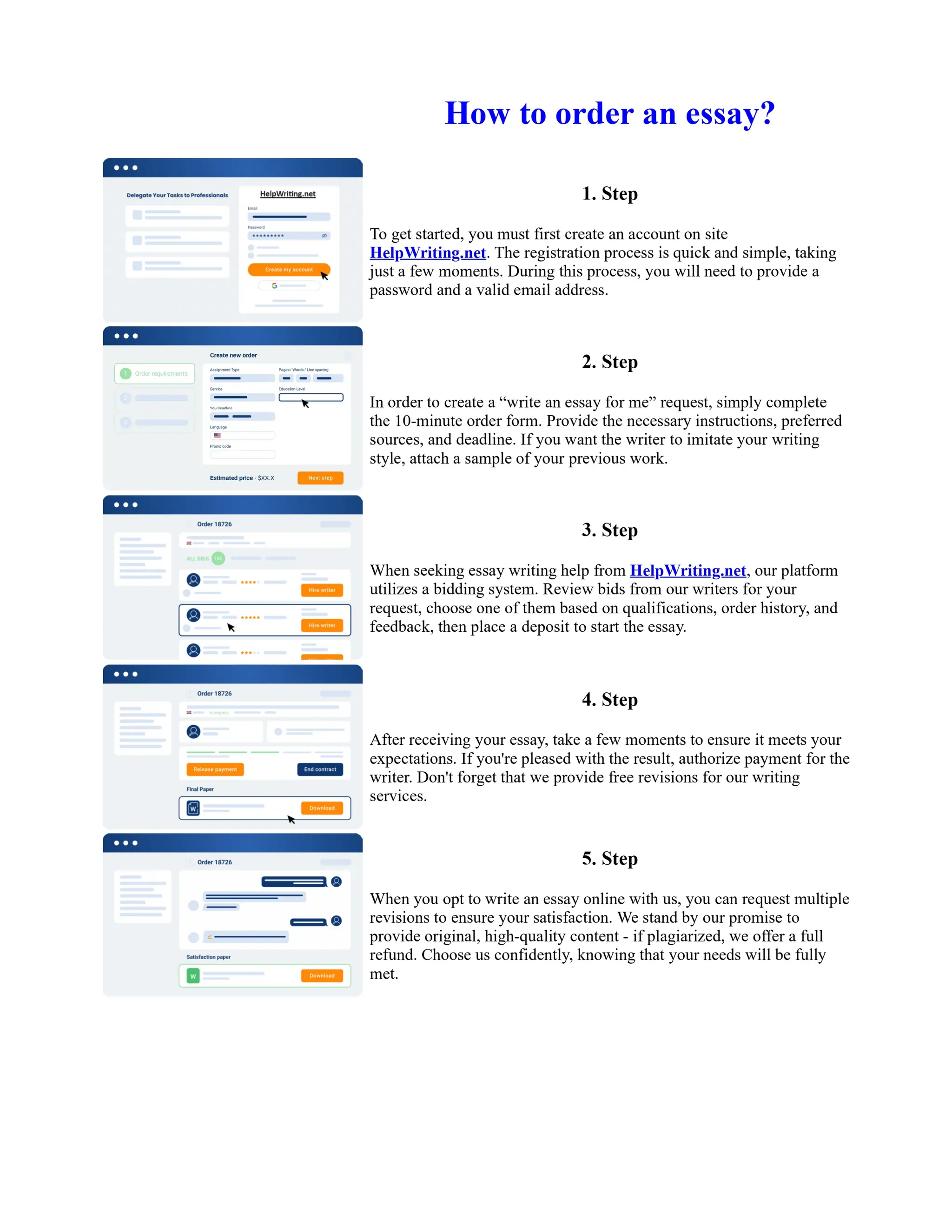
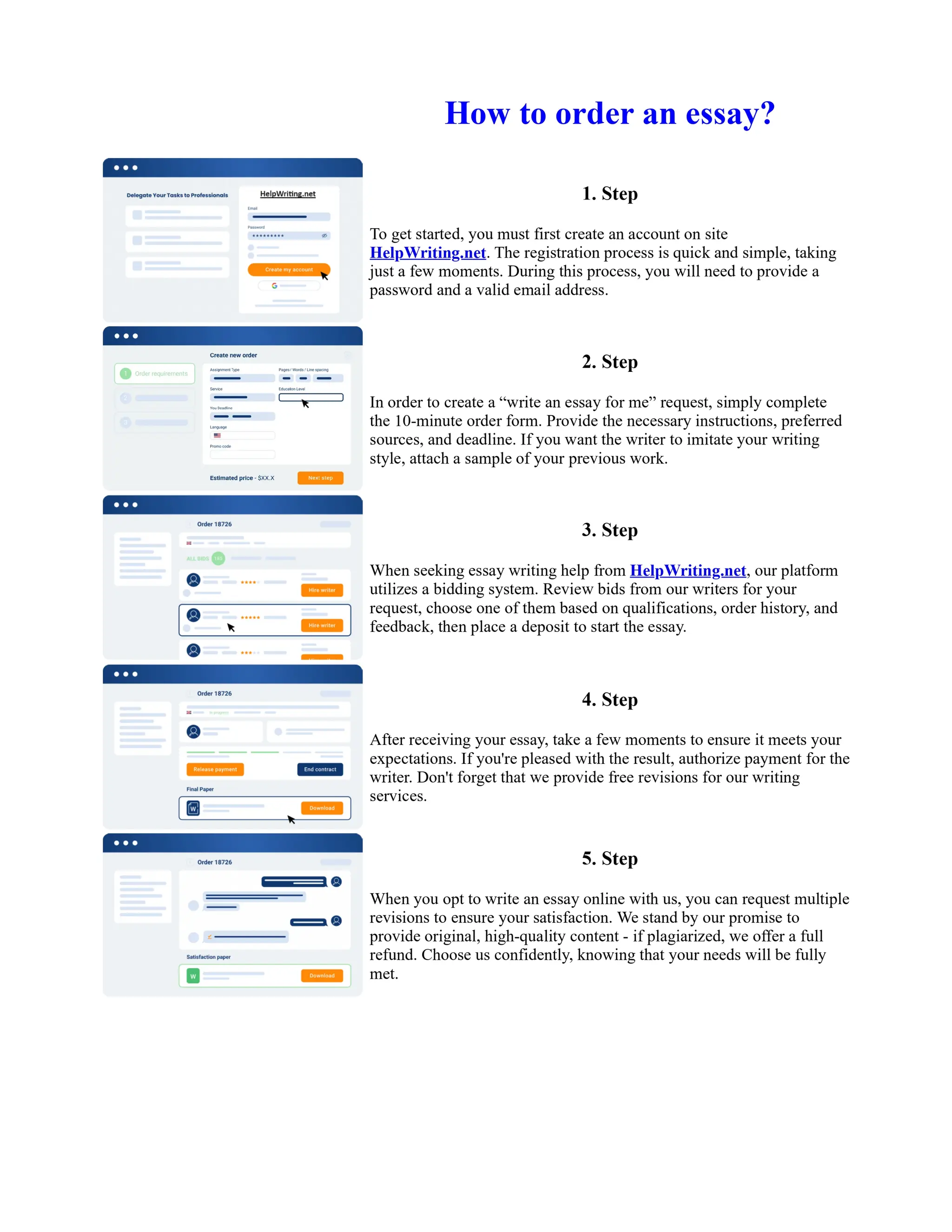
