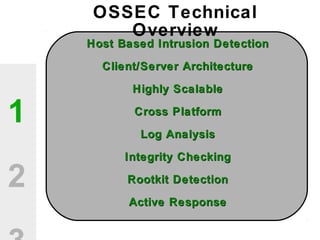
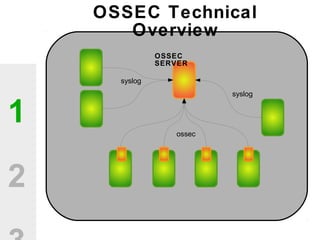
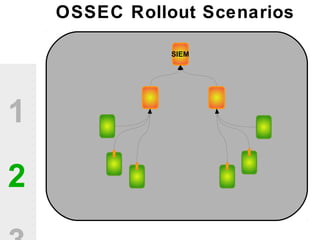
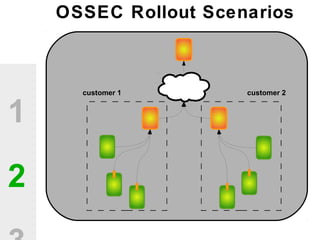
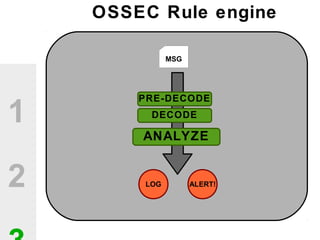
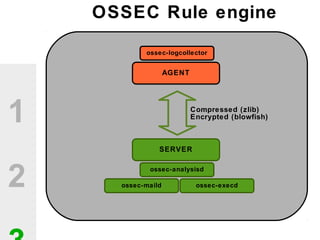
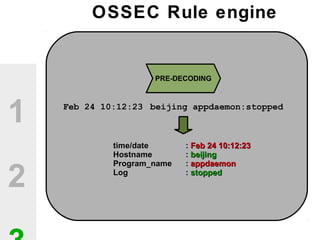
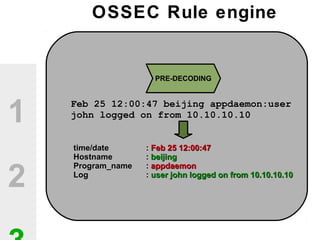
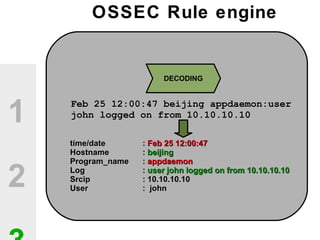
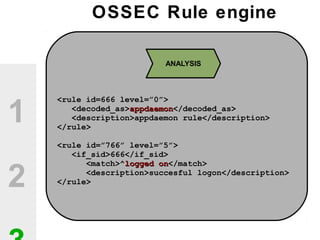
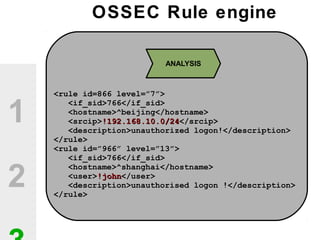
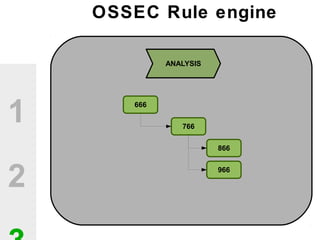
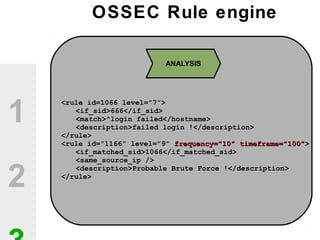
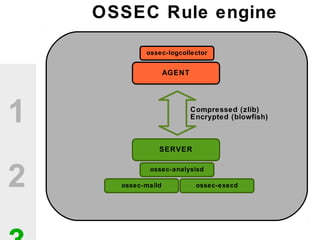
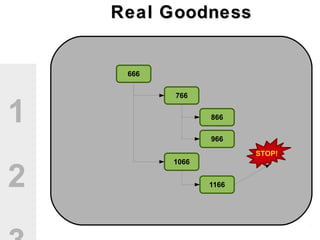
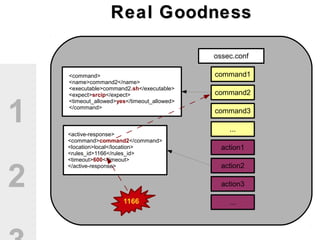
The document discusses the value of open source solutions in security infrastructure, particularly focusing on OSSEC, a host-based intrusion detection system. It highlights various features of OSSEC such as log analysis, integrity checking, rootkit detection, and the flexibility of its rule engine. The text includes technical details, rollout scenarios, and examples of rules for analyzing log data to detect unauthorized access and potential security threats.