The document discusses cybersecurity software development at LogPoint, a company focused on security information and event management (SIEM). It provides an overview of LogPoint's products, services, organizational structure, and use of agile software development methodology. LogPoint's main product is a SIEM tool that provides advanced threat detection, security monitoring, and incident response capabilities. The company uses an agile approach like Scrum for software development, with sprints, daily stand-ups, and emphasis on customer collaboration and feedback.























![21 | P a g e
REFERENCES
[1]Organizational Structure Defination and Therory
“http://www.businessdictionary.com/definition/organizational-structure.html”
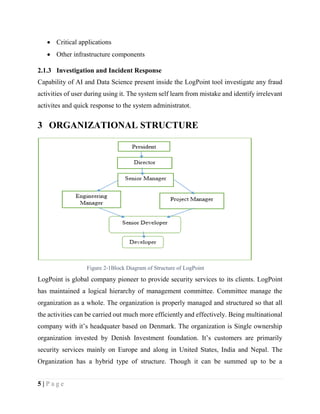
[2] A Guide to the Project Management Body of Knowledge (PMBOK® Guide) — Sixth
Edition and Agile Practice Guide (ENGLISH)](https://image.slidesharecdn.com/sharemyorganizationmanagementreport-190311045743/85/Organization-And-Management-Case-Study-Report-IOE-TU-25-320.jpg)