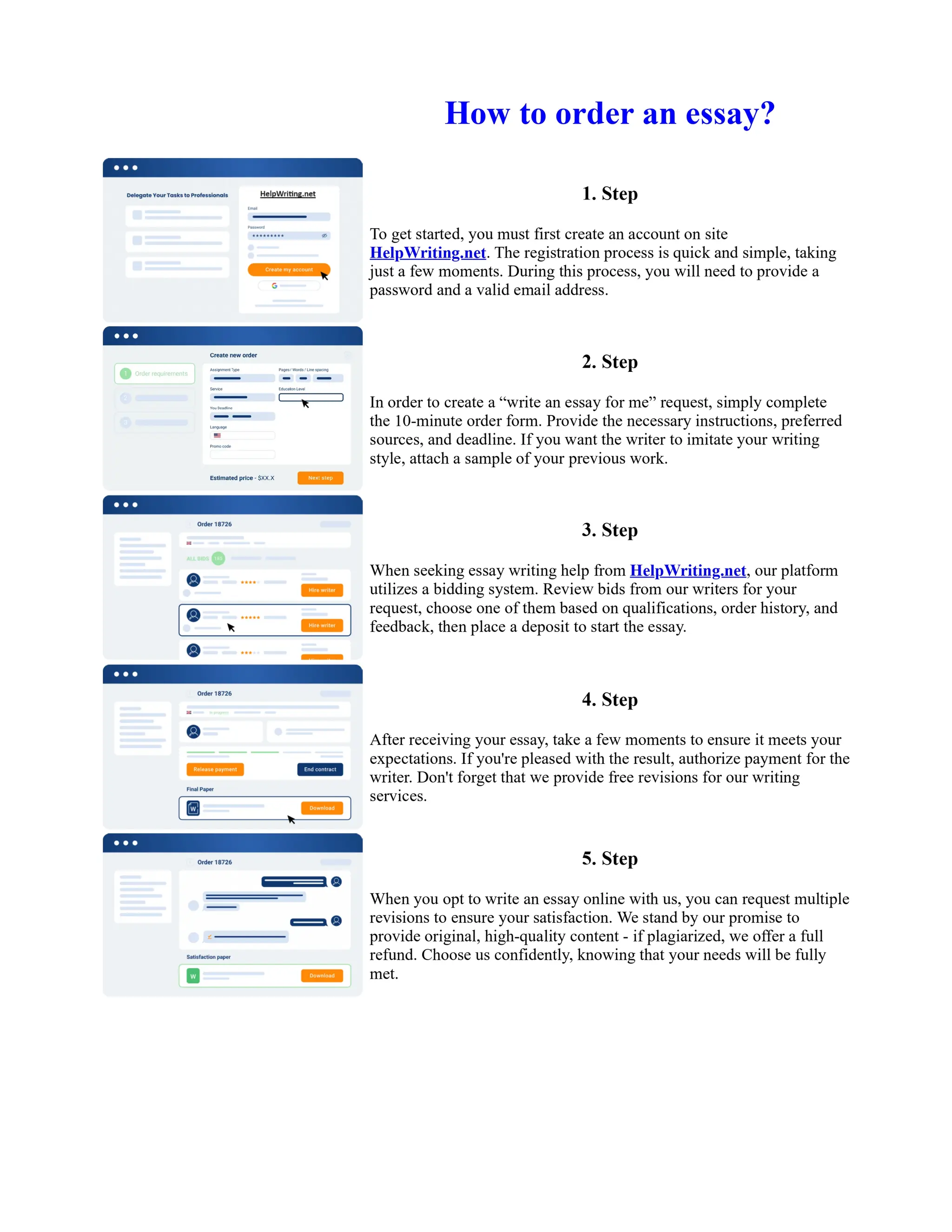
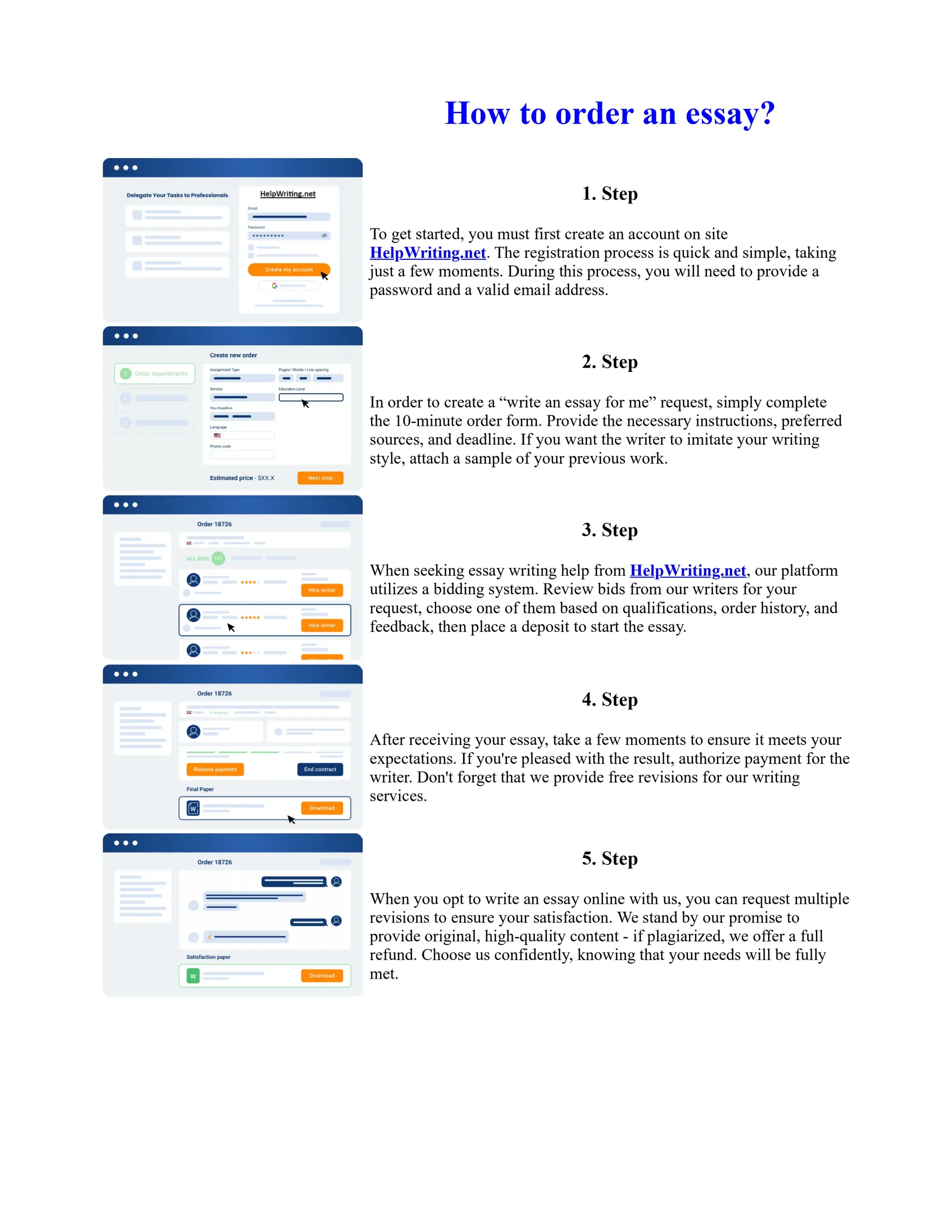
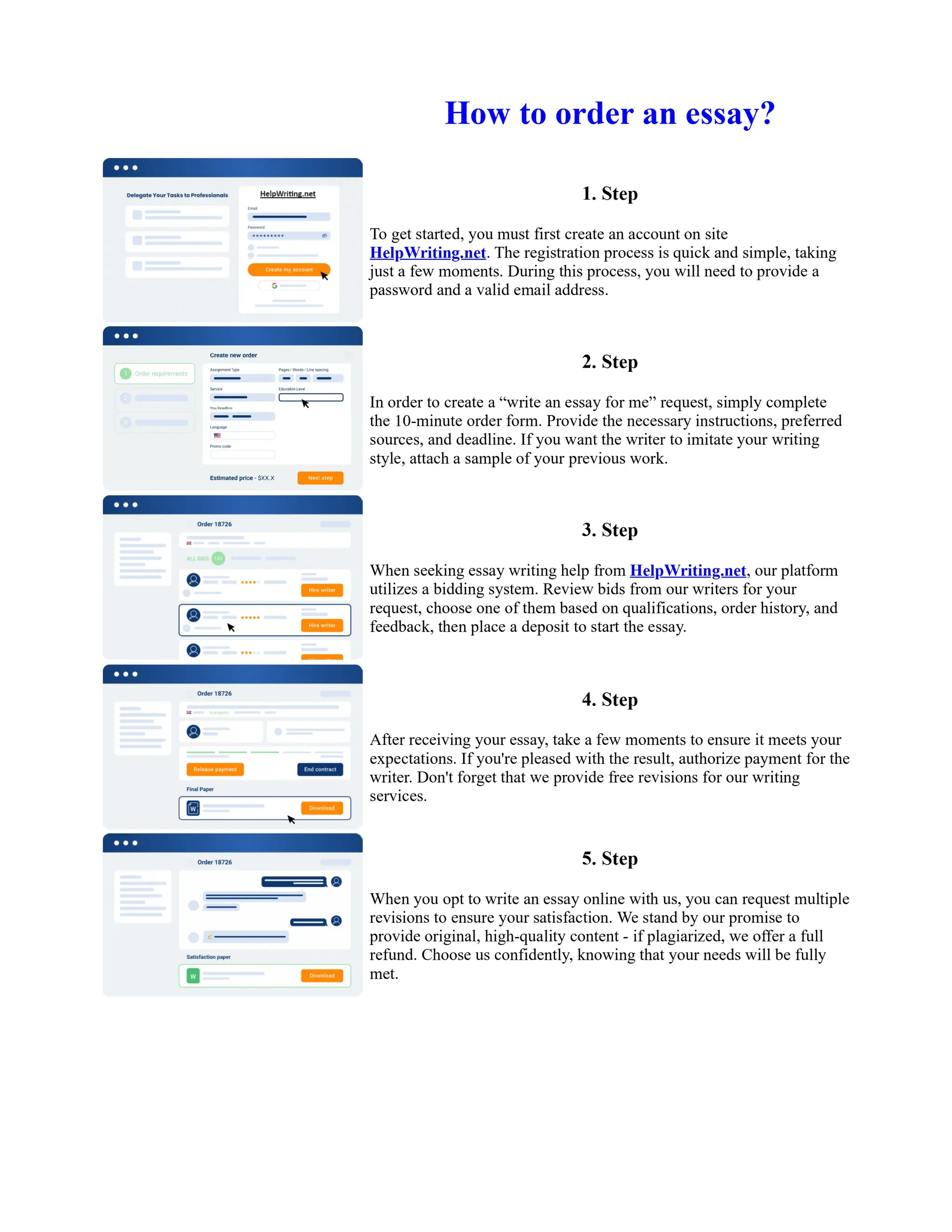
