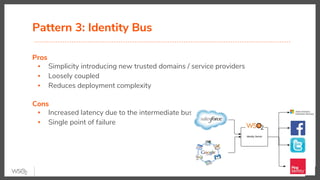
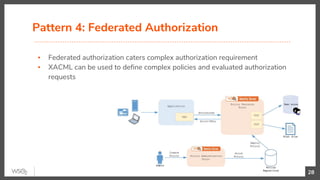
The document discusses identity federation using WSO2 Identity Server, showcasing its capabilities and benefits for managing digital identities across multiple service providers. It explains various patterns and problems associated with identity federation, including single sign-on, inter-domain token exchange, and the challenges posed by identity silos. The text emphasizes the importance of federated authorization and its advantages over traditional mechanisms, aimed at enhancing user experience and security in complex organizational environments.