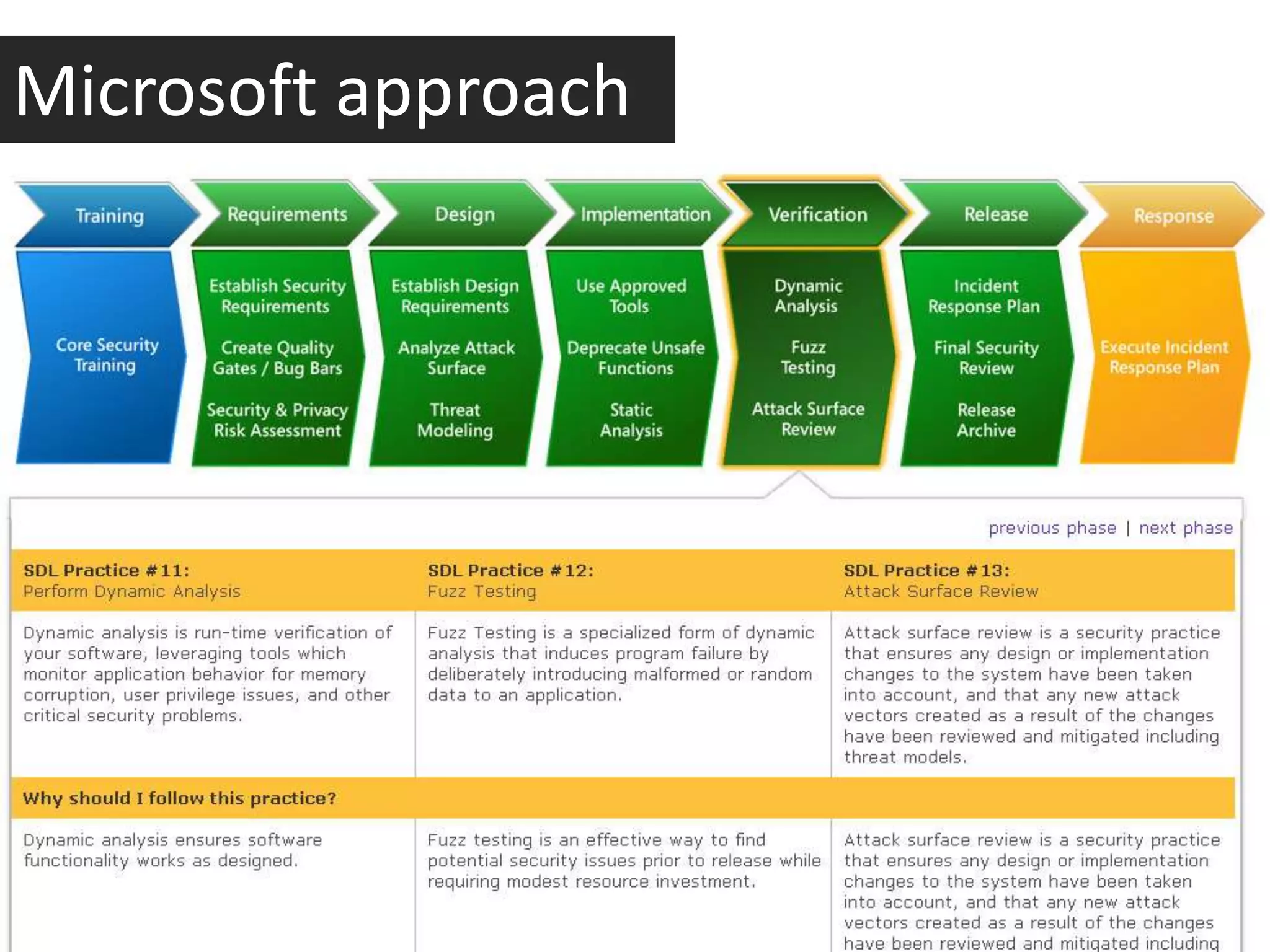
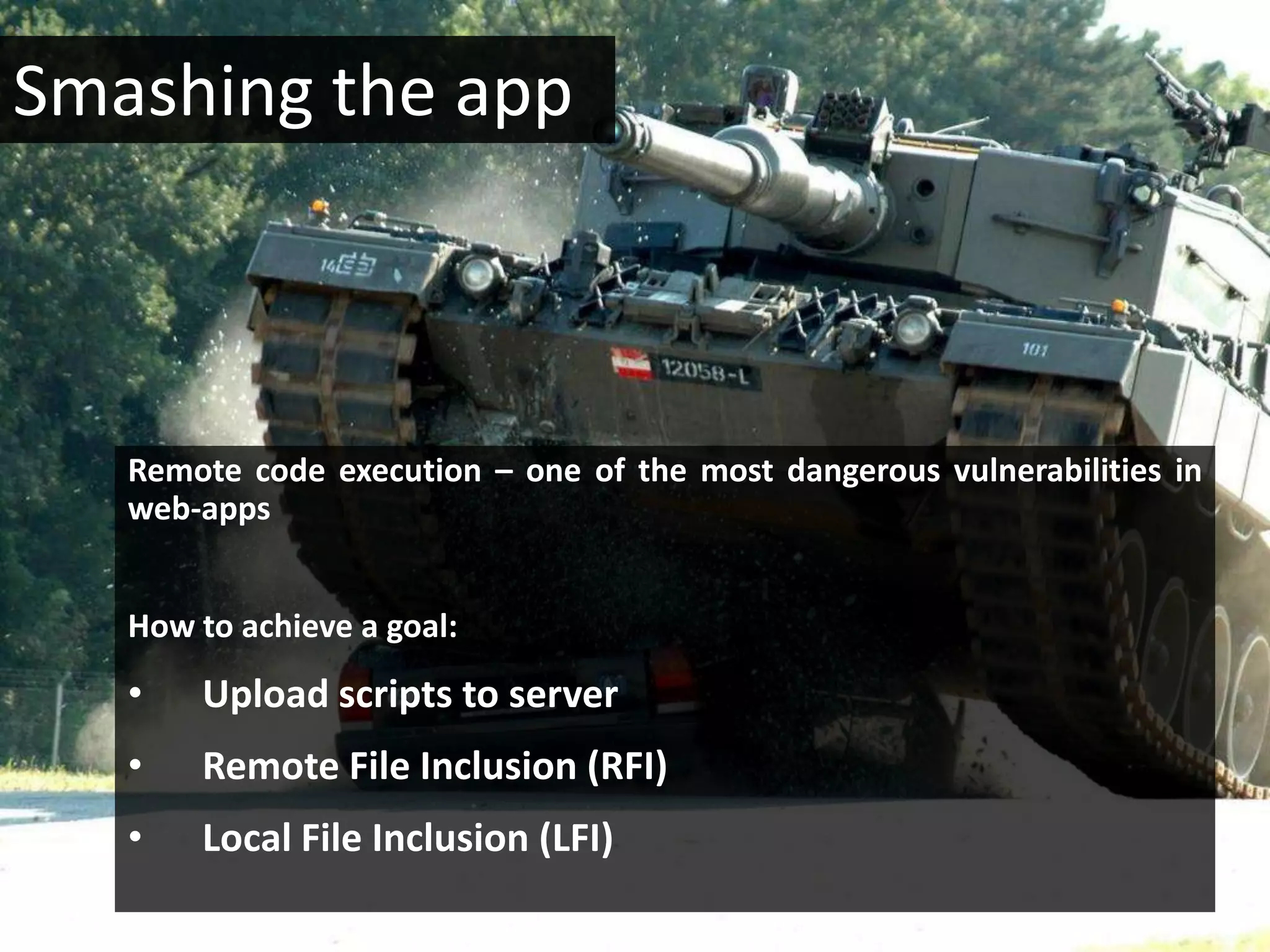
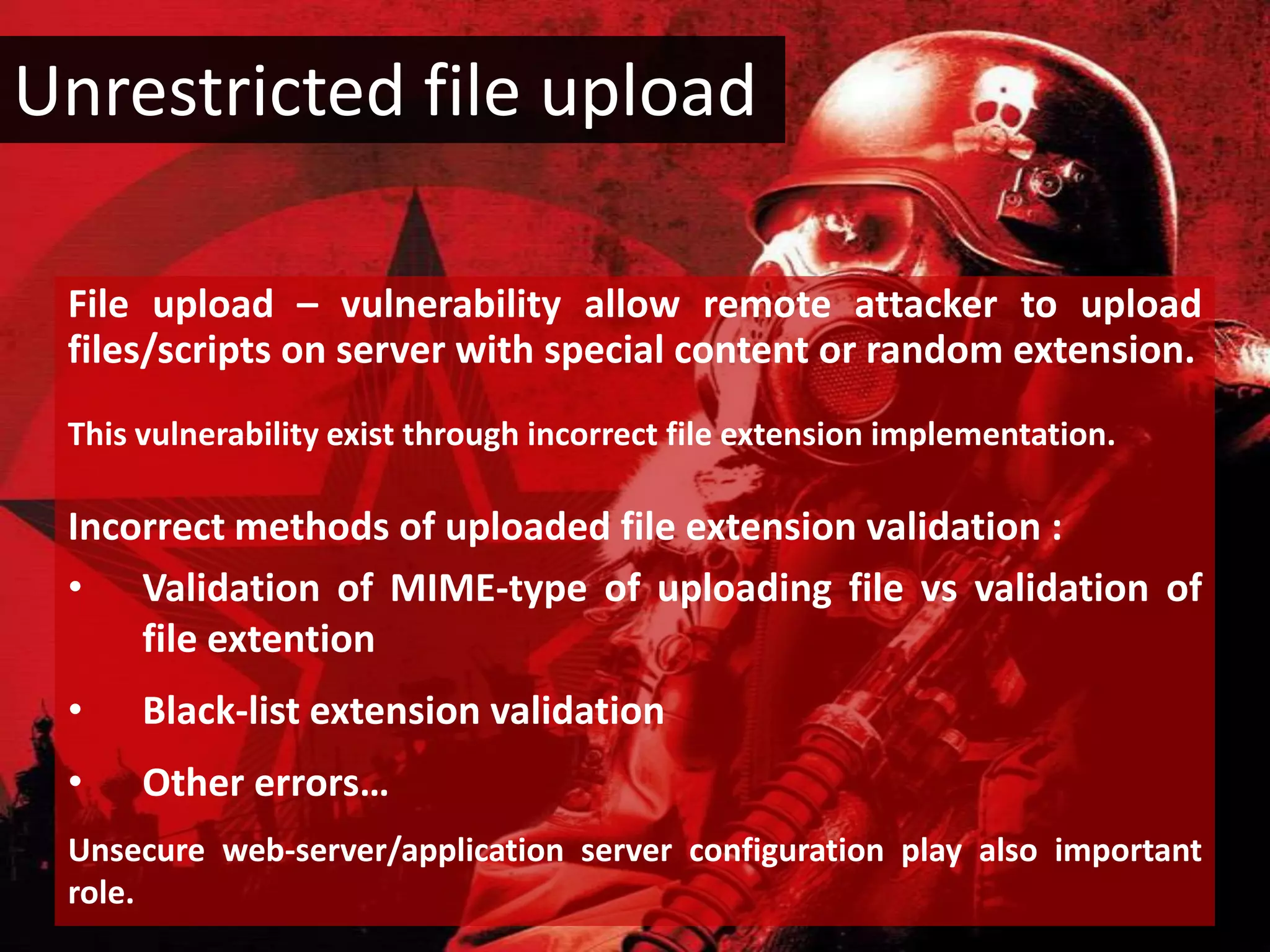
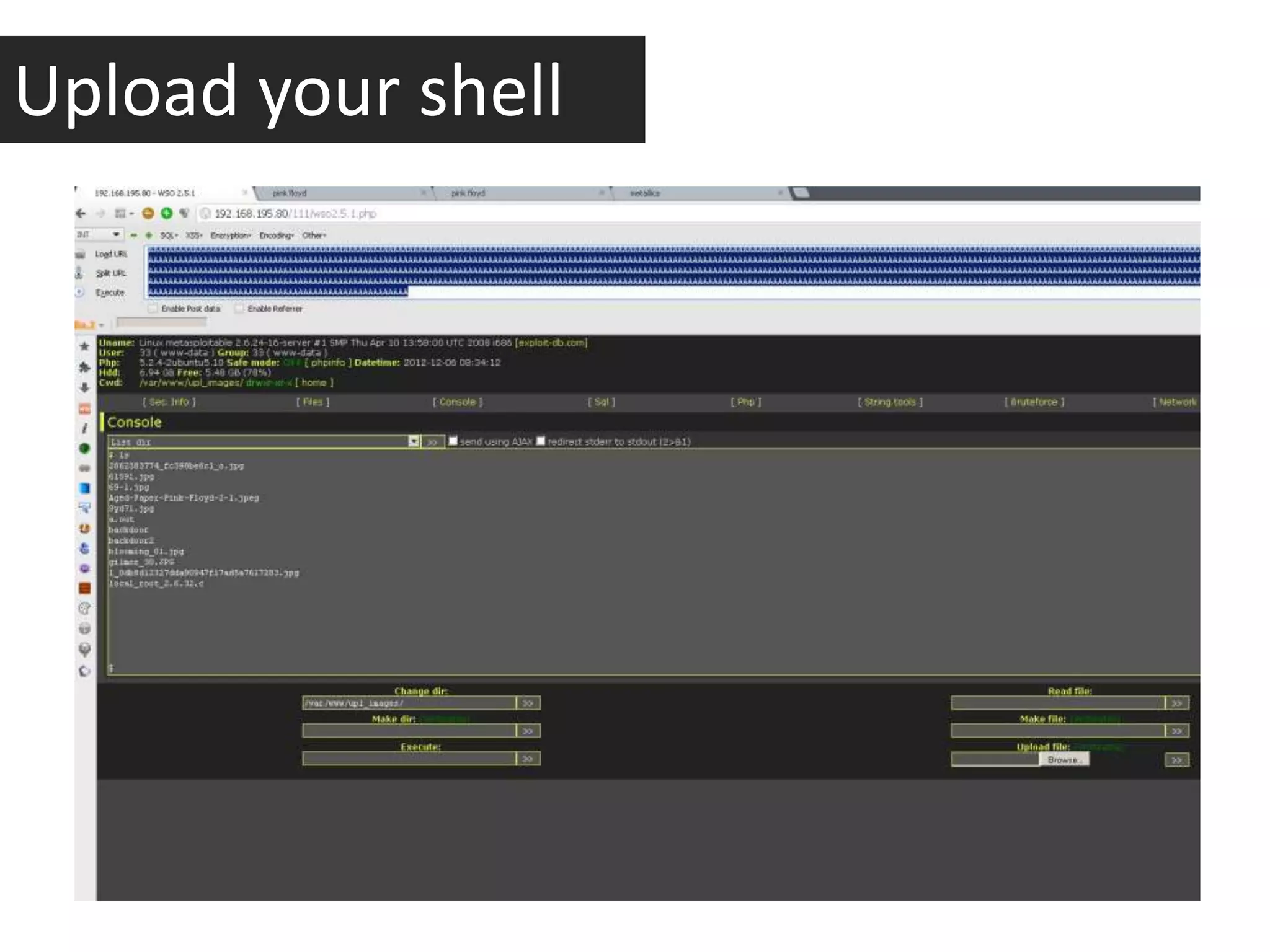
This document discusses whether application security is more of a science or a quality assurance process. It argues that security and quality assurance teams should work together, as a collaborative approach is more powerful. Various security tools and techniques are demonstrated, such as exploiting file upload vulnerabilities, local file inclusion, and directory traversal. The document encourages becoming a security analyst by using OWASP resources, doing research, and participating in the security community.











![Changing MIME type
Validation sample:
<?php
$imageTypes = array("image/gif", "image/jpg", "image/png");
if(isset($_FILES["image"])) {