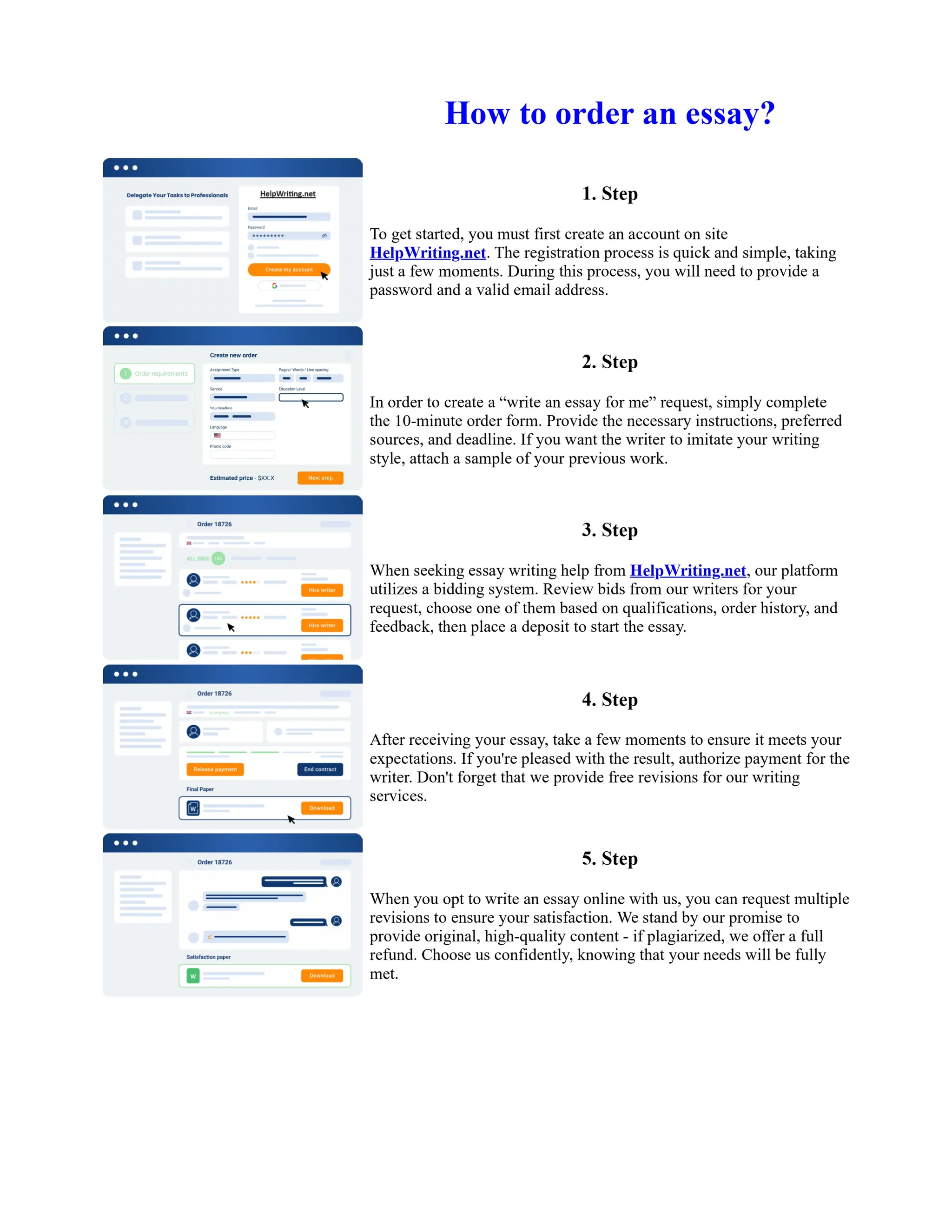
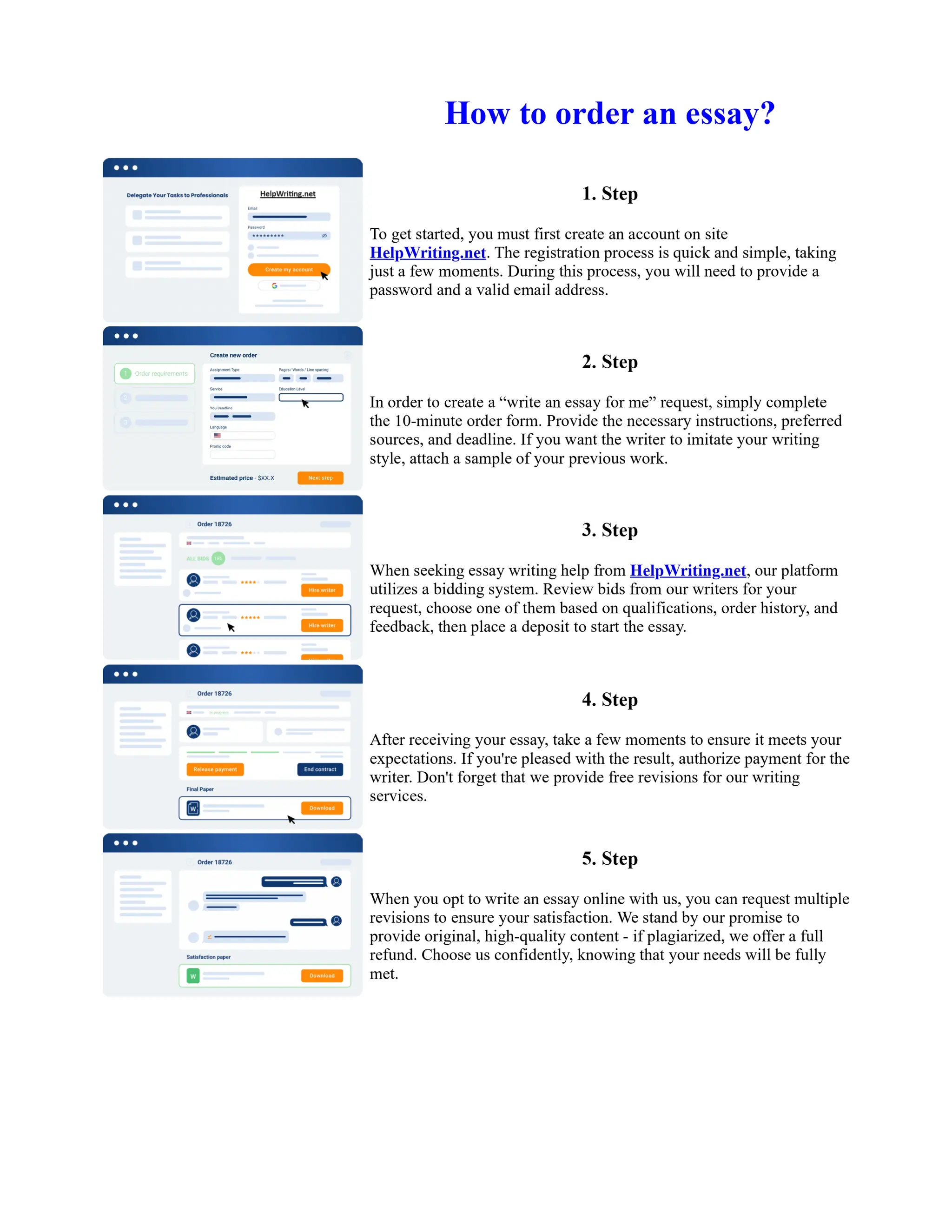
