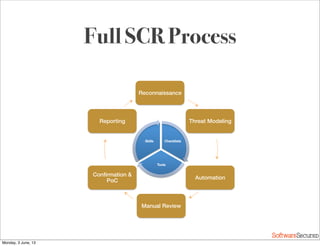
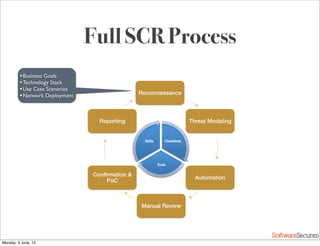
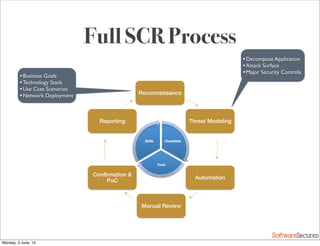
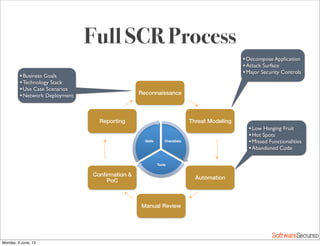
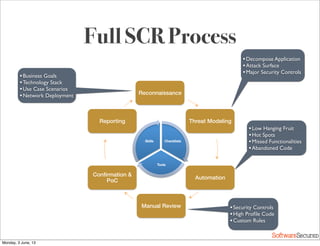
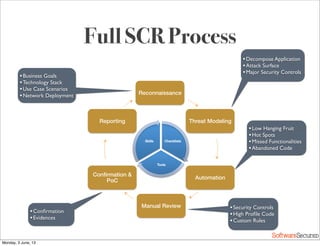
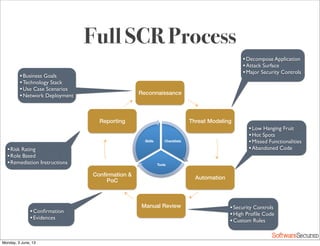
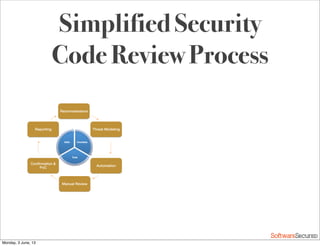
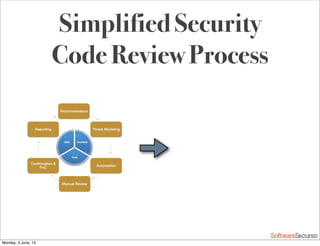
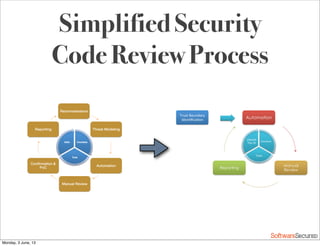
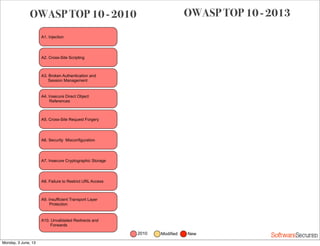
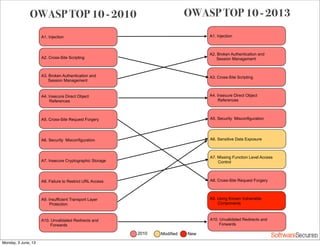
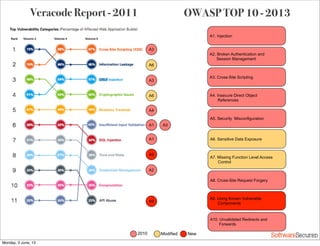
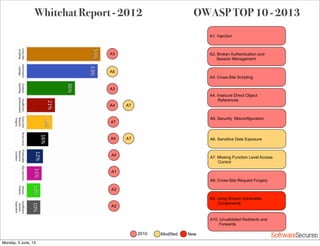
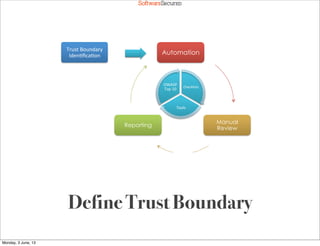
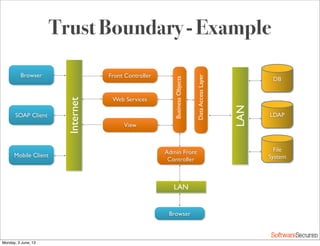
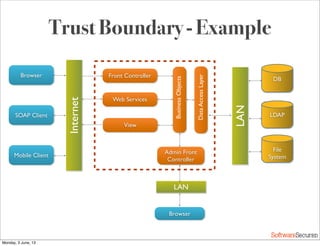
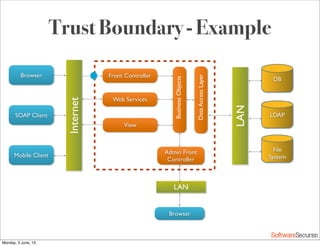
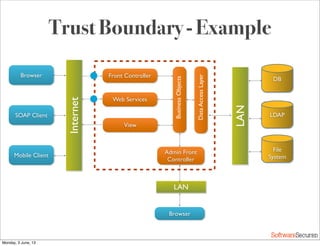
