Embed presentation
Download as PDF, PPTX




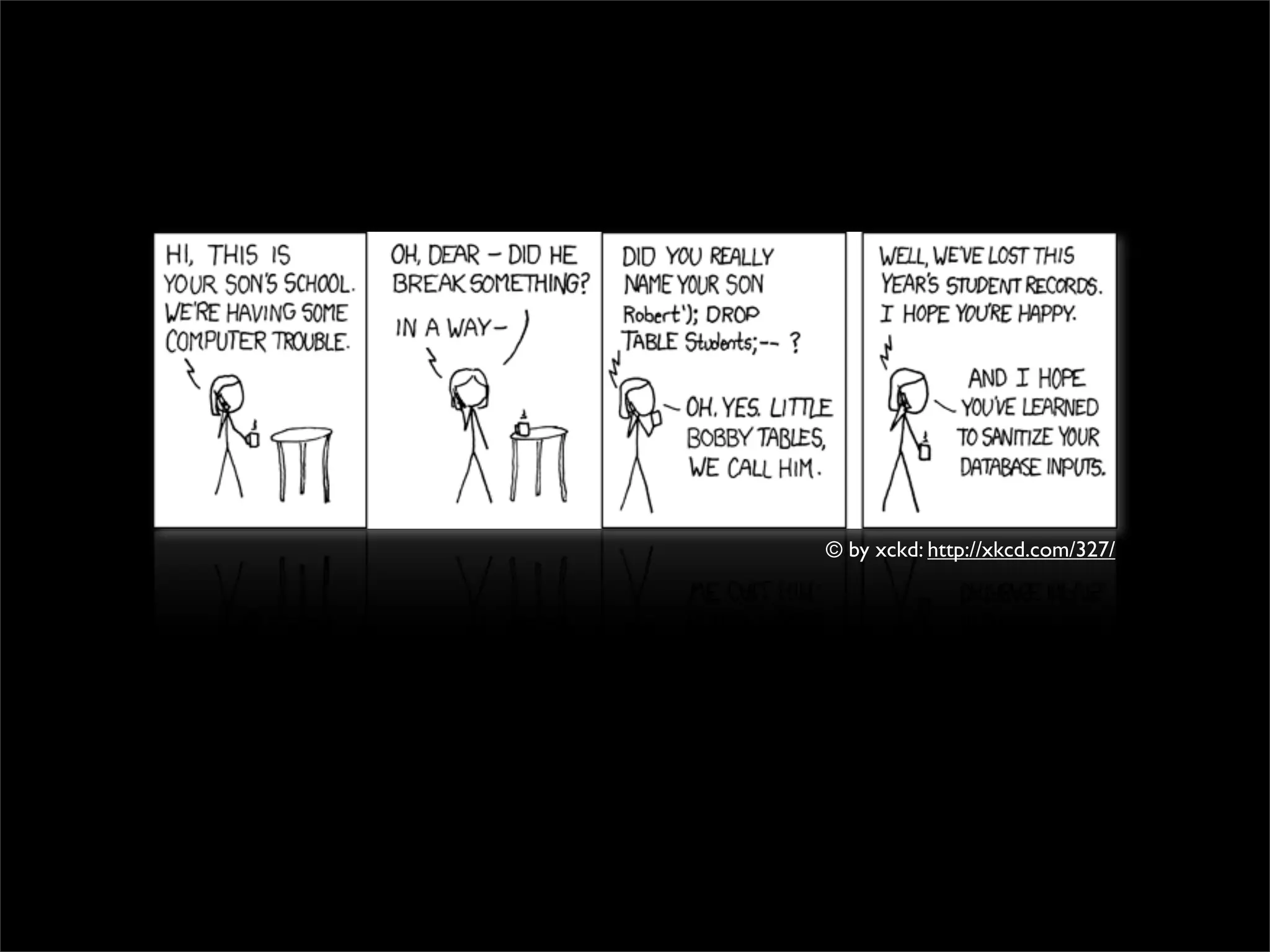
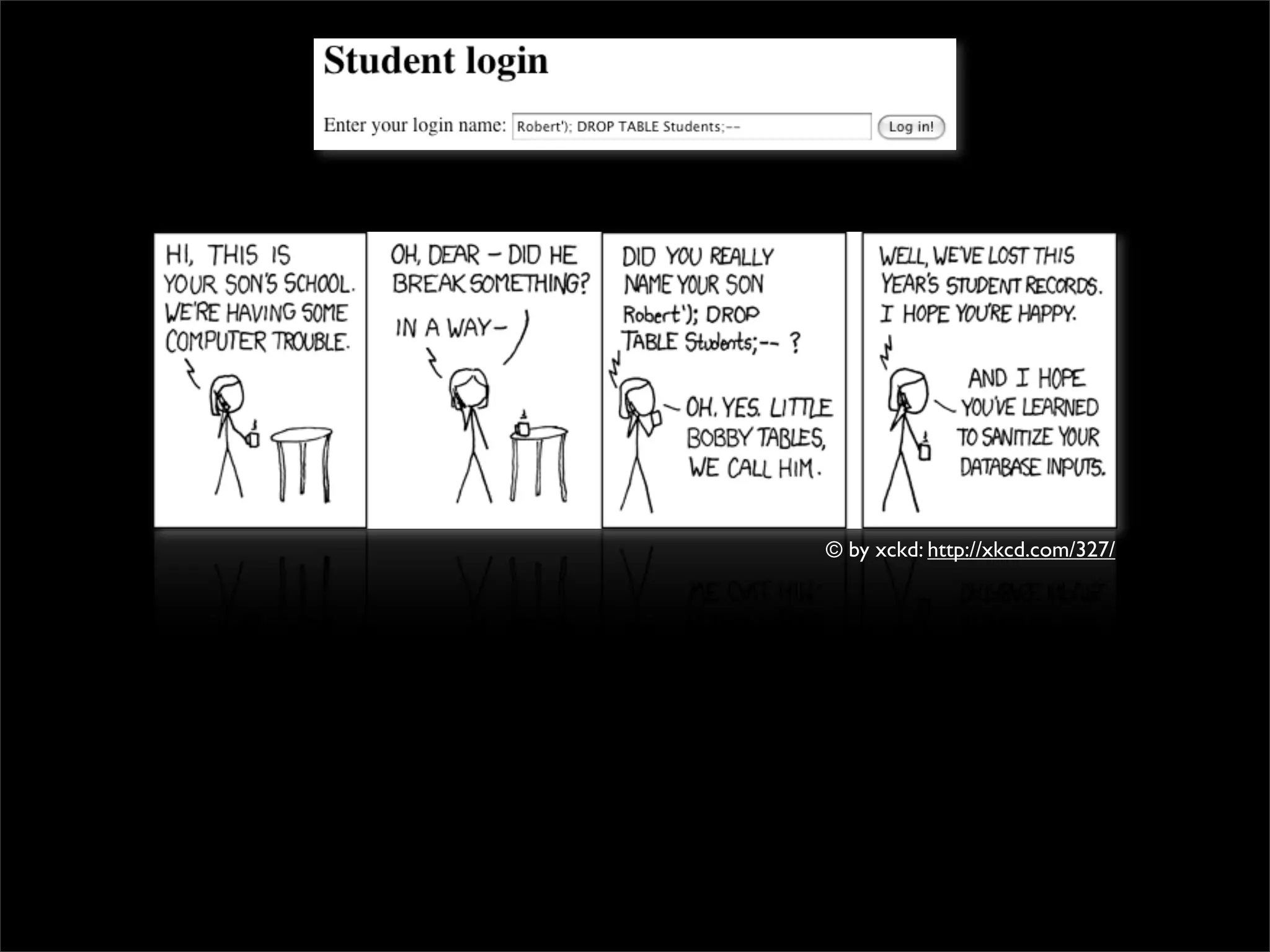