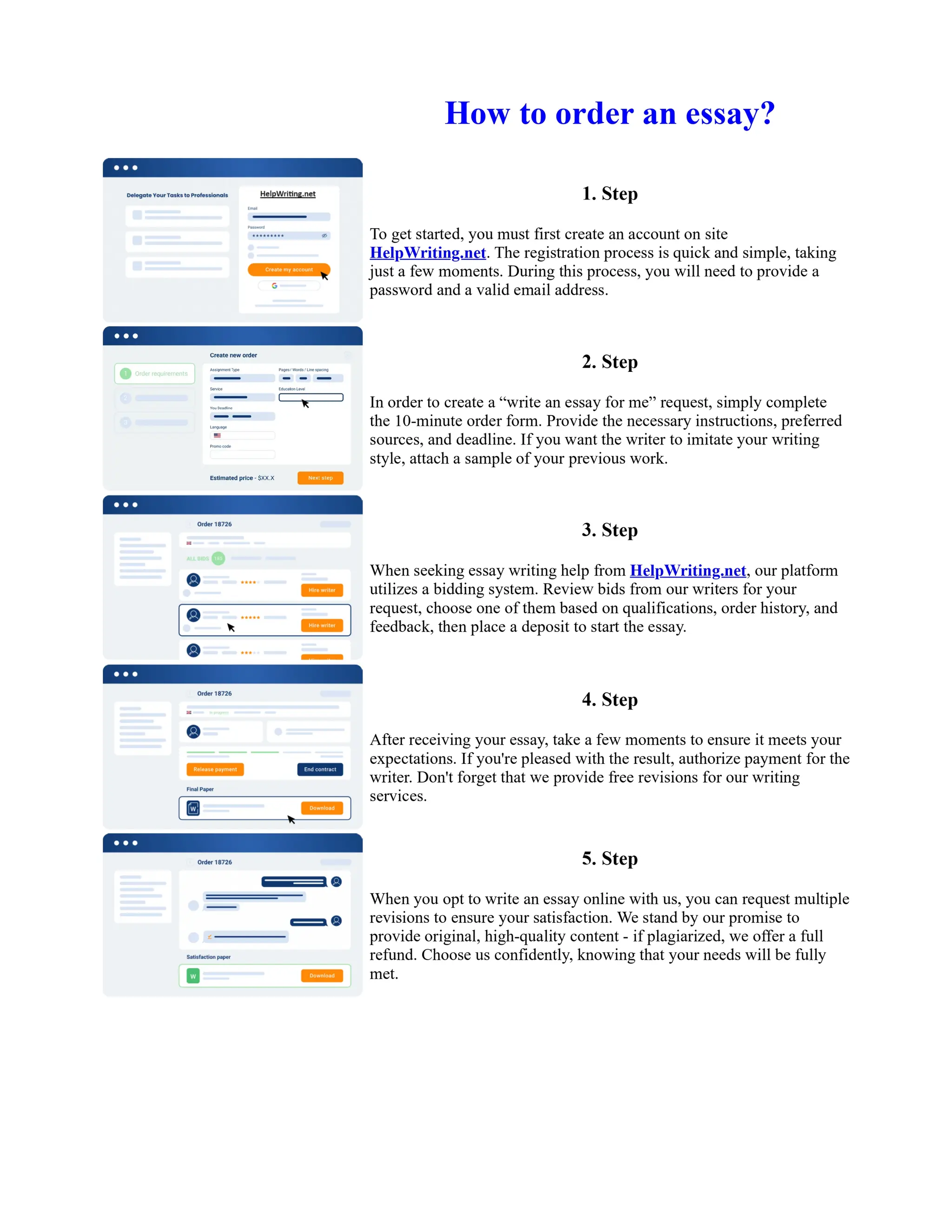
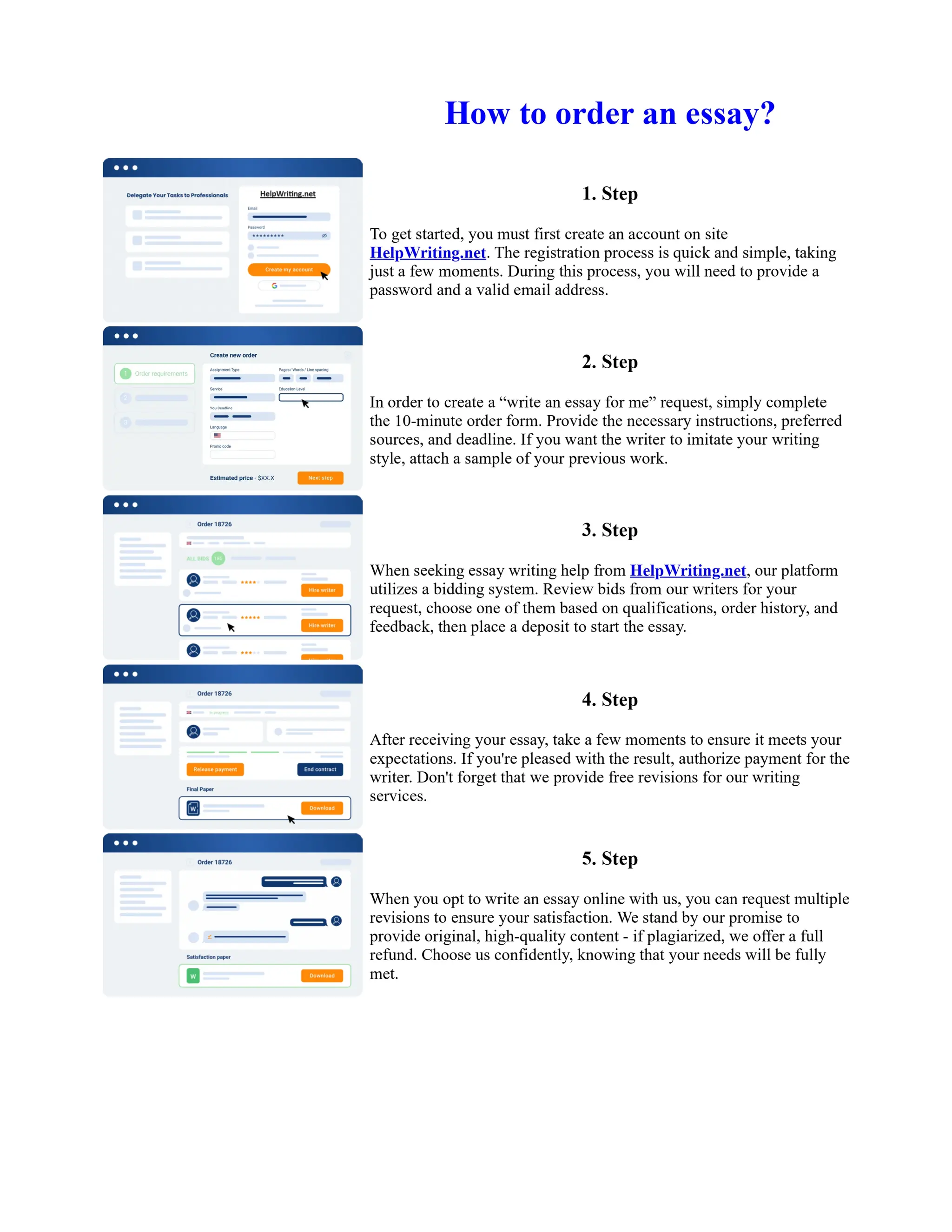
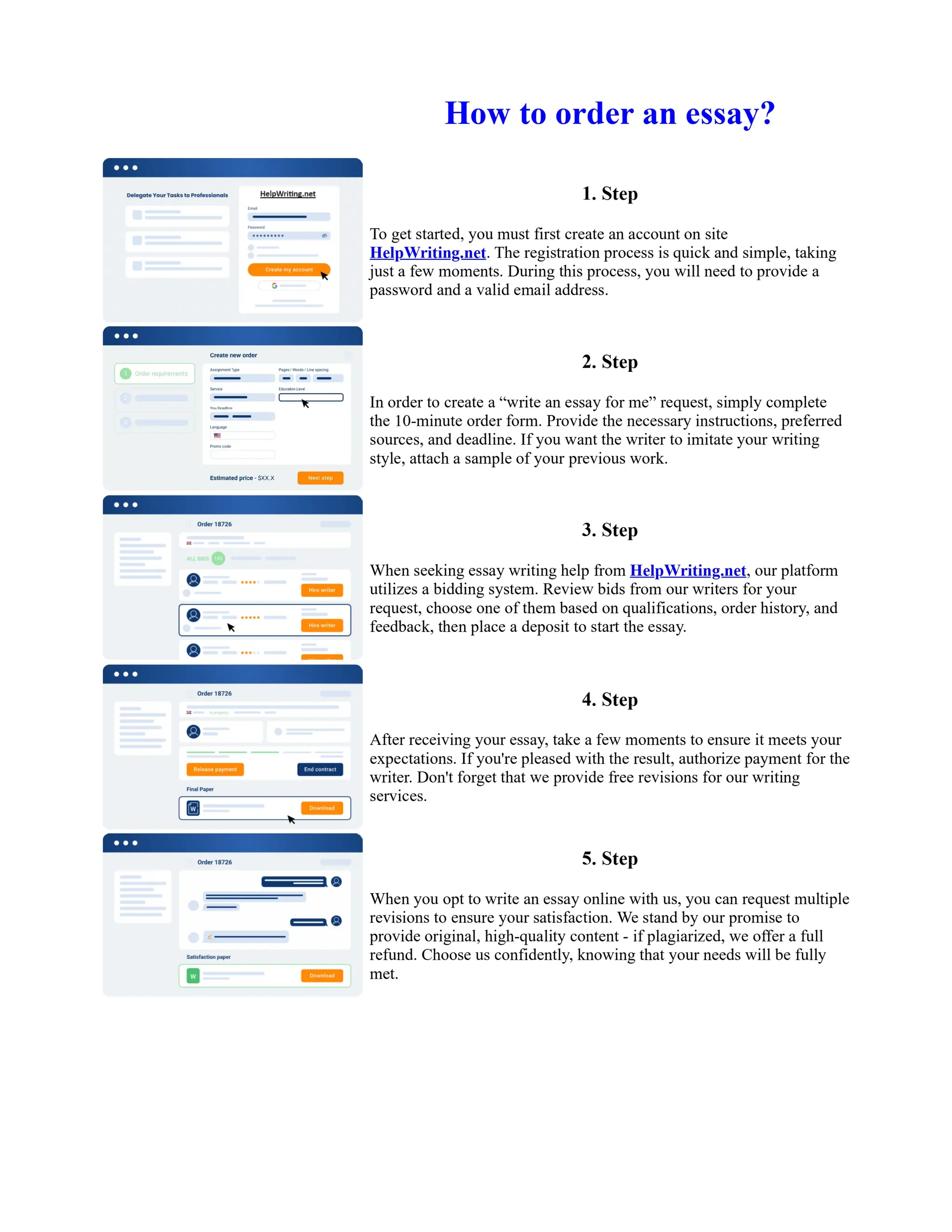
