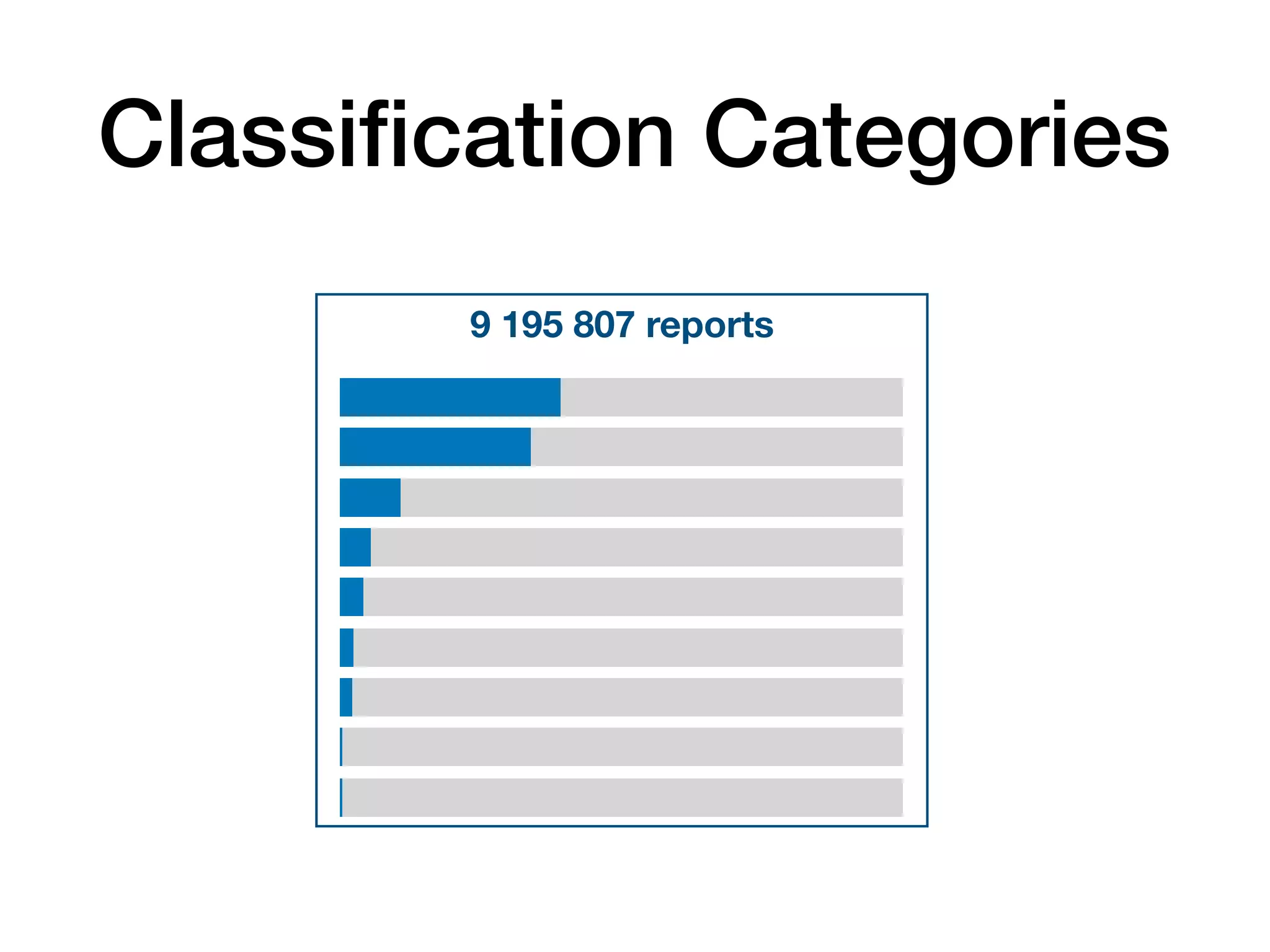
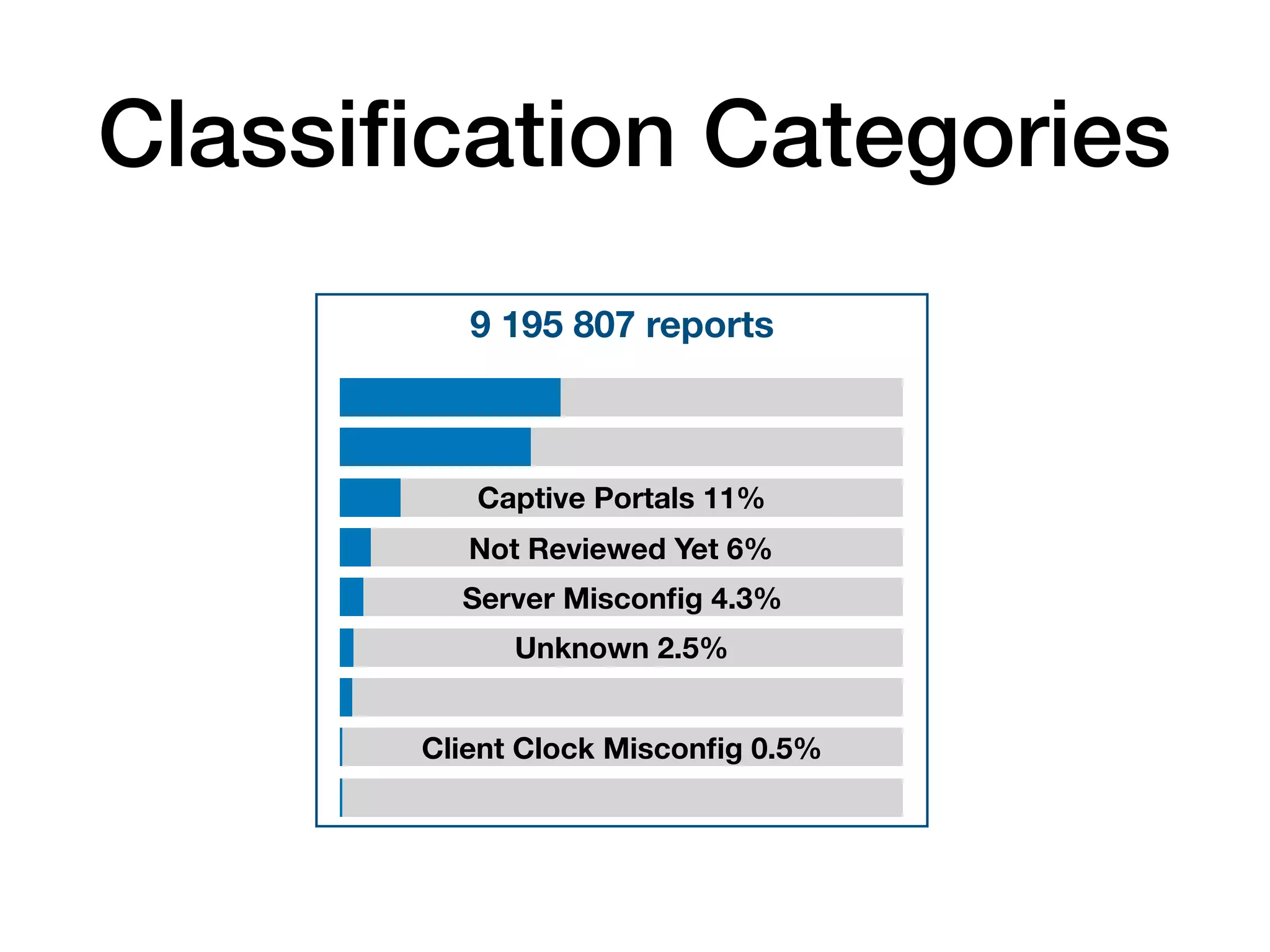
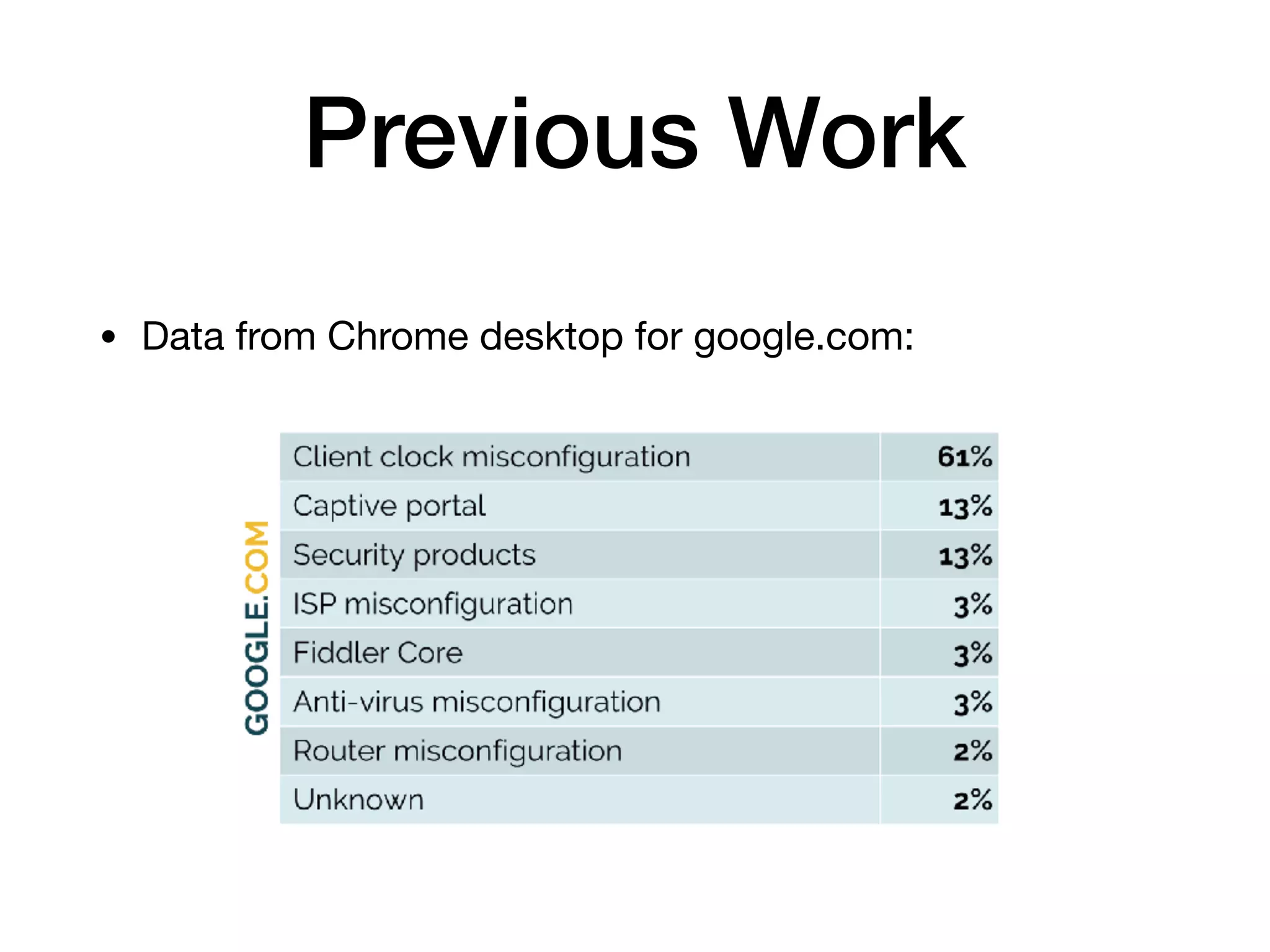
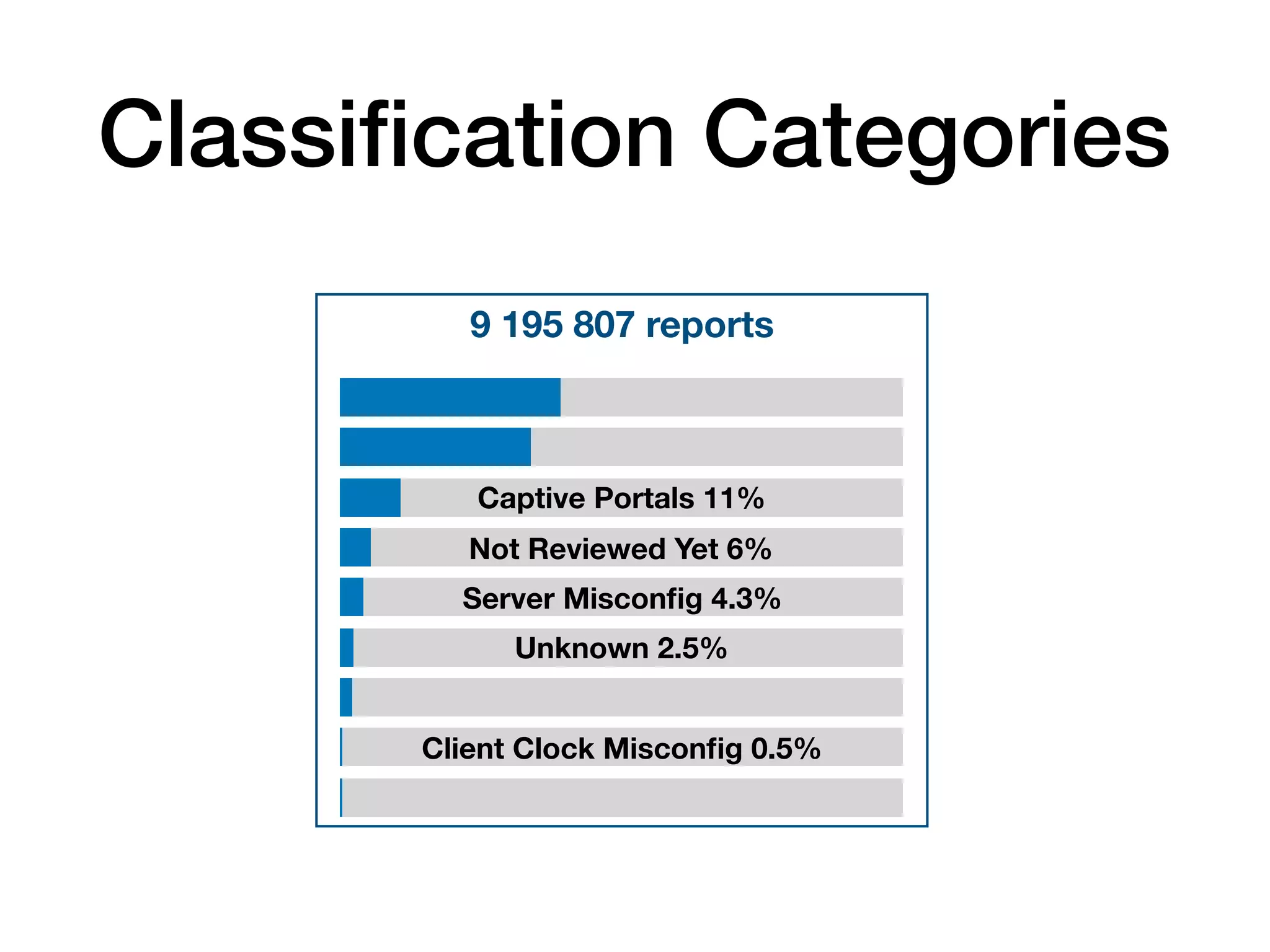
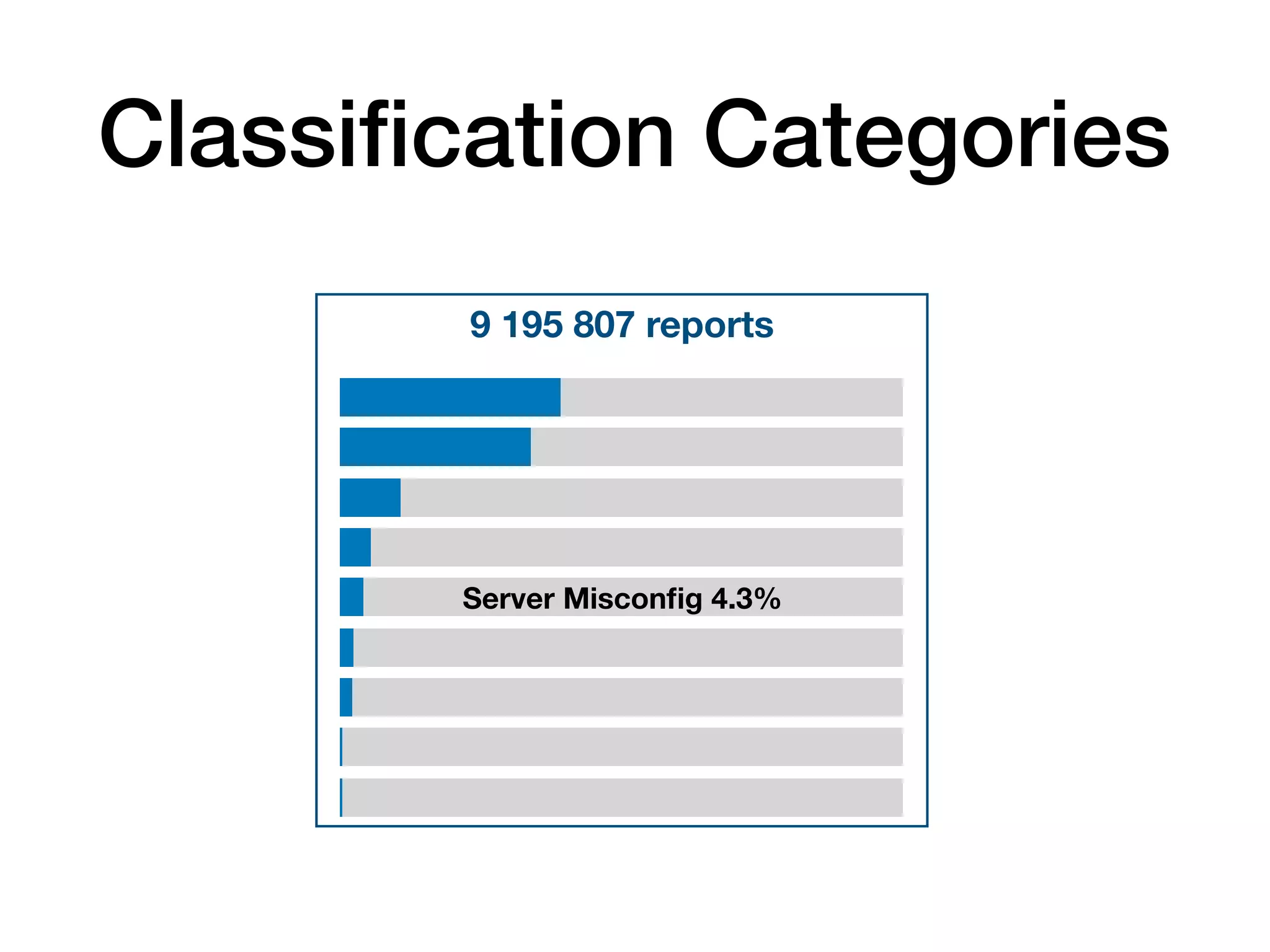
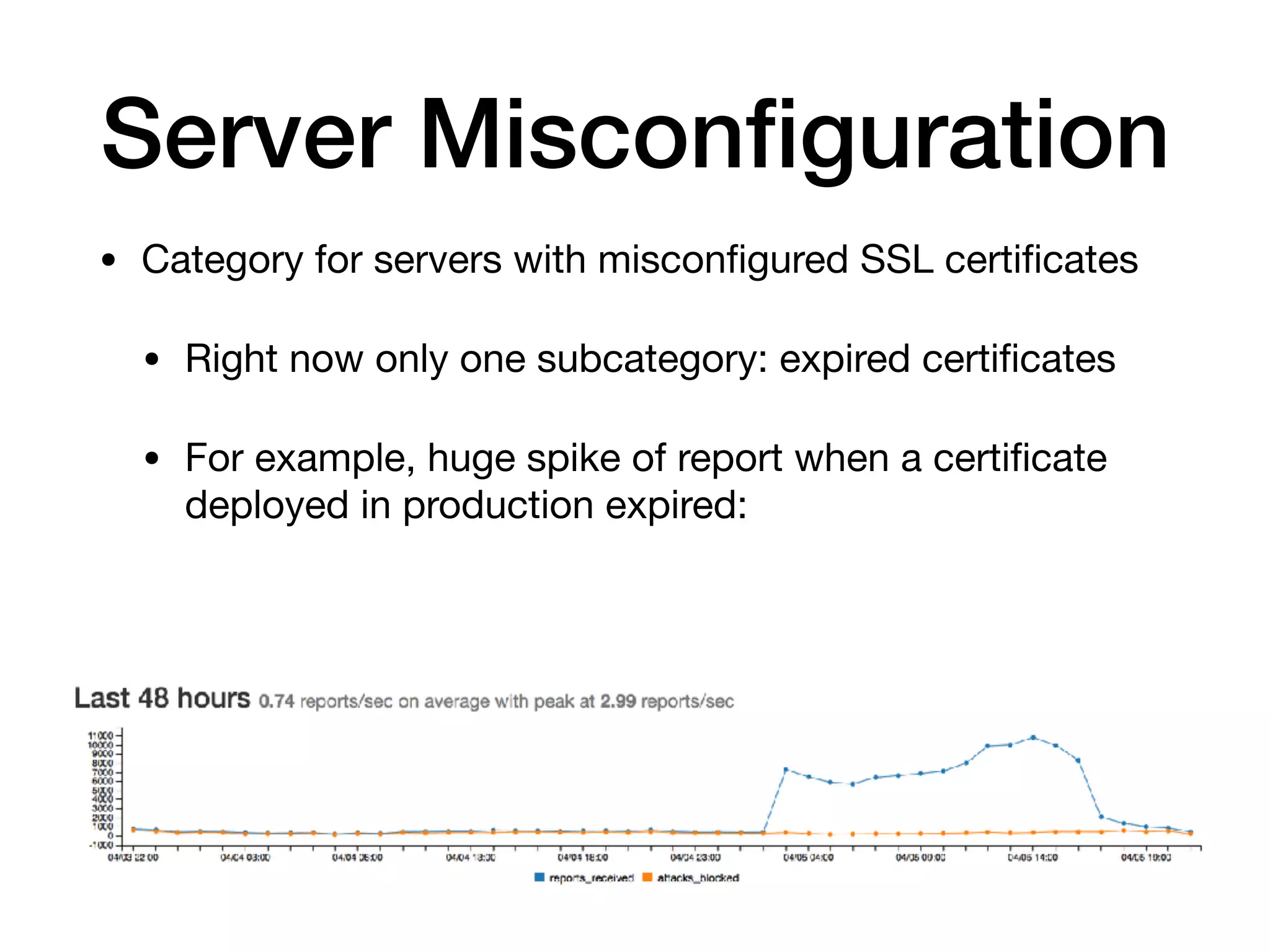
