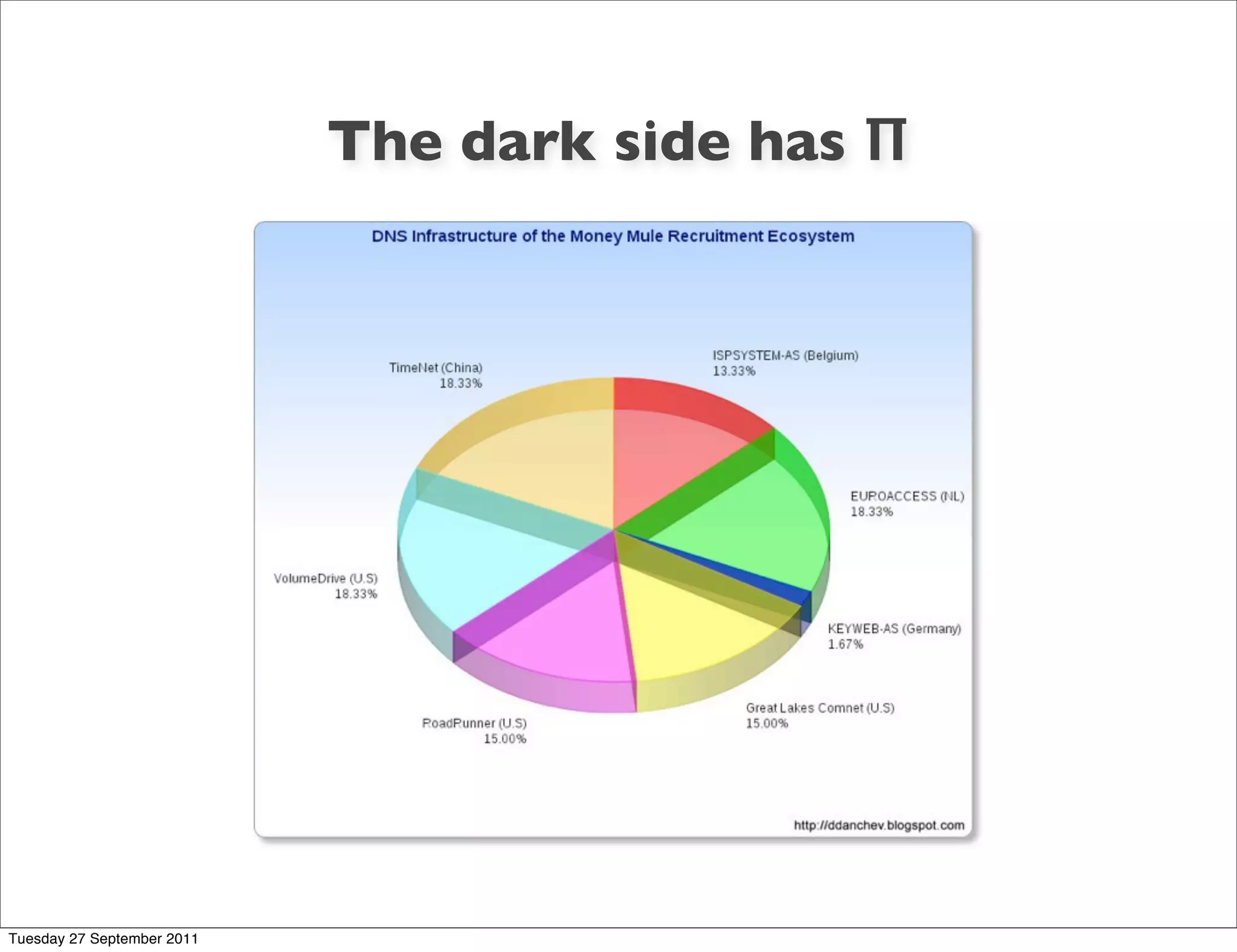
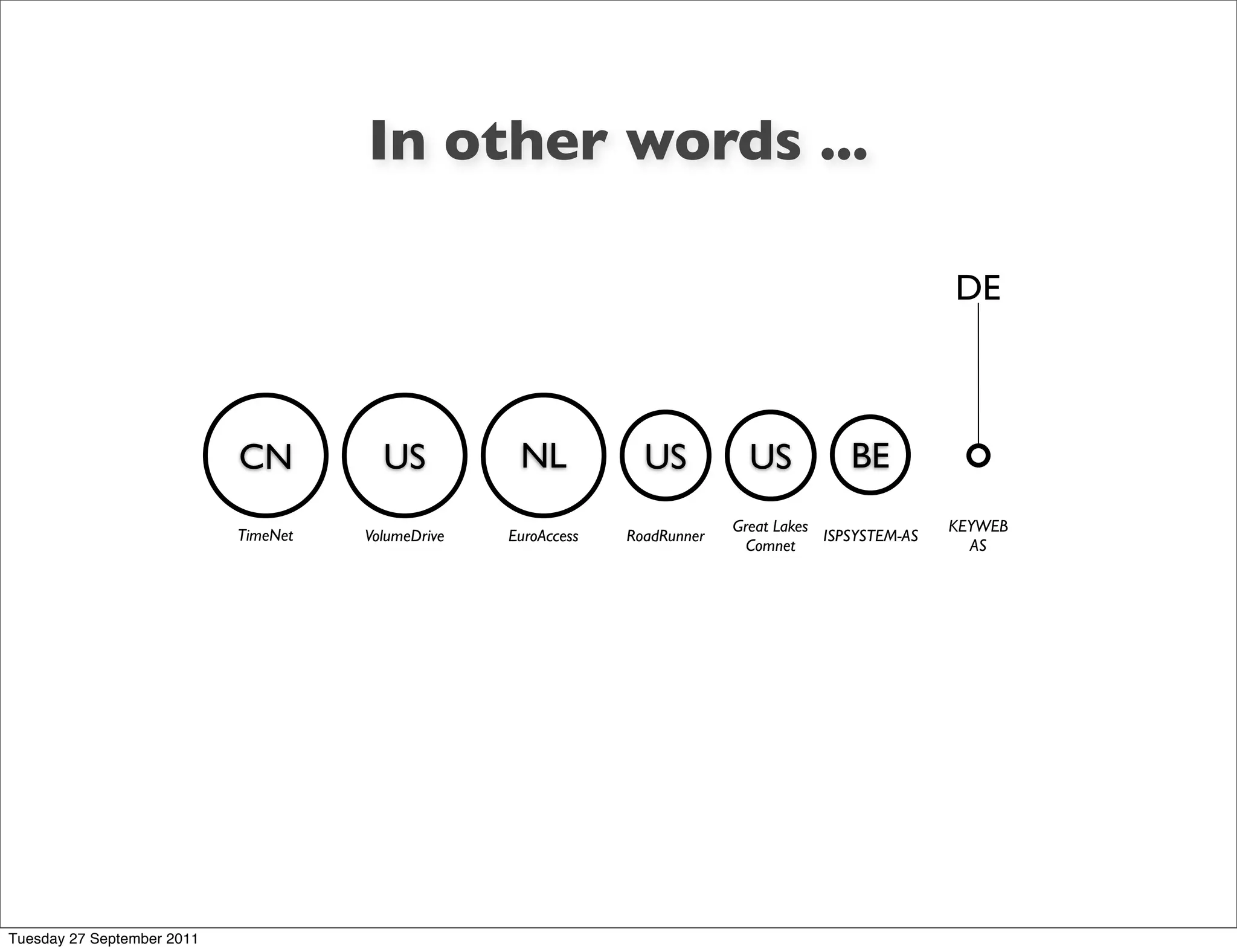
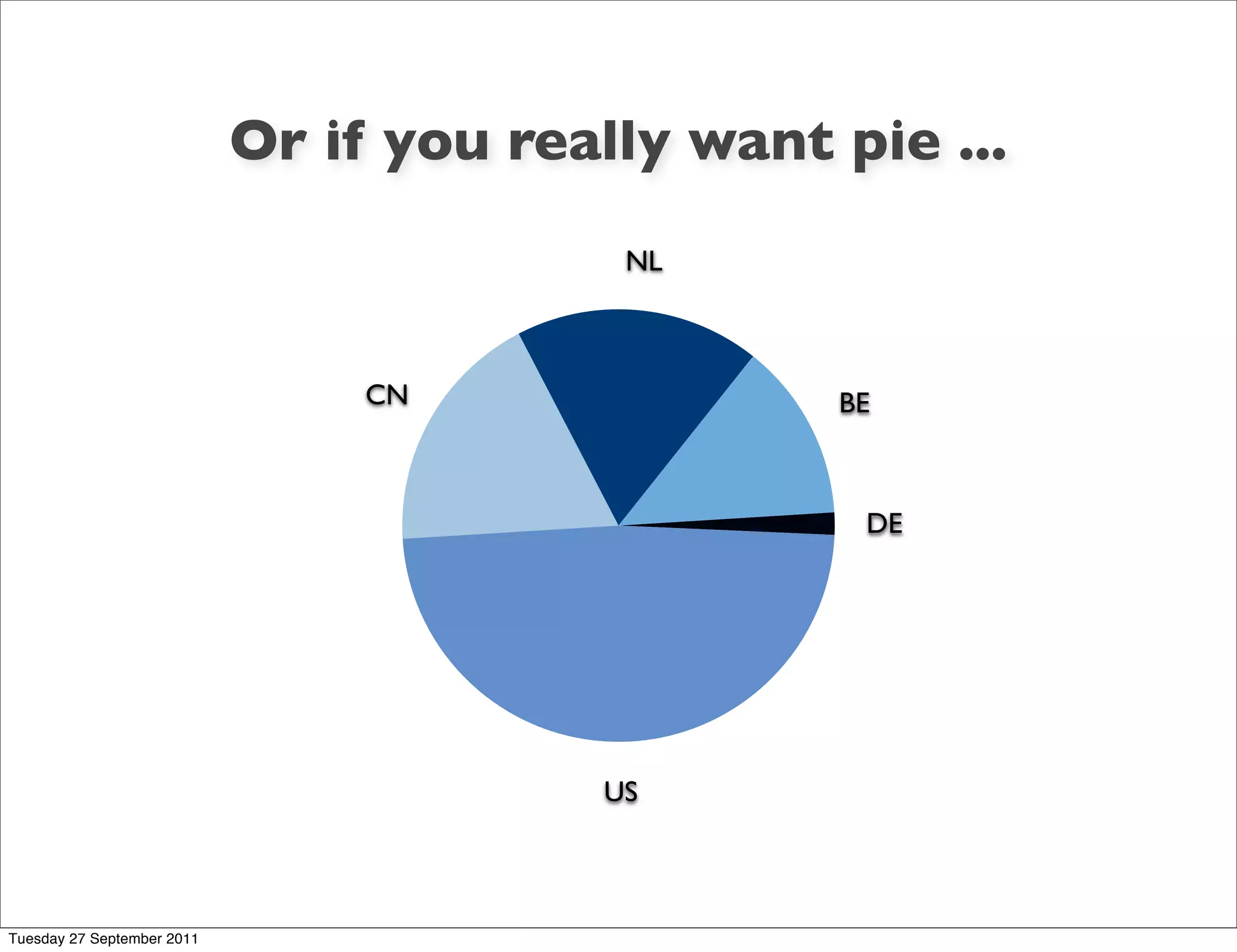
The document discusses information visualization and dashboard design. It provides tips from experts like Edward Tufte and Stephen Few on creating effective visual displays of data that are clean, simple and focus on the most important information. Various charts and visualization examples are presented to illustrate good and bad practices for dashboarding.

![about me ...
information security manager
big 4 company
incident response/security management/SIEM
[running in the 2011 (ISC)2 board elections]
Tuesday 27 September 2011](https://image.slidesharecdn.com/idc2011talk-110927154938-phpapp01/75/And-suddenly-I-see-IDC-IT-Security-Brussels-2011-2-2048.jpg)