1) The document discusses Oracle Identity Governance and Access Management projects for several clients, including integrating numerous applications with OIM and implementing ESSO.
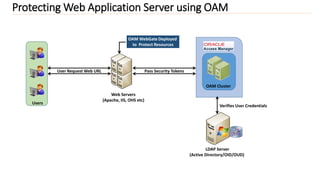
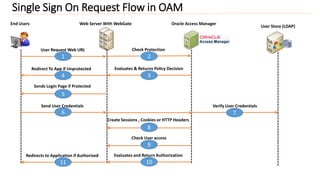
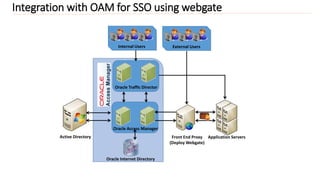
2) It provides an overview of integrating applications with OIM using connectors and protecting web applications using OAM with WebGates deployed.
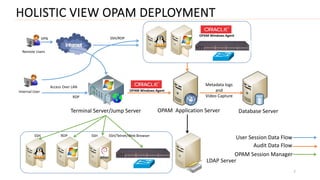
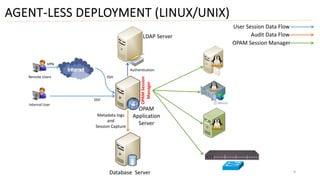
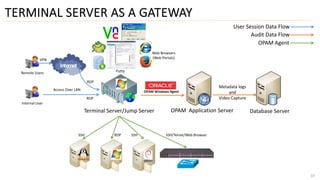
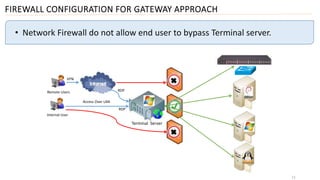
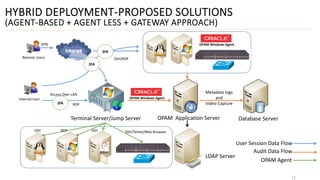
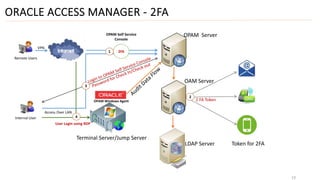
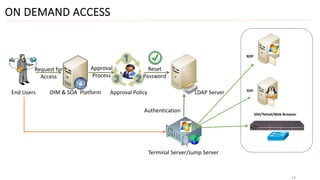
3) Finally, it outlines different deployment approaches for OAM including agent-based, agent-less, using a terminal server as a gateway, and a hybrid approach combining methods.


![Integration with OIM using connectors
3
Application Database
Recon Employee Master Data
Provisioning
Reconciliation Adapter
Provisioning Adapter
Reconciliation
HRMS
Data From Authentic Source
(Trusted Reconciliation)
Oracle Identity Manager
Identity Connector Framework
(ICF)
[DBAT]](https://image.slidesharecdn.com/e7e22223-4319-4360-8c7f-0ea6061af3e2-161010070129/85/Presentation-on-OIM-3-320.jpg)