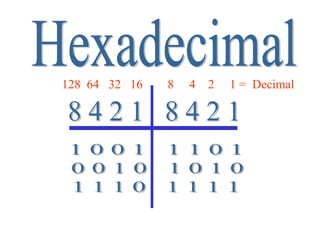
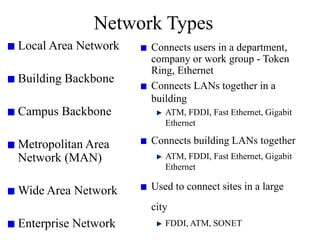
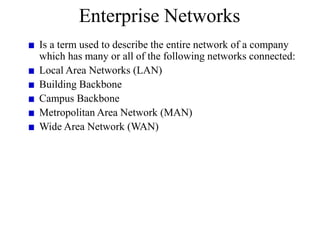
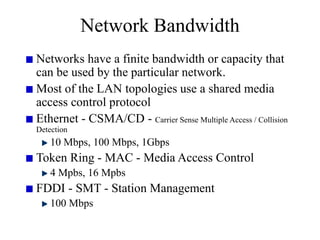
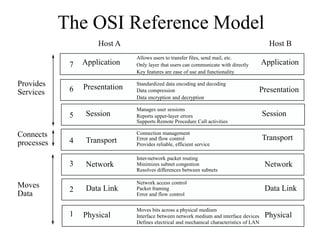
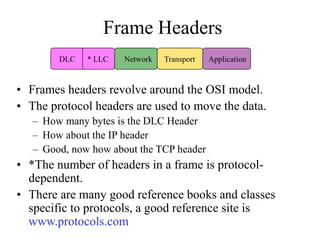
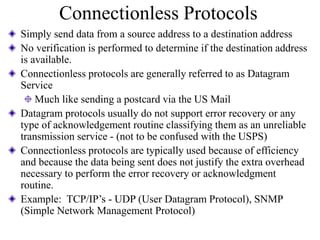
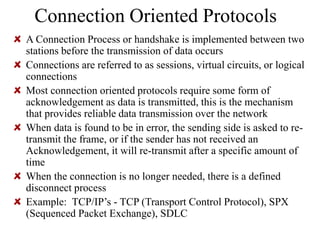
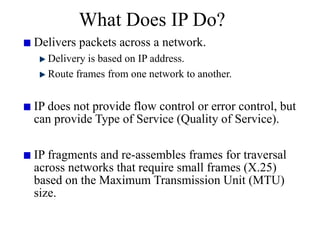
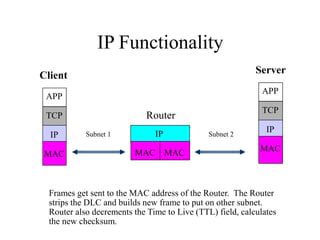
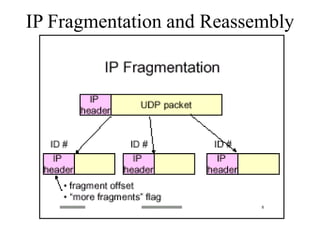
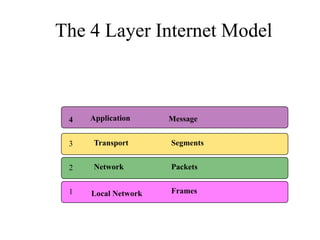
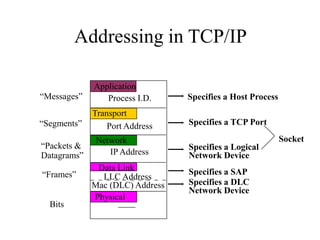
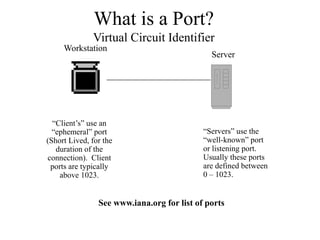
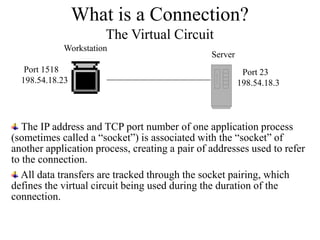
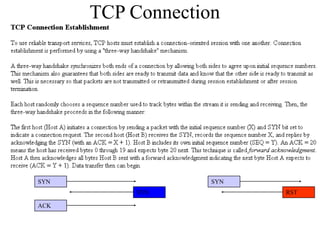
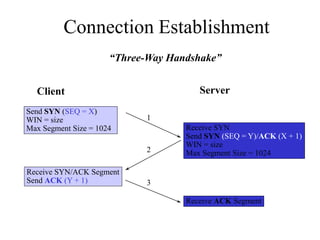
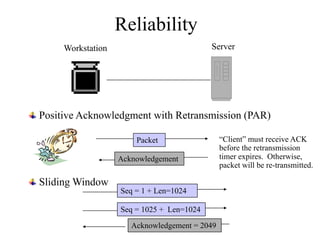
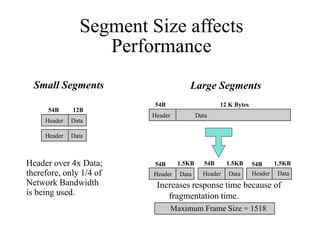
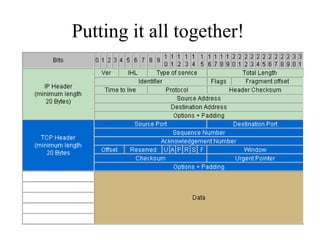
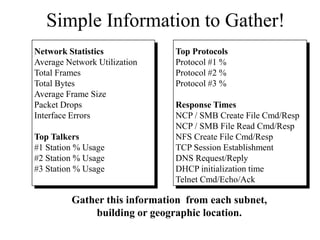
Everything you need to know about network troubleshooting can be learned in elementary school. Networking involves hardware and software that allows computers to communicate. No two networks are exactly alike. Basic network components include end stations, applications, and the network itself. The OSI model provides a standard way to understand how data moves through a network via different layers. TCP/IP is the most common network protocol and uses IP for addressing and routing and TCP for reliable data delivery. Gathering basic network statistics is an important part of troubleshooting.