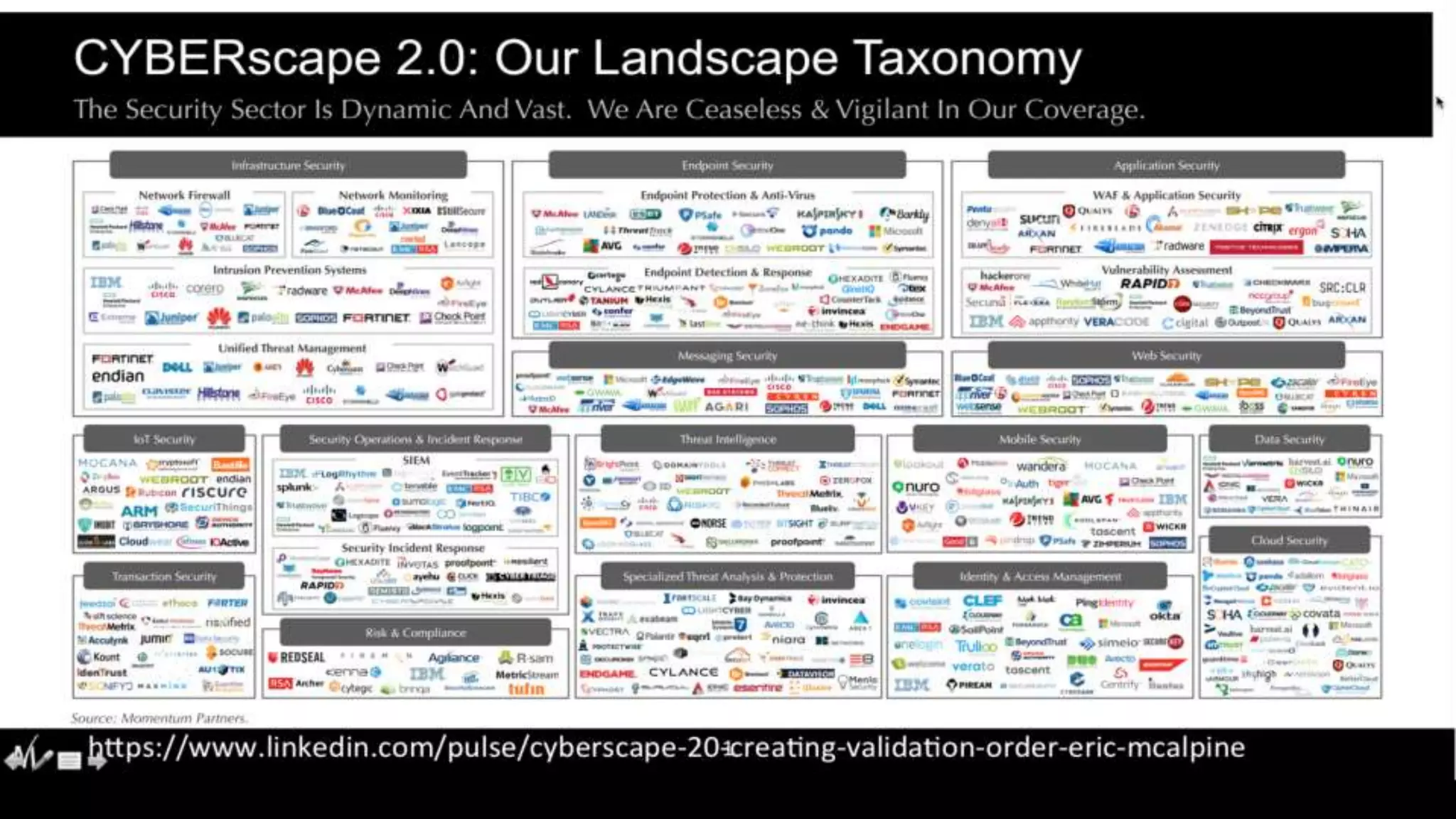
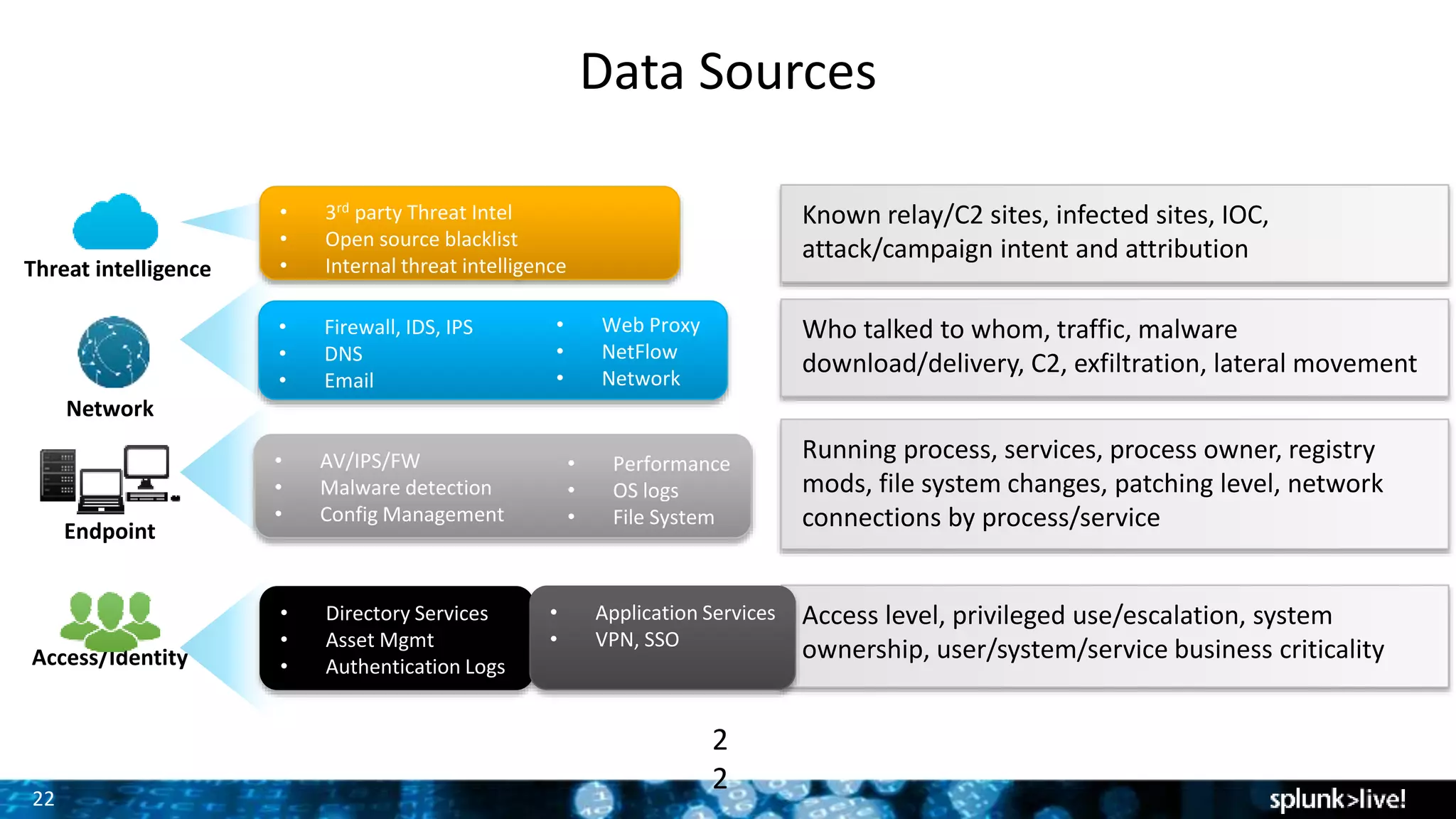
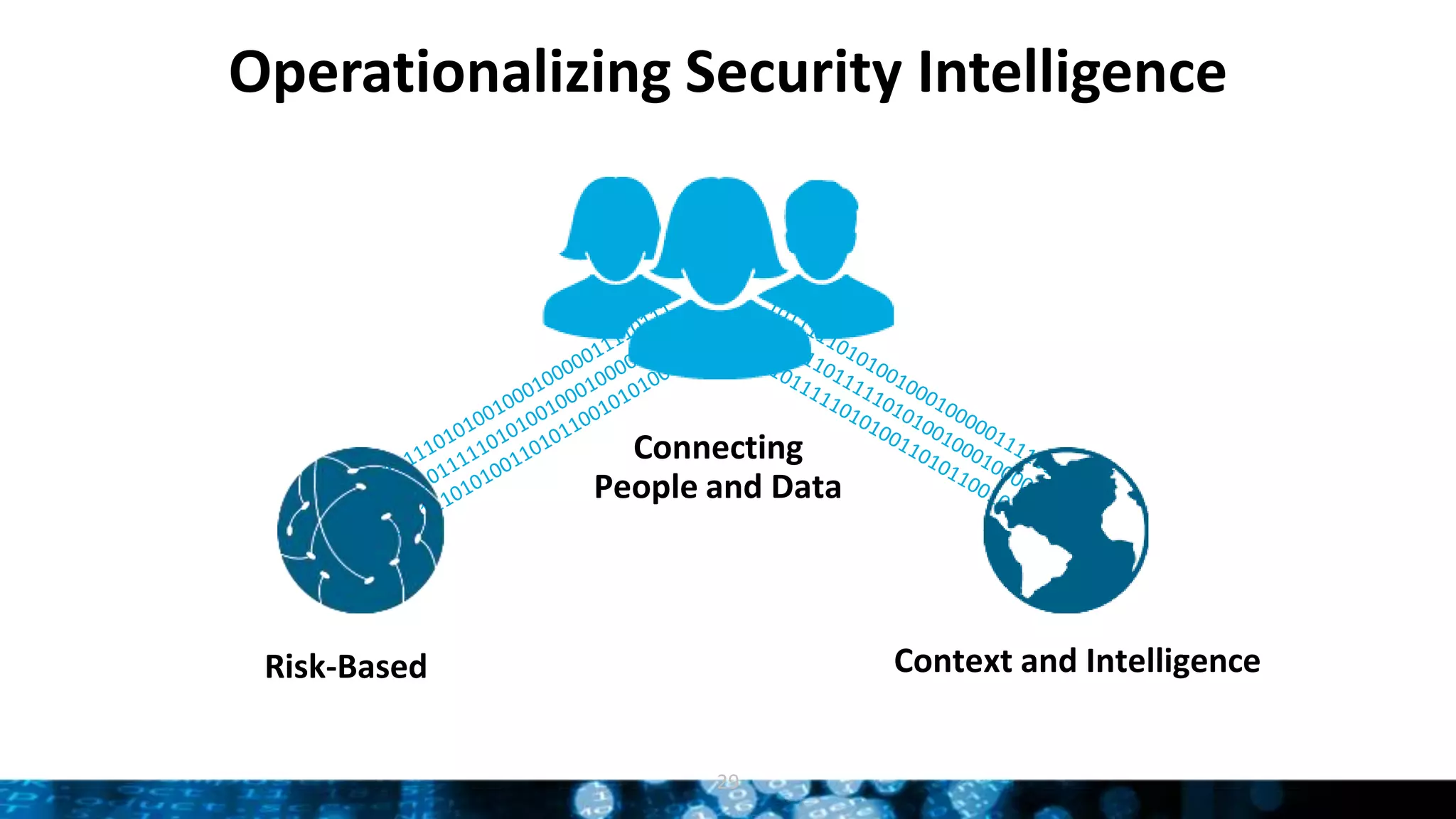
