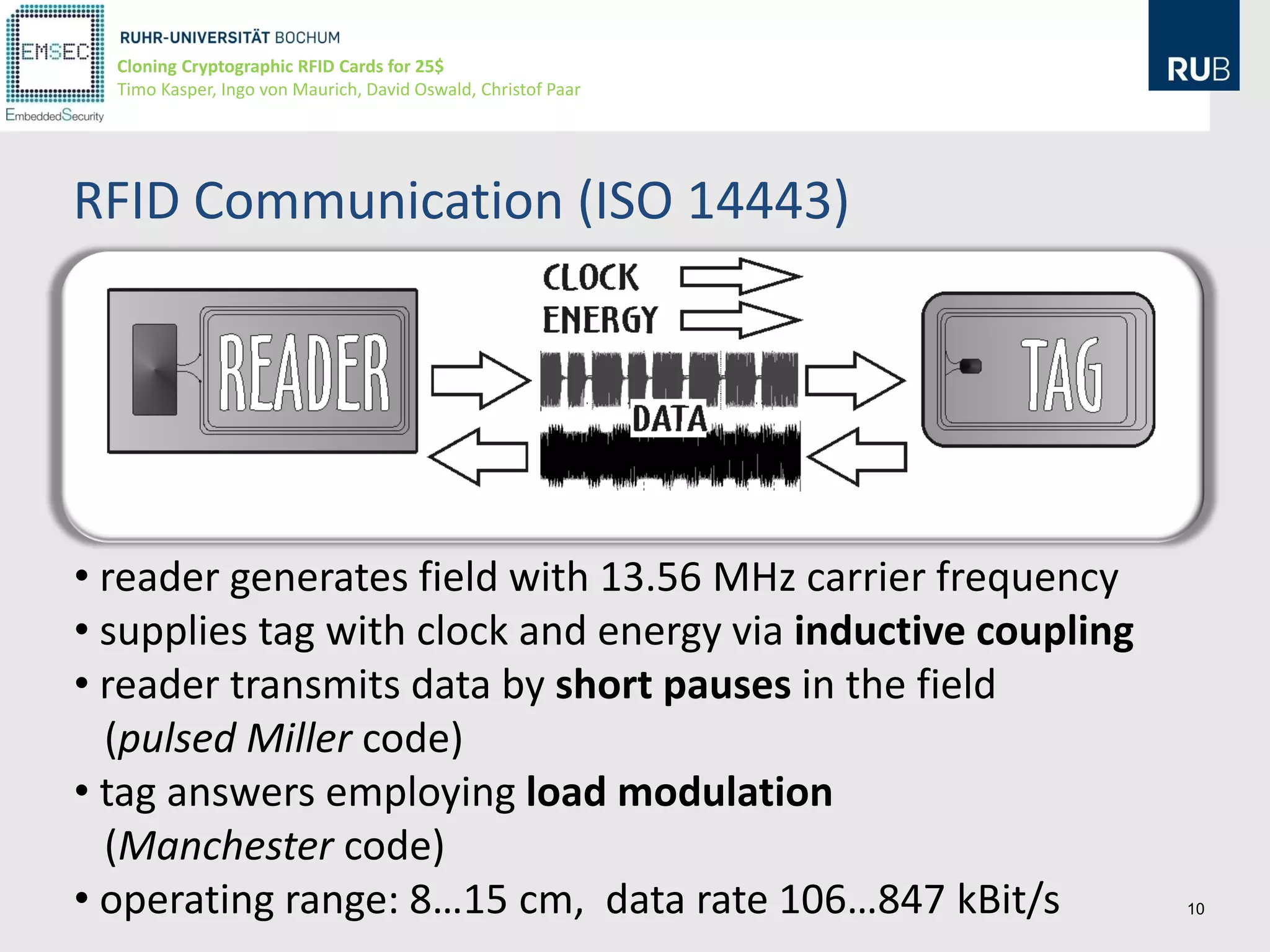
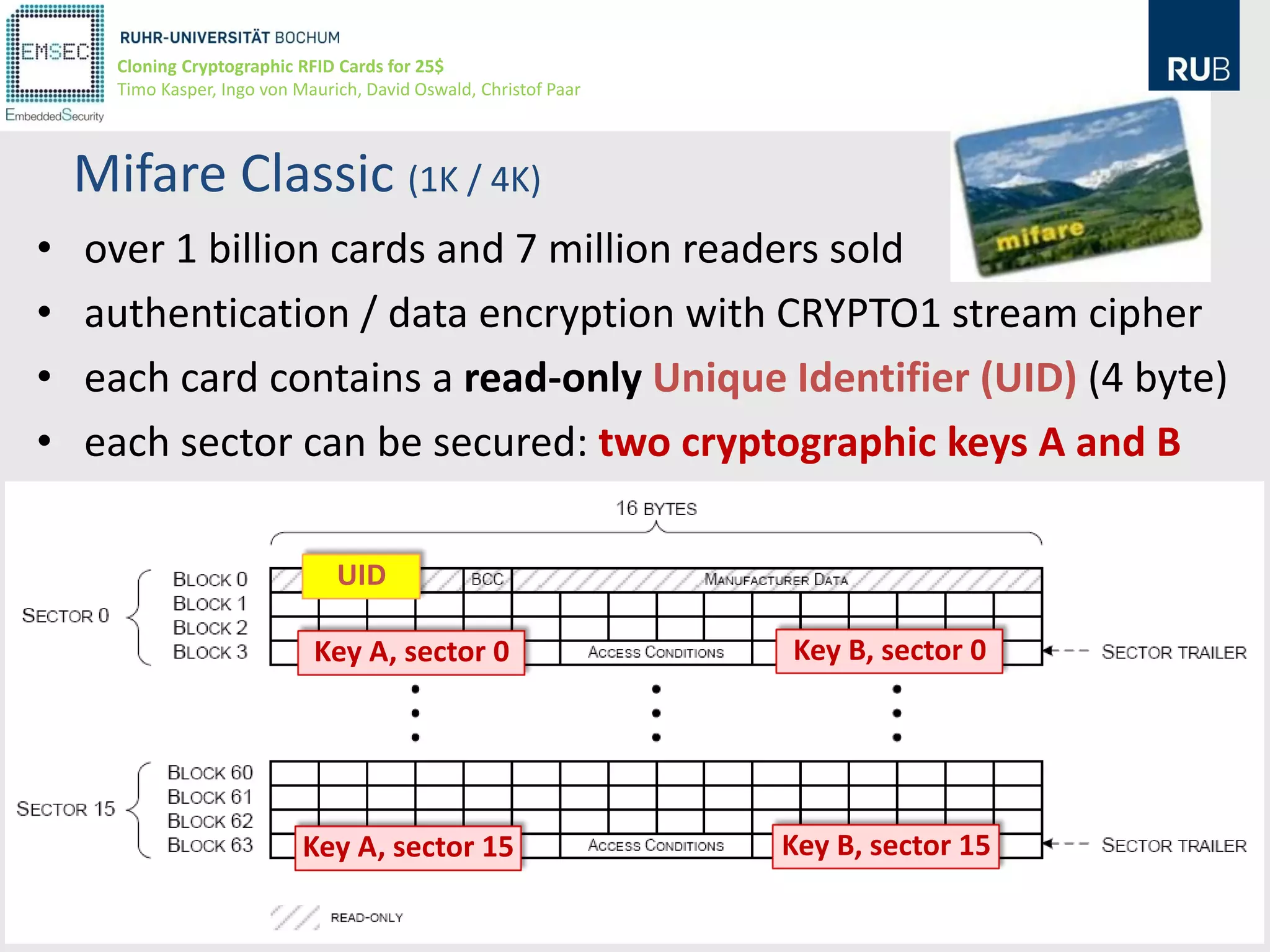
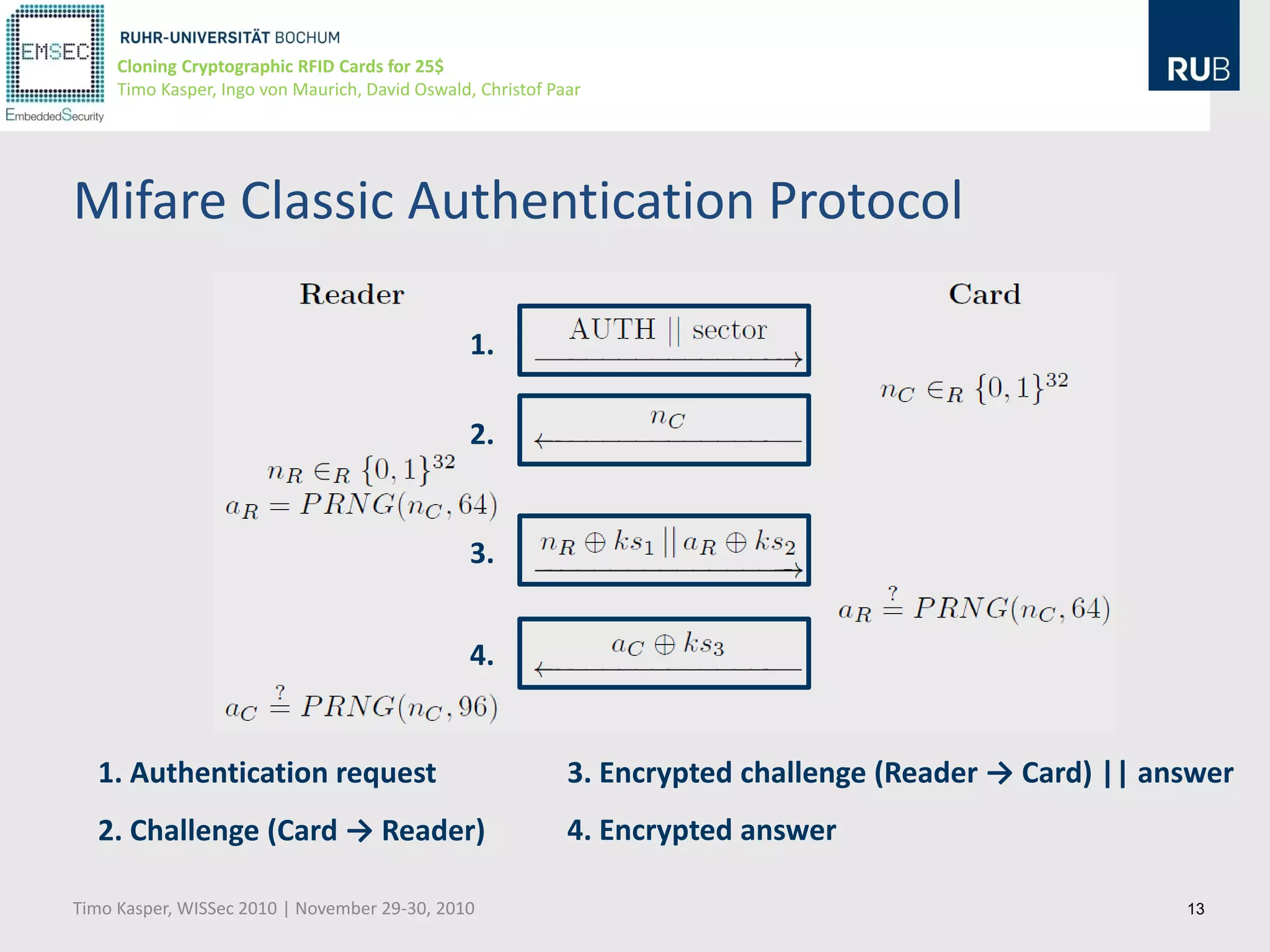
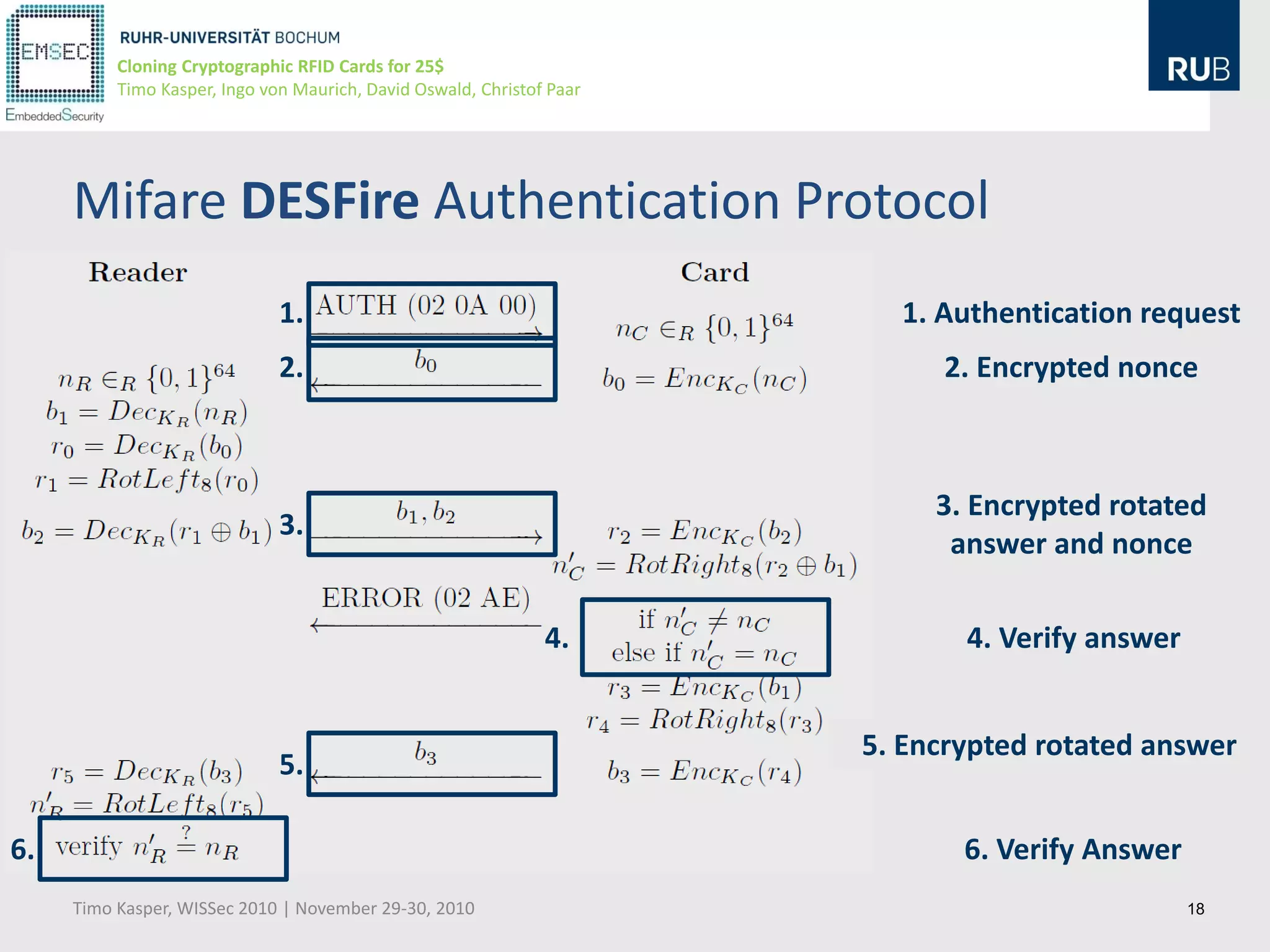