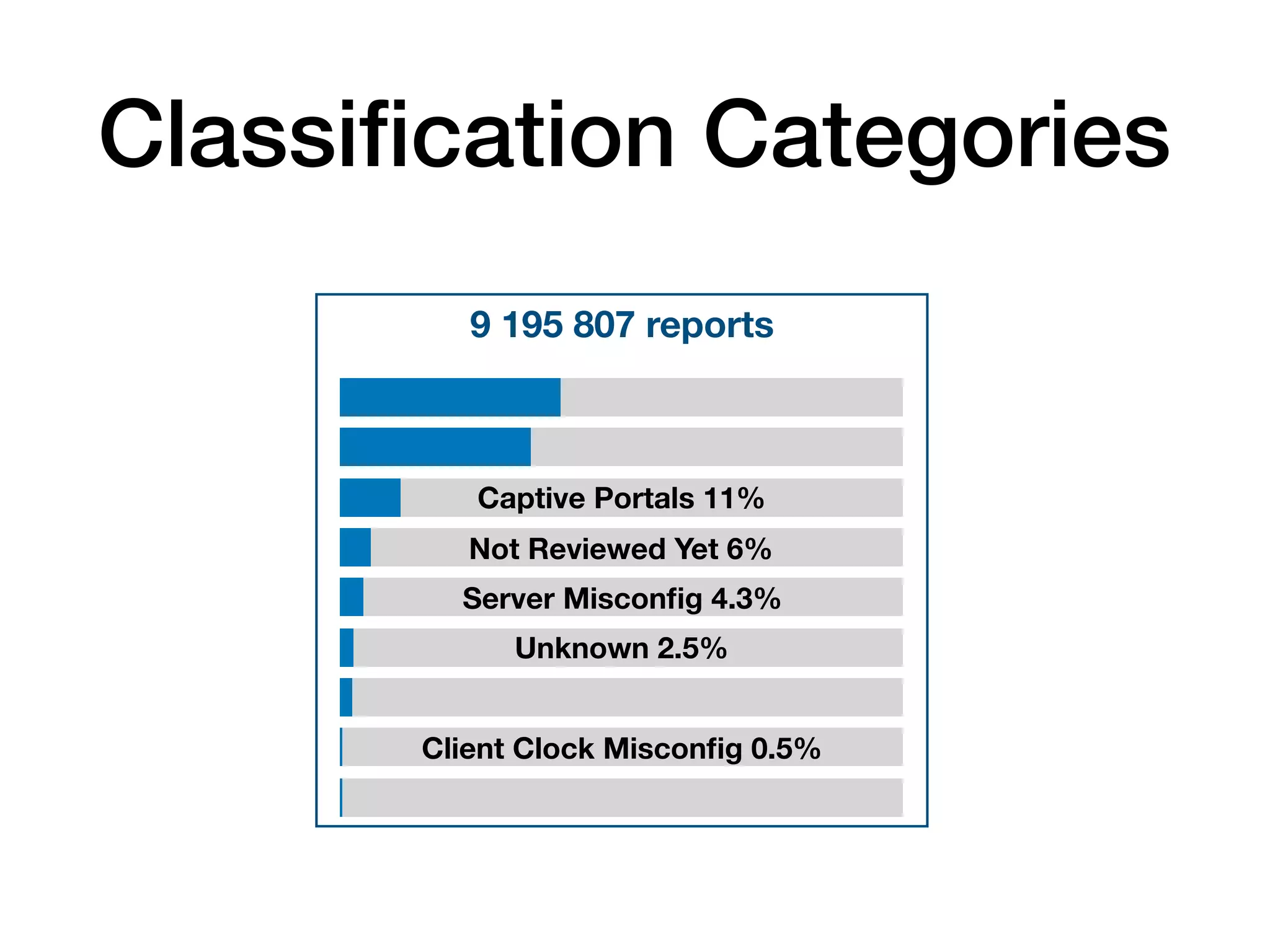
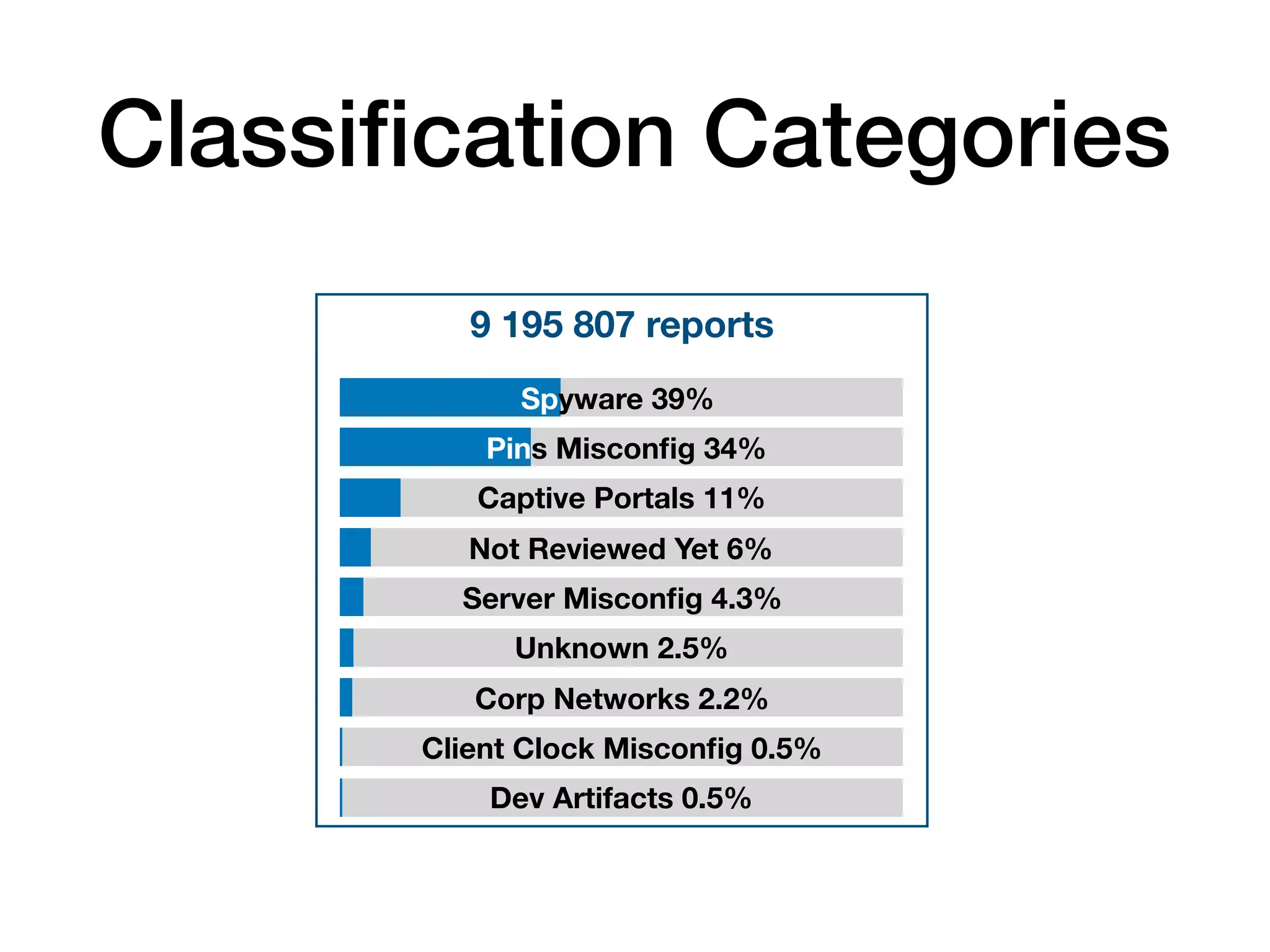
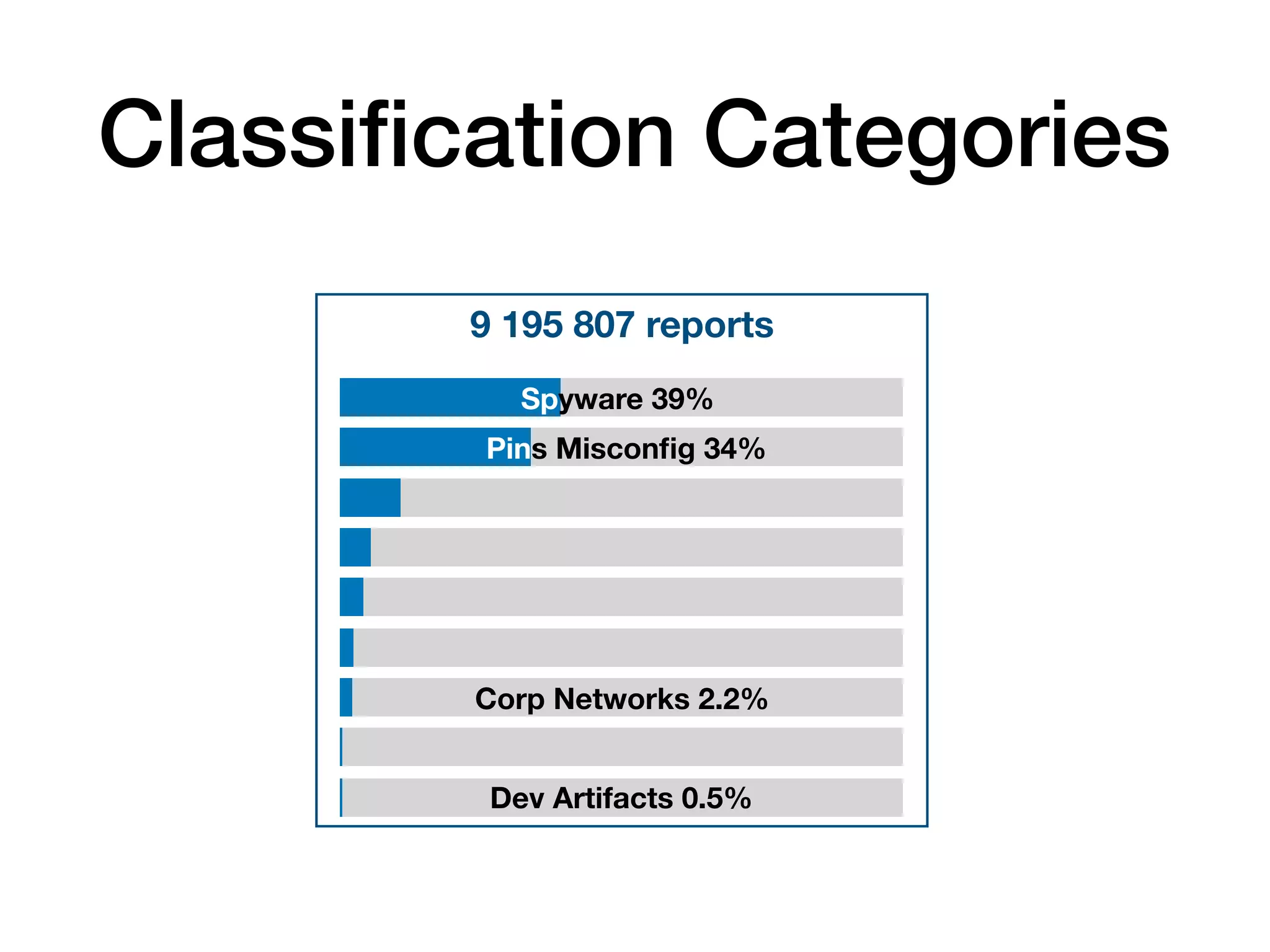
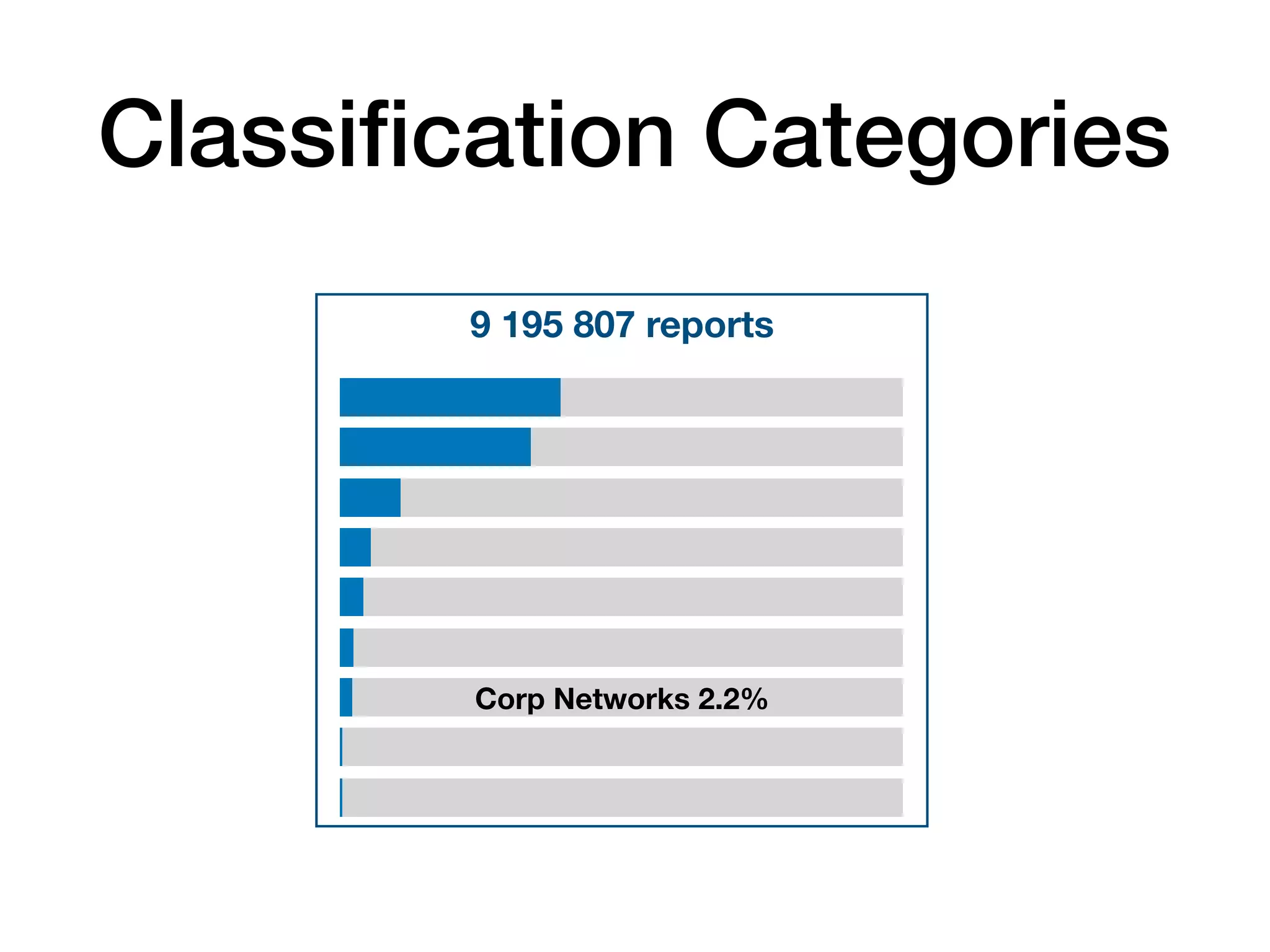
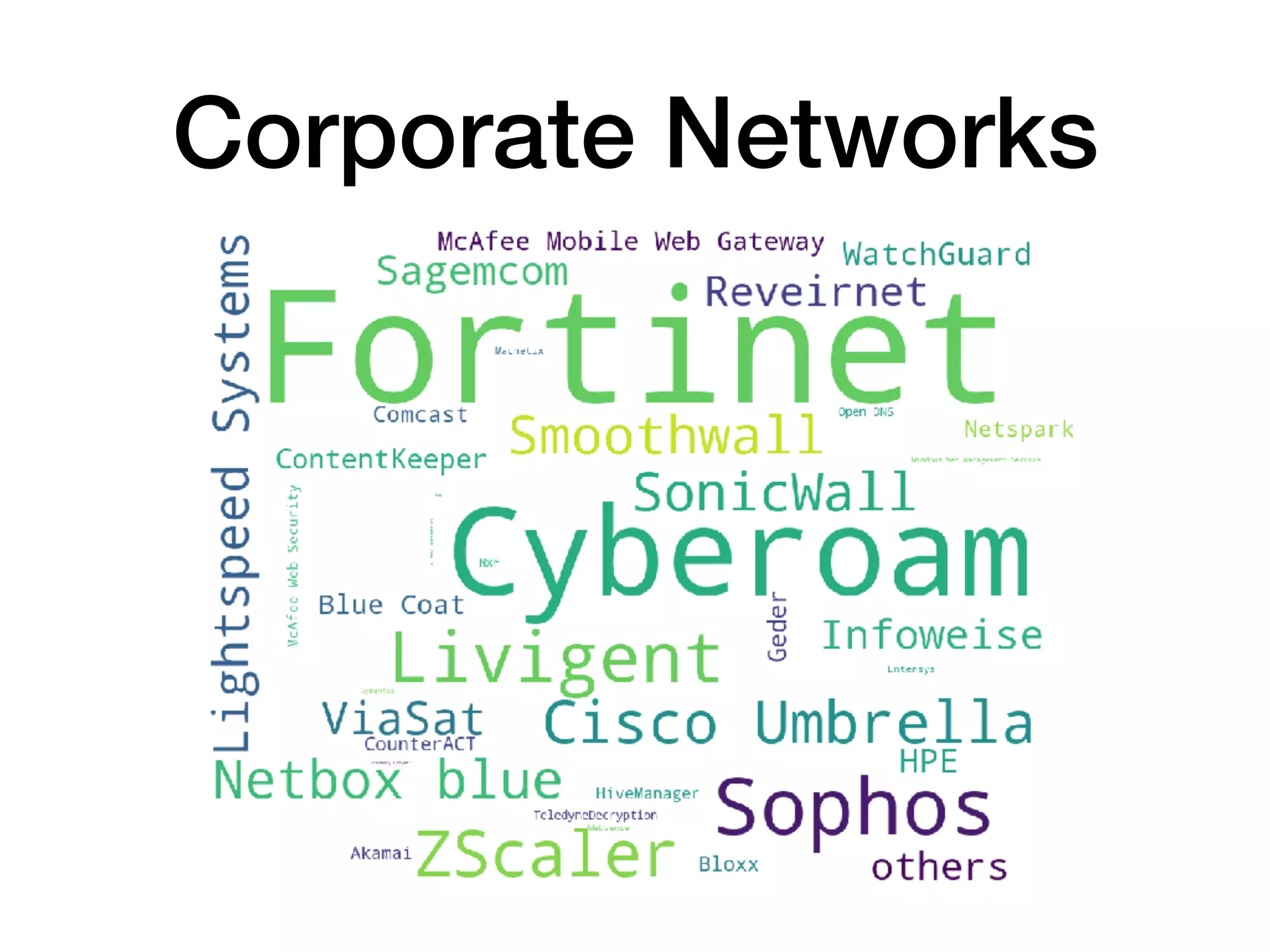
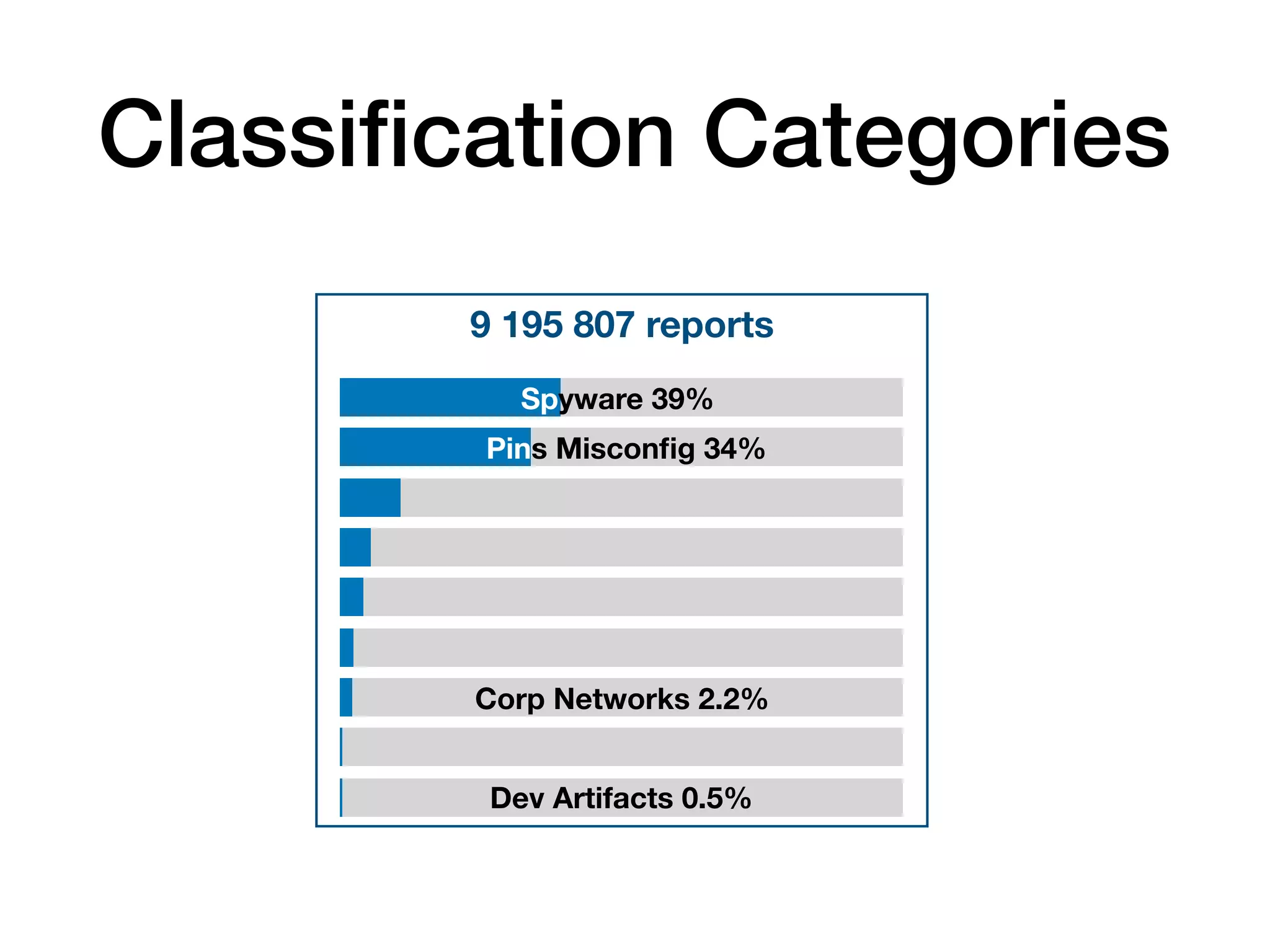