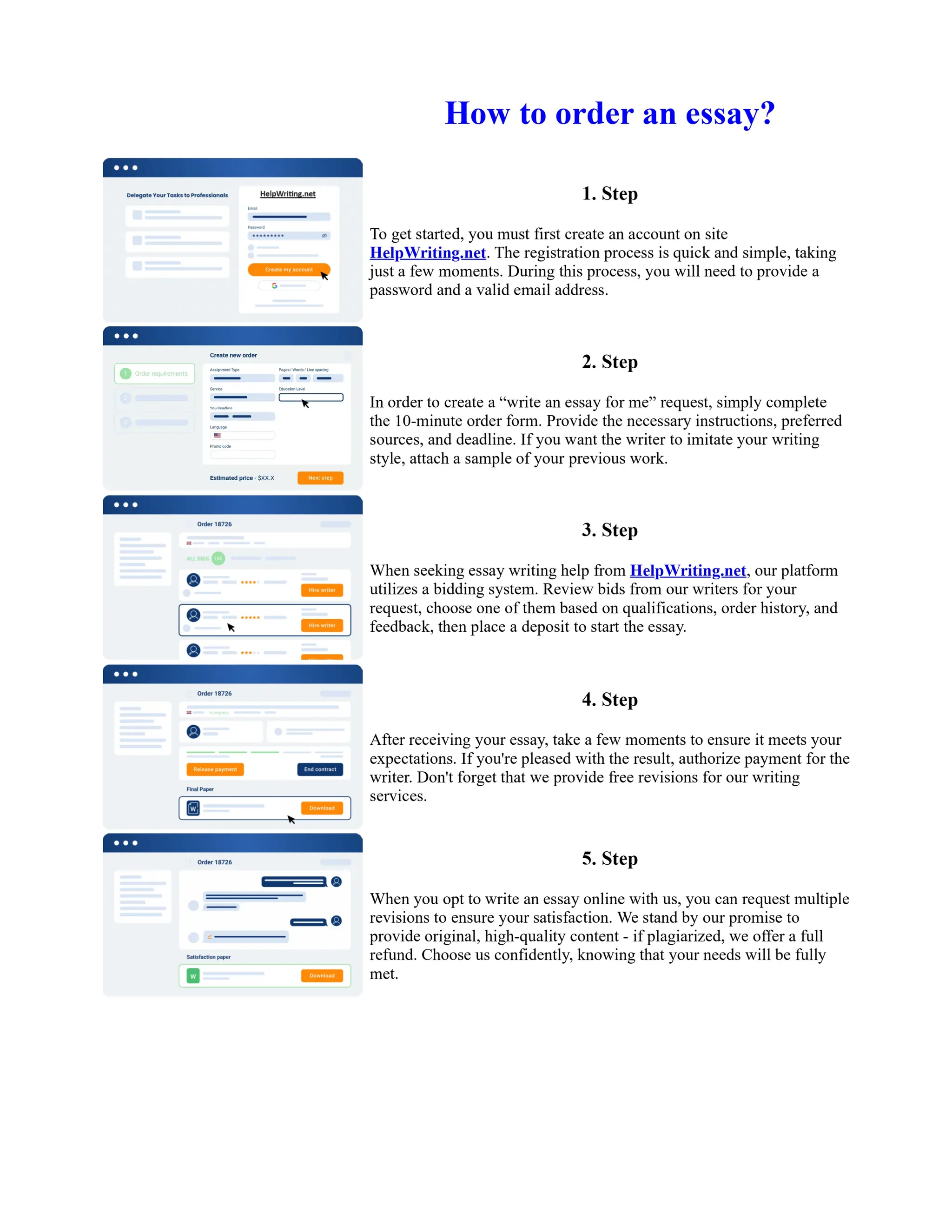
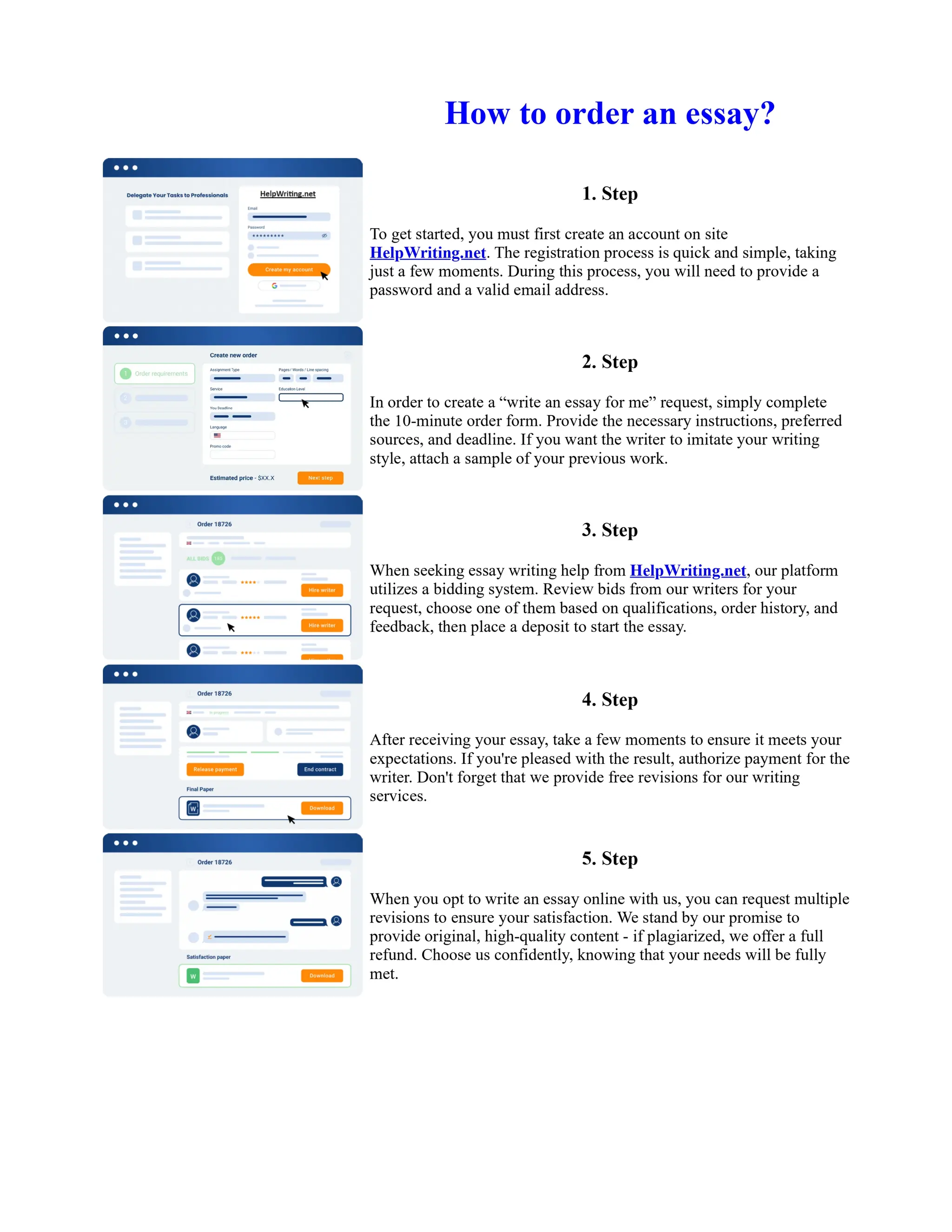
