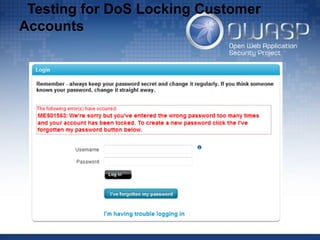
This document provides an introduction to the Open Web Application Security Project (OWASP) and web application security testing. It discusses what OWASP is, why it is needed, and how individuals can get involved. The document then outlines common web application security testing techniques such as information gathering, configuration management testing, authentication testing, and denial of service testing. It provides examples of how to use open source tools to conduct these tests and find vulnerabilities in web applications.













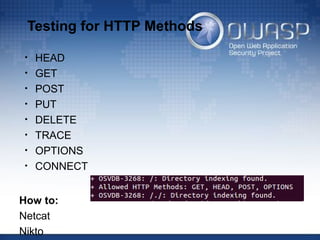










![Testing for SQL Wildcard Attacks
SELECT * FROM Article WHERE Content LIKE '%foo%'
SELECT TOP 10 * FROM Article WHERE Content LIKE
'%_[^!_%/%a?F%_D)_(F%)_%([)({}%){()}£$&N%_)$*£()
$*R"_)][%](%[x])%a][$*"£$-9]_%'](https://image.slidesharecdn.com/owasptalk-150413035418-conversion-gate01/85/Introduction-to-OWASP-Web-Application-Security-34-320.jpg)