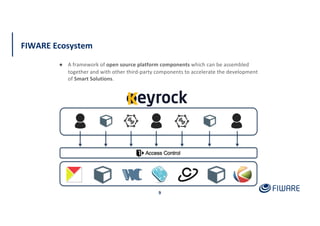
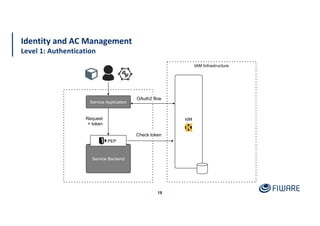
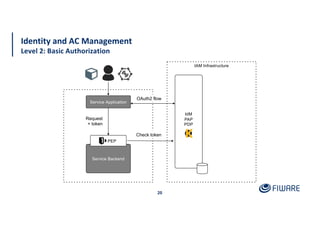
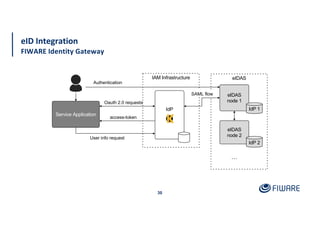
The document presents an overview of the FIWARE Identity Management and Access Control framework, detailing its components such as Keyrock for identity management, Wilma for policy enforcement, and Authzforce for authorization. It outlines the integration with European eIDAS standards for secure electronic interactions and describes the layered access control levels from basic authentication to advanced authorization. Key terminologies related to identity and access management, such as JWT, XACML, OAuth2, and various control models, are also defined.