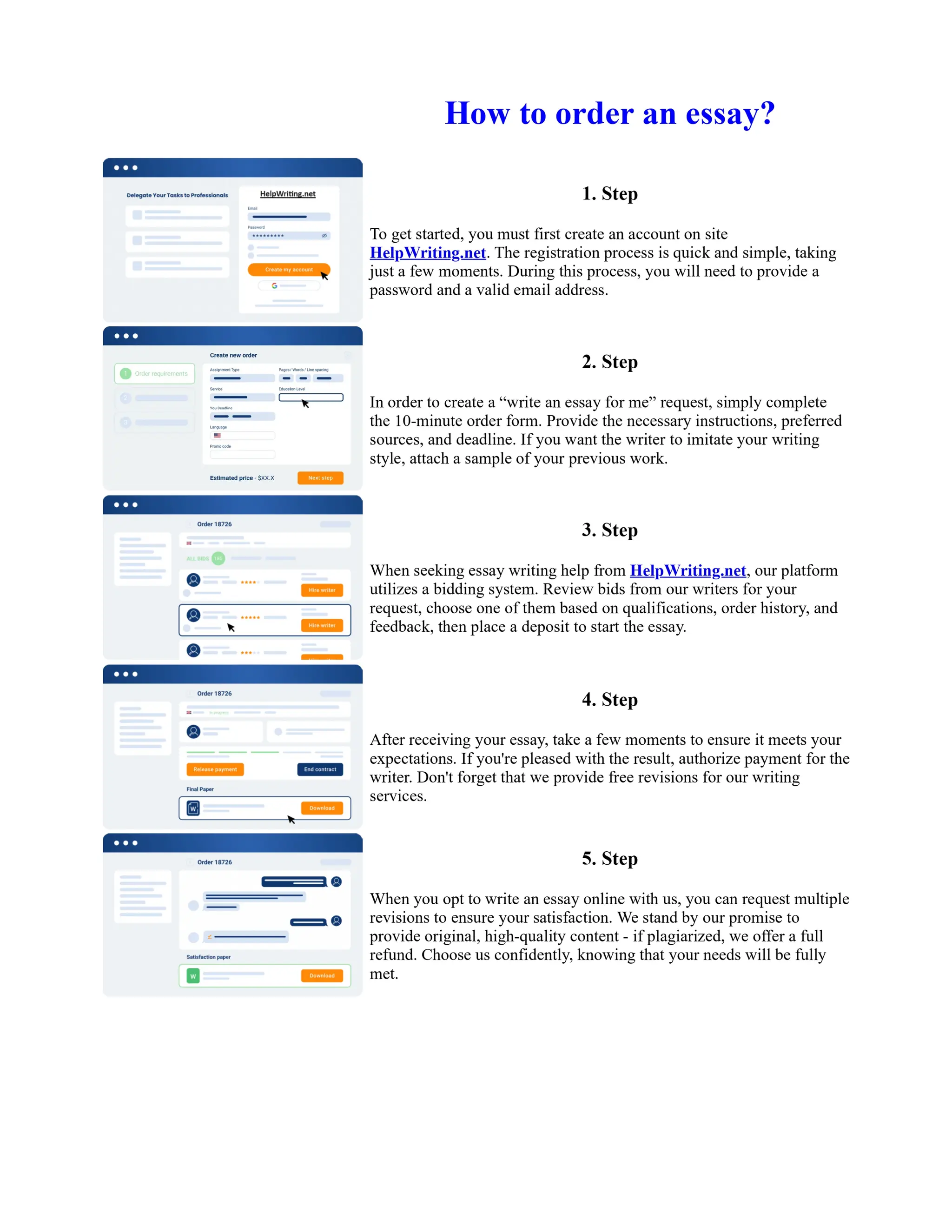
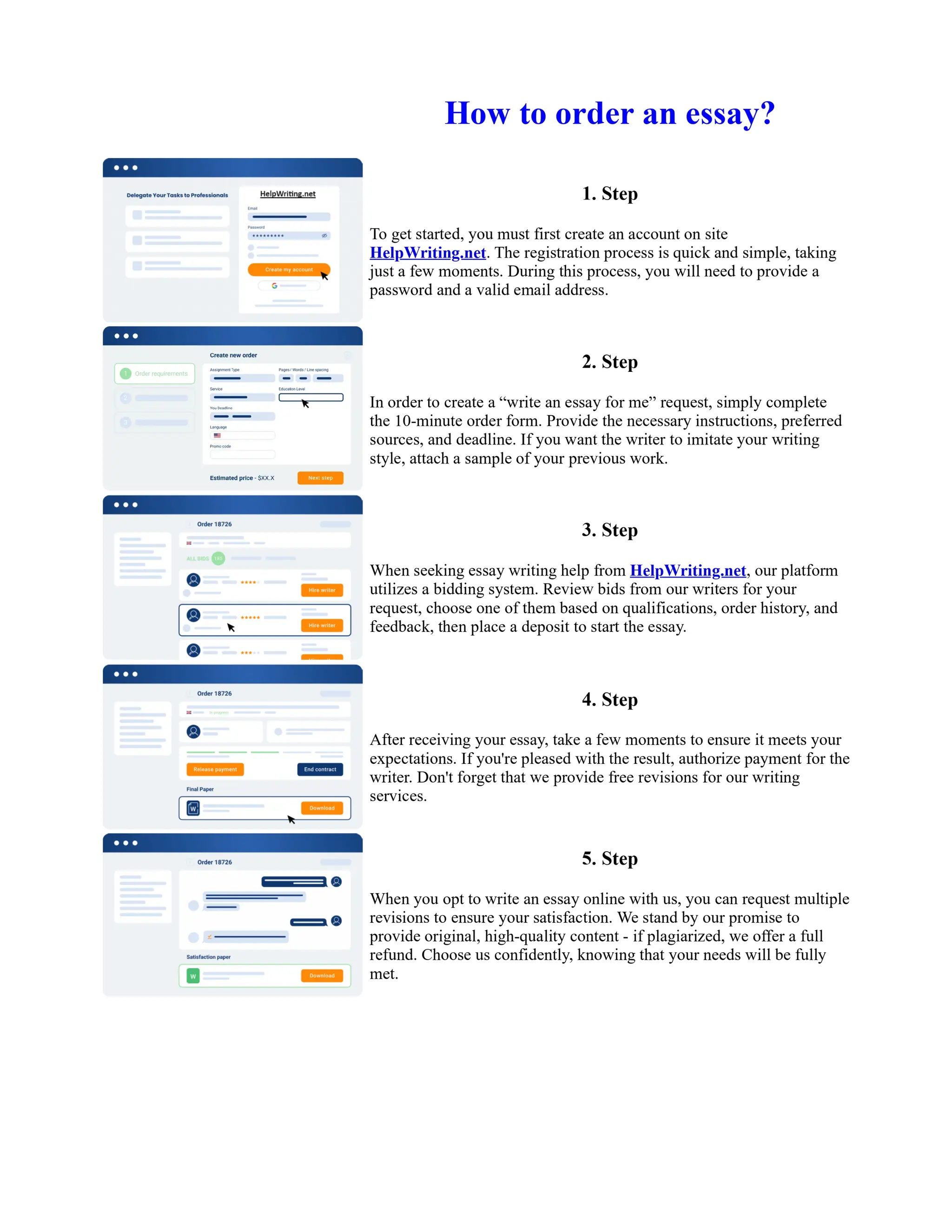