if(!in_array($_FILES["image"]["type"], $imageTypes)) {
die("Hacking Attempt!"); }
copy($_FILES["image"]["tmp_name"], "images/{$_FILES["image"]["name"]}");
} ?>
Problem: It’s easy to change type of file – as it’s setting by
browser in HTTP-request. And all variables that are set by
browser – can be easily changed by user.](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-18-2048.jpg)
![Content Black list:
validation Wrong way
<?php if(isset($_FILES["image"])) {
if(preg_match('#.((php)|(php3)|(
php4)|(php5))$#i',$_FILES["image
"]["name"])
){
die("Hacking Attempt!");
}
copy($_FILES["image"]["tmp_nam
e"], "images/{$_FILES["image"]["n
ame"]}"); } ?>](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-19-2048.jpg)
![Regular expressions
<?php
if(isset($_FILES["image"])) {
if(preg_match('#.jpg#i', $_FILES["image"]["name"])) {
copy($_FILES["image"]["tmp_name"], "images/{$_FILES["image"]["name"]}
");
} } ?>
In this sample name of uploaded file is checking for
string .jpg. But regular expression is working as control
symbol $ that indicate EOL is missed,.
As a result file shell.jpg.php will be successes fully
uploaded.](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-20-2048.jpg)
![Right way
<?php
if(isset($_FILES["image"])) {
if(preg_match('#^[a-z0-9-
_]+.((jpg)|(png)|(bmp))$#i', $_FILES["image"]["name"])
){
move_uploaded_file($_FILES["image"]["tmp_name"], "ima
ges/{$_FILES["image"]["name"]}");
} }
?> White list
validation](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-21-2048.jpg)

![Directory
Traversal
Filtration can prevent Directory Traversal.
Very often developers apply Filtration of ../ :
<?php include(str_replace("../", "", $_GET["page"]).".inc"); ?>
../../../etc/passwd --> Filtration --> etc/passwd --> fail
But such filtration is not enough – it’s not recursive:
..././..././..././etc/passwd --> Filtration --> ../../../etc/passwd --> profit ](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-23-2048.jpg)
![Secure Validation
Secure Validation – validation of filename for service
symbols
if(preg_match('#[^a-z0-9-_]#i', $page)) {
die("Hacking Attempt!");
}
include("{$page}.inc");
In this sample if we will try to add file with symbols
other than A-Z, a-z, 0-9 and symbol «-» & «_» execution
of PHP-script will be interrupted.](https://image.slidesharecdn.com/securityhole5applicationsecurity-scienceorqualityassurance-121206092958-phpapp02/75/Security-hole-5-application-security-science-or-quality-assurance-24-2048.jpg)