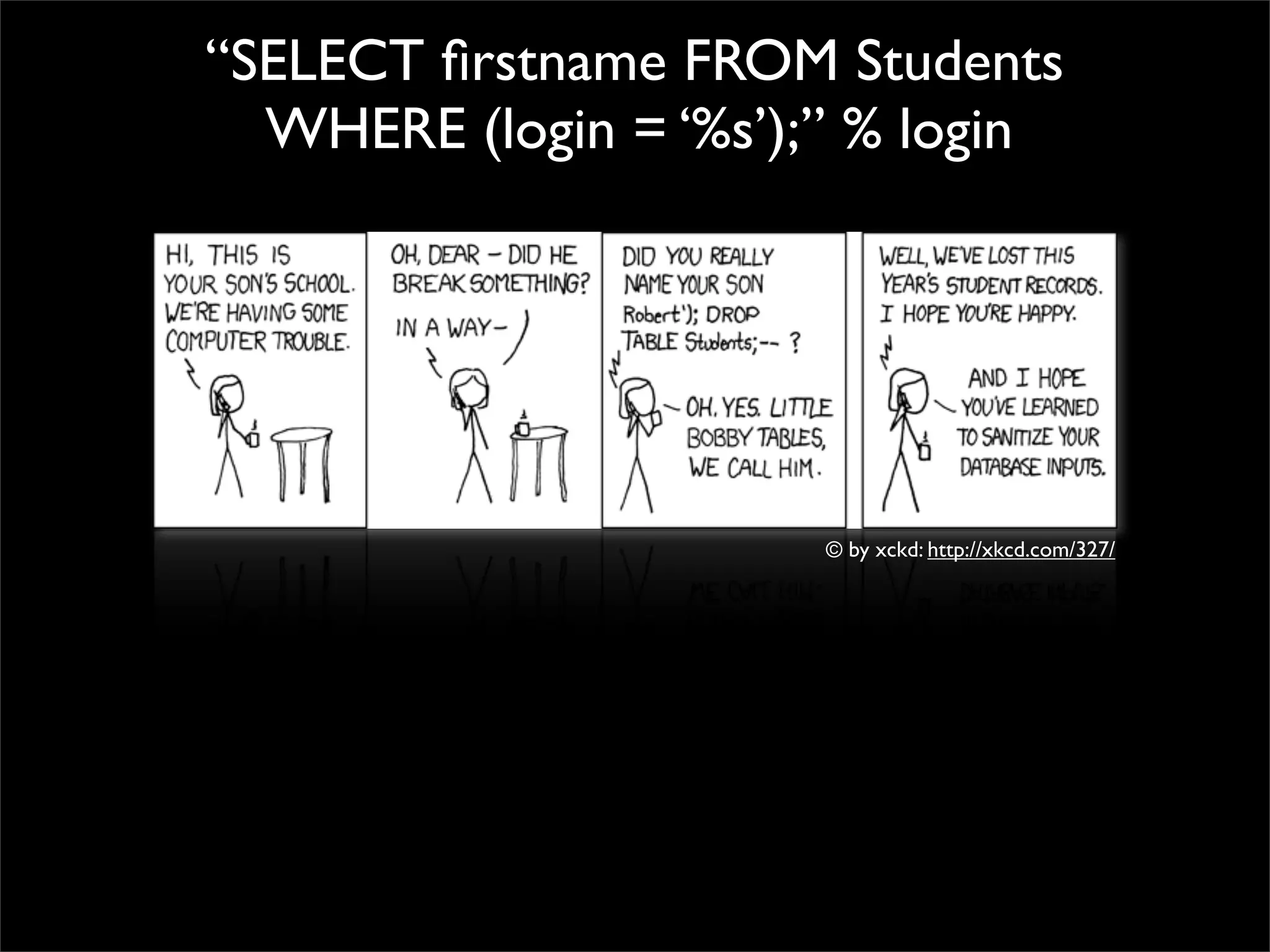
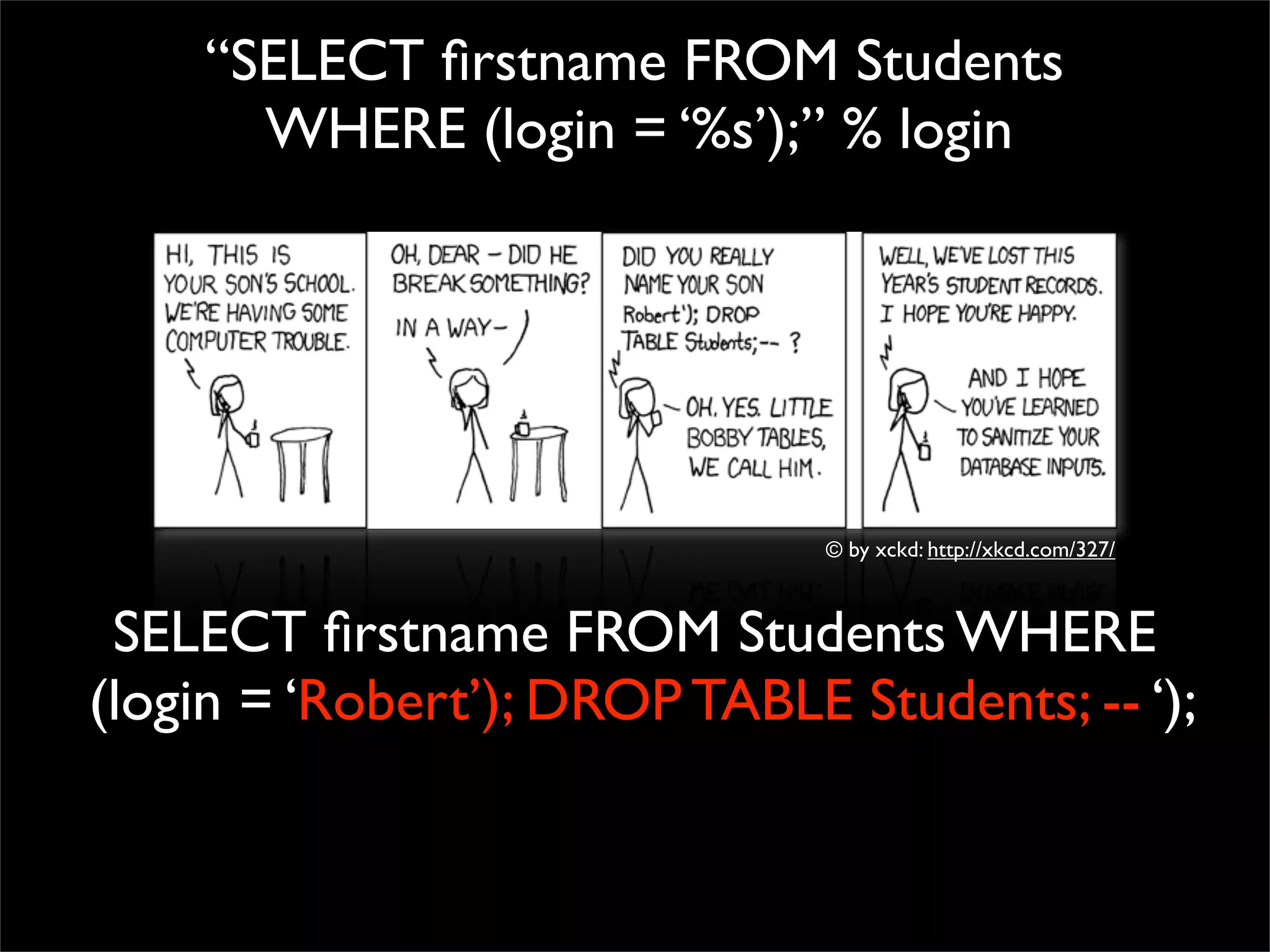










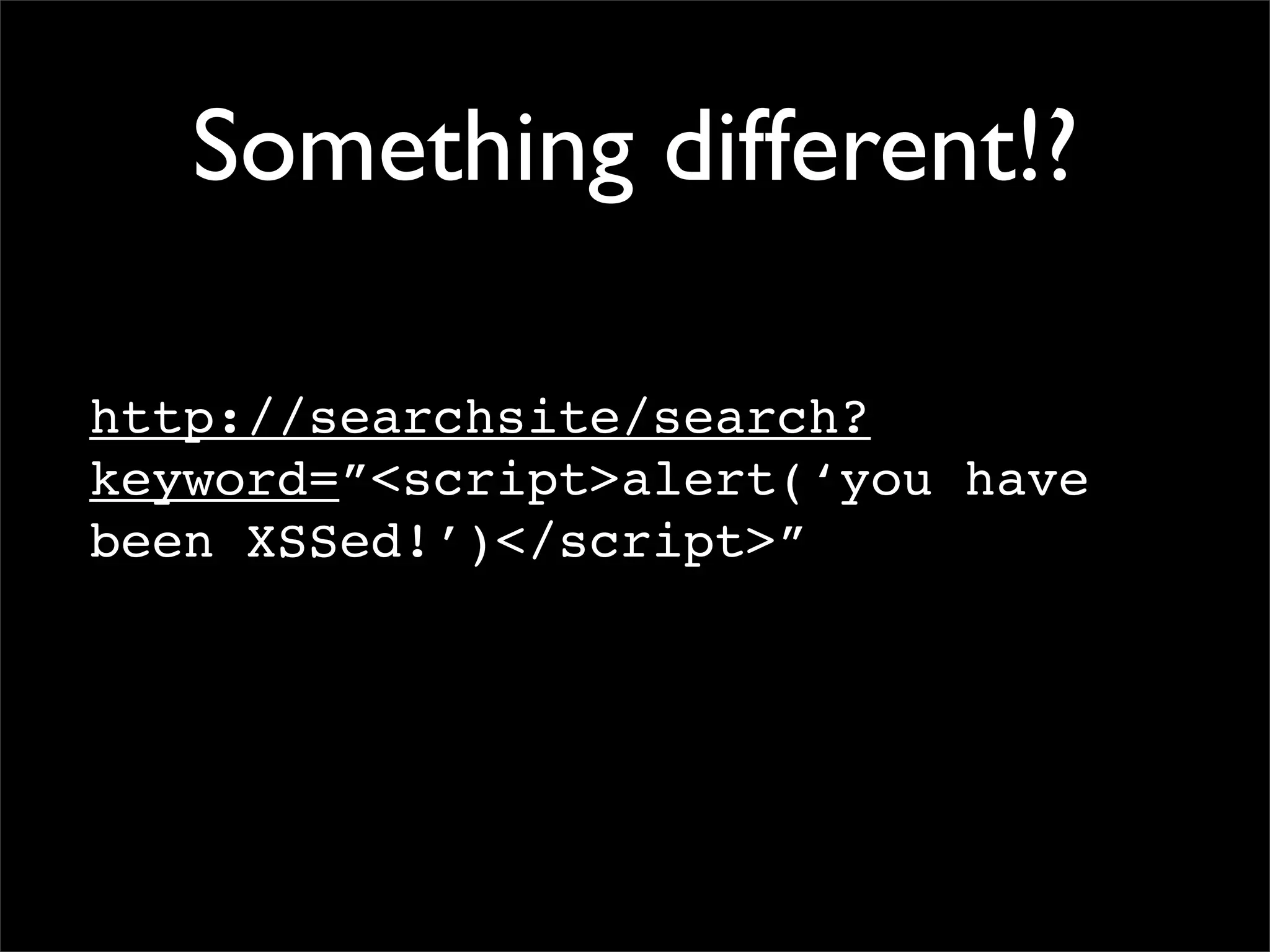