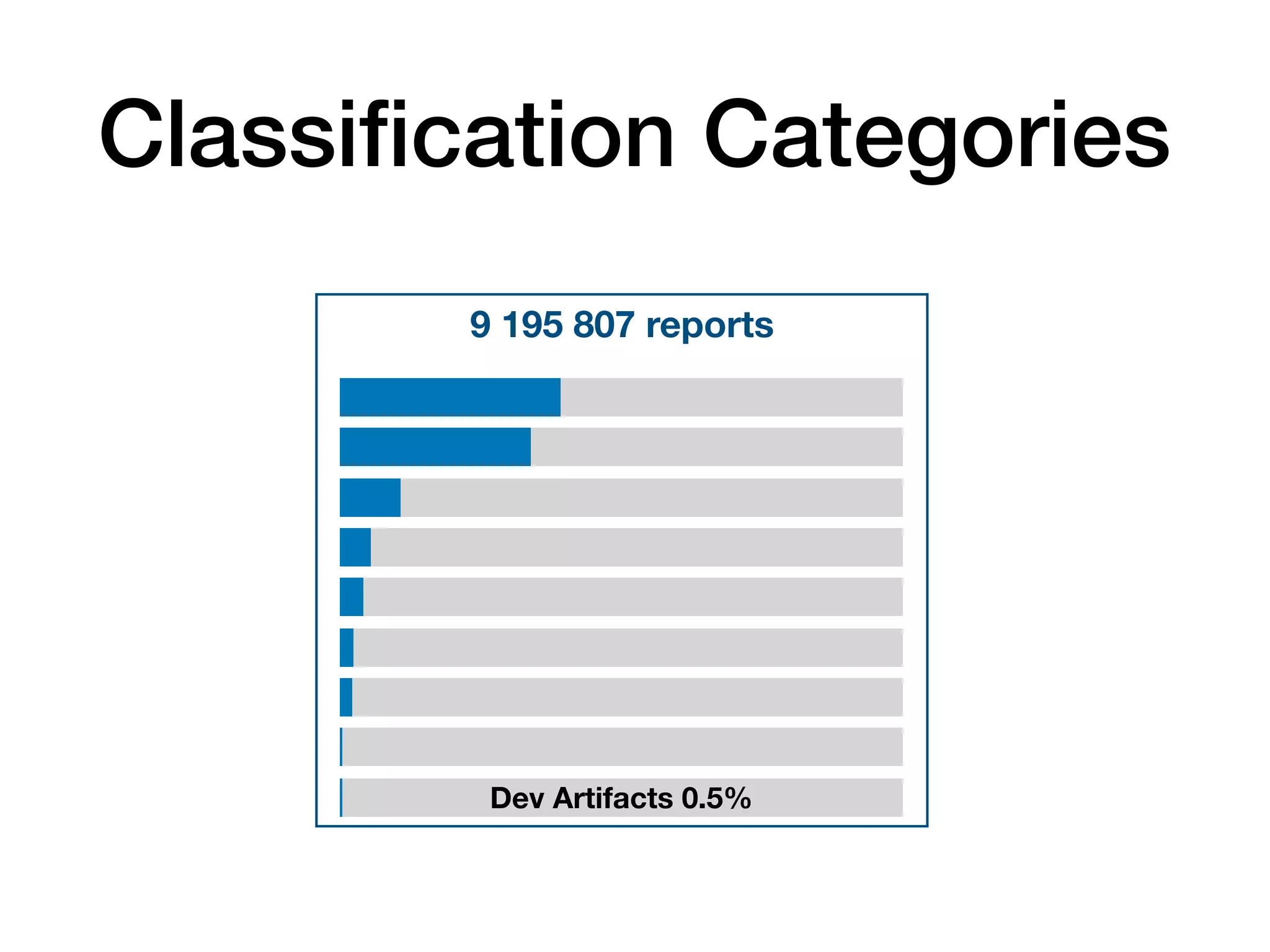
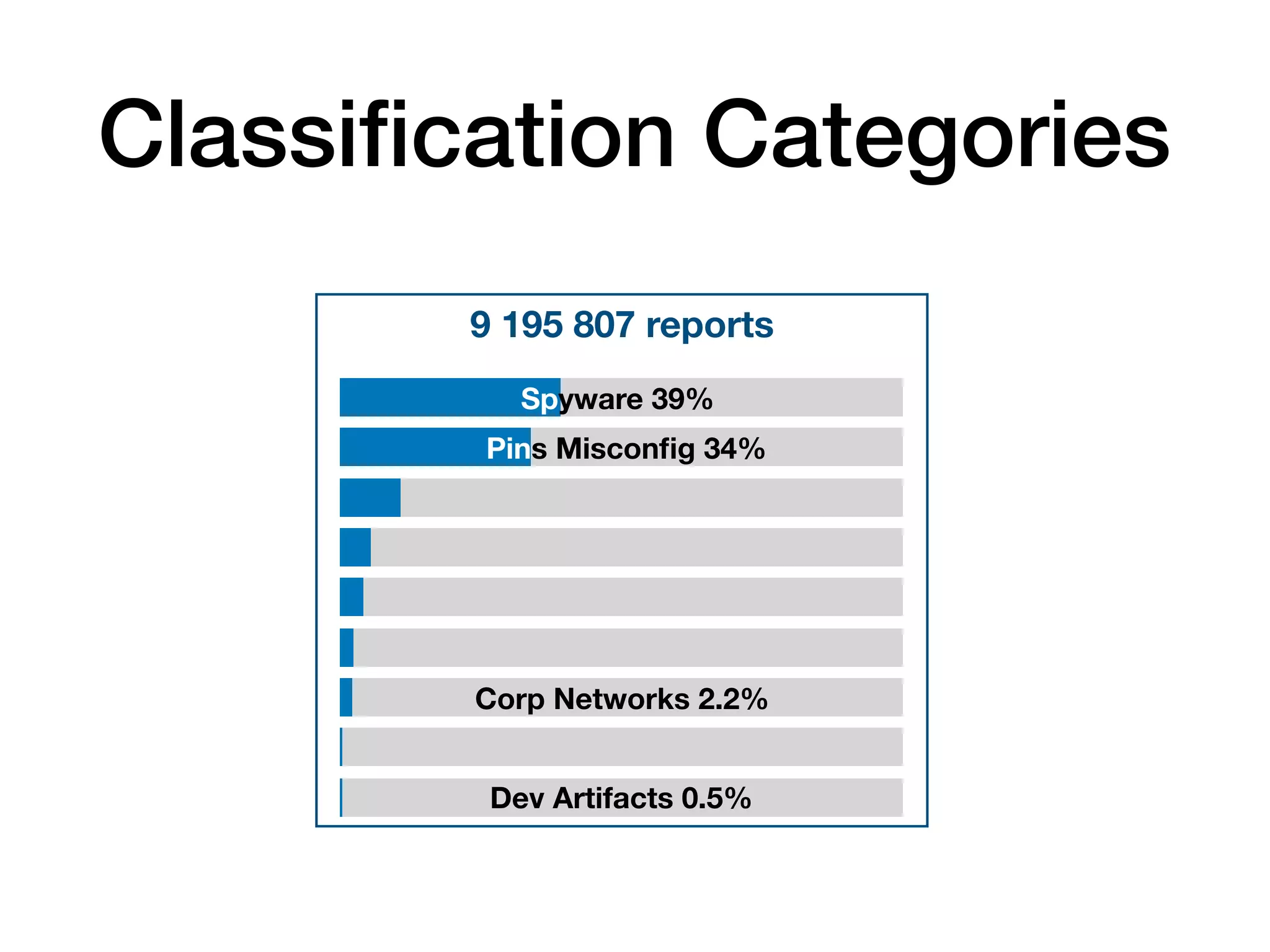
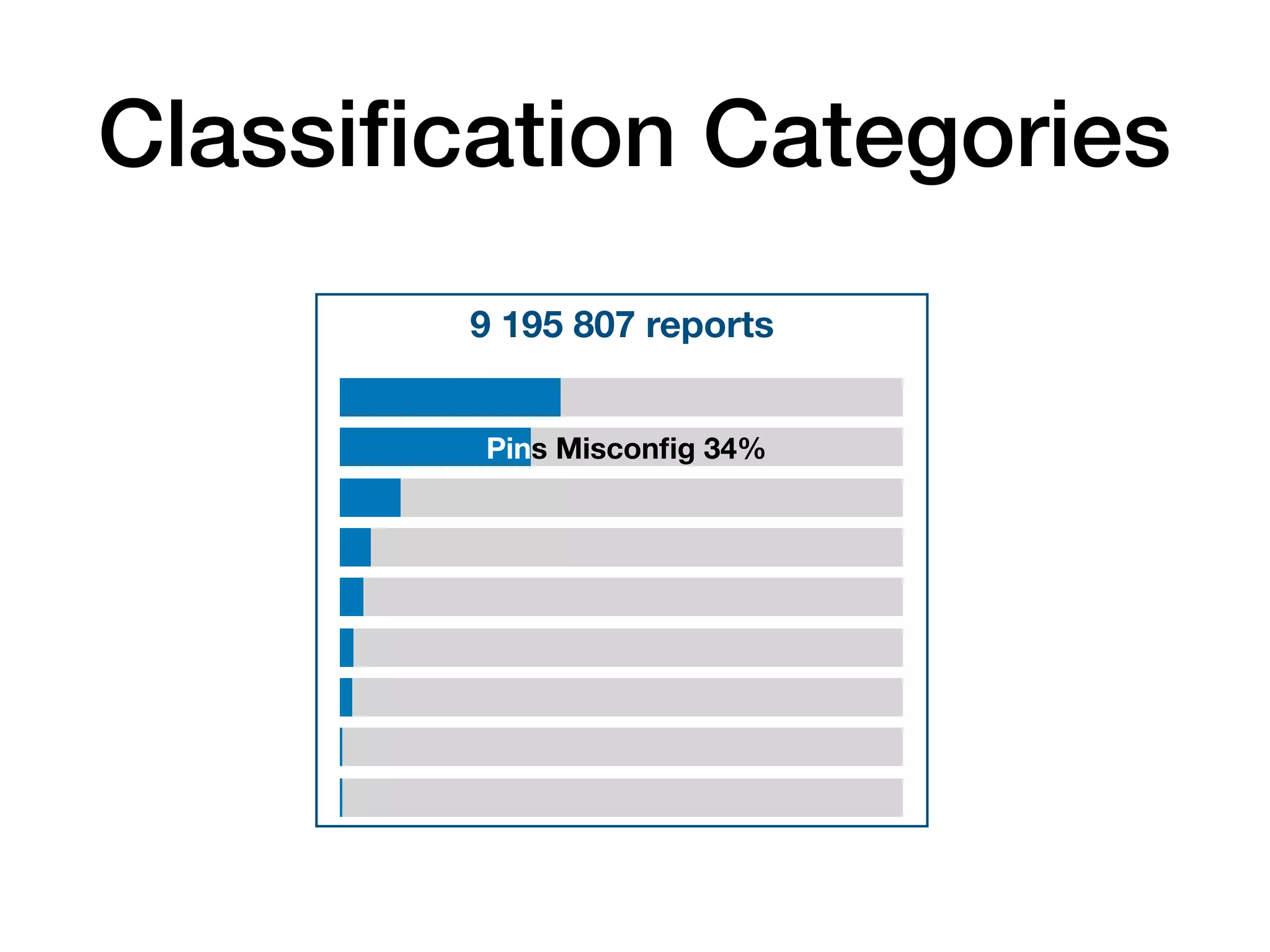
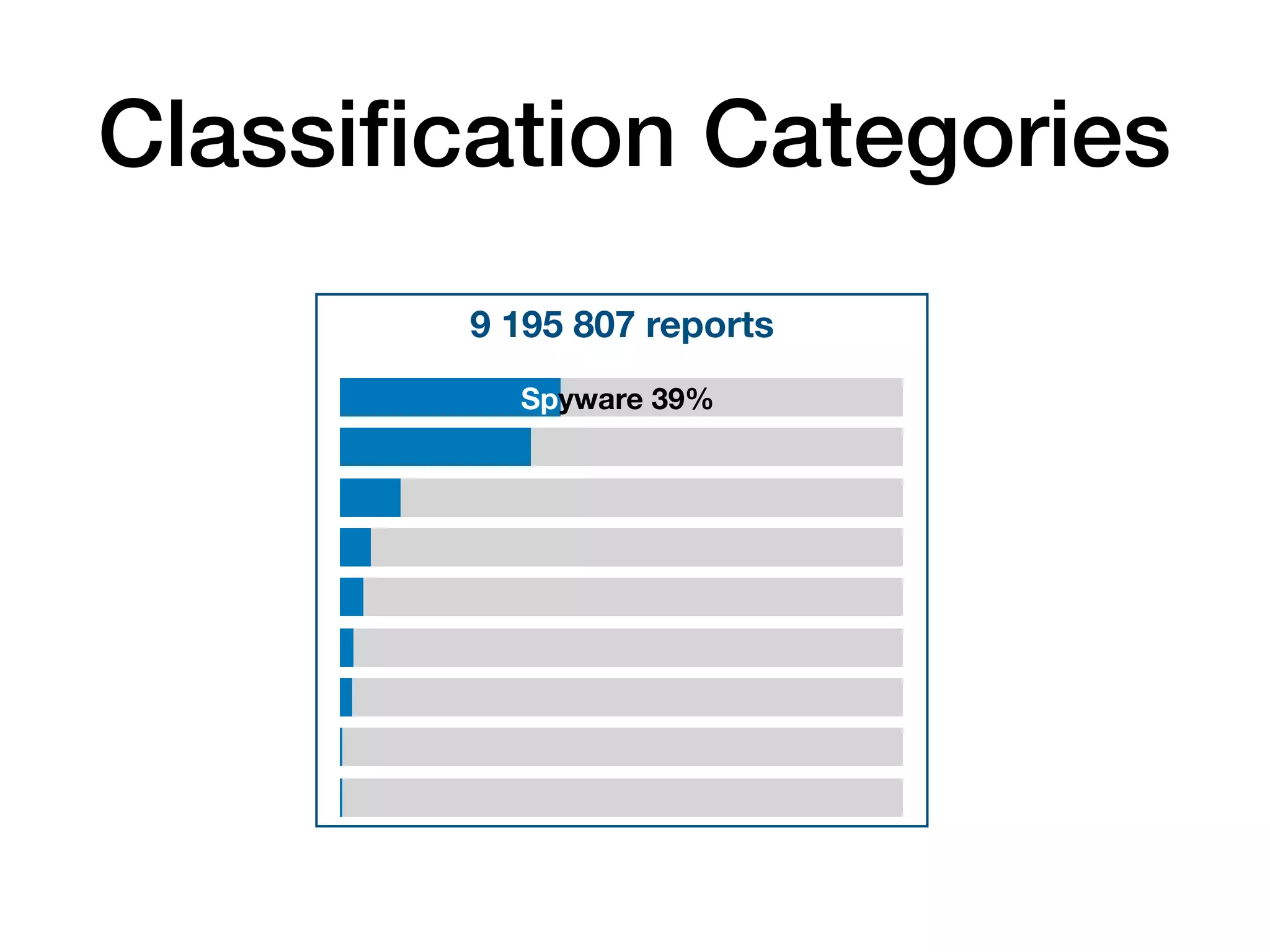
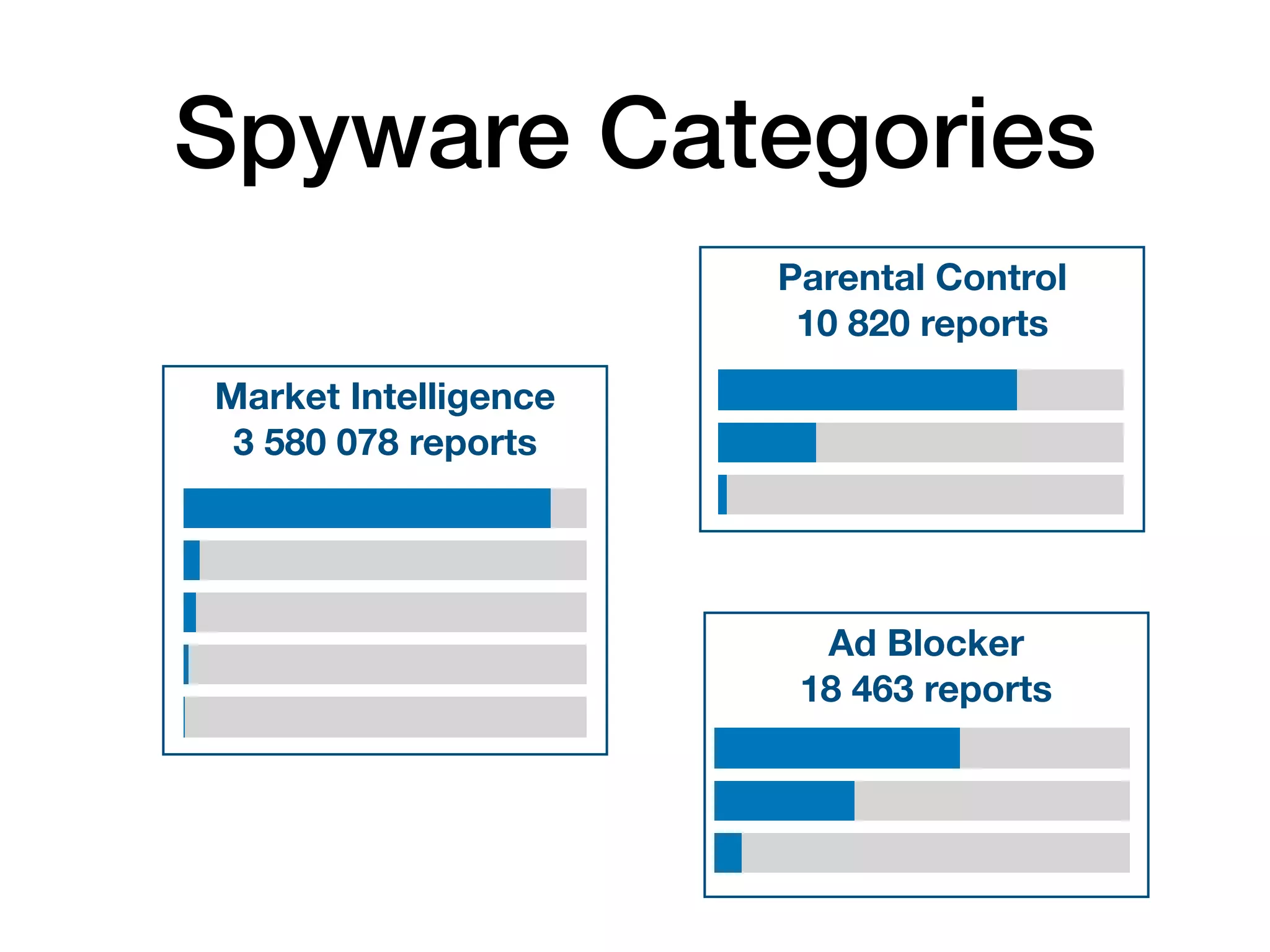
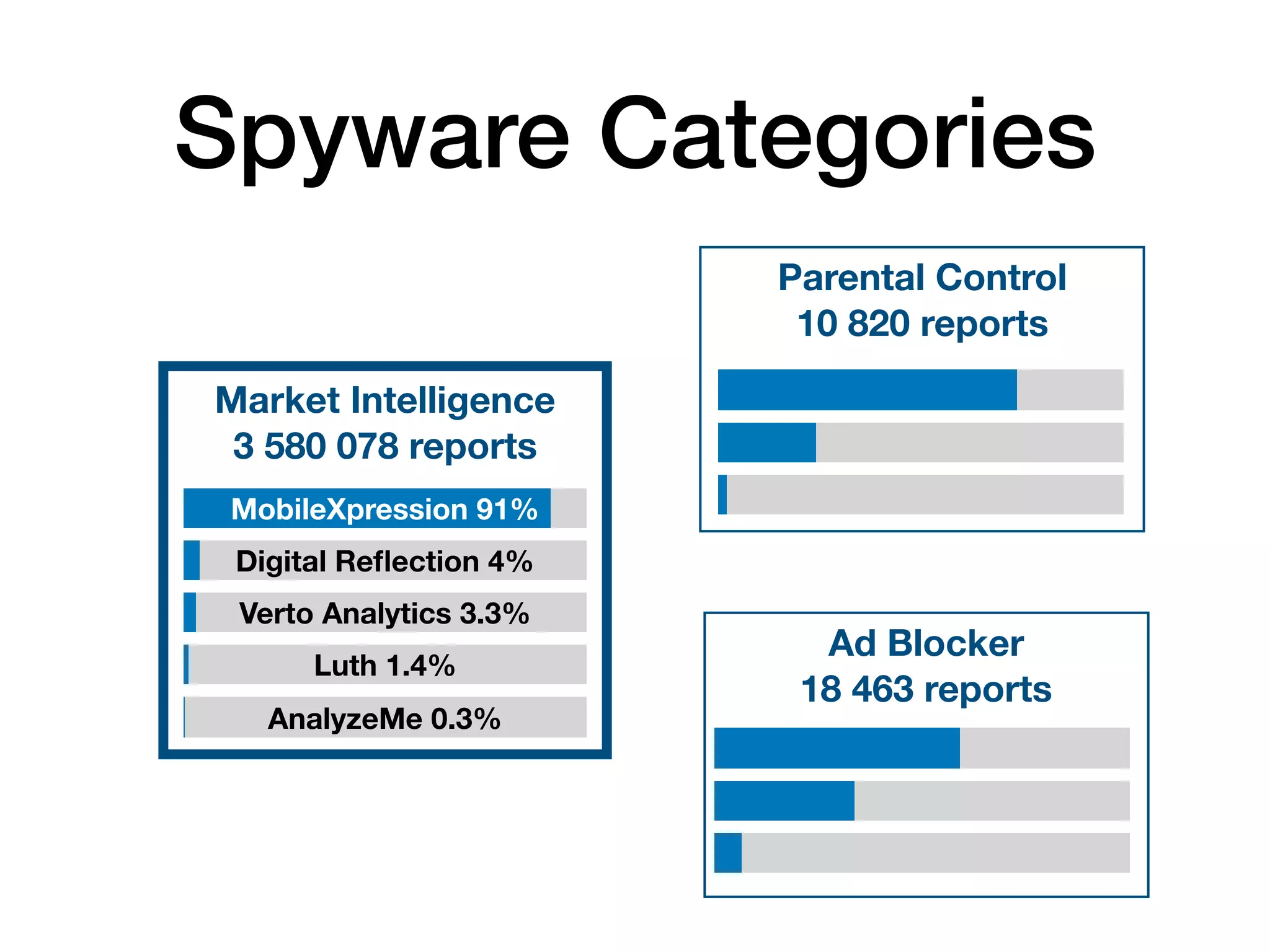
