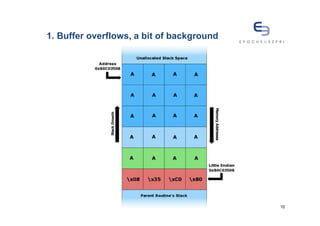
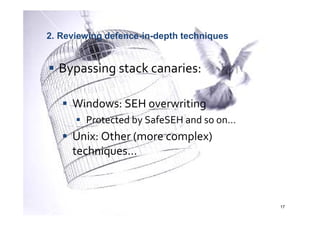
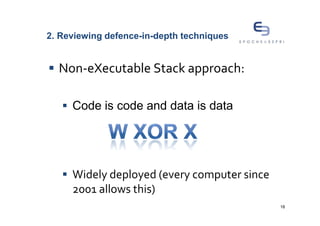
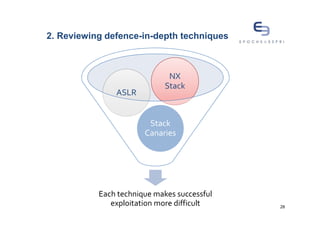
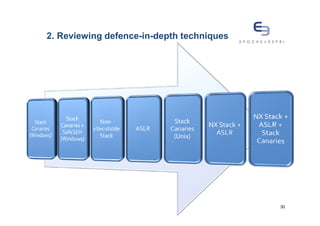
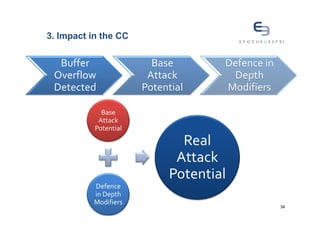
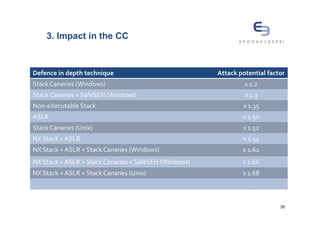
The document discusses buffer overflows, a common security vulnerability, and reviews various defense-in-depth techniques such as stack canaries and Address Space Layout Randomization (ASLR). It examines the effectiveness of these defenses against attacks and their potential to be bypassed. The author emphasizes the importance of a mixed approach to strengthen security against evolving attacker methods.





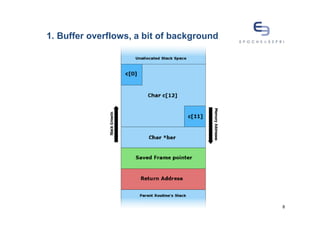
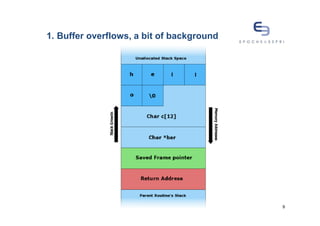
![1. Buffer overflows, a bit of background
You know... The classic stack overflow….
#include <string.h>
void foo (char *bar) {
char c[12];
strcpy(c, bar); // no bounds checking...
}
int main (int argc, char **argv) {
foo(argv[1]);
}
7](https://image.slidesharecdn.com/overflowingattackpotentialscoringdefence-in-depth-120913054608-phpapp02/85/Overflowing-attack-potential-scoring-defence-in-depth-7-320.jpg)