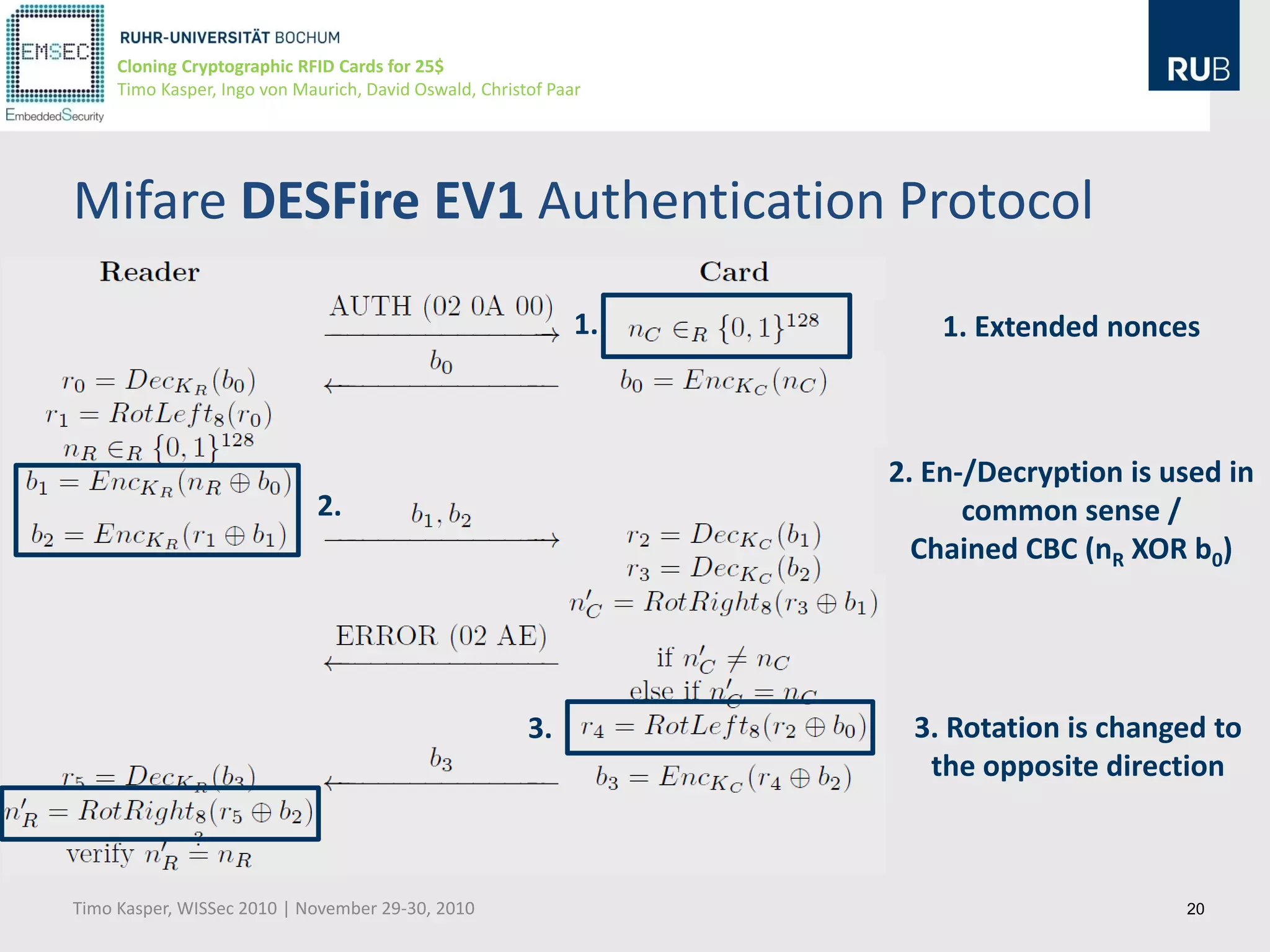
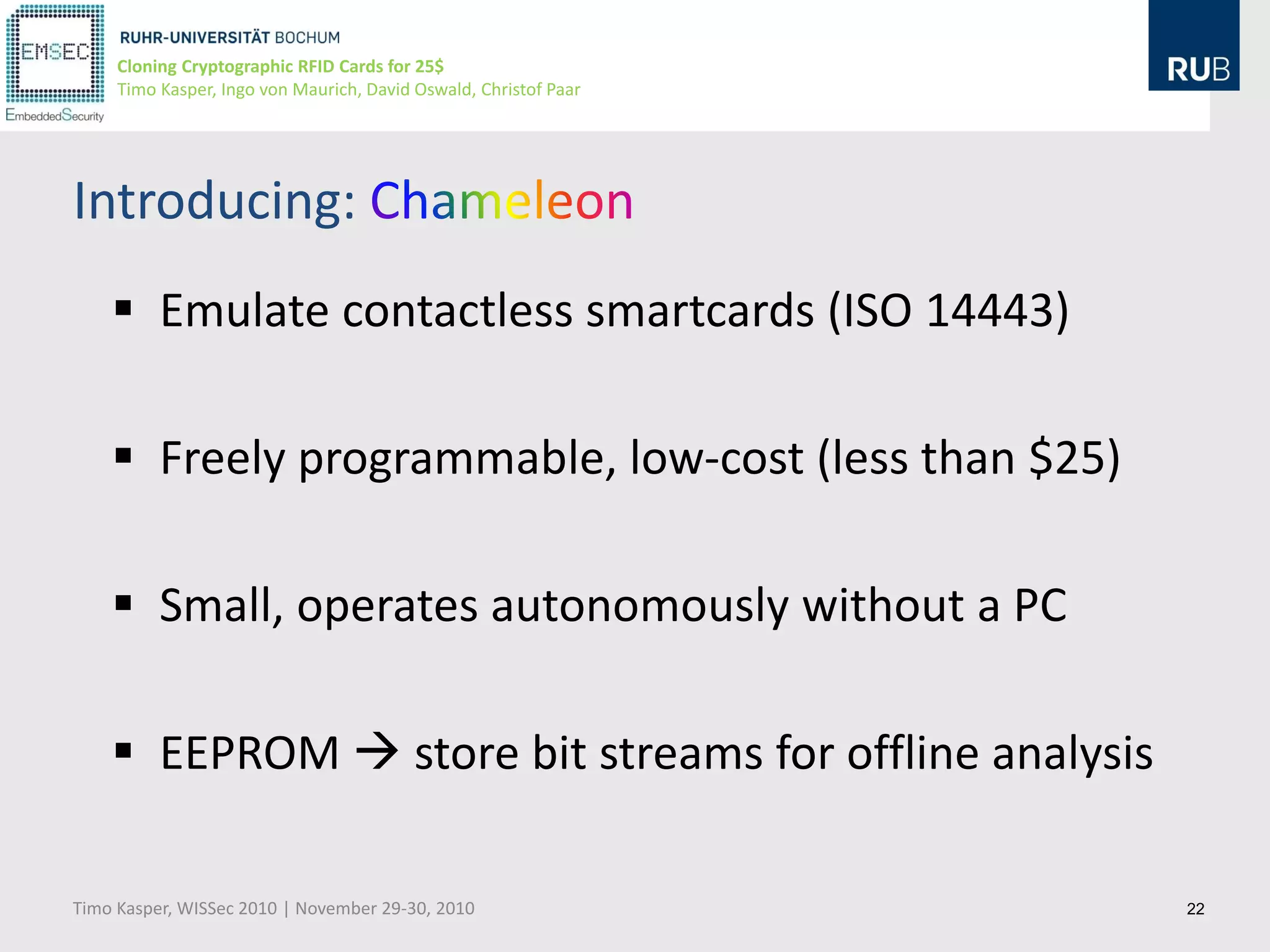
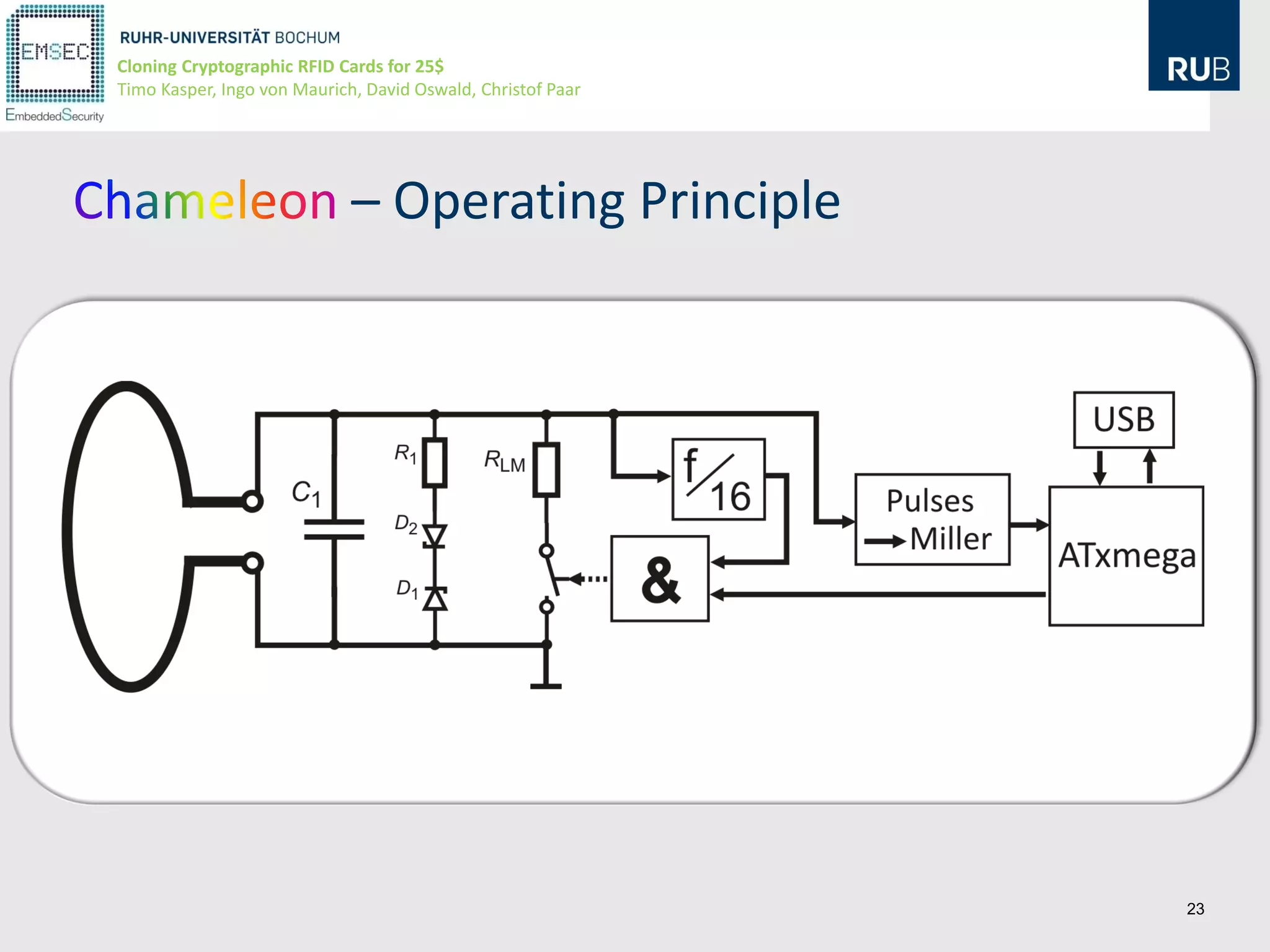