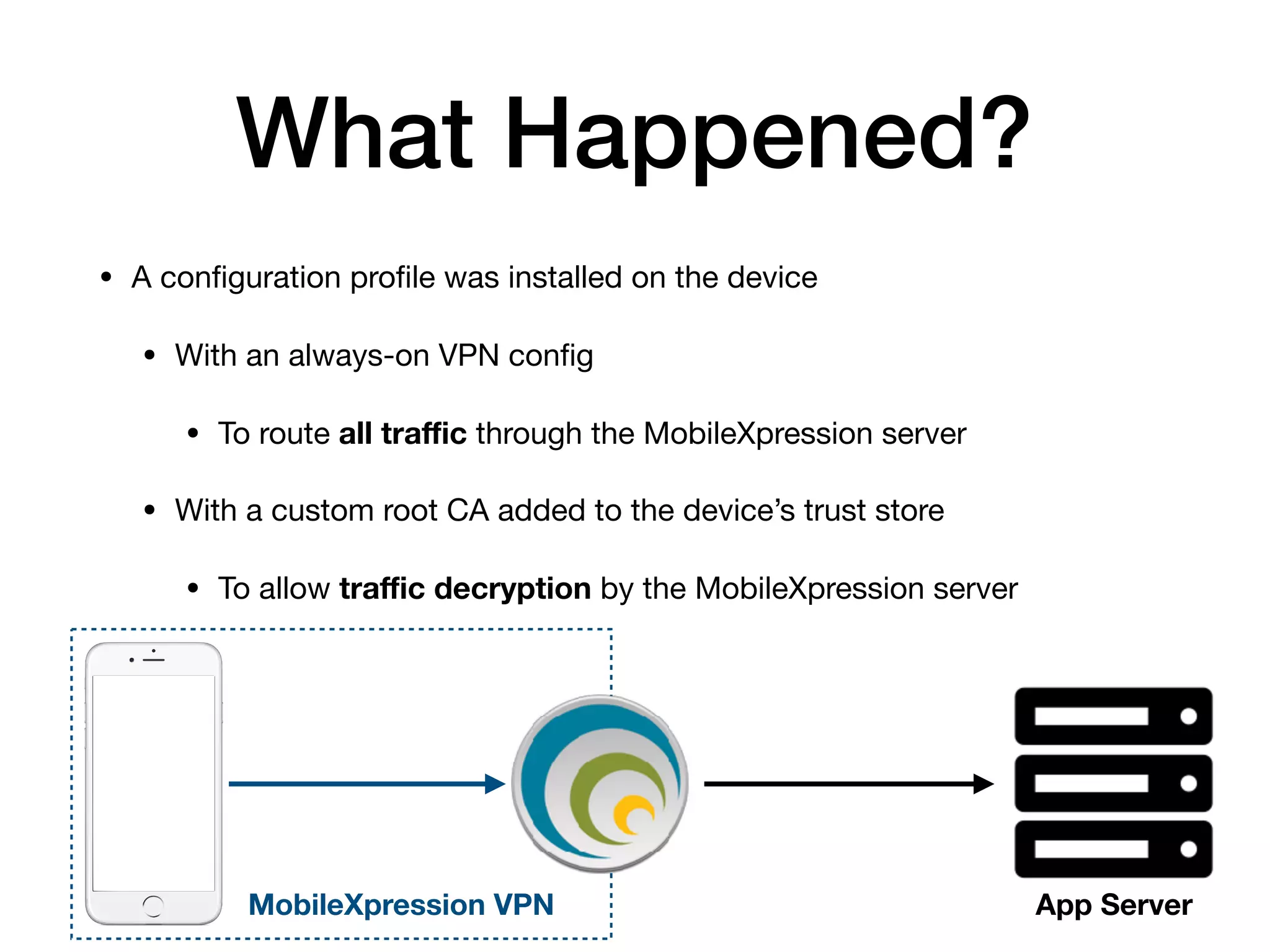
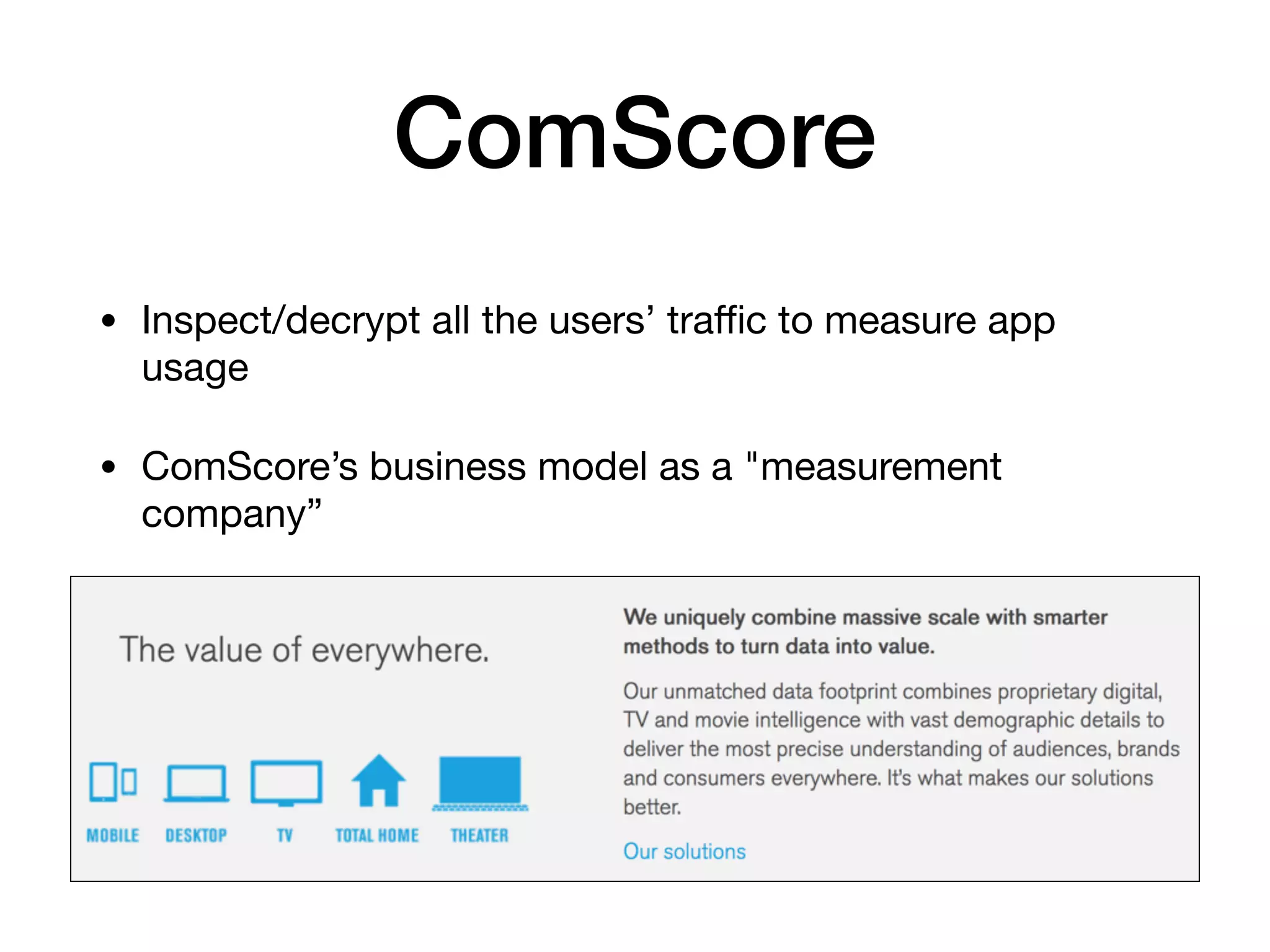
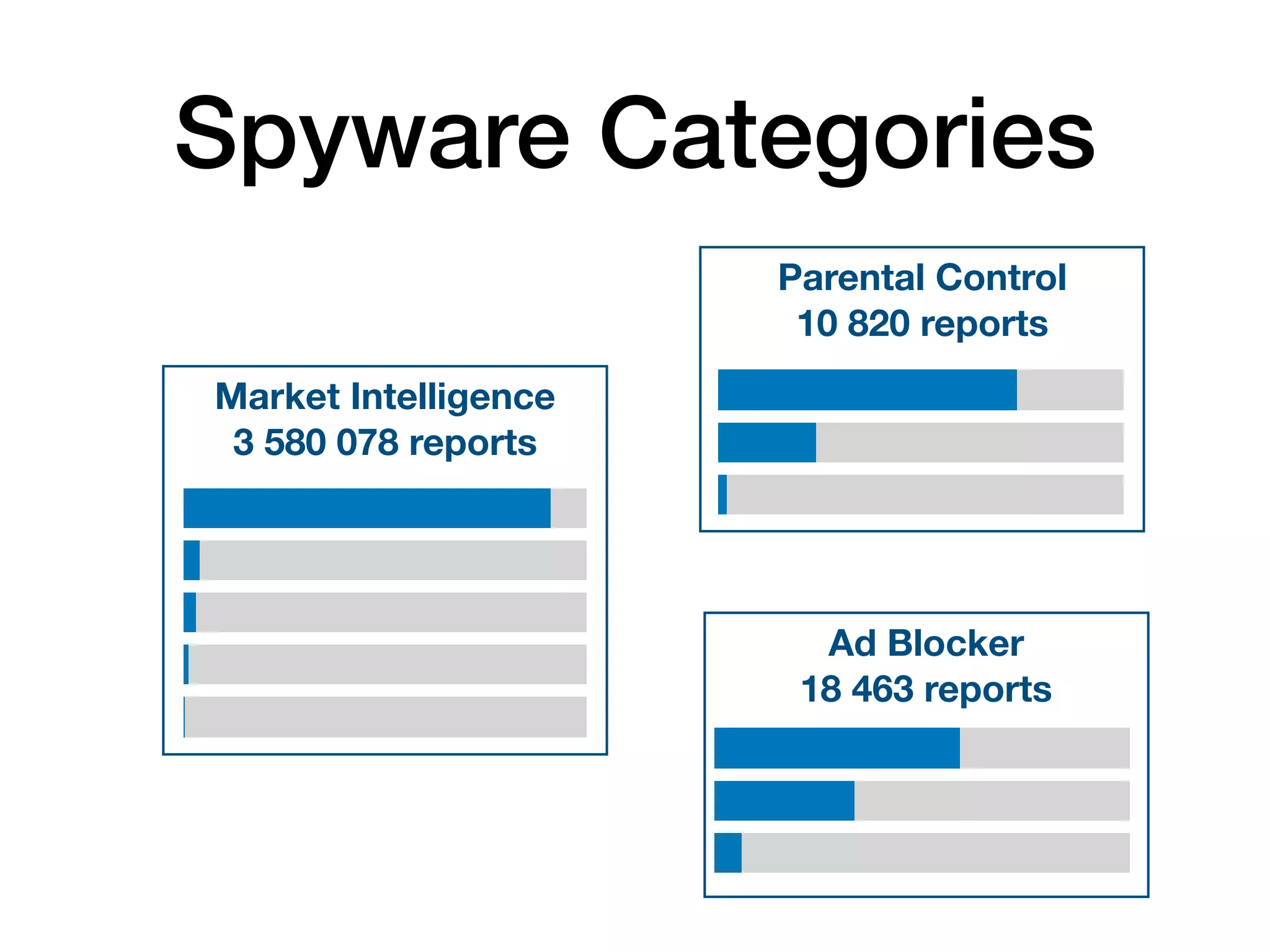
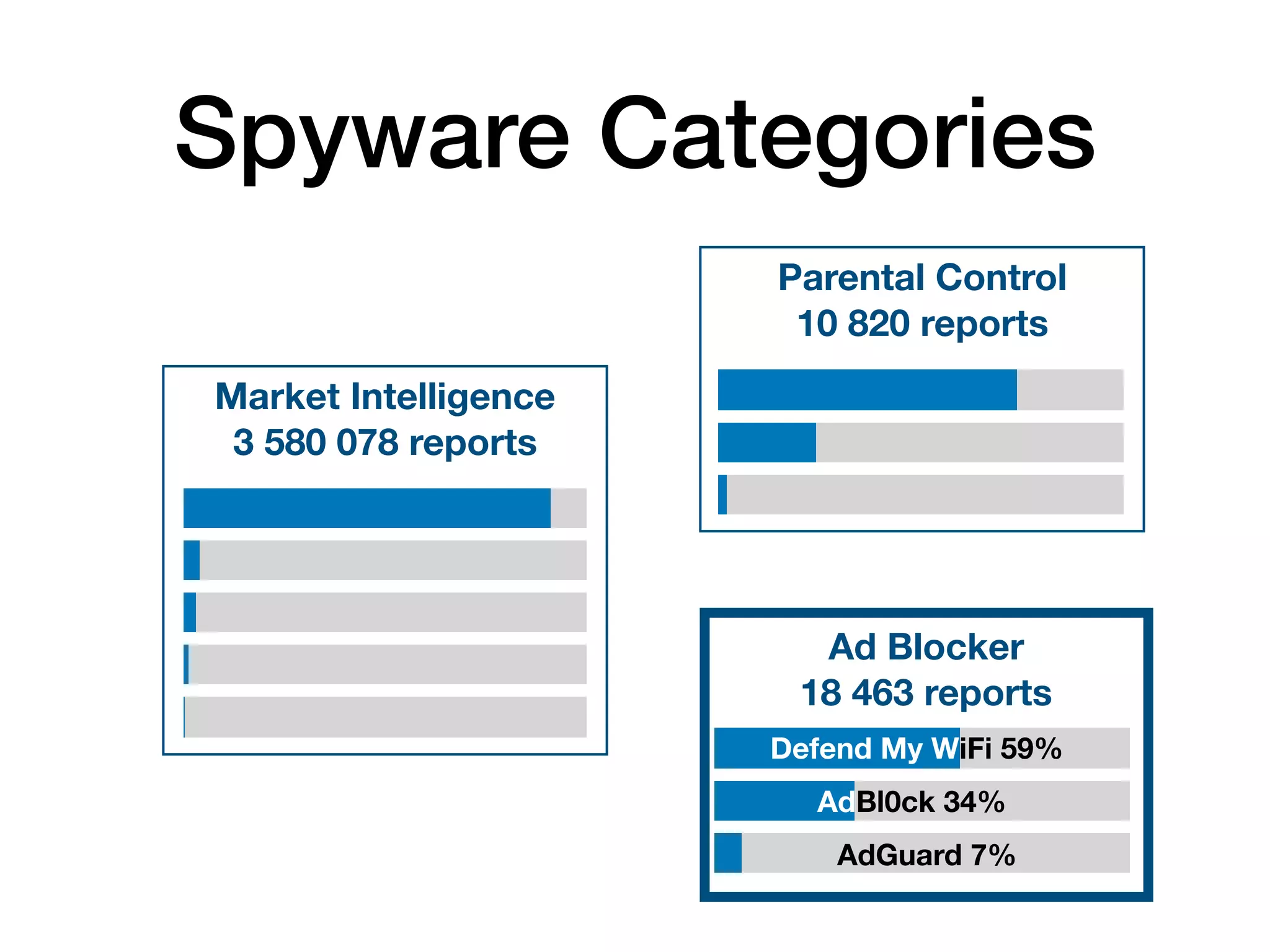
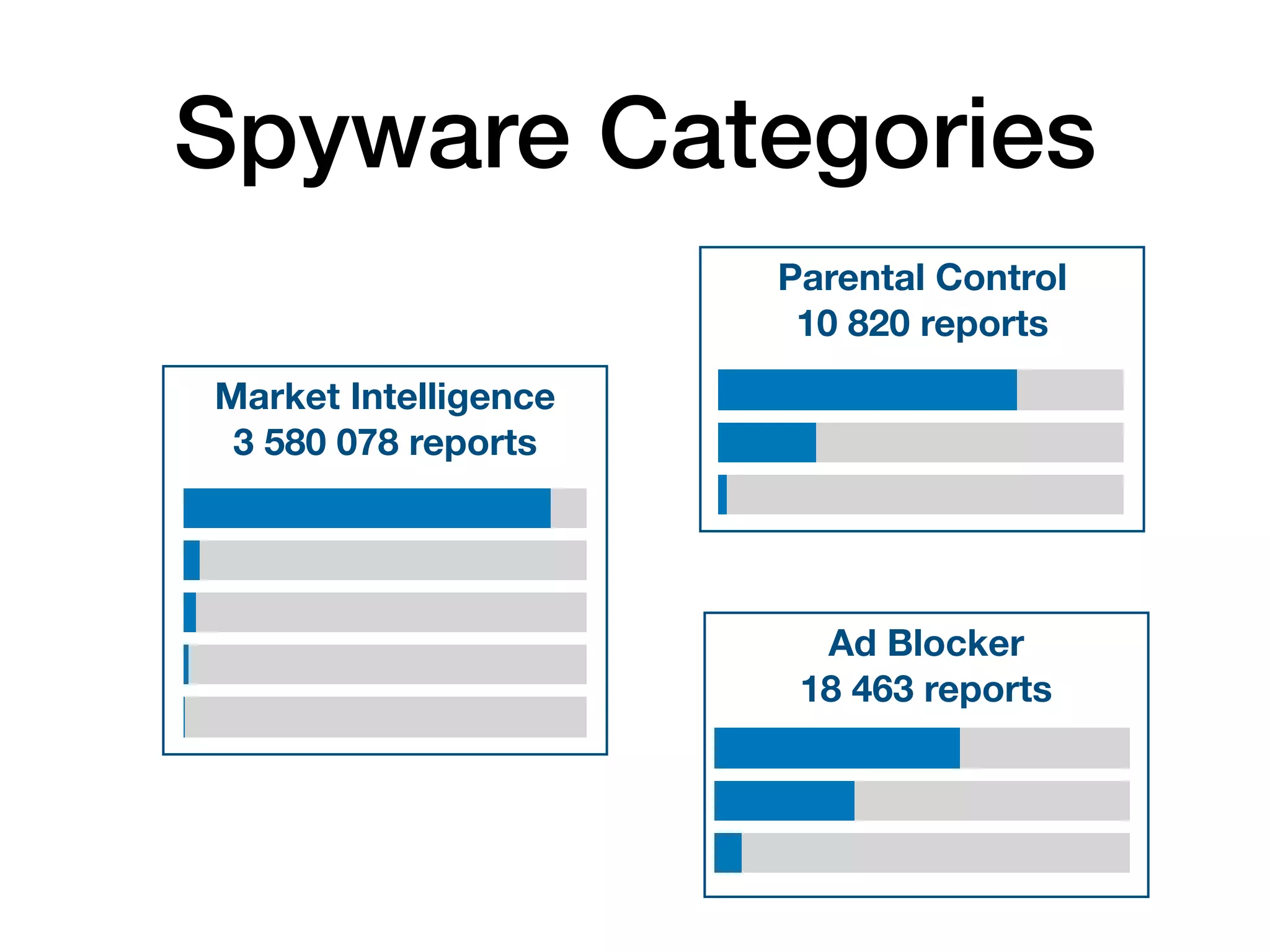
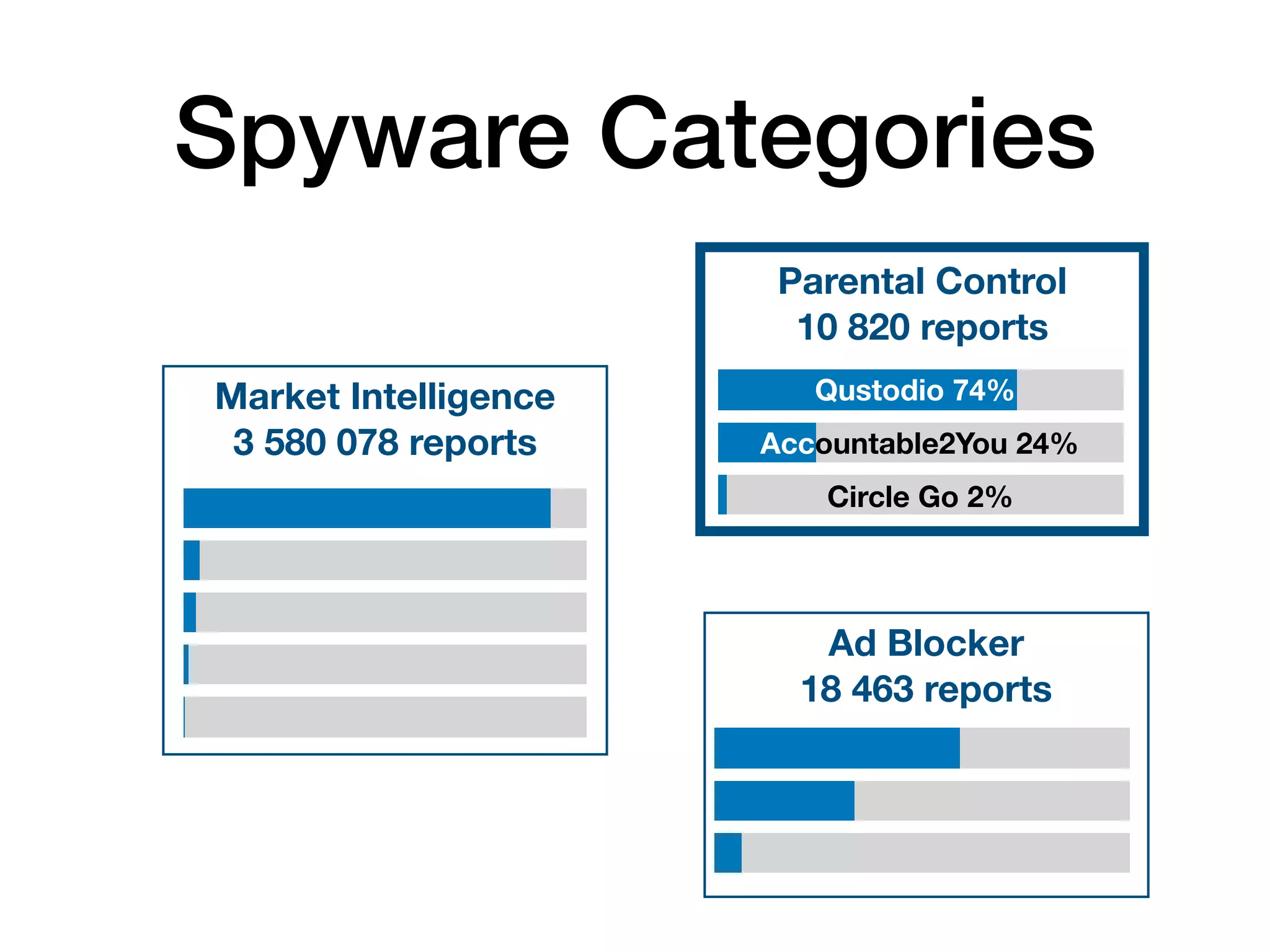
