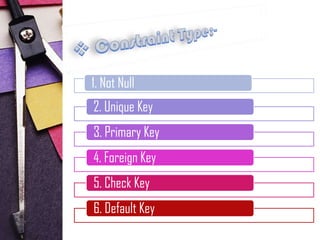
This document discusses SQL constraints. It defines constraints as limitations on the type of data that can go into a table. The main types of constraints covered are:
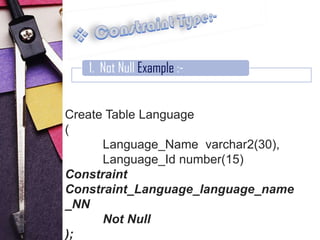
1. Not null constraints, which enforce that a column cannot be null
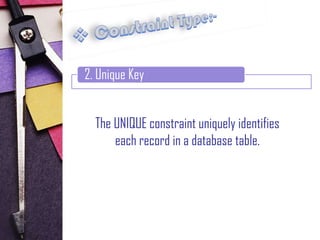
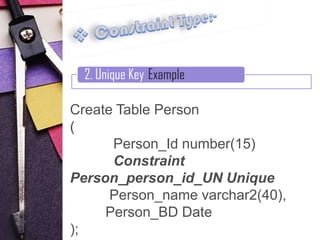
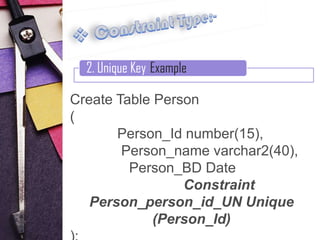
2. Unique constraints, which uniquely identify each record in a table
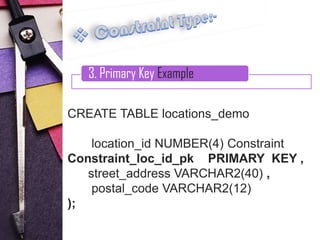
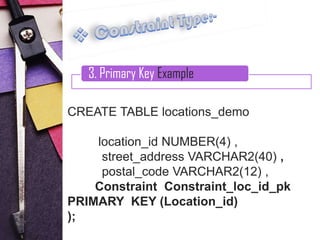
3. Primary key constraints, which uniquely identify each record and cannot be null
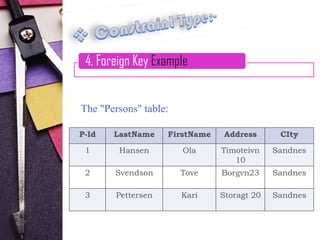
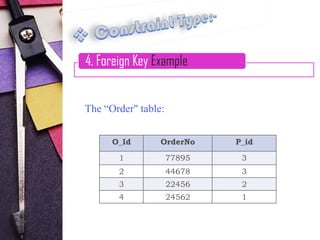
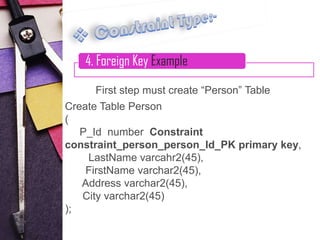
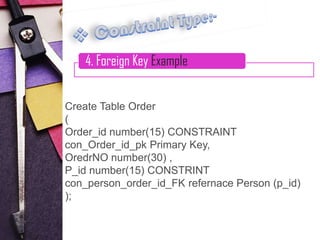
4. Foreign key constraints, which link to primary keys in other tables to define relationships
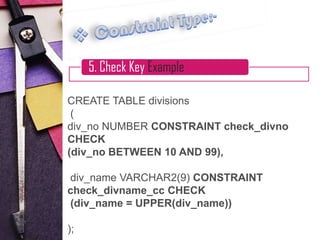
5. Check constraints, which define valid value ranges for a column
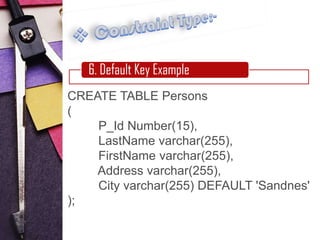
6. Default constraints, which provide a default value for a column if no other value is specified.
Examples are provided for each constraint type to illustrate their syntax and usage



![Constraint [Constraint name] Constraint Type](https://image.slidesharecdn.com/sqlconstraint-copy-120220160804-phpapp02/85/oracle-Sql-constraint-4-320.jpg)