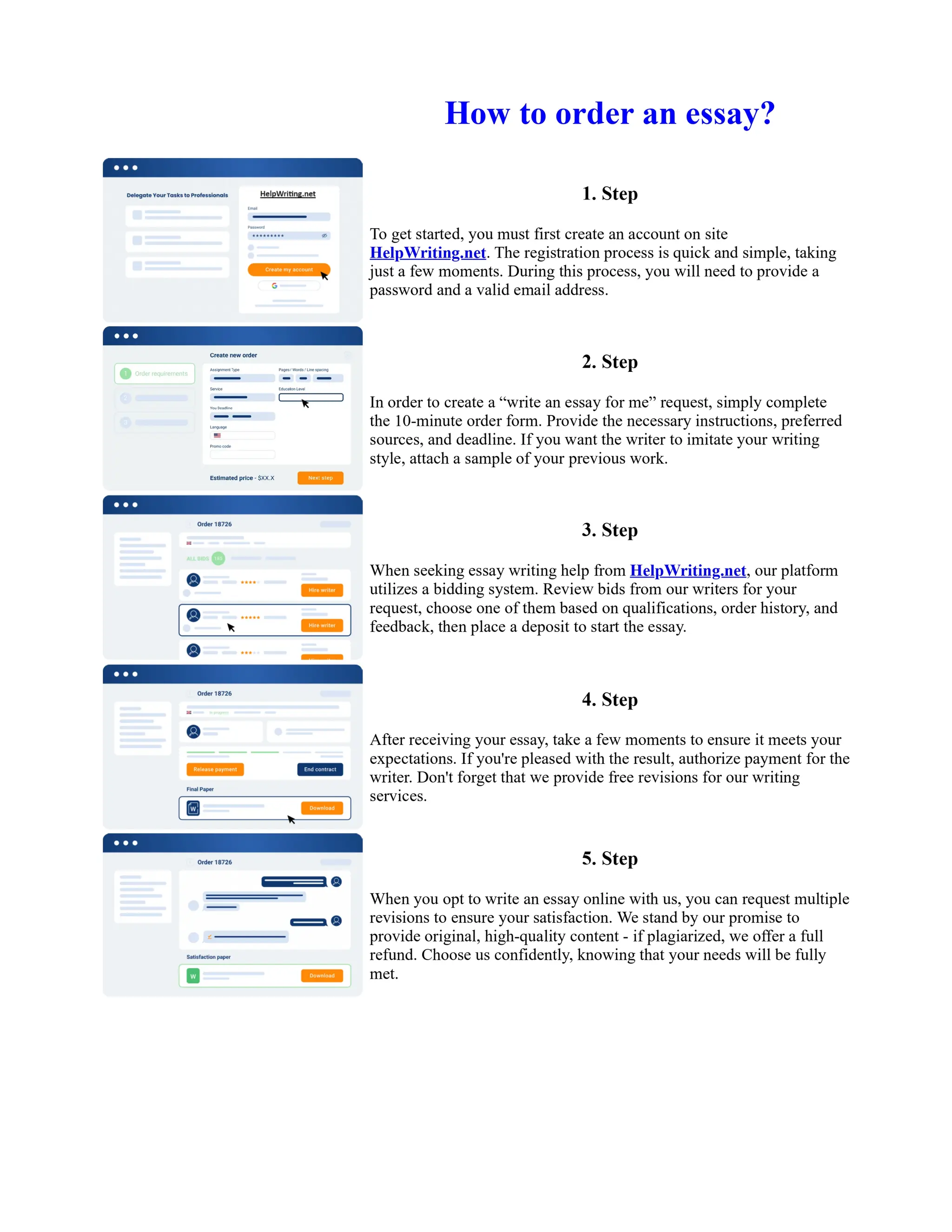
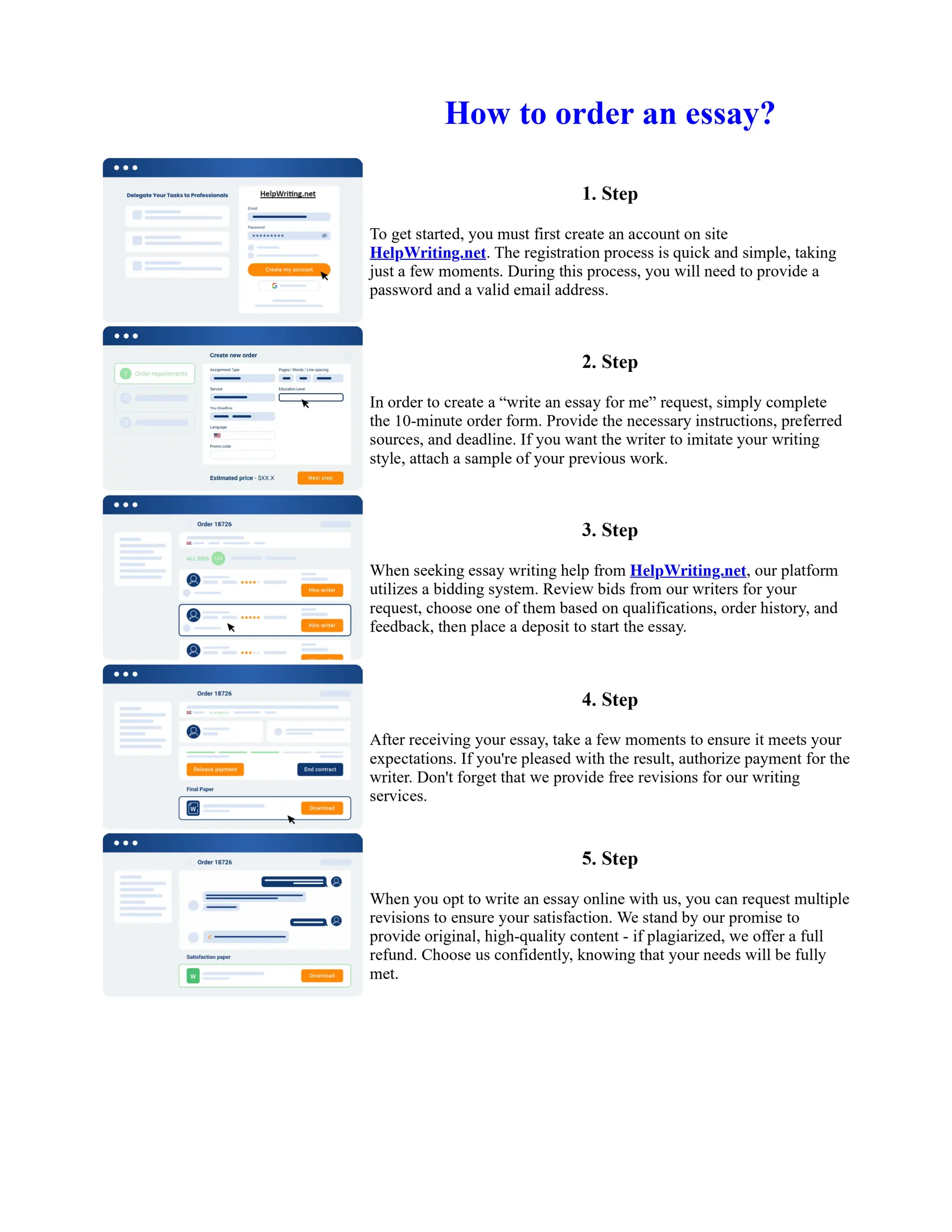
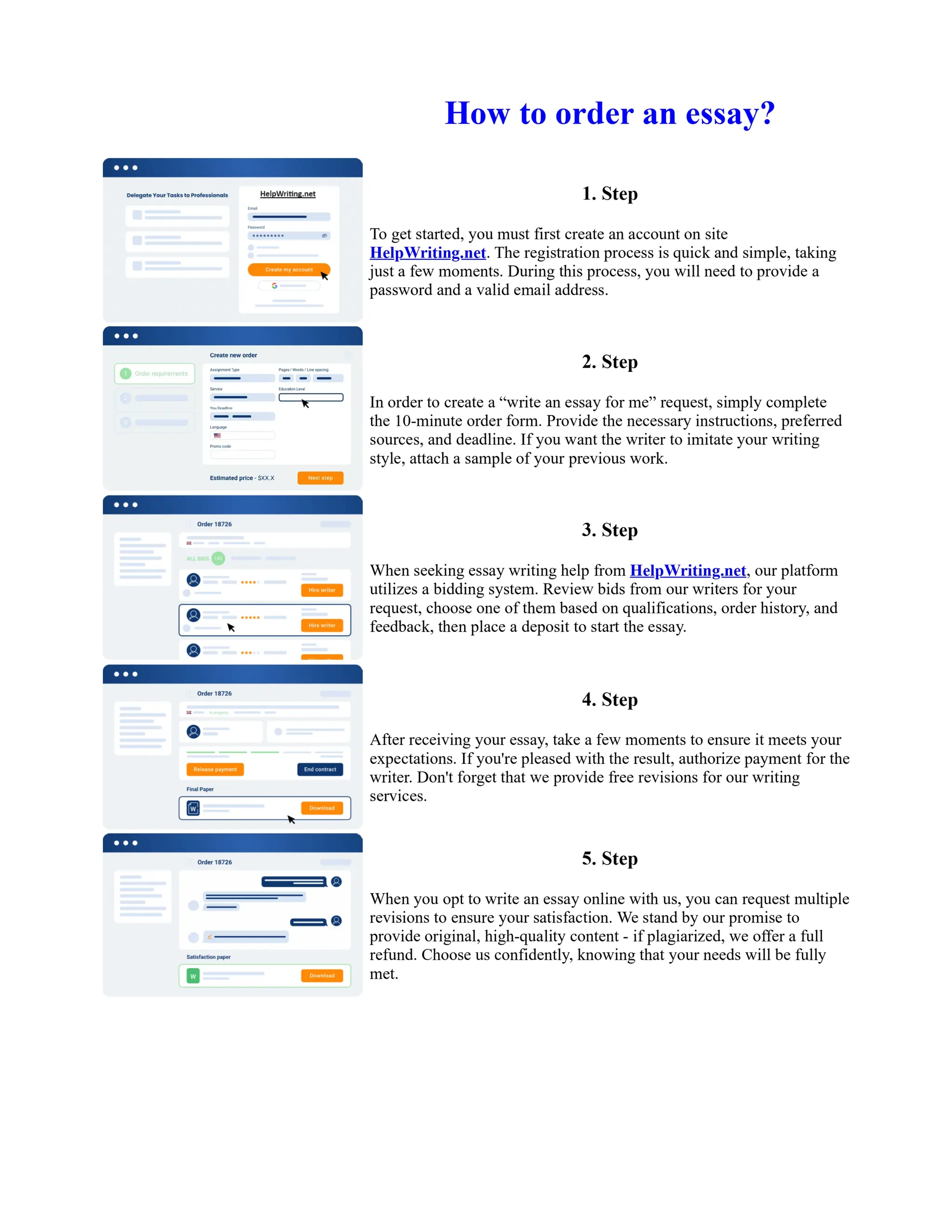