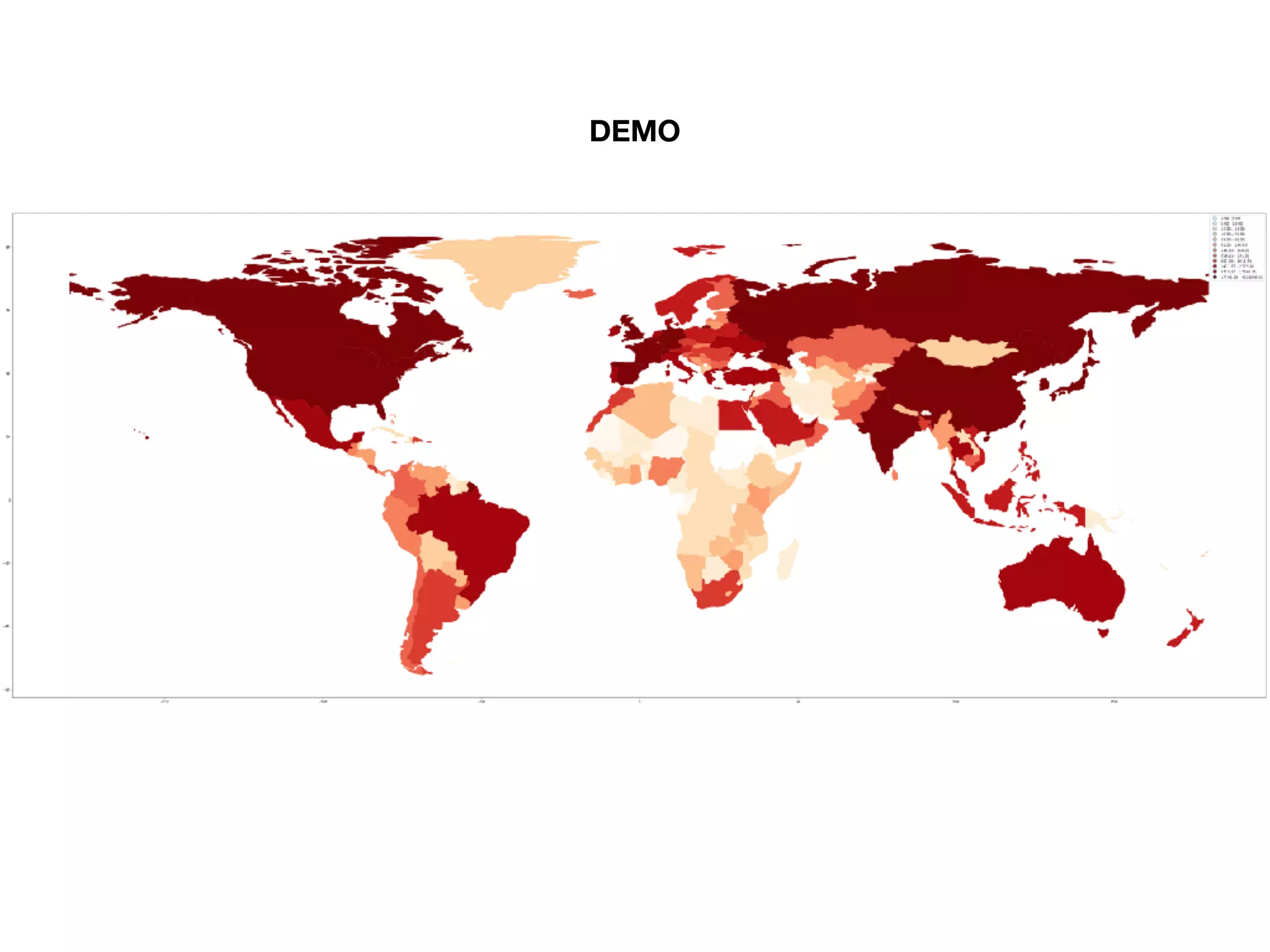
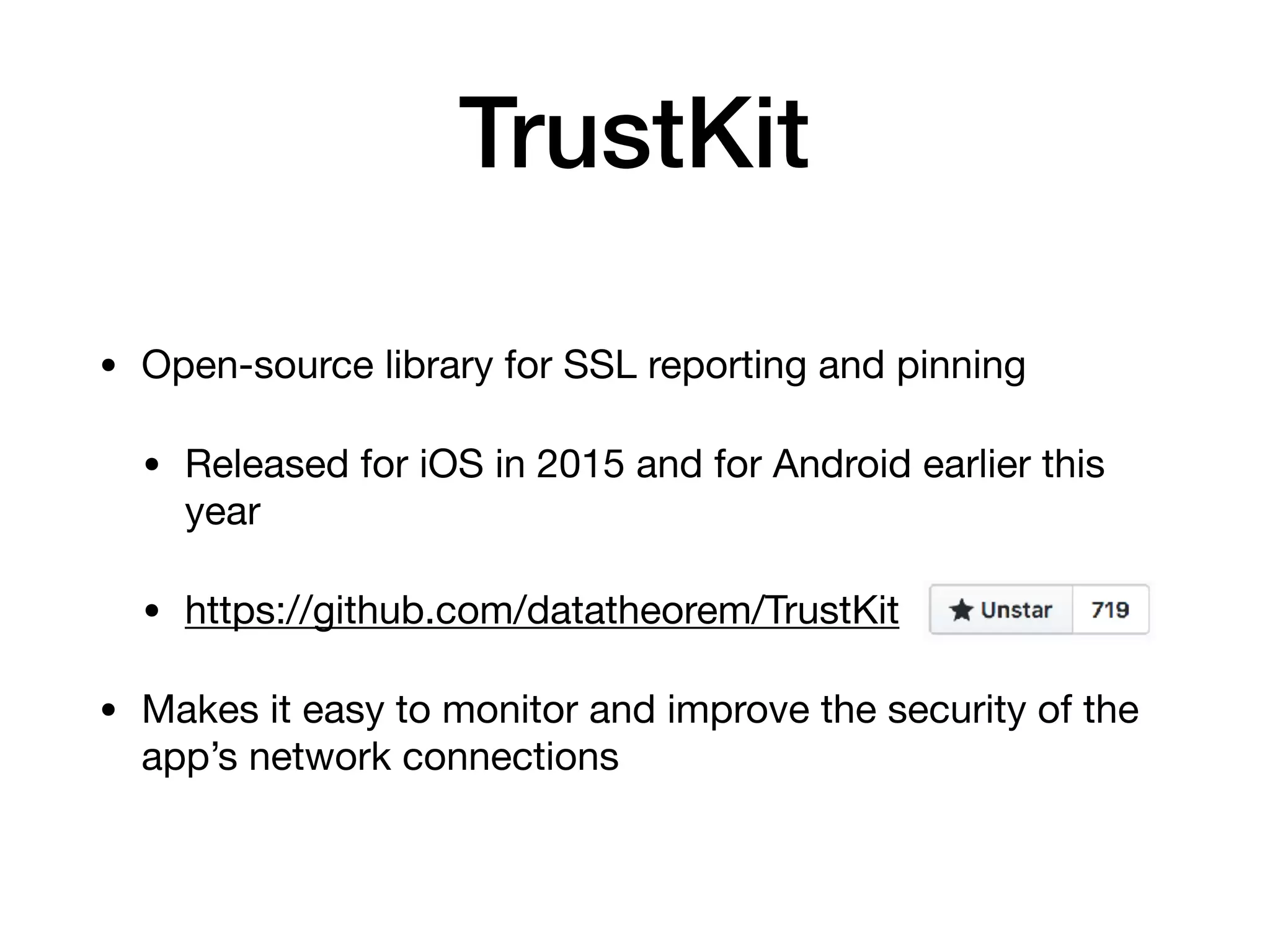
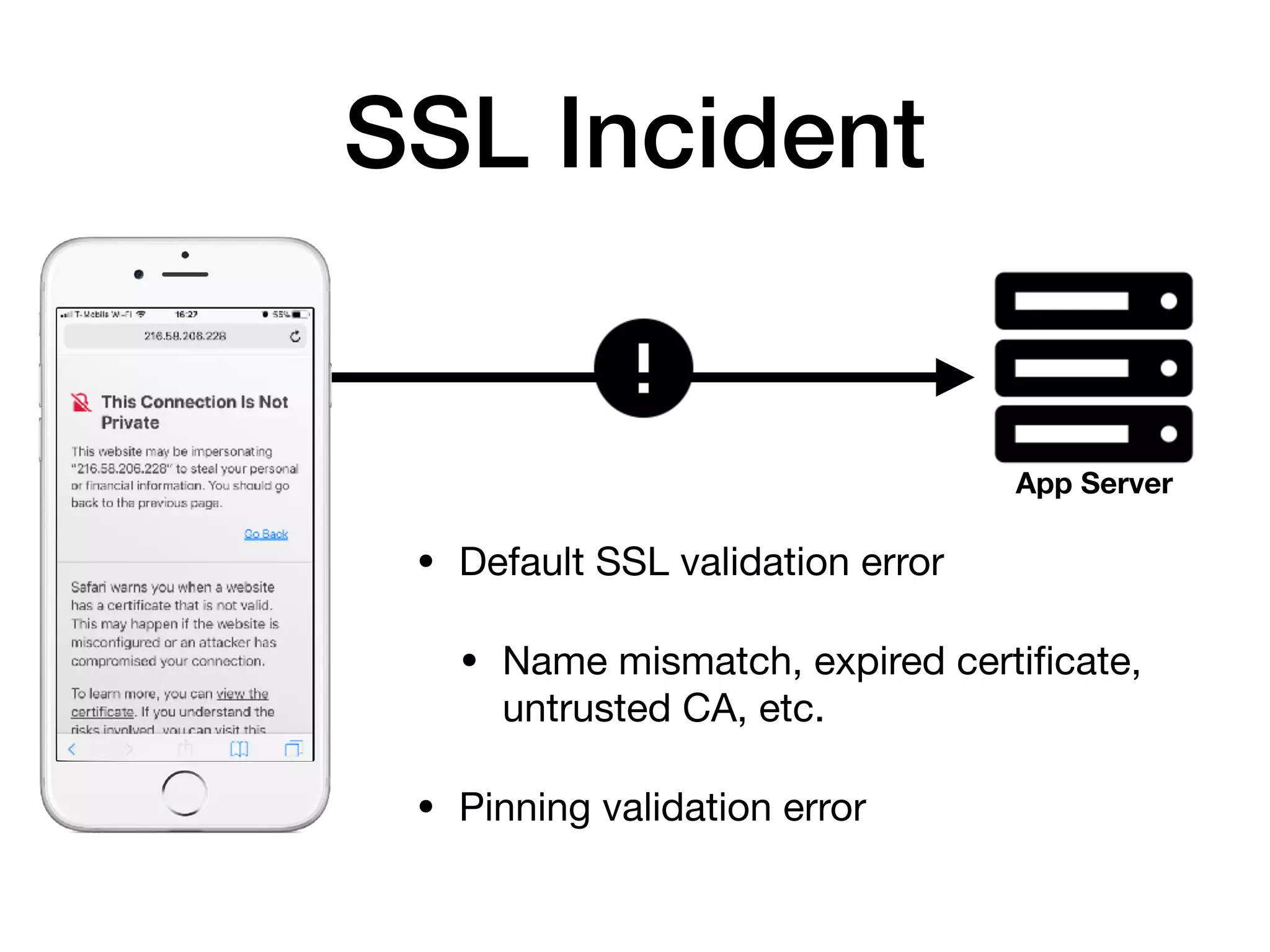
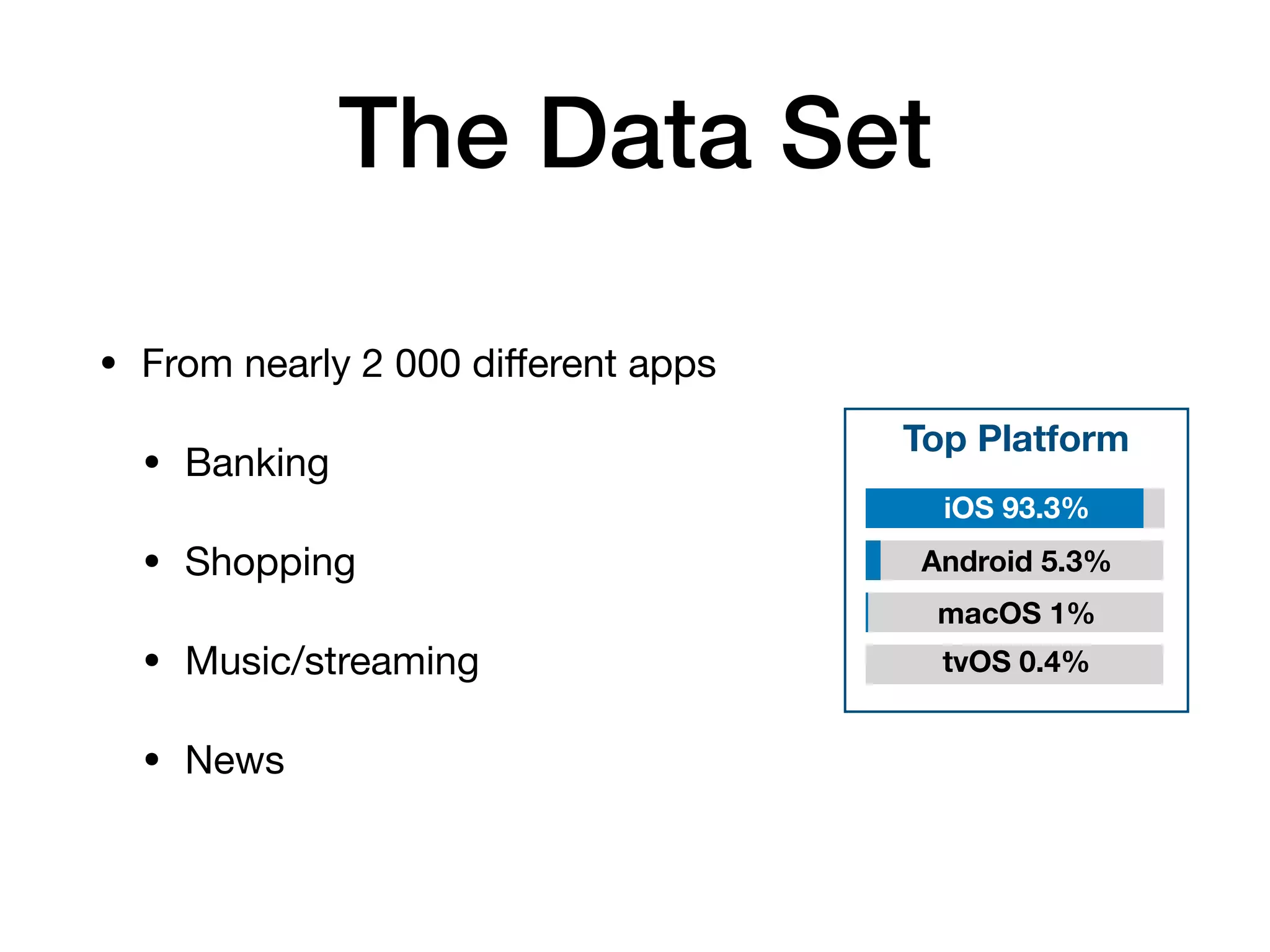
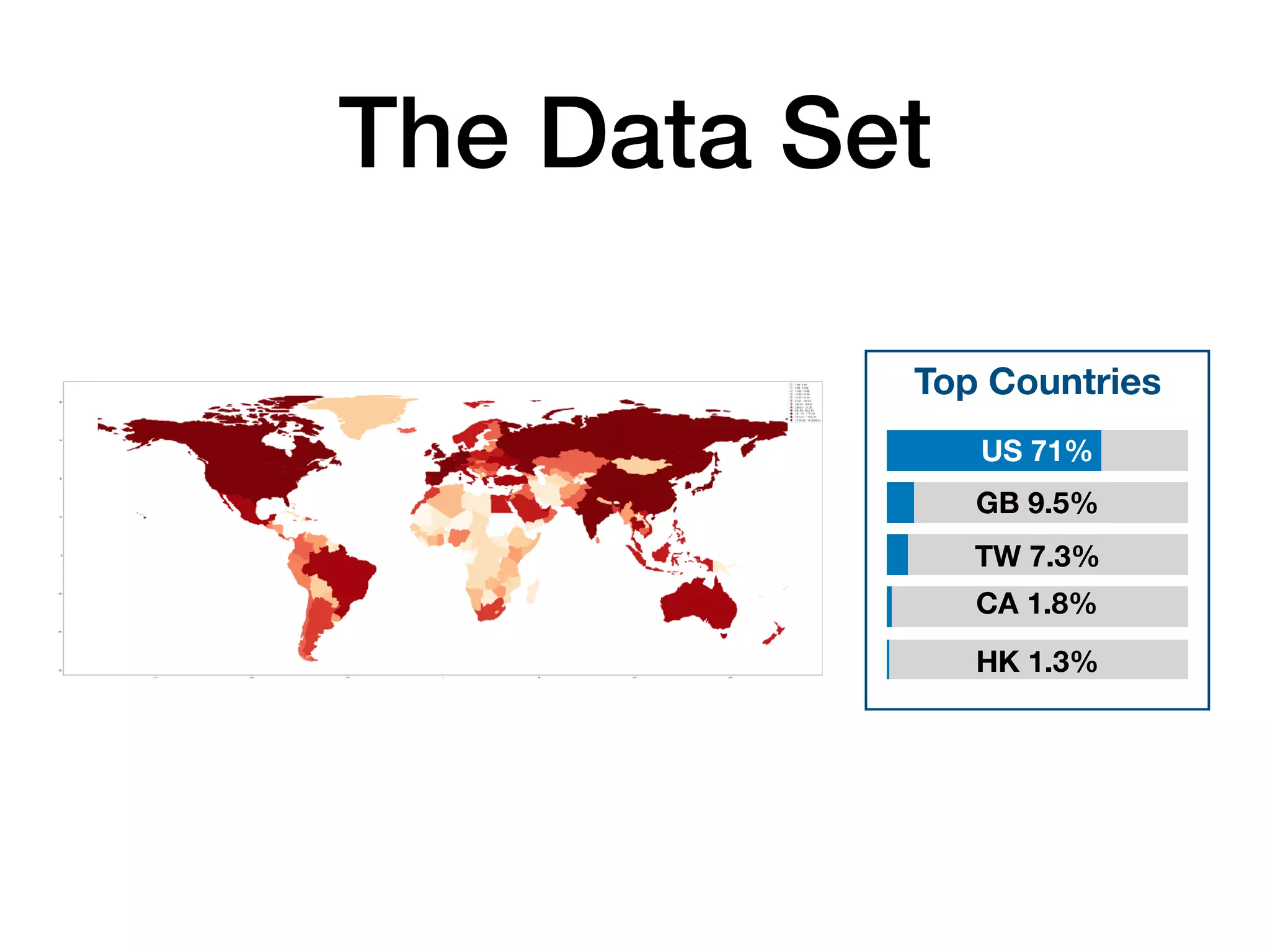
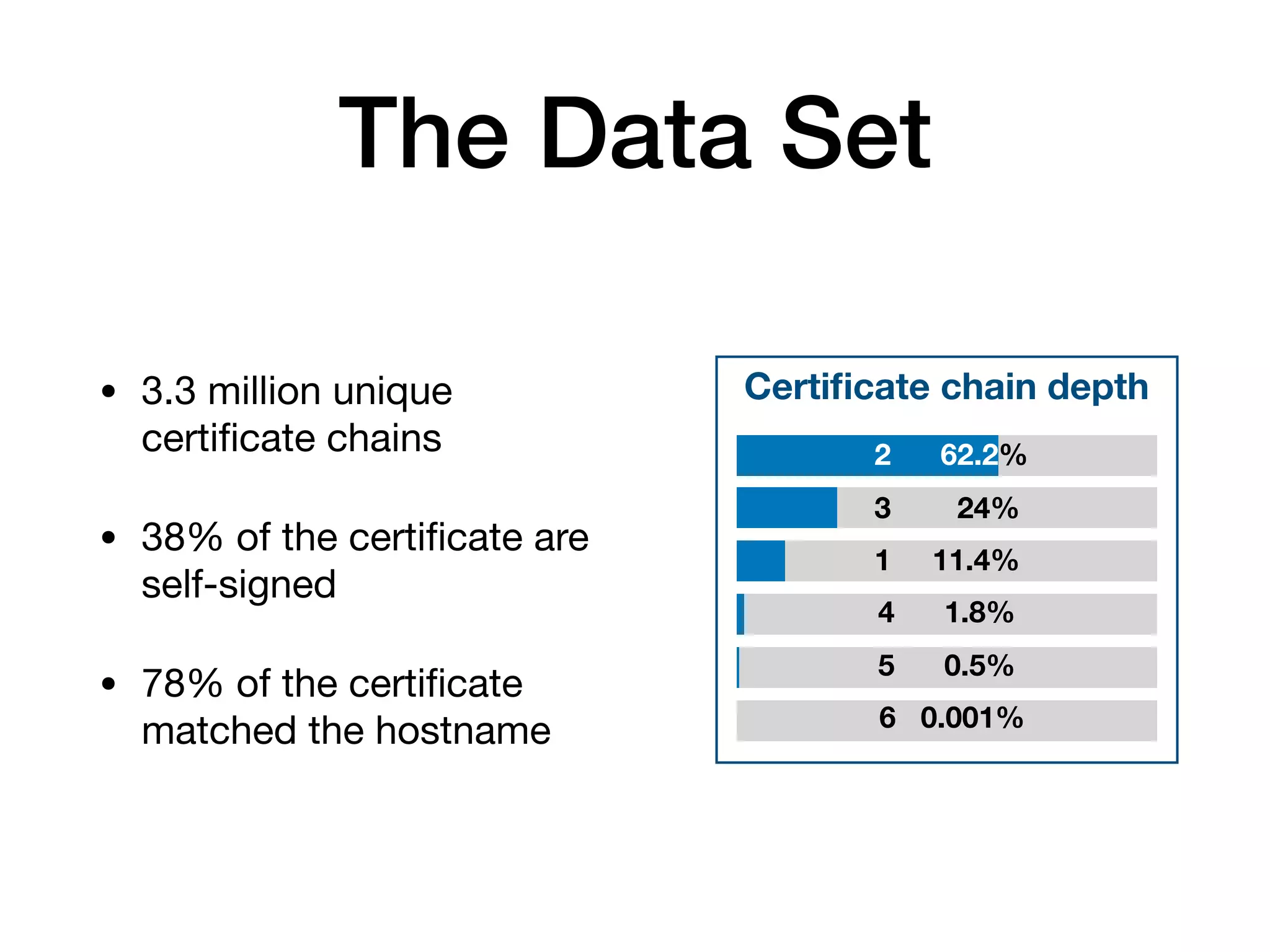
The document analyzes 10 million SSL incident reports from mobile devices to understand SSL interception, with a focus on data collection methodology using the open-source TrustKit library for SSL reporting and pinning. It presents findings from a diverse dataset primarily comprising iOS devices and reviews common SSL incidents, such as validation errors and misconfigurations. The analysis aids developers in implementing SSL pinning to enhance app security by reporting SSL errors and validating certificate chains.





