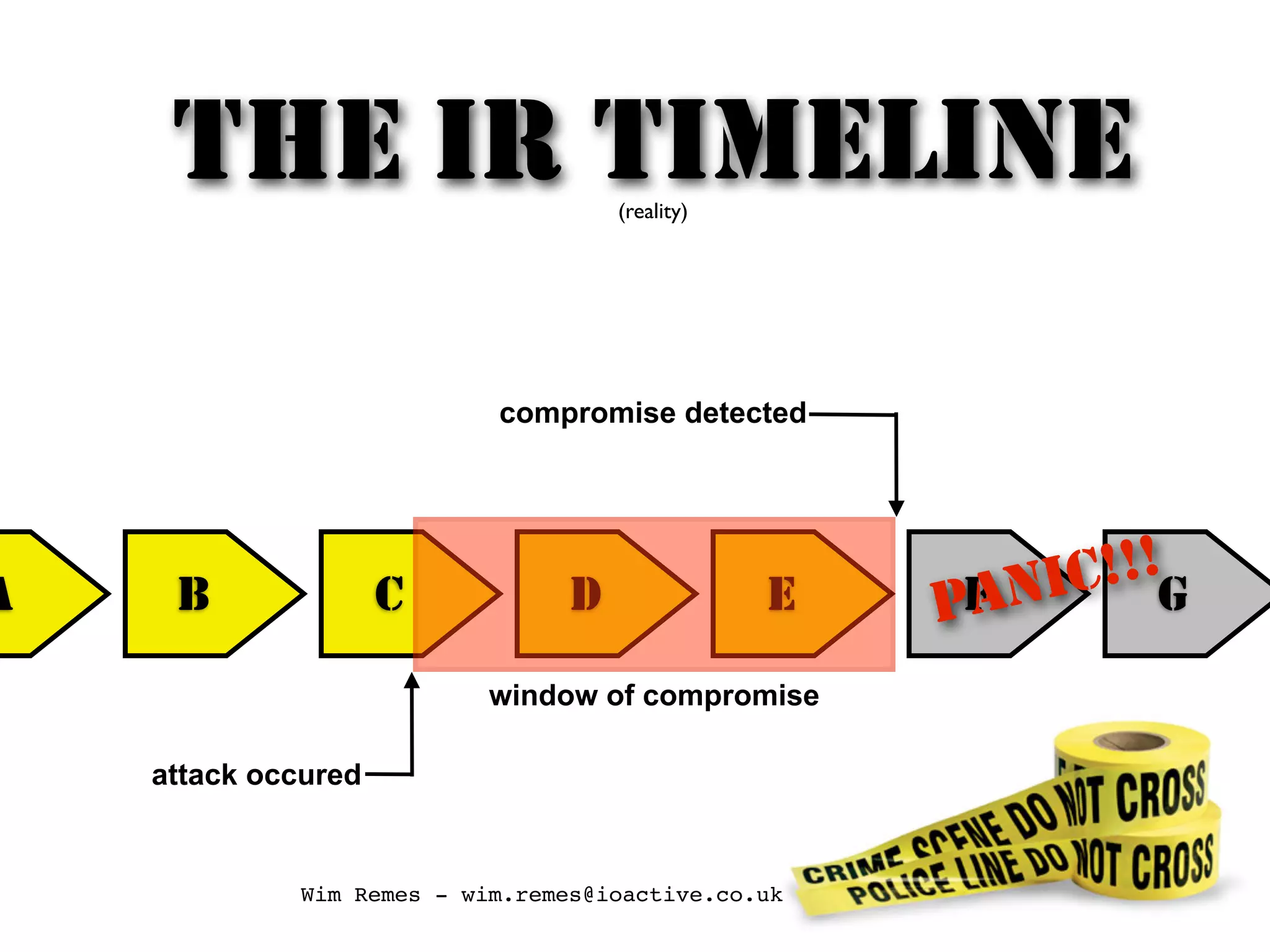
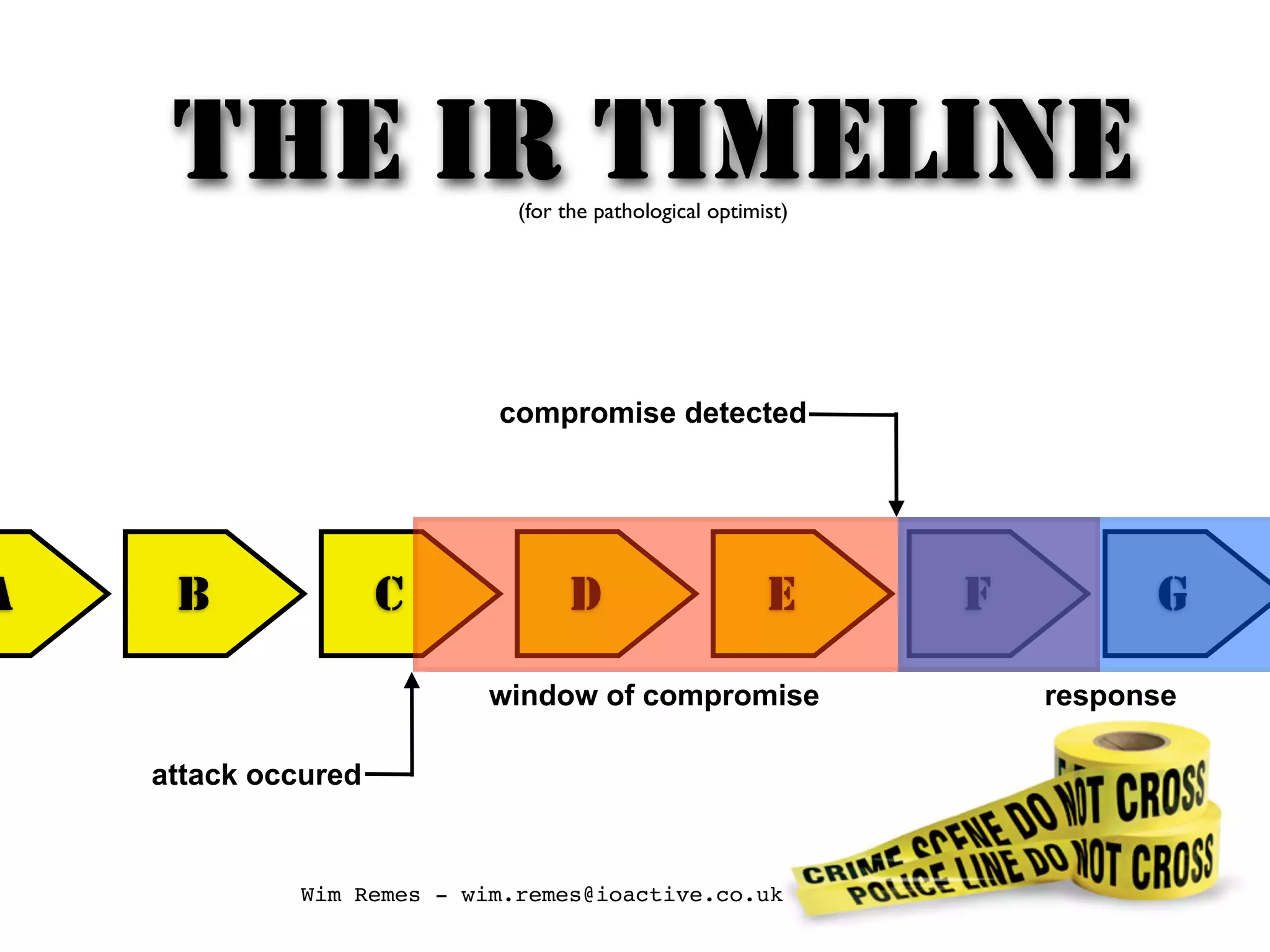
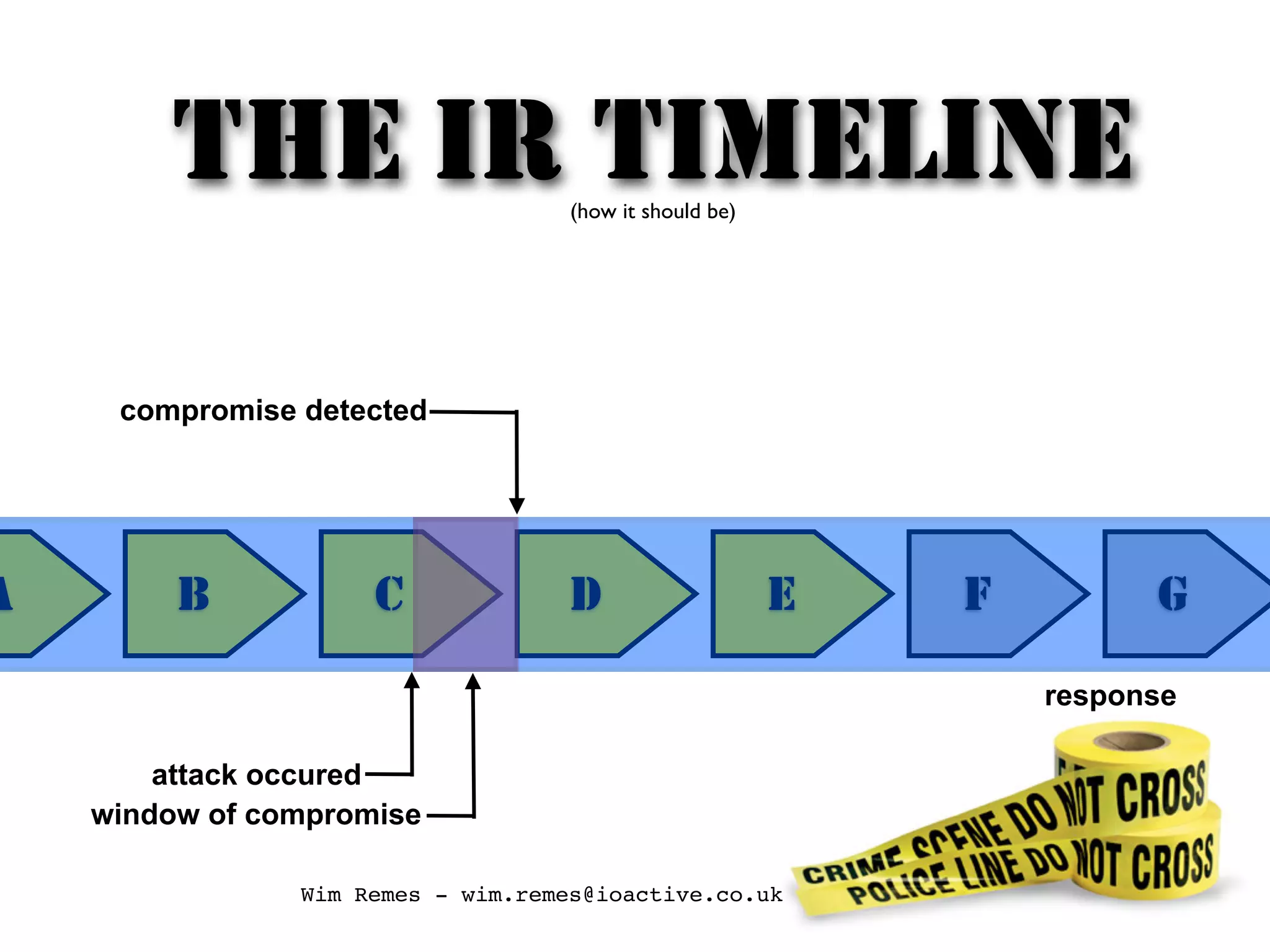
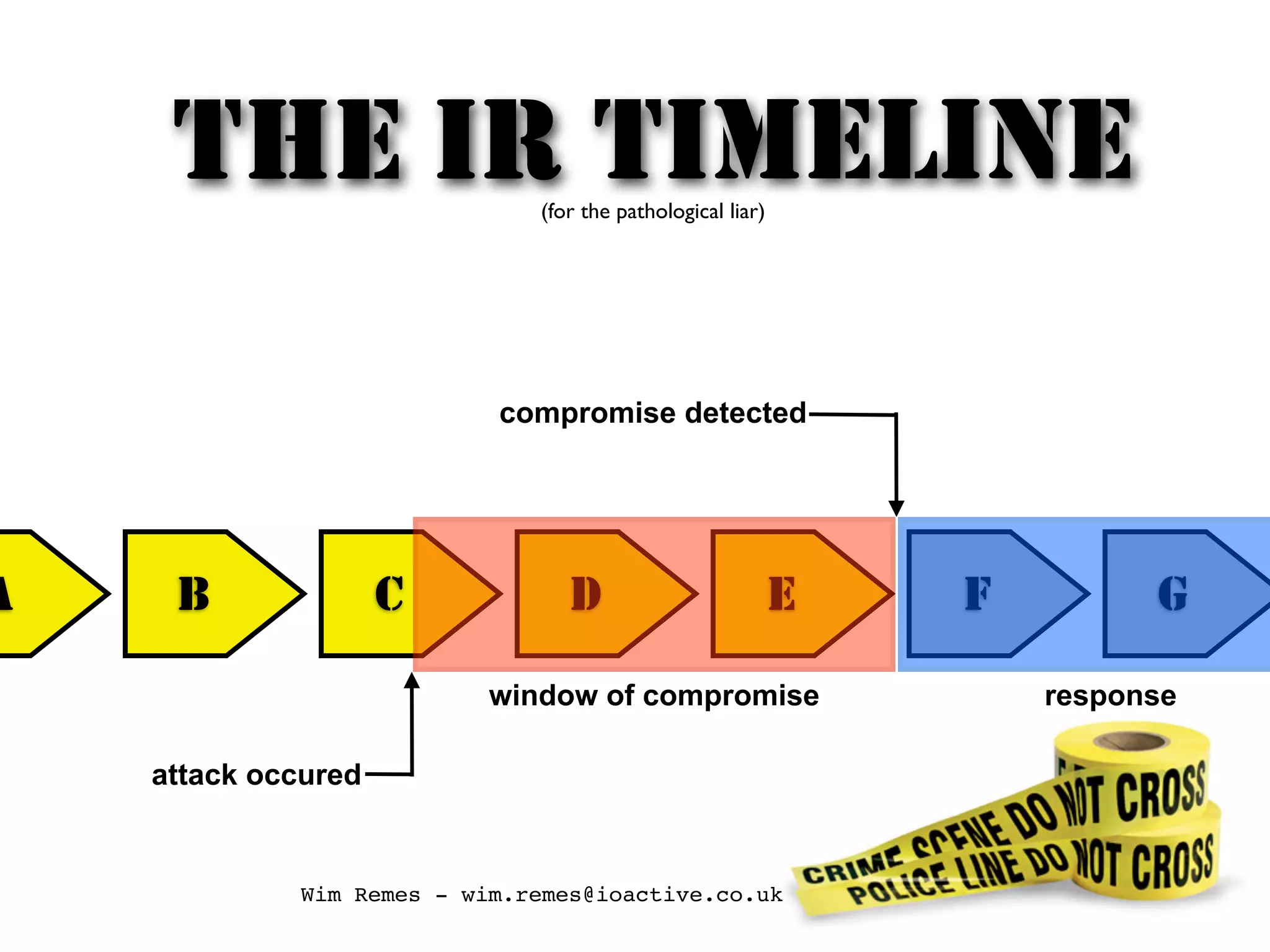