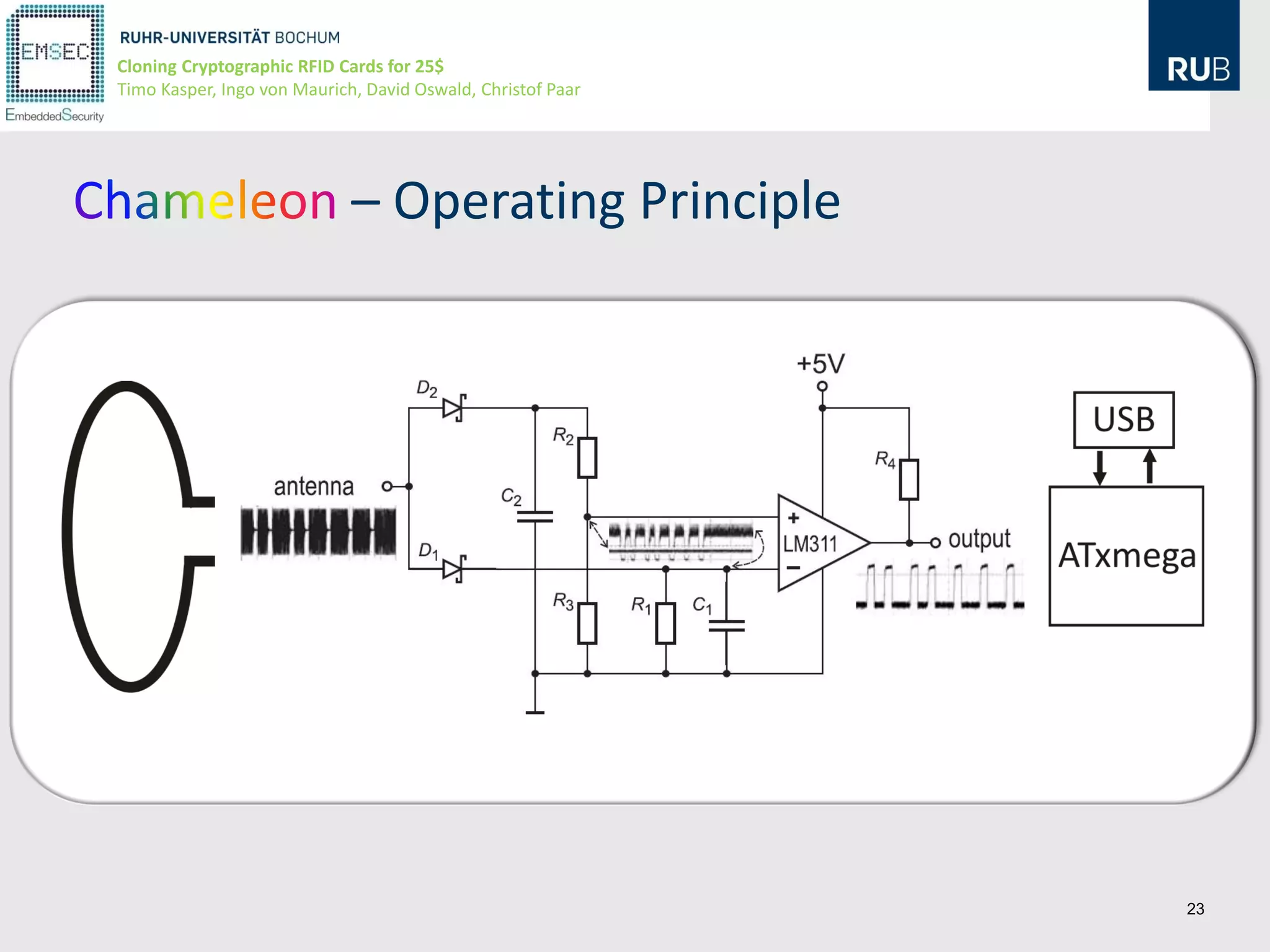
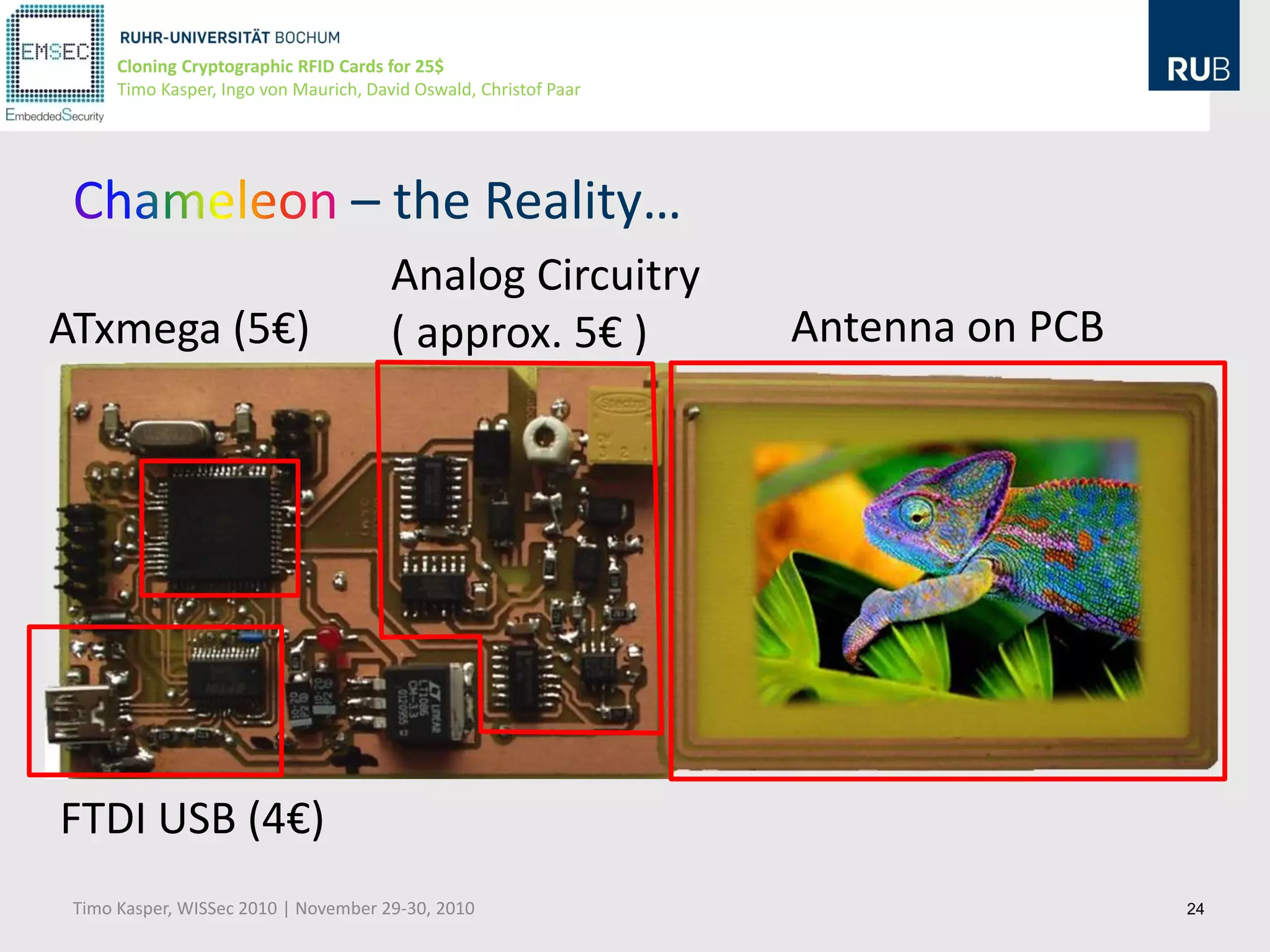
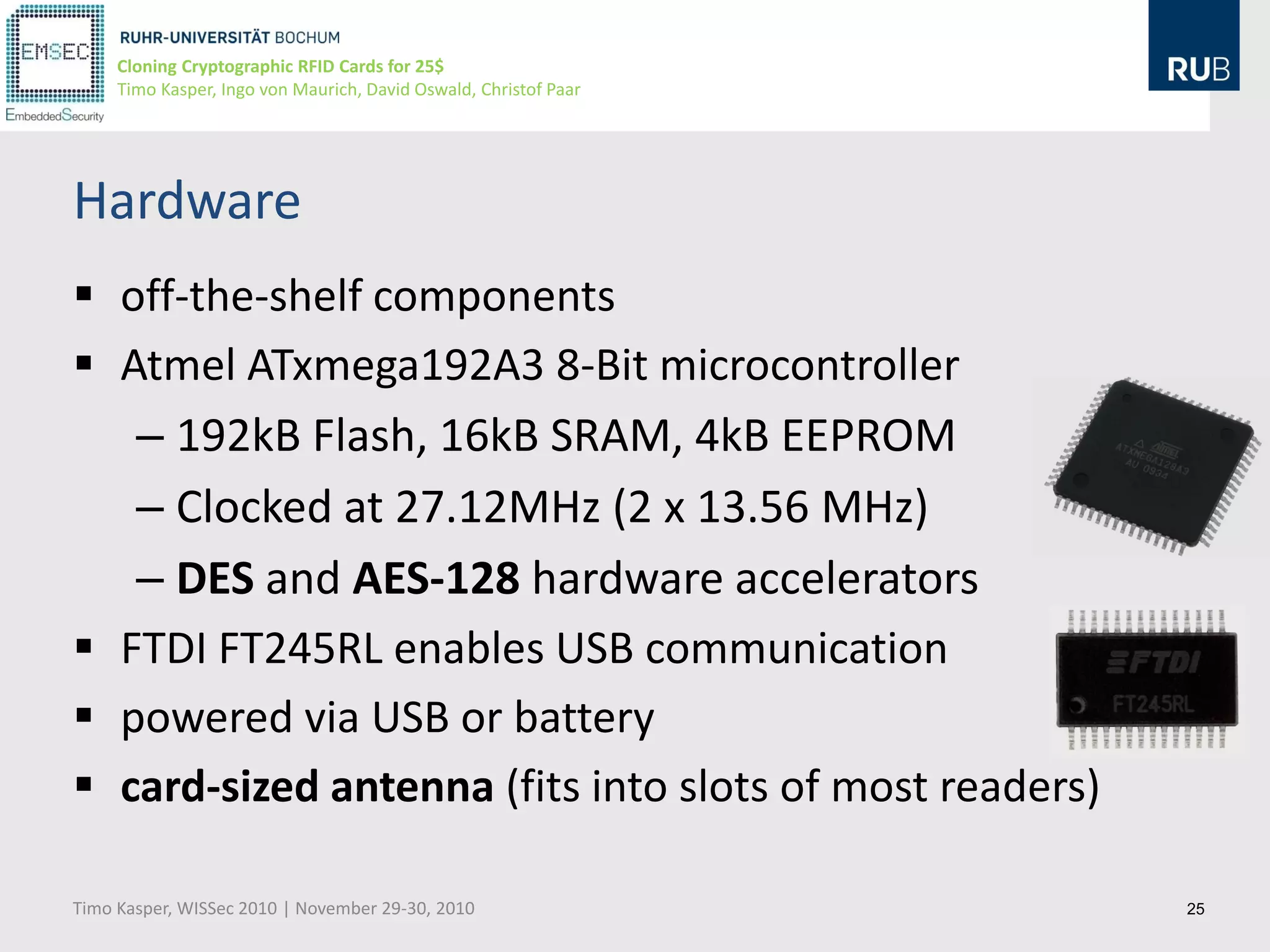
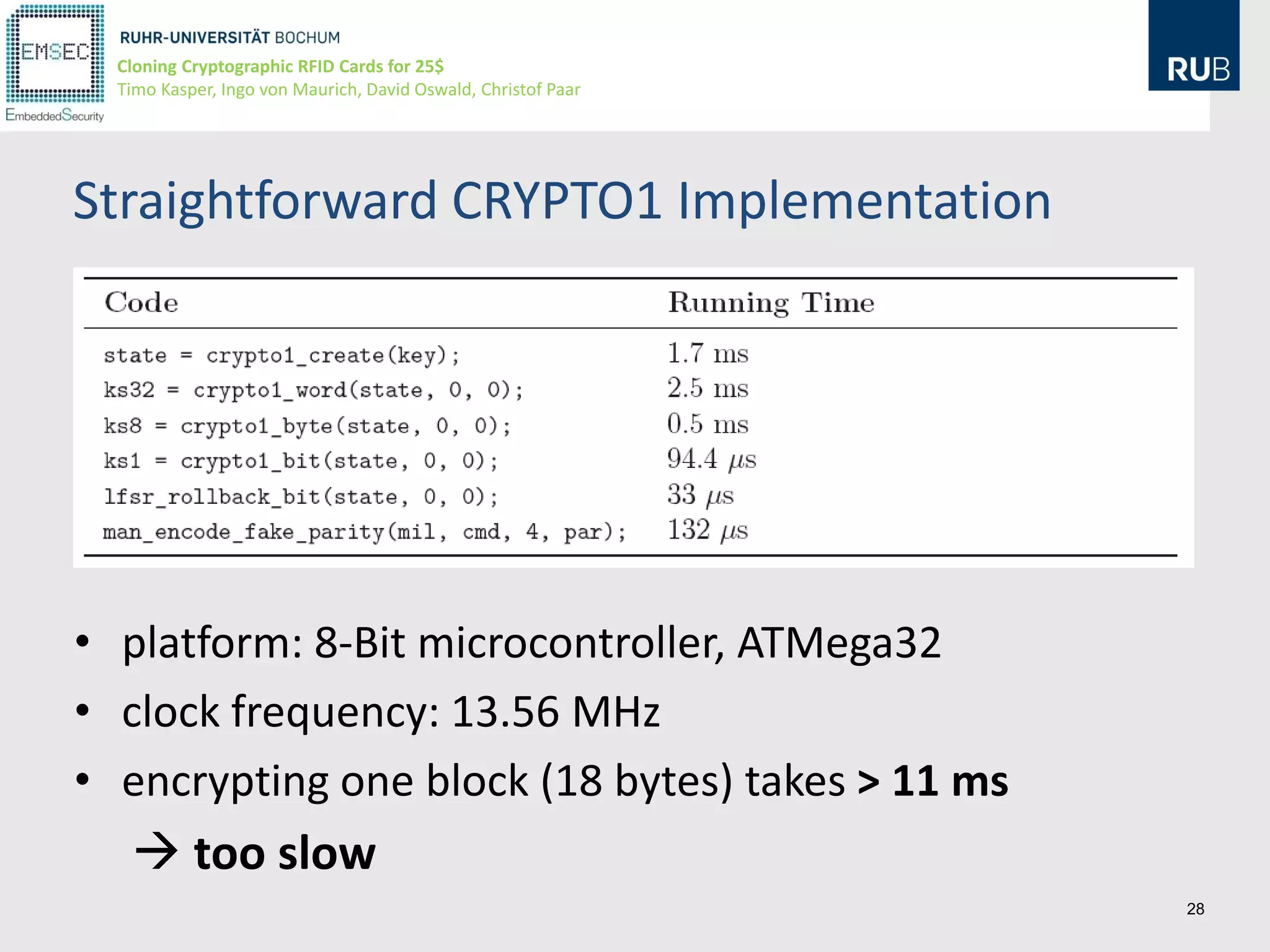