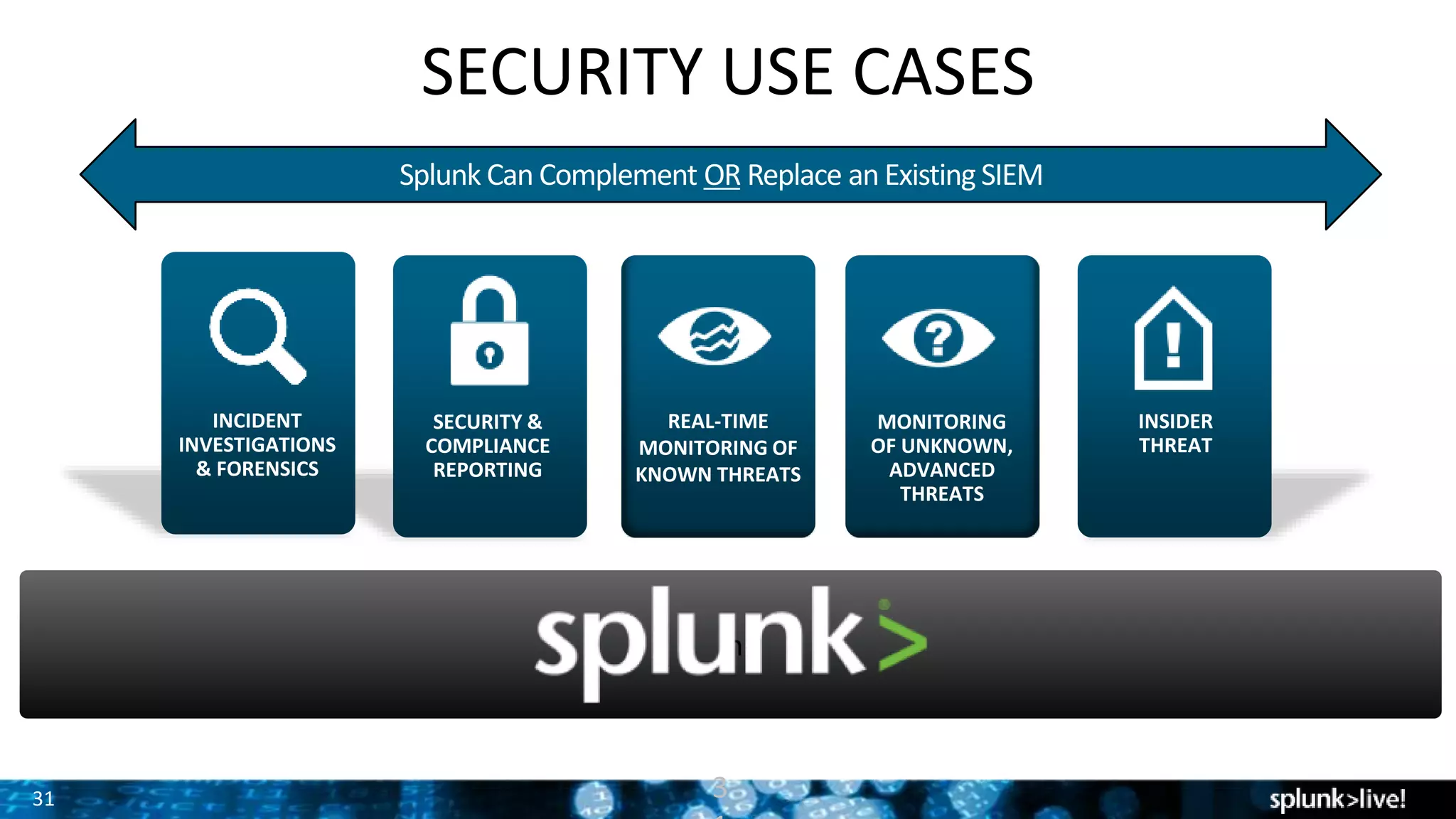
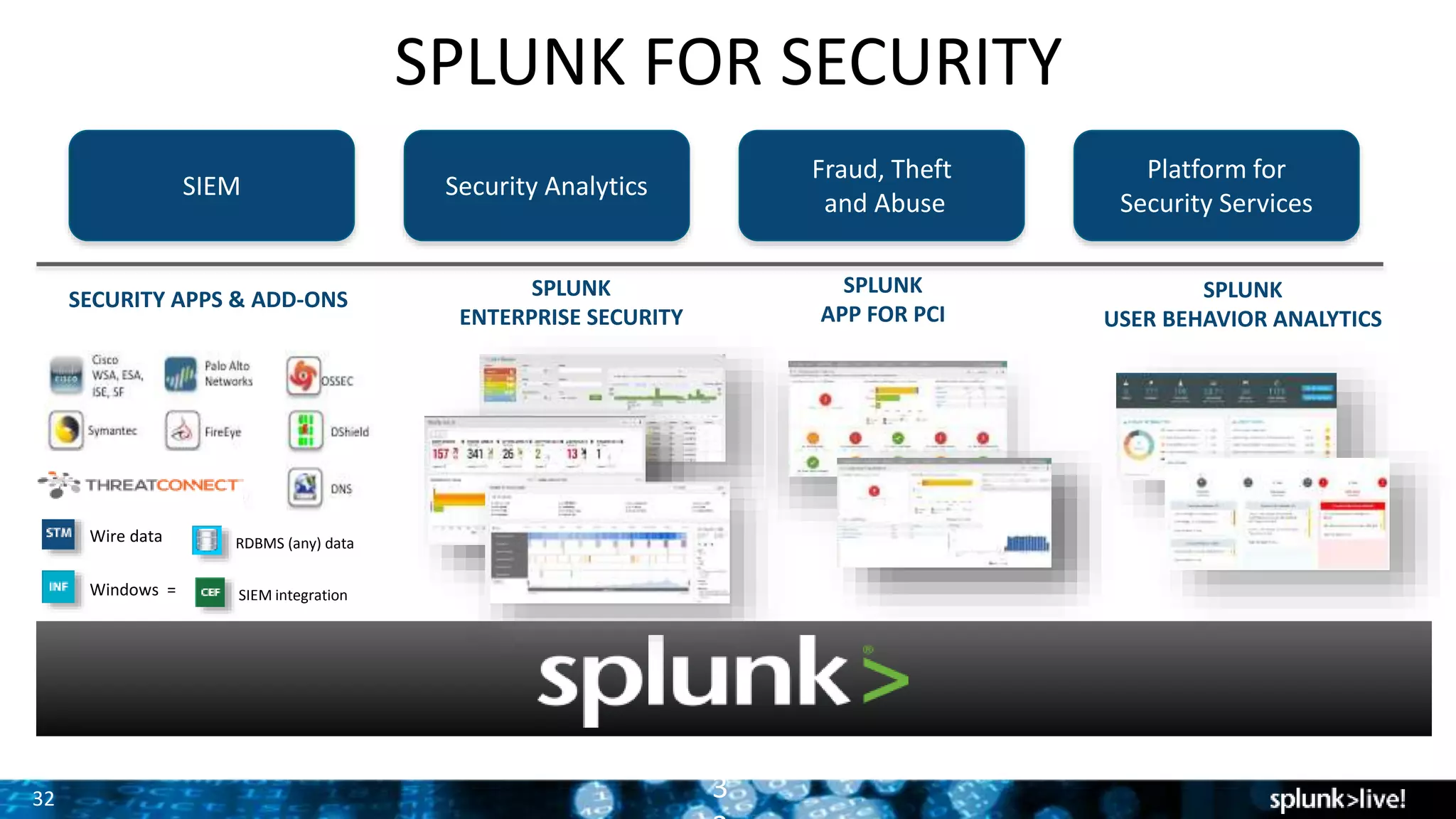
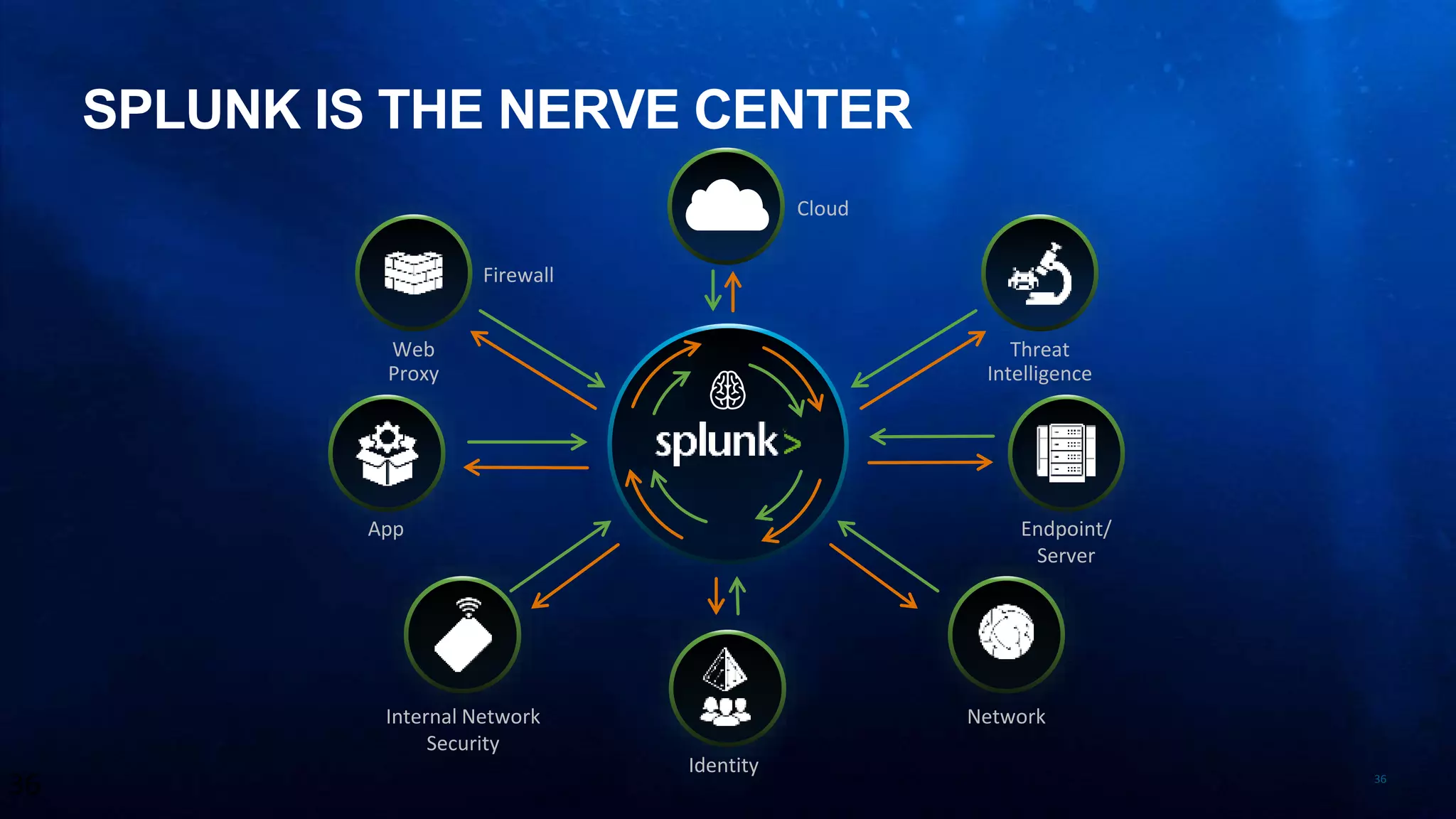
The presentation discusses the concept of security intelligence, which involves processes, policies, and tools for protecting organizations from internal and external threats. It emphasizes the need for risk-based analytics and integrating various data sources to enhance decision-making and strategic advantage. Additionally, it highlights the role of Splunk as a central platform for operationalizing security intelligence, facilitating real-time monitoring and incident investigations.