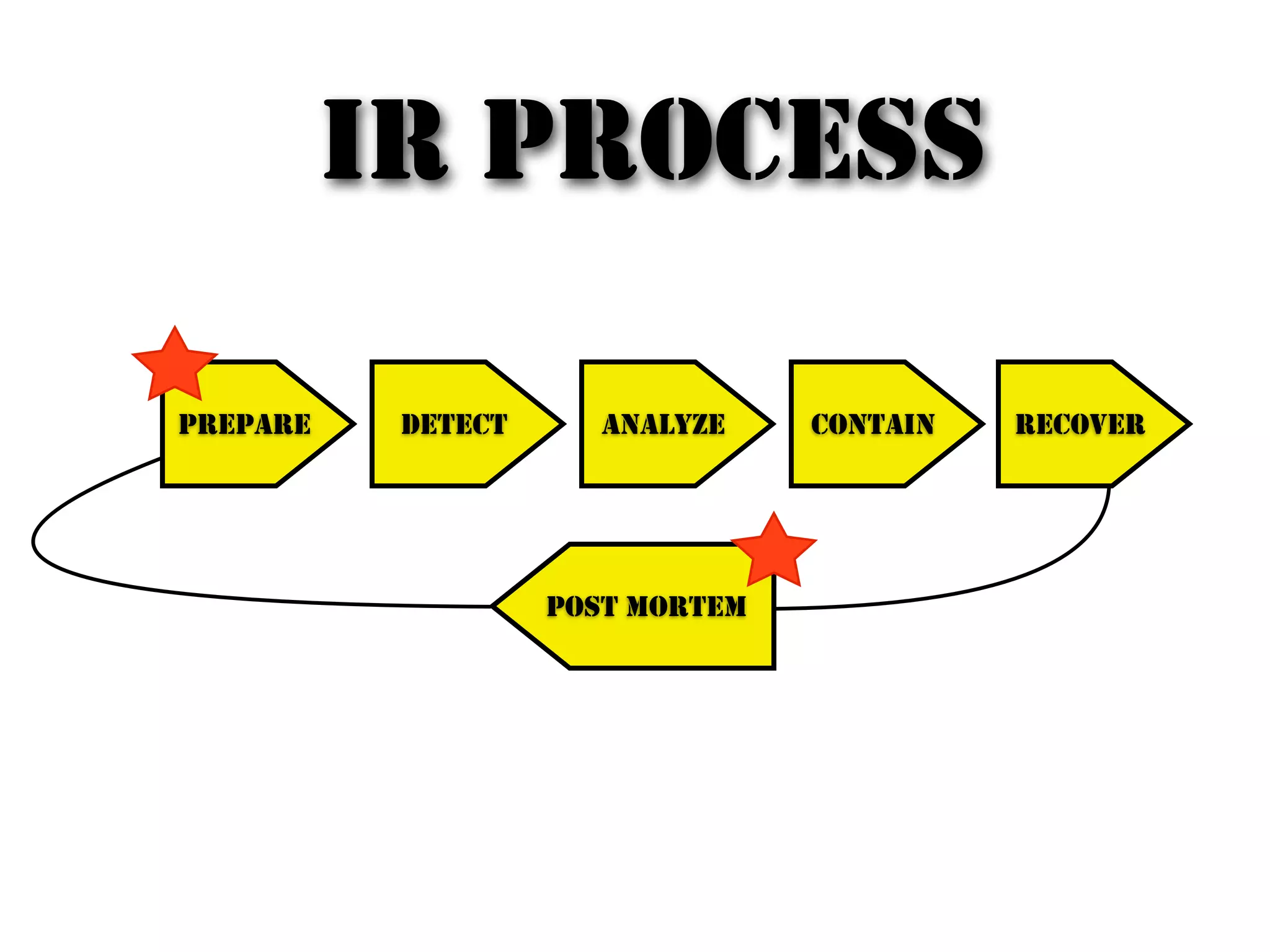
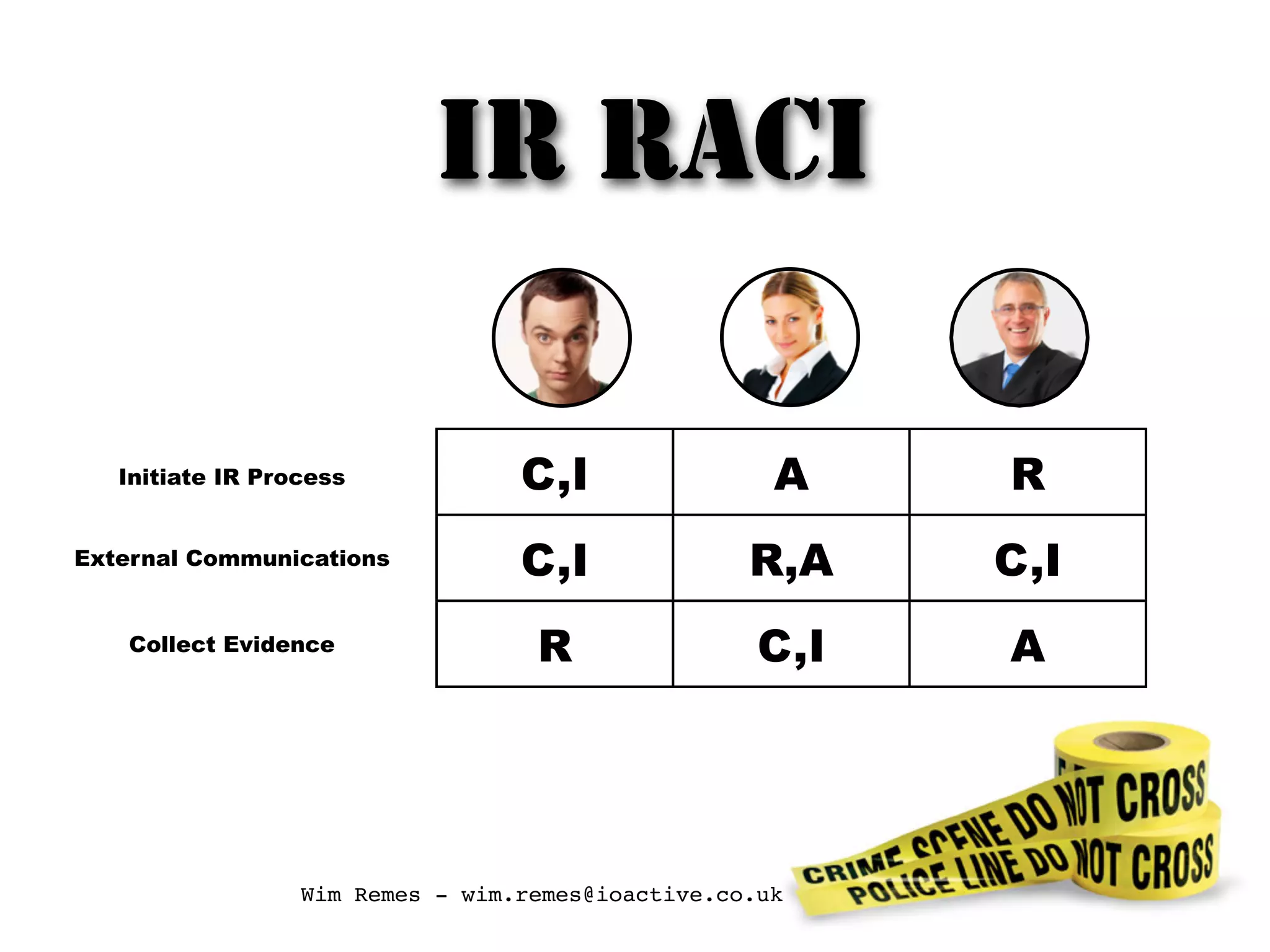
The document discusses building an incident response program and timeline. It recommends having the right people, management support, a documented incident response process, supporting technology like logging and network segmentation, and ongoing training and testing. It also identifies different roles involved in incident response, such as IT personnel, management, law enforcement and press. The overall message is that organizations need to prepare and plan their incident response capabilities in advance through people, processes, technology and training in order to effectively respond when an incident occurs.