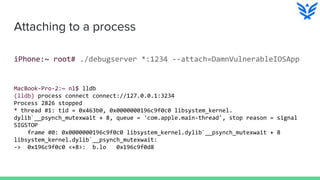
The document outlines techniques for exploring and debugging Objective-C on iOS, emphasizing the process of tracing function calls and manipulating memory for reverse engineering. It details the setup and usage of tools for jailbreaking, memory corruption vulnerabilities, and the internal workings of Objective-C method calls through assembly instructions. Additionally, it provides resources and challenges for further learning and engagement in iOS security research.










![@interface TestObject : NSObject { }
-(void)print;
@end
@implementation TestObject
-(void)print { NSLog(@"Test Object"); }
@end
…
TestObject* obj = [TestObject alloc];
[obj print];](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-14-320.jpg)
![__text:0000000100000DB0 mov rsi, cs:classRef_TestObject
__text:0000000100000DB7 mov rdi, cs:selRef_alloc
__text:0000000100000DBE mov [rbp+var_38], rdi
__text:0000000100000DC2 mov rdi, rsi
__text:0000000100000DC5 mov rsi, [rbp+var_38]
__text:0000000100000DC9 call _objc_msgSend
__text:0000000100000DCE mov [rbp+var_18], rax
__text:0000000100000DD2 mov rax, [rbp+var_18]
__text:0000000100000DD6 mov rsi, cs:selRef_print
__text:0000000100000DDD mov rdi, rax
__text:0000000100000DE0 call _objc_msgSend](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-15-320.jpg)
![[obj print];
objc_msgSend(obj, “print”);
-[TestObject print](obj, “print”);
id objc_msgSend(id self, SEL op, ...)
void __cdecl -[TestObject print]
(struct TestObject *self, SEL)](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-16-320.jpg)



![Step 3 - Copy bytes from objc_msgSend
*t_func = *(jump_page());
// save first 4 32bit instructions
// original -> trampoline
instruction_t* orig_preamble = (instruction_t*)o_func;
for(int i = 0; i < 4; i++) {
t_func->inst [i] = orig_preamble[i];
t_func->backup[i] = orig_preamble[i]; }](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-21-320.jpg)

![Step 3 - Copy bytes from objc_msgSend
__text:18DBB41C0 EXPORT _objc_msgSend
__text:18DBB41C0 _objc_msgSend
__text:18DBB41C0 CMP X0, #0
__text:18DBB41C4 B.LE loc_18DBB4230
__text:18DBB41C8 loc_18DBB41C8
__text:18DBB41C8 LDR X13, [X0]
__text:18DBB41CC AND X9, X13, #0x1FFFFFFF8](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-24-320.jpg)
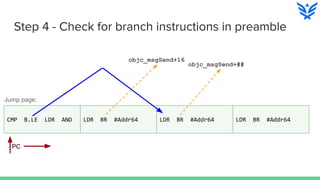
![Step 4 - Check for branch instructions in preamble
(lldb) x/10i 0x0000000104ef4000 ; Jump page
0x104ef4000: 0xf100001f cmp x0, #0
0x104ef4004: 0x540000ed b.le 0x104ef4020
0x104ef4008: 0xf940000d ldr x13, [x0]
0x104ef400c: 0x927d75a9 and x9, x13, #0x1fffffff8
; Jump patch 1
0x104ef4010: 0x58000050 ldr x16, #8
0x104ef4014: 0xd61f0200 br x16
0x104ef4018: 0x964efbd0 bl 0xfe2b2f58
0x104ef401c: 0x00000001 .long 0x00000001 ; unknown opcode
; Jump patch 2
0x104ef4020: 0x58000050 ldr x16, #8
0x104ef4024: 0xd61f0200 br x16](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-26-320.jpg)
![Step 4 - Working with instructions
typedef struct {
uint32_t offset : 26;
uint32_t inst_num : 6;
} inst_b;
…
instruction_t inst = t_func->inst[i];
inst_b* i_b = (inst_b*)&inst;
inst_b_cond* i_b_cond = (inst_b_cond*)&inst;
if(i_b->inst_num == 0x5) {
// unconditional branch](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-27-320.jpg)
![Step 5 - Modify objc_msgSend preamble
Think back to d_jump_patch
(lldb) x/10i 0x1964efbc0 ; objc_msgSend
-> 0x1964efbc0: 0x58000050 ldr x16, #8 ; <+8>
0x1964efbc4: 0xd61f0200 br x16
0x1964efbc8: 0x04eeb730 .long 0x04eeb730 ; unknown opcode
0x1964efbcc: 0x00000001 .long 0x00000001 ; unknown opcode
0x1964efbd0: 0xa9412d2a ldp x10, x11, [x9, #16]
0x1964efbd4: 0x0a0b002c and w12, w1, w11
0x1964efbd8: 0x8b0c114c add x12, x10, x12, lsl #4](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-28-320.jpg)
![Step 5 - Jump patch destination
__attribute__((naked)) id objc_msgSend_trace(id self, SEL op) { __asm__ __volatile__ (
"stp fp, lr, [sp, #-16]!;n"
"mov fp, sp;n"
"sub sp, sp, #(10*8 + 8*16);n"
"stp q0, q1, [sp, #(0*16)];n"
...
"stp x0, x1, [sp, #(8*16+0*8)];n"
..
"BL _hook_callback64_pre;n"
"mov x9, x0;n"
// Restore all the parameter registers to the initial state.
"ldp q0, q1, [sp, #(0*16)];n"
...
"ldp x0, x1, [sp, #(8*16+0*8)];n"
// Restore the stack pointer, frame pointer and link register
"mov sp, fp;n"
"ldp fp, lr, [sp], #16;n"
"BR x9;n" // call the original ); }](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-29-320.jpg)
![The end game!
void* hook_callback64_pre(id self, SEL op, void* a1, … ) {
// get the important bits: class, method
char* classname = (char*) object_getClassName( self );
char* opname = (char*) op;
// print some useful info.
fprintf(output, "%016x: [%s %s (", pthread_self(), classname, (char*)opname);
int printParam = 0;
for(int i = 0; i < namelen; i++) {
if(opname[i] == ':') {
fprintf(output, "%p ", getParam(printParam, a1, a2, a3, a4, a5));
}
}
return original_msgSend;
}](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-32-320.jpg)
![Done! Let’s execute.
On the command line:
iPhone:~ root# DYLD_INSERT_LIBRARIES=libobjc_trace.dylib /Applications/Maps.app/Maps
objc_msgSend function substrated from 0x197967bc0 to 0x10065b730, trampoline
0x100718000
000000009c158310: [NSStringROMKeySet_Embedded alloc ()]
000000009c158310: [NSSharedKeySet initialize ()]
000000009c158310: [NSStringROMKeySet_Embedded initialize ()]
000000009c158310: [NSStringROMKeySet_Embedded init ()]
000000009c158310: [NSStringROMKeySet_Embedded initWithKeys:count: (0x0 0x0 )]
000000009c158310: [NSStringROMKeySet_Embedded setSelect: (0x1 )]
000000009c158310: [NSStringROMKeySet_Embedded setC: (0x1 )]
000000009c158310: [NSStringROMKeySet_Embedded setM: (0xf6a )]
000000009c158310: [NSStringROMKeySet_Embedded setFactor: (0x7b5 )]](https://image.slidesharecdn.com/nyu-hacknightapril62016-160415031709/85/NYU-hacknight-april-6-2016-33-320.jpg)