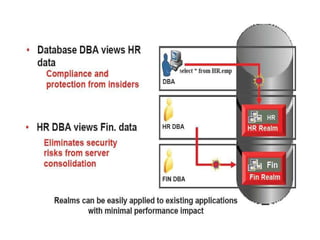
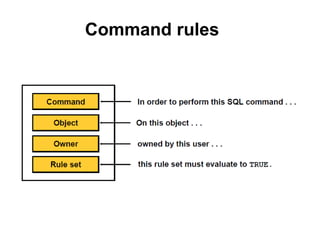
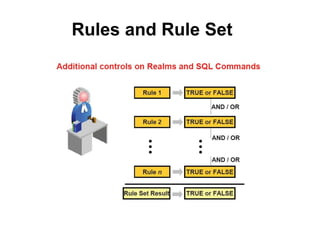
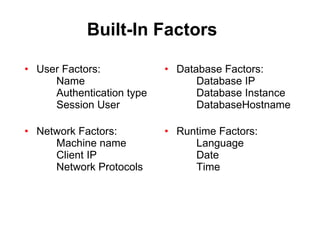
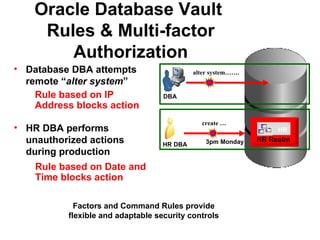
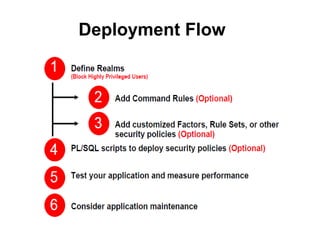
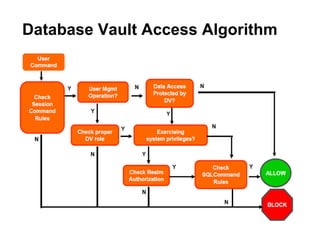
The document discusses Oracle Database Vault, which provides an integrated security framework to control access to databases based on factors like network, users, privileges, roles, and SQL commands. It achieves separation of duties and prevents misuse of powerful privileges. Database Vault enforces compliance requirements and supports database consolidation while requiring no application changes and having minimal performance impact.