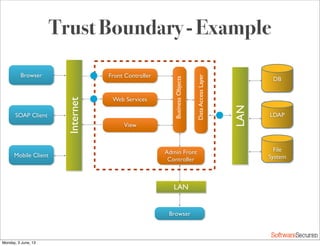
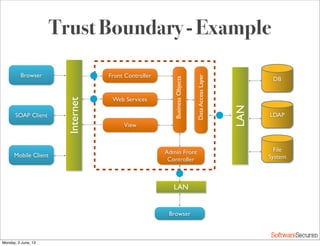
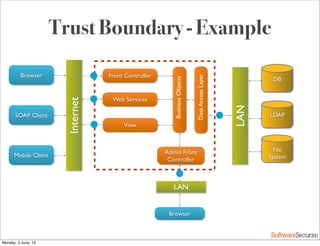
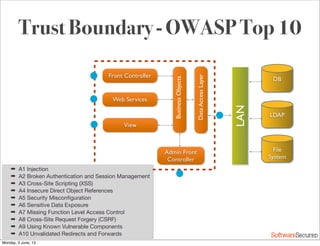
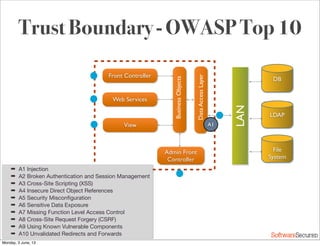
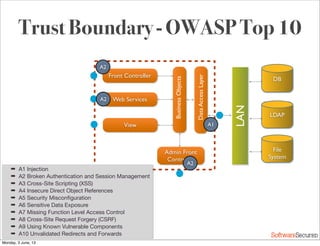
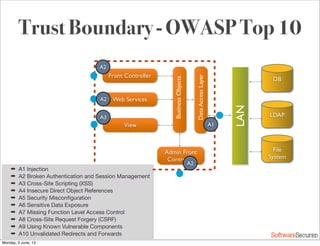
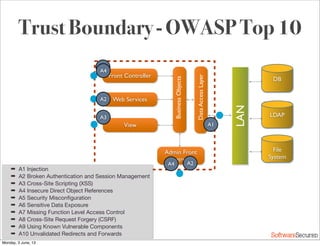
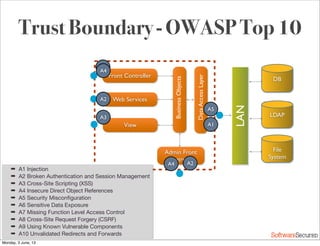
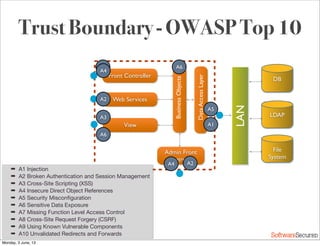
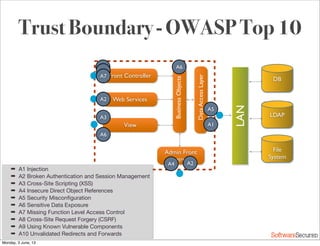
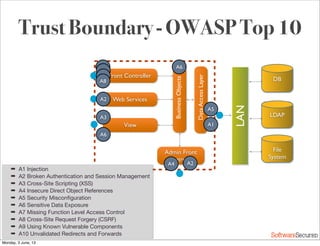
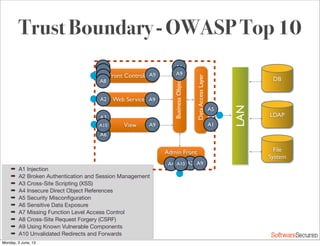
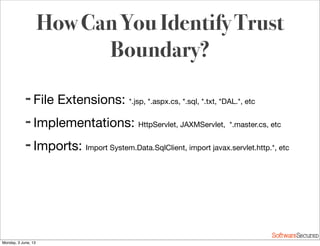
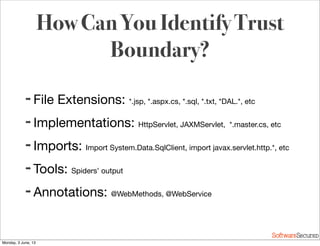
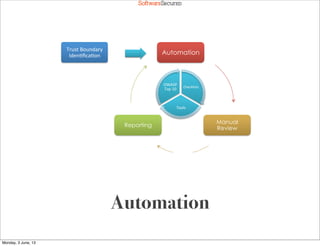
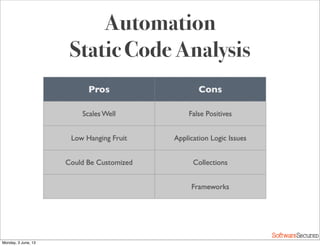
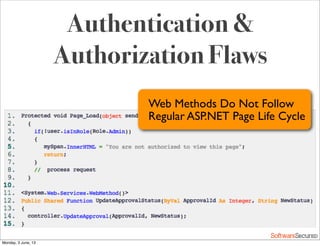
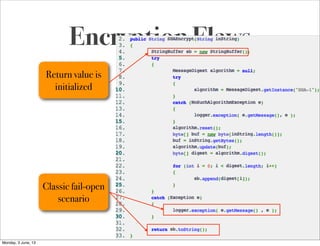
