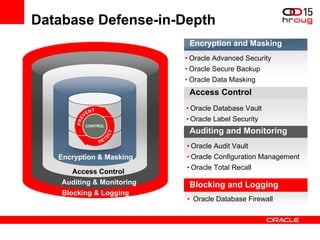
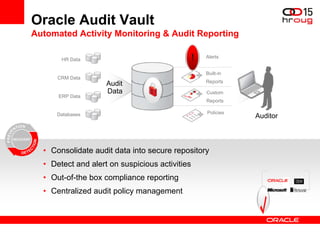
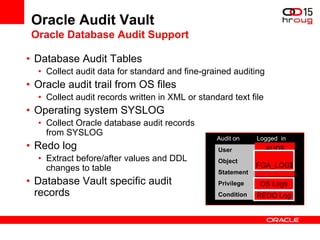
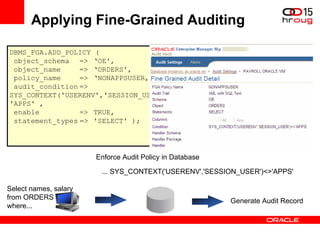
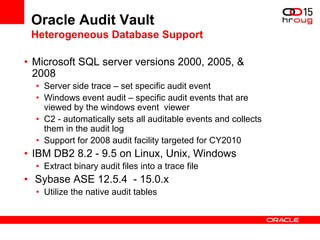
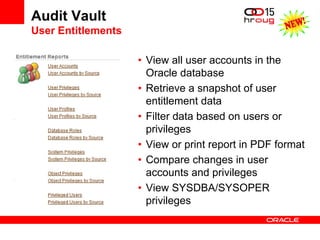
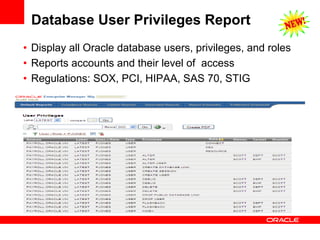
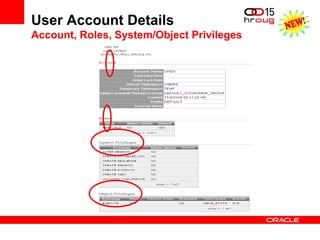
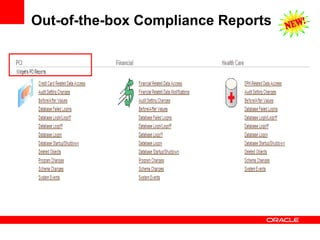
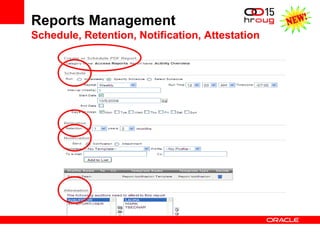
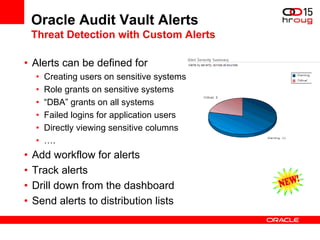
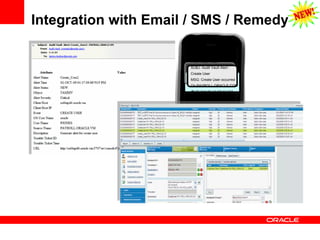
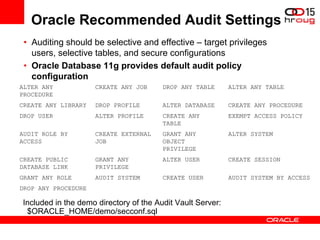
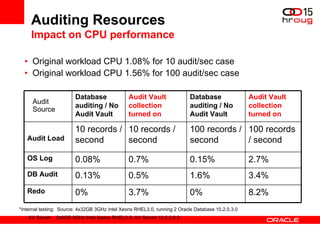
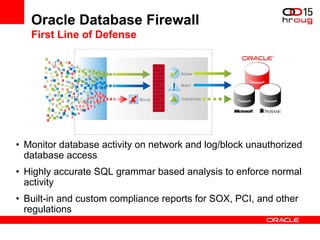
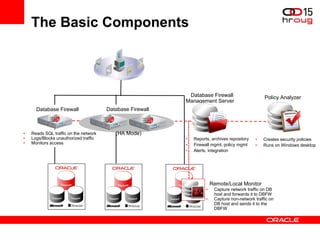
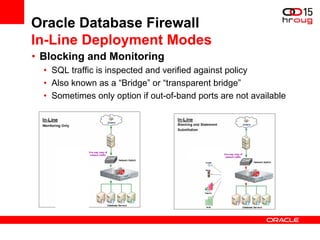
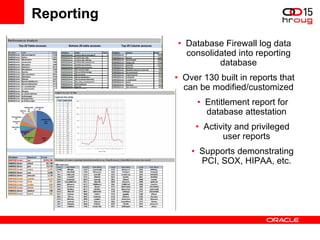
The document discusses various Oracle database security features, including the Oracle Audit Vault, which consolidates audit data and provides automated activity monitoring and compliance reporting. It emphasizes the importance of detective controls for monitoring privileged user accounts and ensuring compliant access to sensitive data. Additionally, it highlights the Oracle Database Firewall as a protective measure against unauthorized access and the flexible deployment options available for database security management.