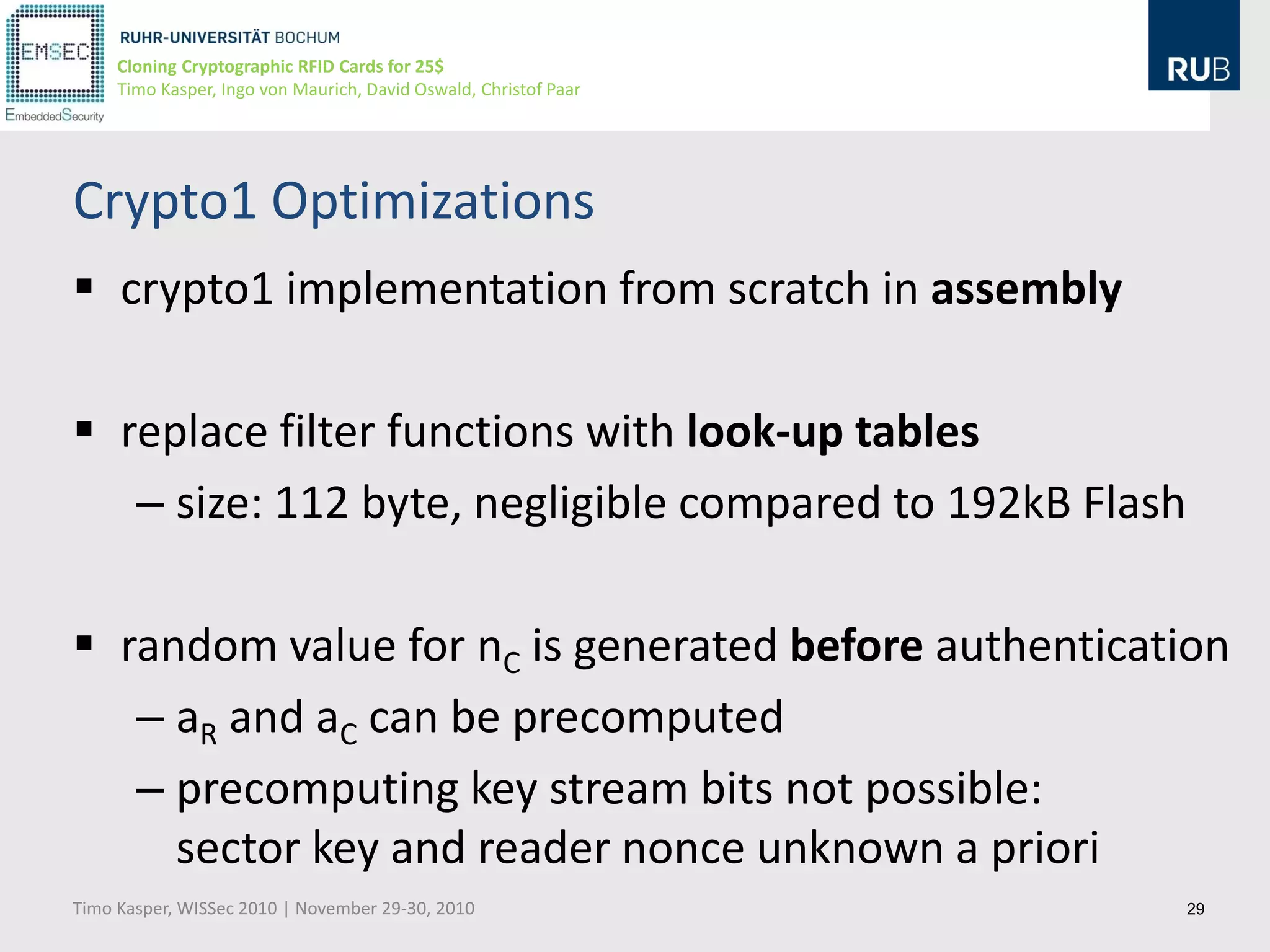
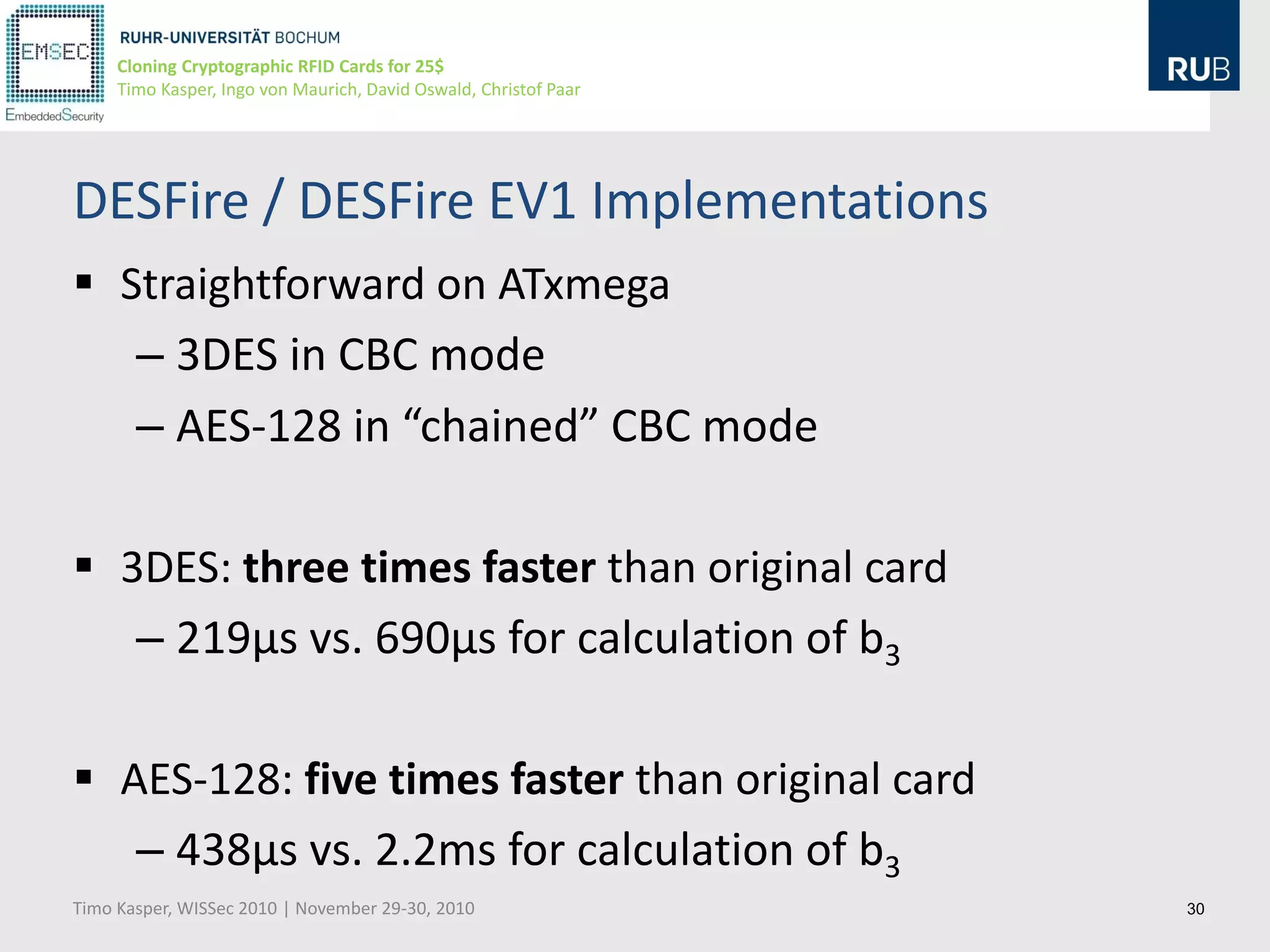
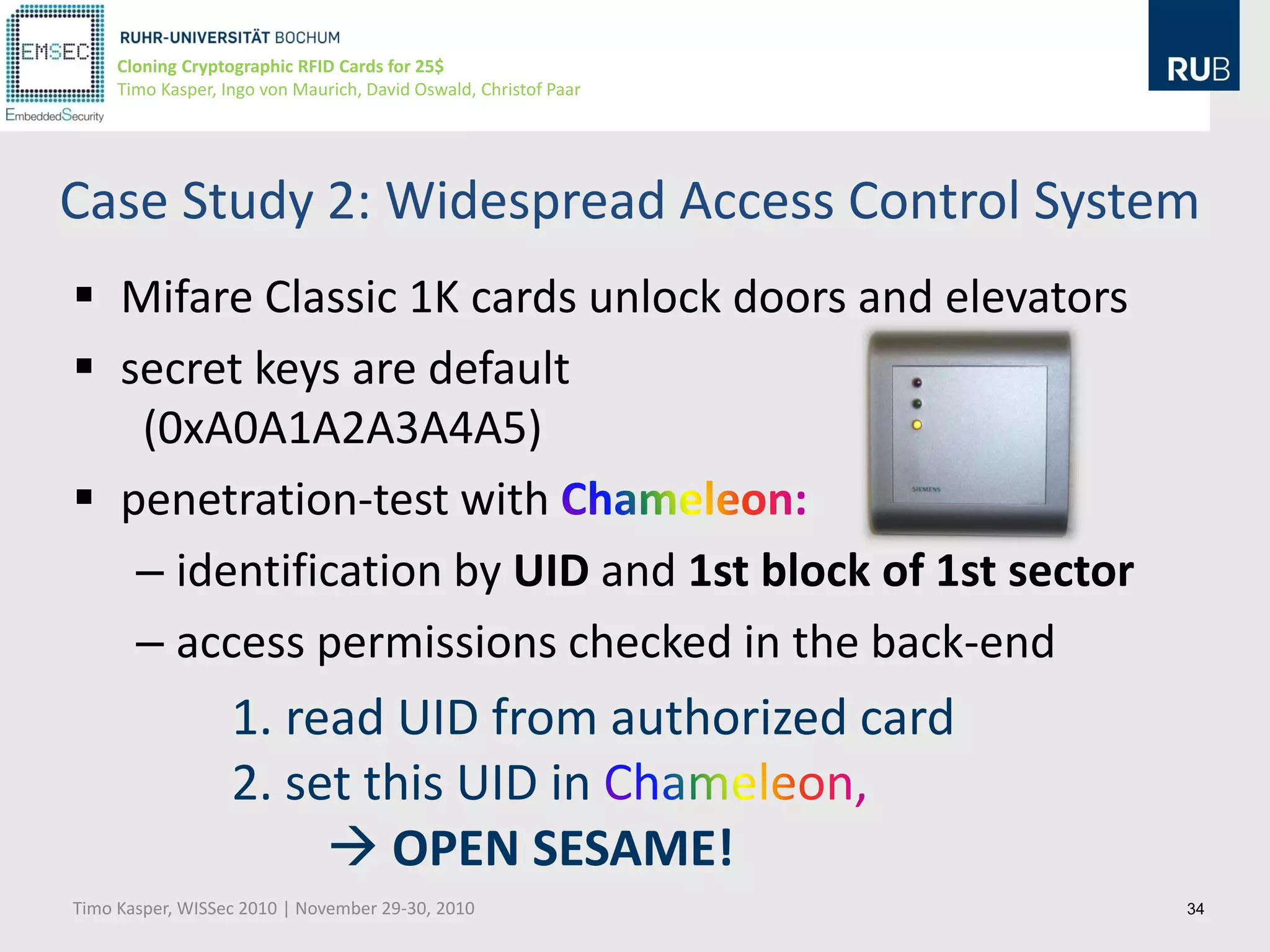