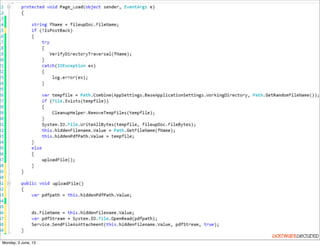
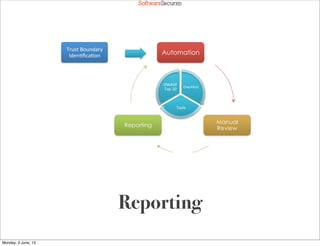
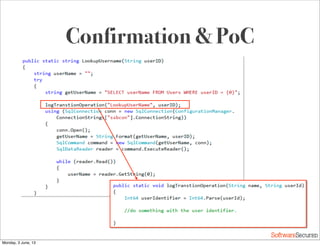
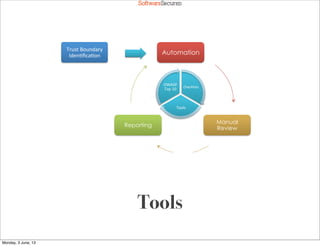
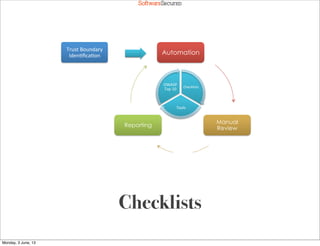
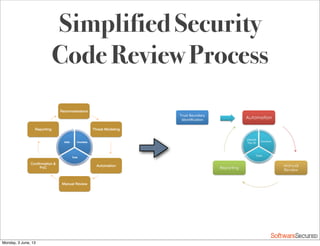
This document summarizes a presentation about simplifying secure code reviews. It discusses defining an effective security code review process, including reconnaissance, threat modeling, automation, manual review, confirmation, and reporting. It also discusses using the OWASP Top 10 list to focus code reviews, and defining trust boundaries to identify areas of code to review for specific vulnerabilities. The goal is to introduce a simplified process that can help development teams integrate security code reviews into their workflow.