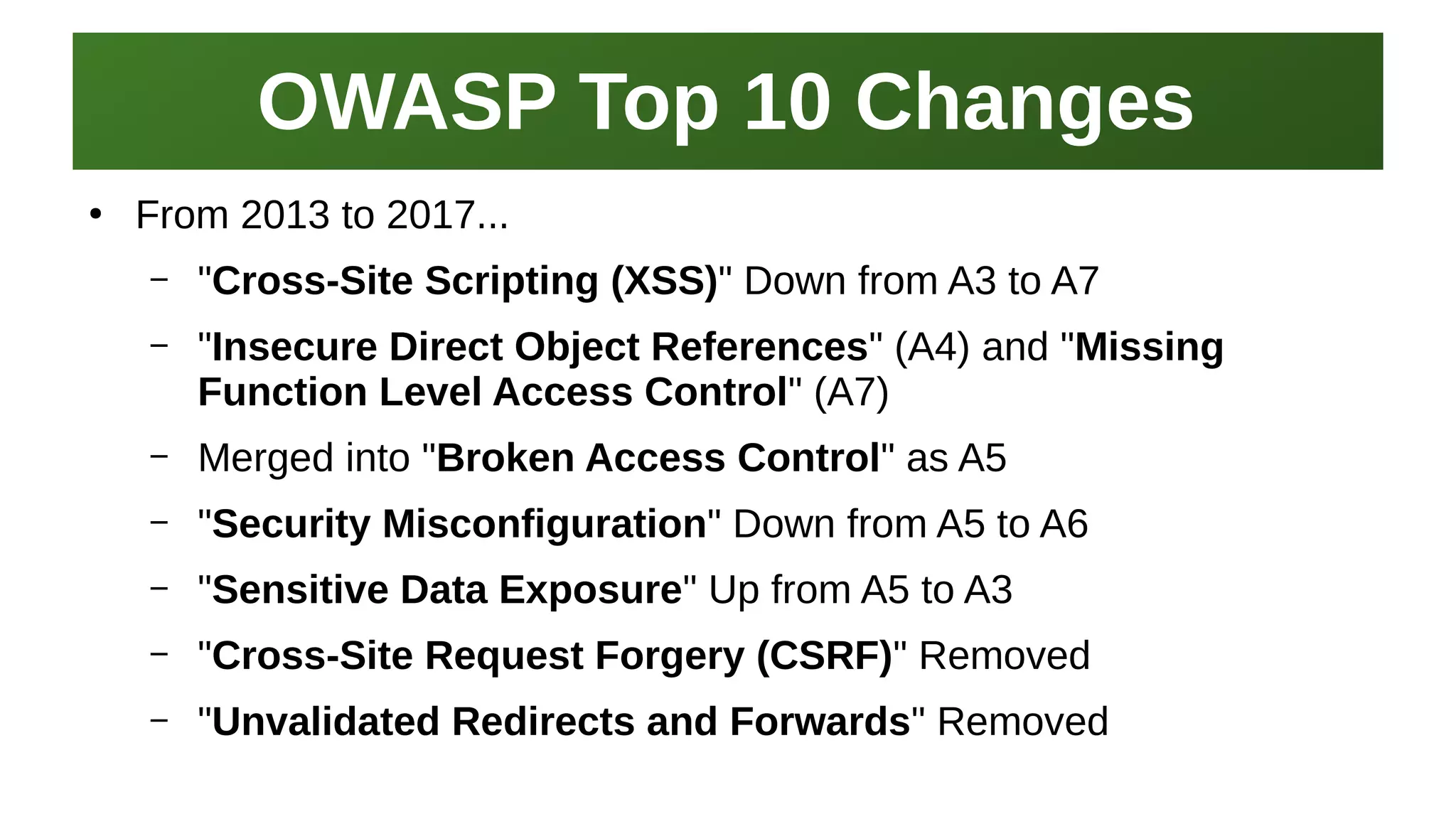
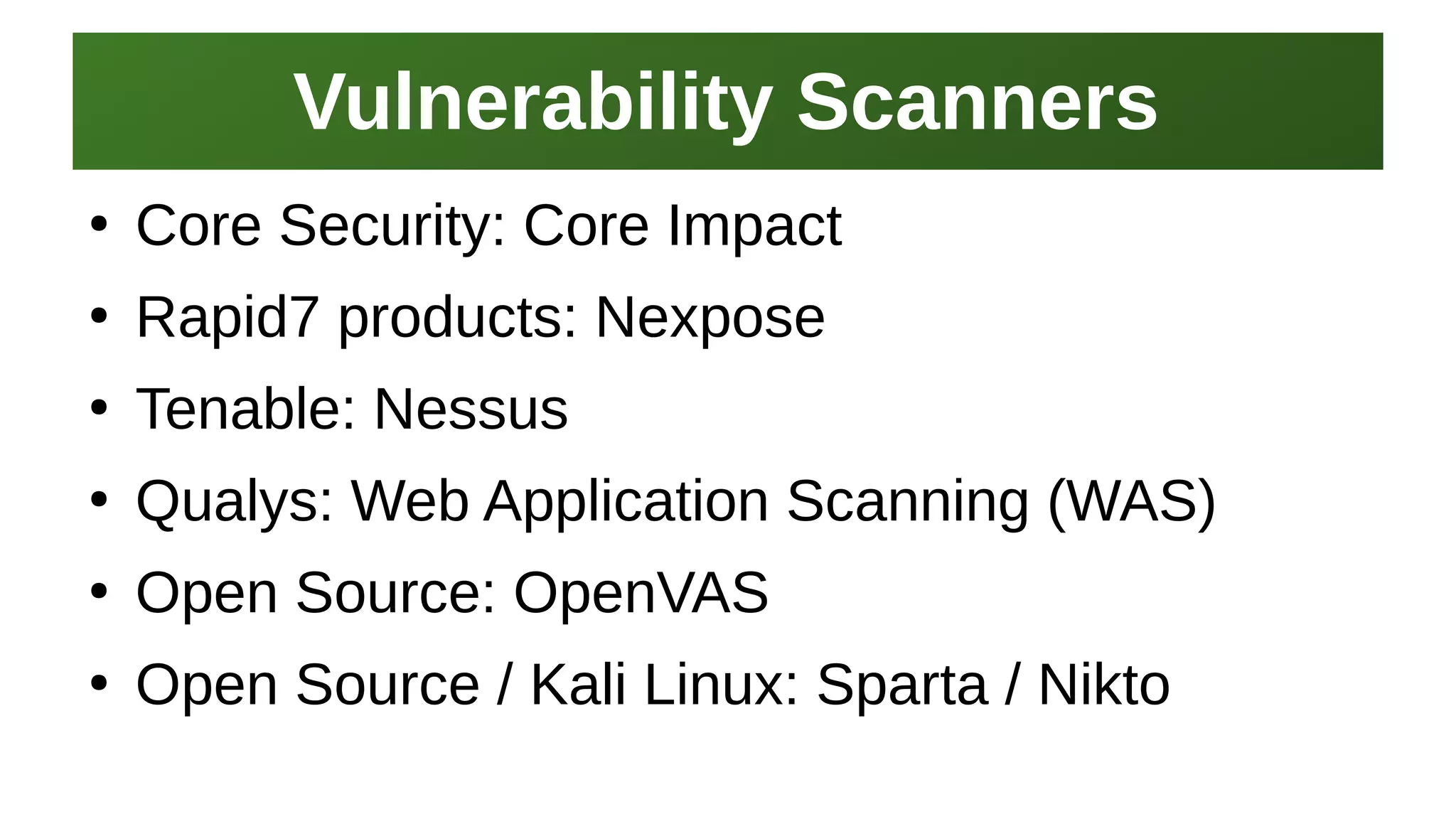
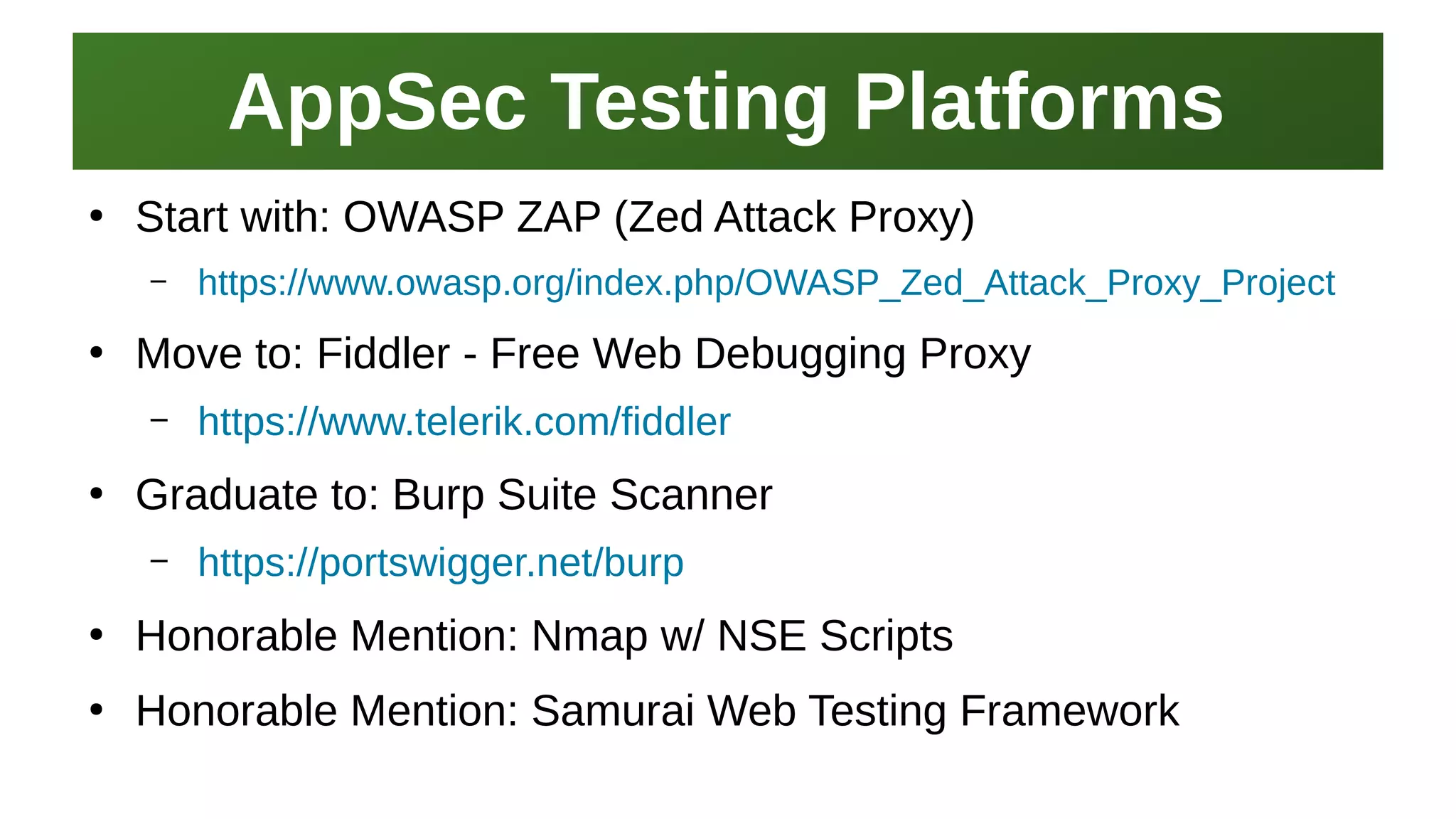
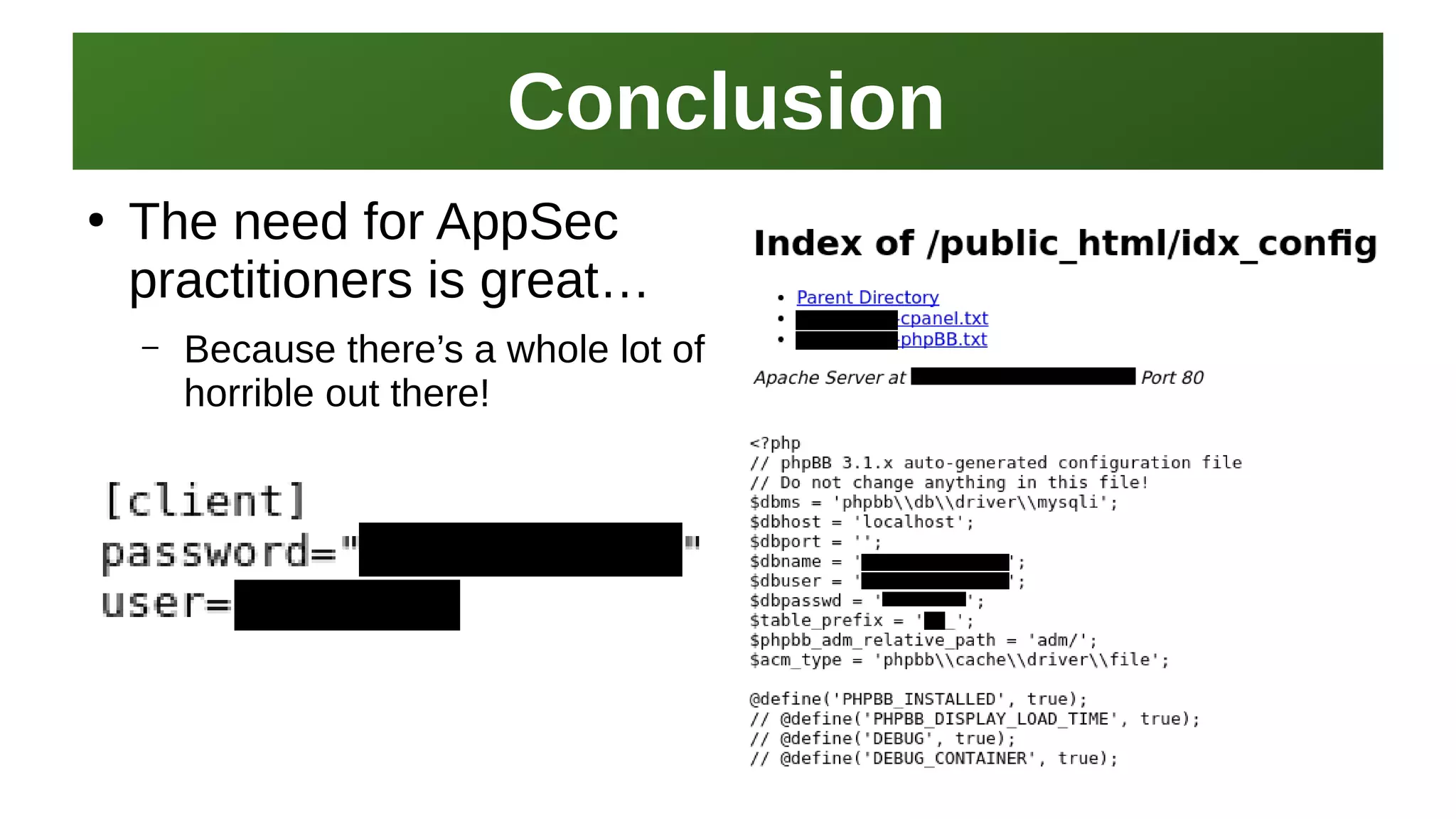
This document provides an overview of application security and the Open Web Application Security Project (OWASP). It discusses what OWASP is, its history and Top 10 list. It also provides resources for learning application development, security testing tools like Nikto and ZAP, and places to learn about application security for free like OWASP itself. The presentation concludes by emphasizing the need for application security practitioners and thanking attendees.