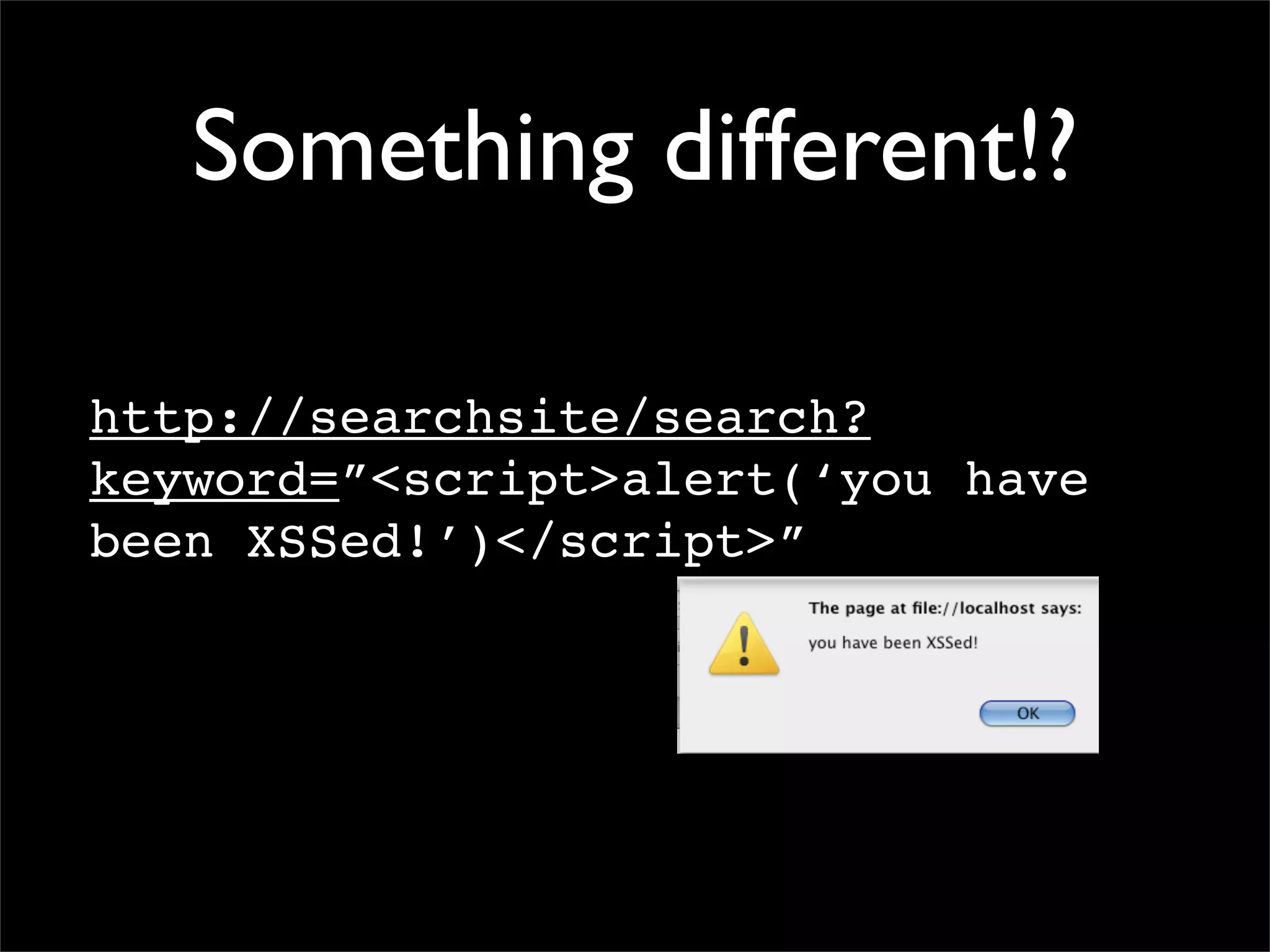





















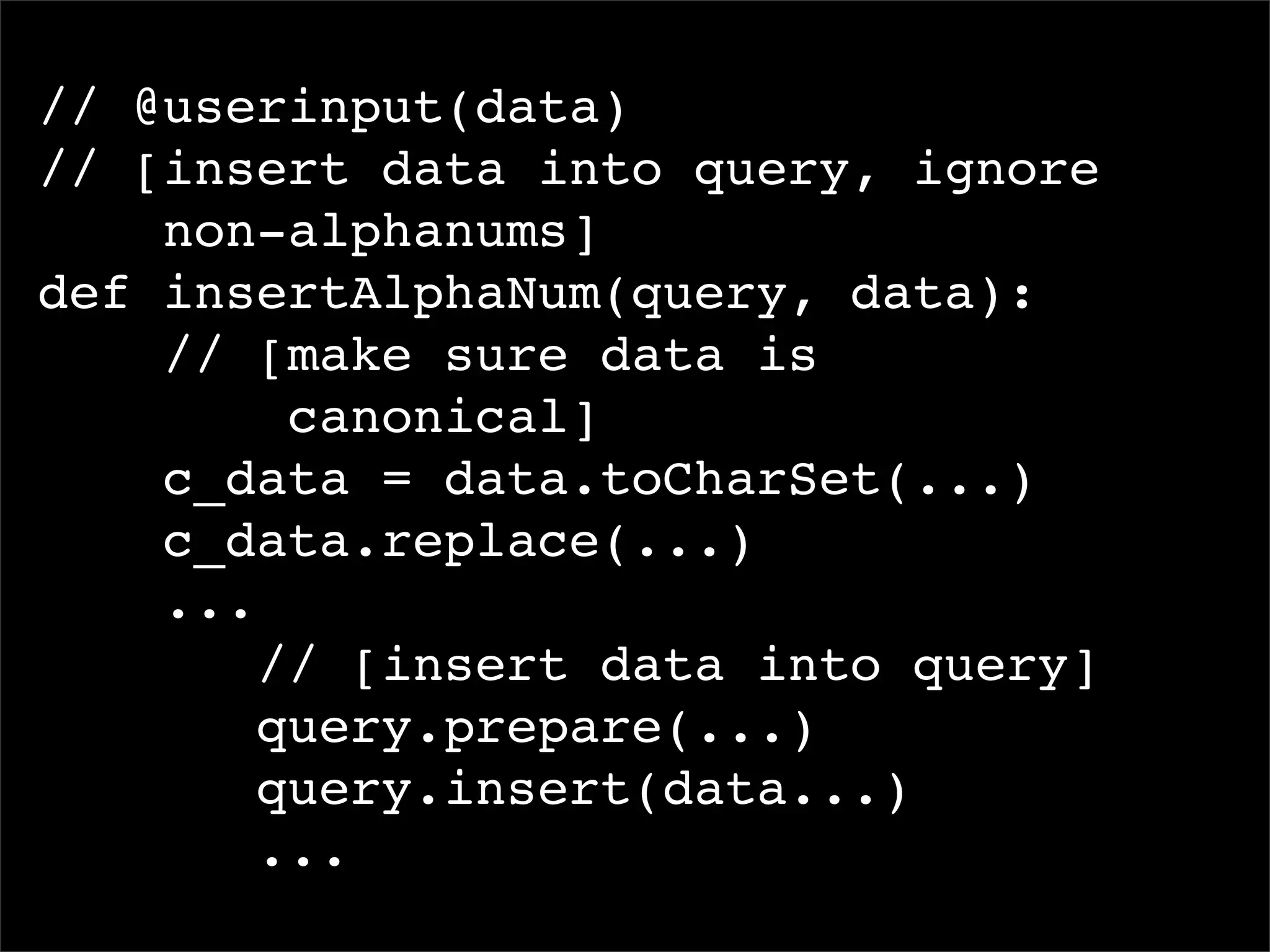





This document discusses techniques for preventing SQL injection and cross-site scripting (XSS) vulnerabilities. It proposes using prepared statements with separate data and control planes as a "safe query object" approach. It also discusses policy-based sanitization of HTML and focusing code reviews on defect detection through annotating suspicious code regions. The overall goal is to help developers adopt architectures and techniques that thoroughly apply technical solutions to recognize and fix security weaknesses.






















