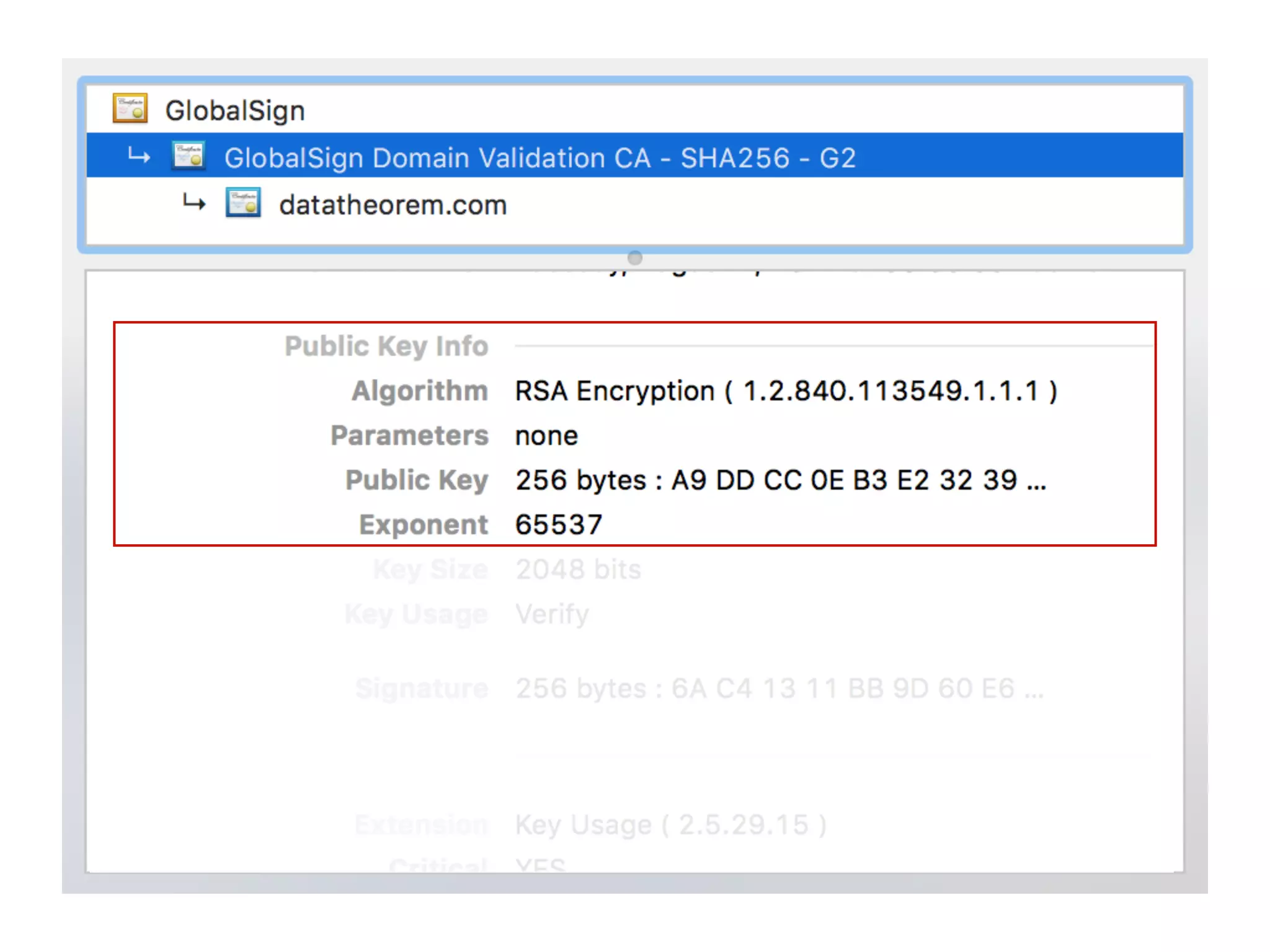

![SSL Pinning
• Hardcode in the app the SSL public key(s) to be expected
to be used by the app’s server(s)
// Initialize TrustKit
NSDictionary *trustKitConfig =
@{
kTSKPinnedDomains: @{
@"www.datatheorem.com" : @{
kTSKPublicKeyHashes : @[
@"lCppFqbkrlJ3EcVFAkeip0+44VaoJUymbnOaEUk7tEU=",
@"TQEtdMbmwFgYUifM4LDF+xgEtd0z69mPGmkp014d6ZY=",
]
}}};
[TrustKit initializeWithConfiguration:trustKitConfig];](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-12-2048.jpg)
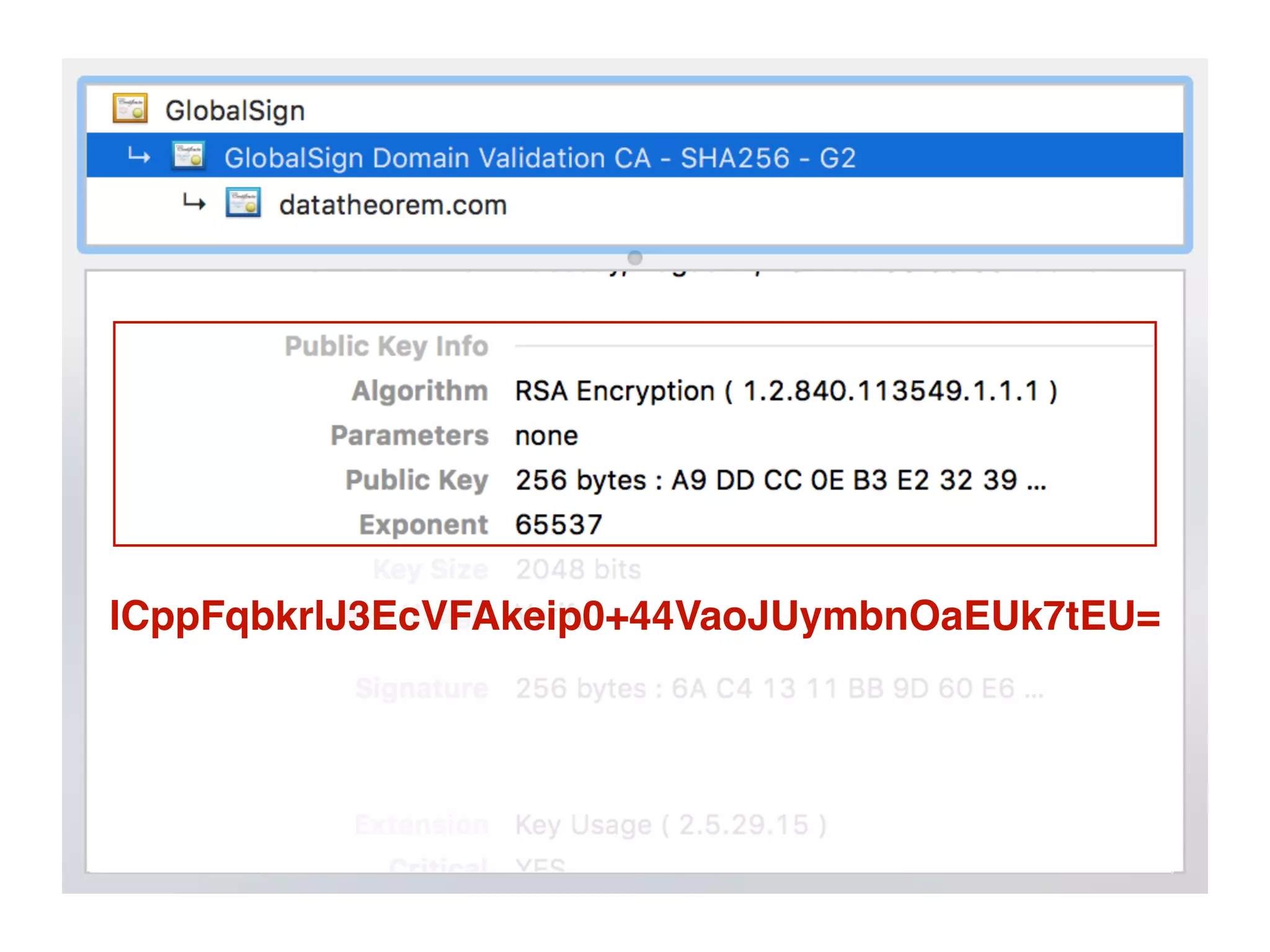
![SSL Pinning
• Hardcode in the app the SSL public key(s) to be expected
to be used by the app’s server(s)
// Initialize TrustKit
NSDictionary *trustKitConfig =
@{
kTSKPinnedDomains: @{
@"www.datatheorem.com" : @{
kTSKPublicKeyHashes : @[
@"lCppFqbkrlJ3EcVFAkeip0+44VaoJUymbnOaEUk7tEU=",
@"TQEtdMbmwFgYUifM4LDF+xgEtd0z69mPGmkp014d6ZY=",
]
}}};
[TrustKit initializeWithConfiguration:trustKitConfig];](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-13-2048.jpg)

![SSL Reporting
{
"app-bundle-id": "com.datatheorem.testtrustkit",
"app-version": “1.2",
"app-vendor-id": "599F9C00-92DC-4B5C-9464-7971F01F8370",
"app-platform": "IOS",
"trustkit-version": “1.5.3",
"hostname": "www.datatheorem.com",
"port": 443,
"noted-hostname": "datatheorem.com",
"include-subdomains": true,
"enforce-pinning": true,
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"date-time": "2015-06-08T01:58:05Z",
"known-pins": [
"pin-sha256="rFjc3wG7lTZe43zeYTvPq8k4xdDEutCmIhI5dn4oCeE="",
"pin-sha256="TQEtdMbmwFgYUifM4LDF+xgEtd0z69mPGmkp014d6ZY=""
],
"validation-result": 1
}](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-16-2048.jpg)




![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-26-2048.jpg)
![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-27-2048.jpg)
![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-28-2048.jpg)
![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-29-2048.jpg)
![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata
==
misconfiguration / certificate_chain_valid](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-30-2048.jpg)
![Report Classification
{
"app-bundle-id": "com.datatheorem.pin_misconfig",
"hostname": "www.datatheorem.com",
"date-time": "2017-05-12T06:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 1,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-12T06:00:25Z",
}
raw report
report metadata
unknown / to_review
!=](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-31-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.coporate_proxy",
"hostname": "www.datatheorem.com",
“validated-certificate-chain”: [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"date-time": "2017-03-03T21:27:12Z",
"validation-result": 1,
"...": “…",
raw report](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-32-2048.jpg)
![{
"app-bundle-id": “com.datatheorem.coporate_proxy",
"hostname": "www.datatheorem.com",
“validated-certificate-chain”: [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"date-time": "2017-03-03T21:27:12Z",
"validation-result": 1,
"...": “…",
Report Classification
raw report](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-33-2048.jpg)
![{
"app-bundle-id": “com.datatheorem.coporate_proxy",
"hostname": "www.datatheorem.com",
“validated-certificate-chain”: [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"date-time": "2017-03-03T21:27:12Z",
"validation-result": 1,
"...": “…",
Report Classification
raw report](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-34-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.coporate_proxy",
"hostname": "www.datatheorem.com",
“validated-certificate-chain”: [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"date-time": "2017-03-03T21:27:12Z",
"validation-result": 1,
"...": “…",
{
"certificate_chain_infos": [
{"issuer":
{"common_name":"Fortigate CA",
“…": […],
raw report
certificate chain info](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-35-2048.jpg)
![Report Classification
corporate_appliance / Fortinet
corporate_appliance:
Fortinet:
leaf:
- !IssuerCommonName 'FortiGate CA'
{
"certificate_chain_infos": [
{"issuer":
{"common_name":"Fortigate CA",
“…": […],
certificate chain info
classifier ruleset](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-36-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.bad_device_clock”,
"hostname": "www.datatheorem.com",
"date-time": "2017-03-14T04:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 2,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-22T04:00:54Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-37-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.bad_device_clock”,
"hostname": "www.datatheorem.com",
"date-time": "2017-03-14T04:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 2,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-22T04:00:54Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-38-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.bad_device_clock”,
"hostname": "www.datatheorem.com",
"date-time": "2017-03-14T04:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 2,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-22T04:00:54Z",
}
raw report
report metadata](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-39-2048.jpg)
![Report Classification
{
"app-bundle-id": “com.datatheorem.bad_device_clock”,
"hostname": "www.datatheorem.com",
"date-time": "2017-03-14T04:00:22Z",
"validated-certificate-chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"validation-result": 2,
"…": […],
"…": […],
"server_certificate_chain": [
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
“-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----",
"-----BEGIN CERTIFICATE-----n[…]n-----END CERTIFICATE-----"
],
"received_at”: “2017-05-22T04:00:54Z",
}
raw report
report metadata
misconfigured_device / bad_clock](https://image.slidesharecdn.com/1108aam2bluehat-v17-data-theorem-ssl-reporting-171209003906/75/BlueHat-v17-Where-how-and-why-is-SSL-traffic-on-mobile-getting-intercepted-A-look-at-three-million-real-world-SSL-incidents-40-2048.jpg)