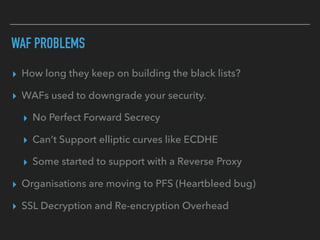
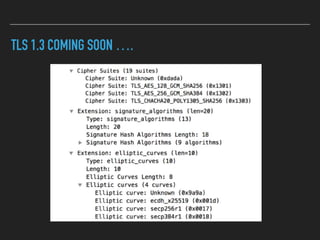
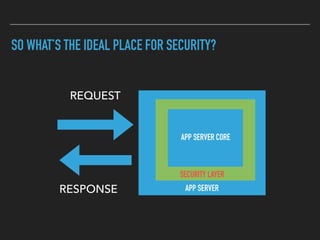
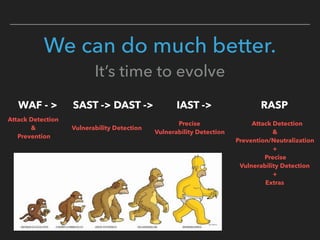
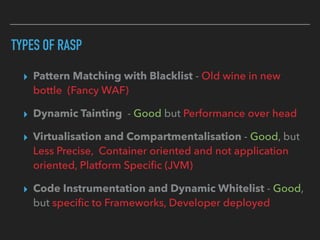
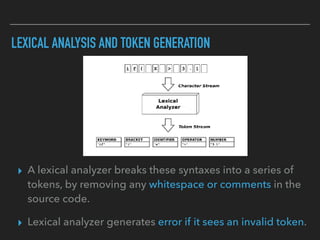
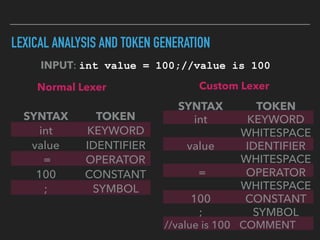
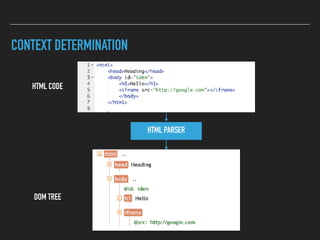
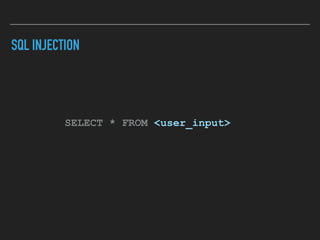
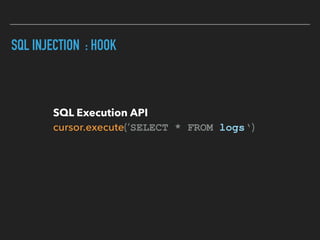
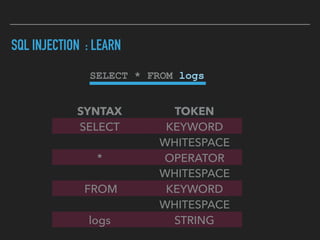
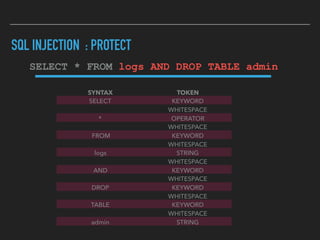
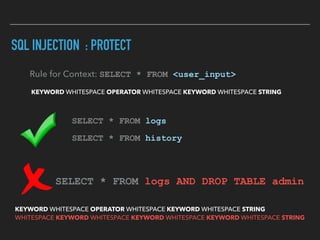
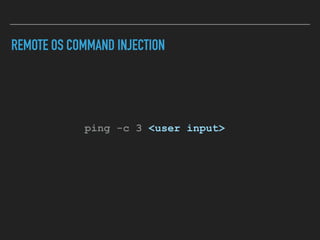
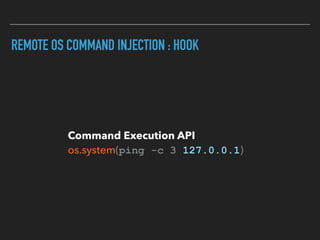
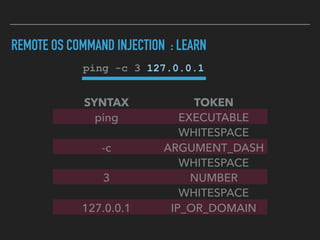
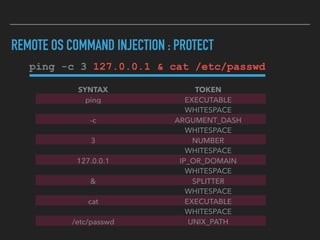
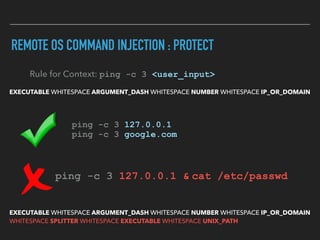
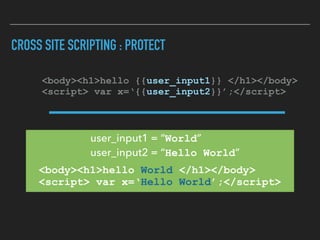
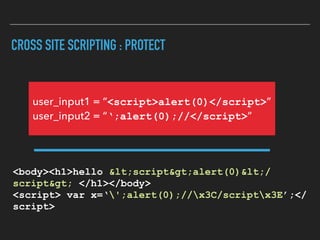
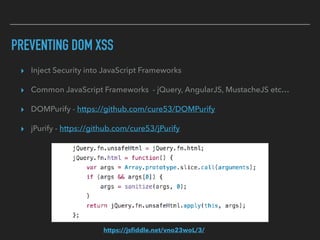
Ajin Abraham discusses the importance of integrating security into web applications through Runtime Application Self-Defense (RASP) and highlights issues with existing Web Application Firewalls (WAFs). The presentation covers the challenges faced in secure coding, vulnerabilities introduced by frameworks, and the benefits of RASP, including improved detection and prevention of attacks without significant code modifications. Abraham emphasizes that the future of web application security lies in proactive, context-aware solutions rather than traditional blacklist-based methods.