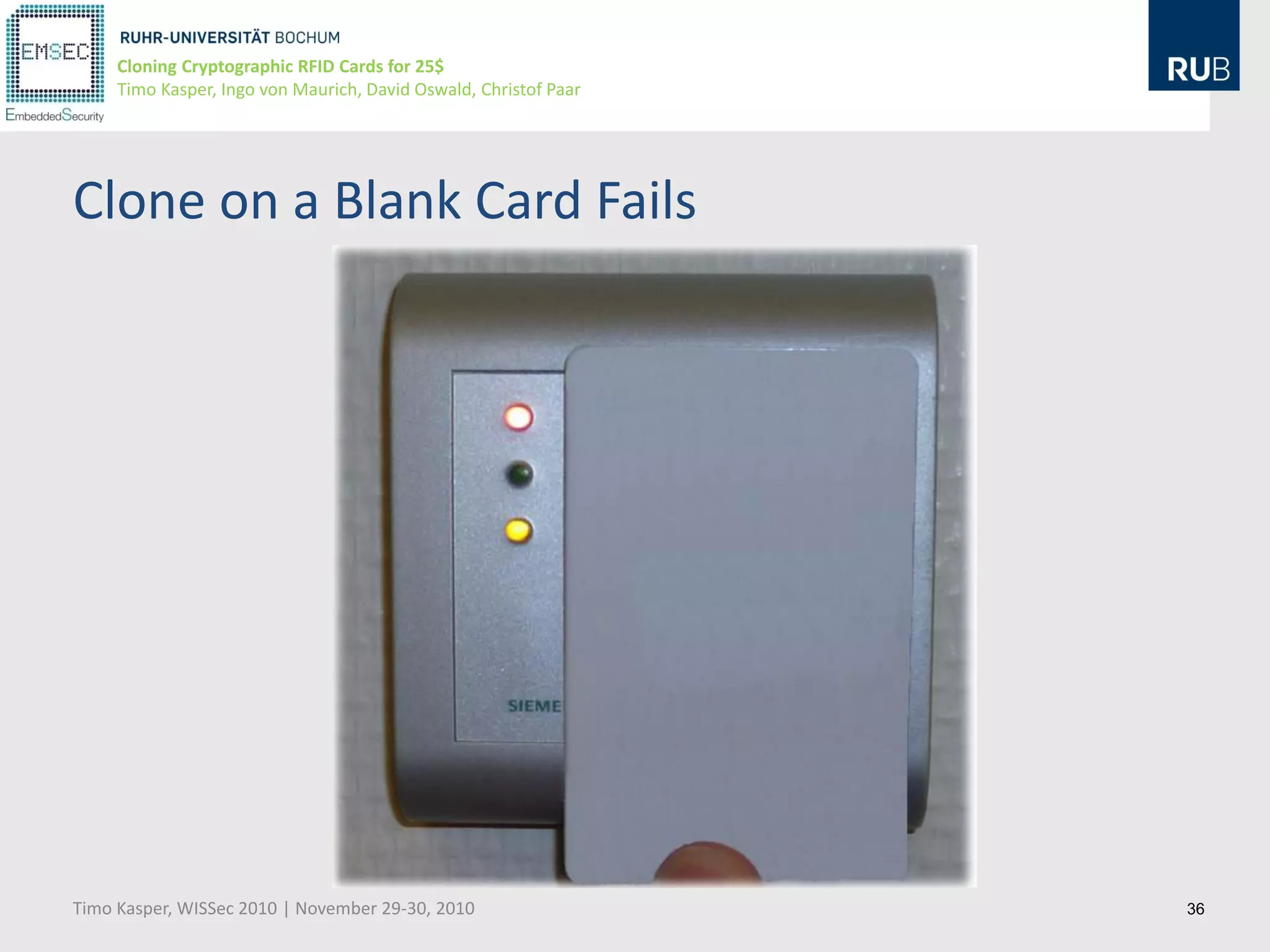
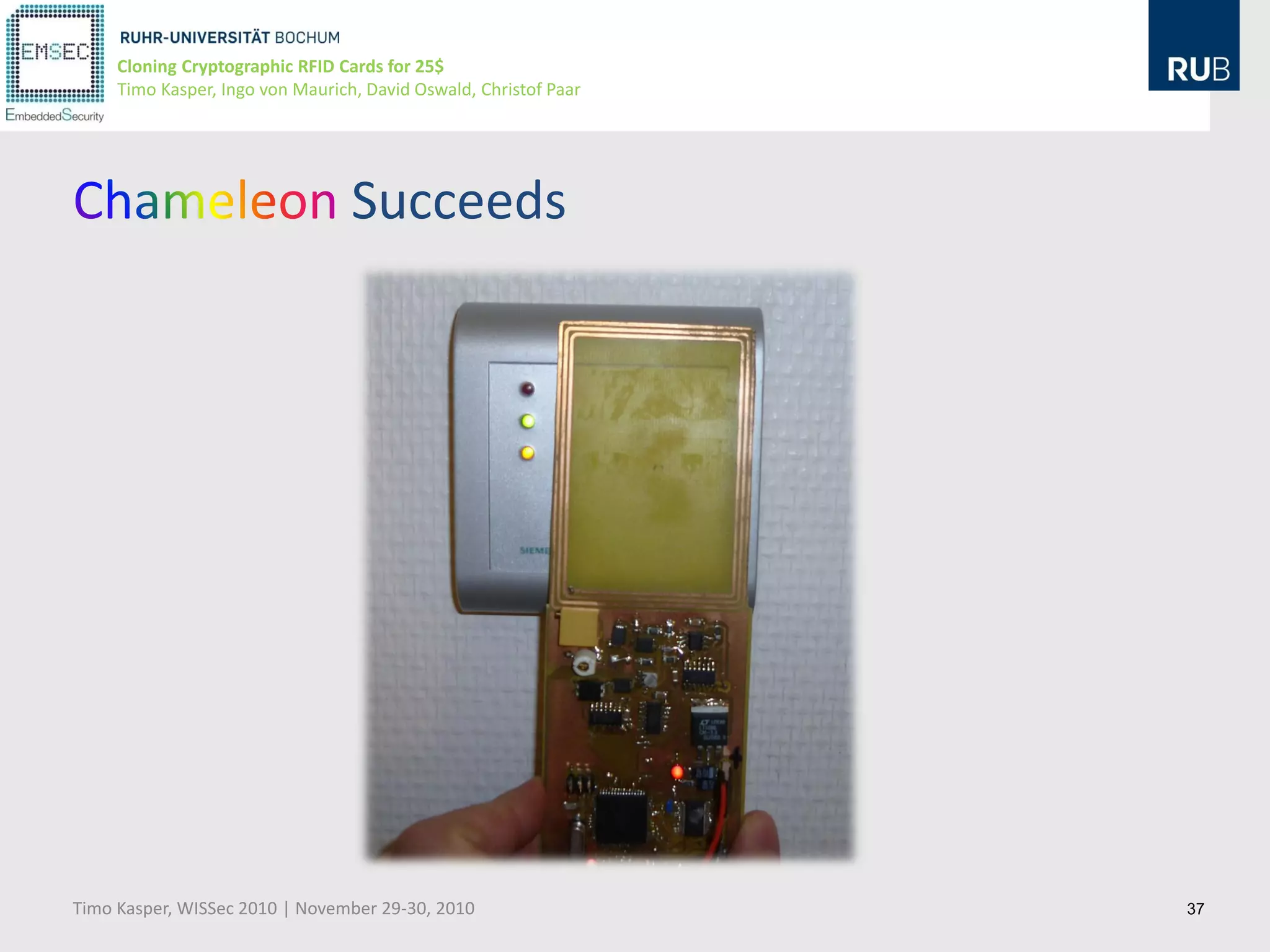
This document discusses cloning cryptographic RFID cards cheaply. It describes motivating real-world attacks on access control and payment systems that use RFID cards. It then provides details on popular RFID card standards like Mifare Classic and DESFire, explaining known vulnerabilities. The document introduces a $25 programmable RFID cloning device that can emulate these cards to support penetration testing and fraud. It concludes by discussing potential real-world attacks using such a device.