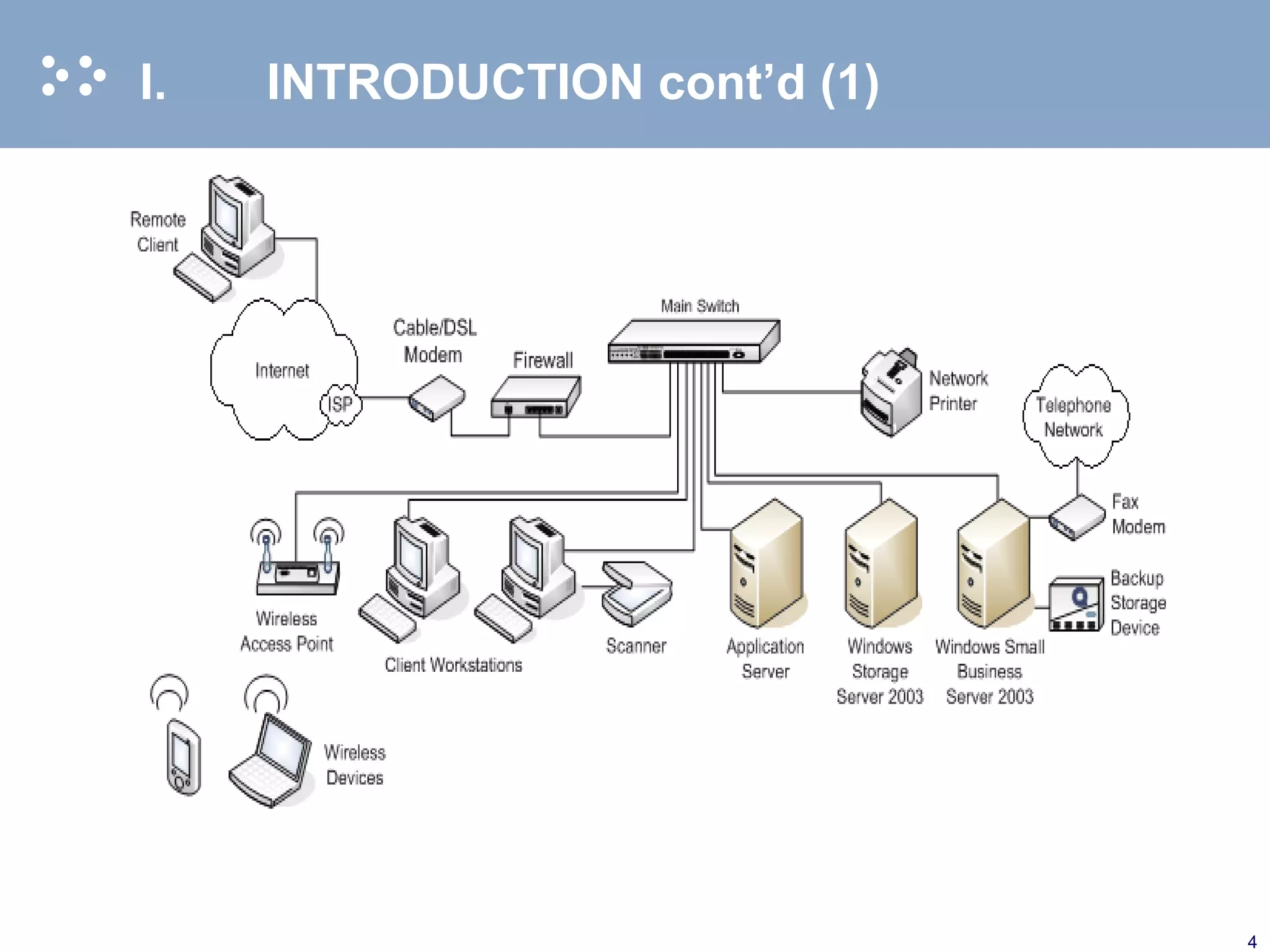
The document discusses the importance of records retention and destruction policies (RRDP) for compliance with statutory and contractual obligations, particularly in the context of increasing electronic data. It outlines the necessary steps for developing and managing an RRDP, including assessing current practices, establishing policies, and ensuring proper implementation. The document also highlights the implications of improper document management in terms of litigation risks and e-discovery processes.


















![II.C Appropriate Document Destruction cont’d 2. Spoliation – Canadian Case Law : Brandon Heating & Plumbing (1972) Ltd. v. Max Systems Inc., [2006] M.J. No. 149 (Q.B.): Claim based or purchase of allegedly faulty accounting software Defendant requires access to operating systems and processors where software installed for defence Plaintiff undertakes to preserve the hardware and disks and to make them available for inspection After three years and a number of inquiries from defendant, plaintiff said that hardware had been replaced. Court found failure to preserve hardware and disks amounted to spoliation and dismissed plaintiff’s action](https://image.slidesharecdn.com/recordsretentionanddestructionpolicies-12699817962681-phpapp02/75/Records-Retention-And-Destruction-Policies-22-2048.jpg)













![IV. Litigation and e-Discovery cont`d Proportionality cont’d: Dulong v. Consumer Packaging Inc. [2000] O.J. No. 161 (S.C.J.): Plaintiff asks “if there are emails in existence which relate to the matters in issue in this litigation”. Court indicates, on plaintiff’s motion to compel answers, that it was: “ too much like fishing and would, having regard to the extent of the defendant’s business, be such a massive undertaking as to be oppressive.”](https://image.slidesharecdn.com/recordsretentionanddestructionpolicies-12699817962681-phpapp02/75/Records-Retention-And-Destruction-Policies-37-2048.jpg)
![IV. Litigation and e-Discovery cont`d Proportionality cont’d: CIBC World Markets Inc. v. Genuity Capital Markets , [2005] O.J. No. 614 (S.C.J.): Forensic consultant granted: “ access for imaging and storing in a safe manner the contents of computers, Blackberries and other types of similar electronic devices of every nature and kind as to which the defendants have in their possession, power, ownership, use or control, directly and indirectly.” (emphasis added) Order extended to devices located at any office, home or elsewhere, regardless of whether the devices owned or used by others. Defendants required to certify they had not used the services of other persons / other electronic devices to send or receive messages (and that they had not deleted records).](https://image.slidesharecdn.com/recordsretentionanddestructionpolicies-12699817962681-phpapp02/75/Records-Retention-And-Destruction-Policies-38-2048.jpg)