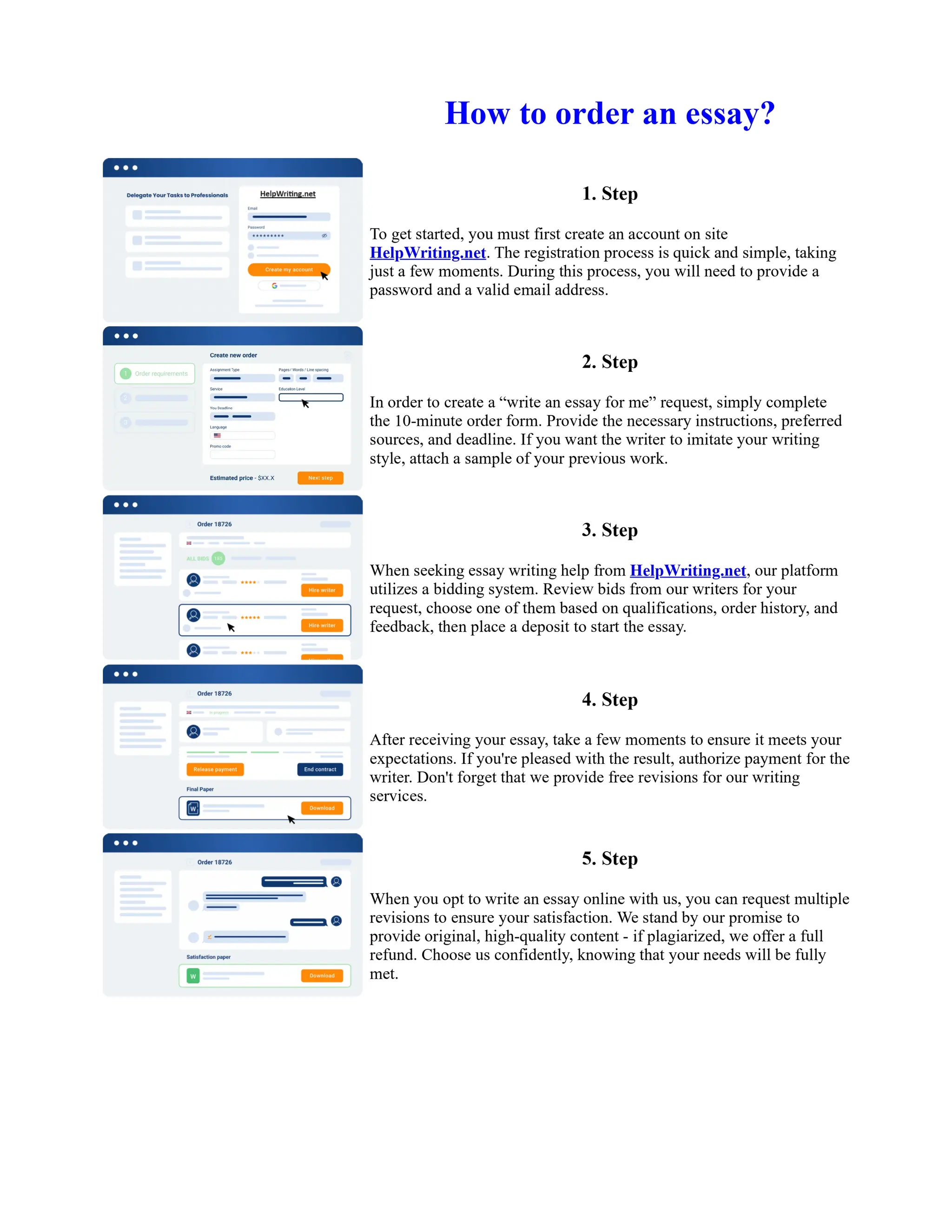
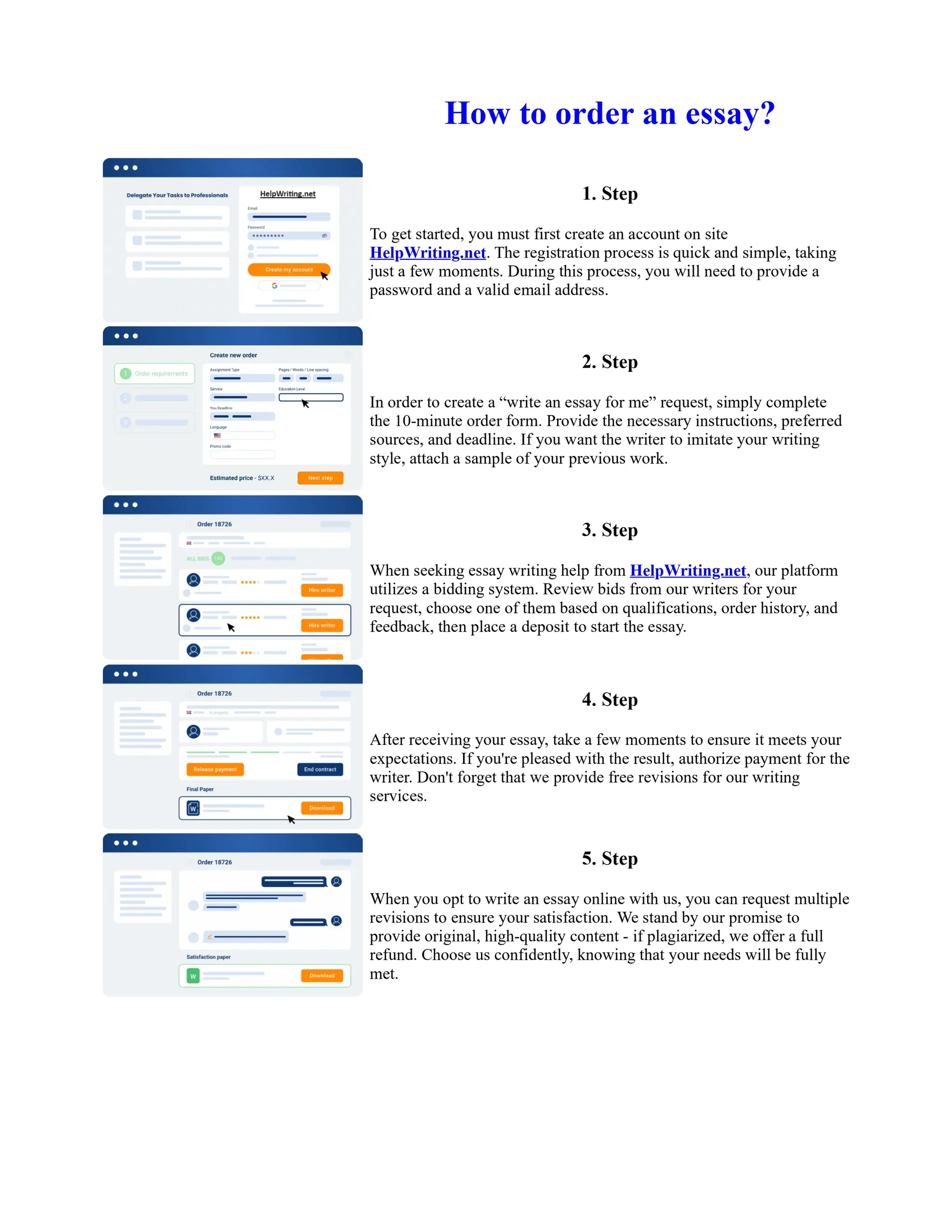
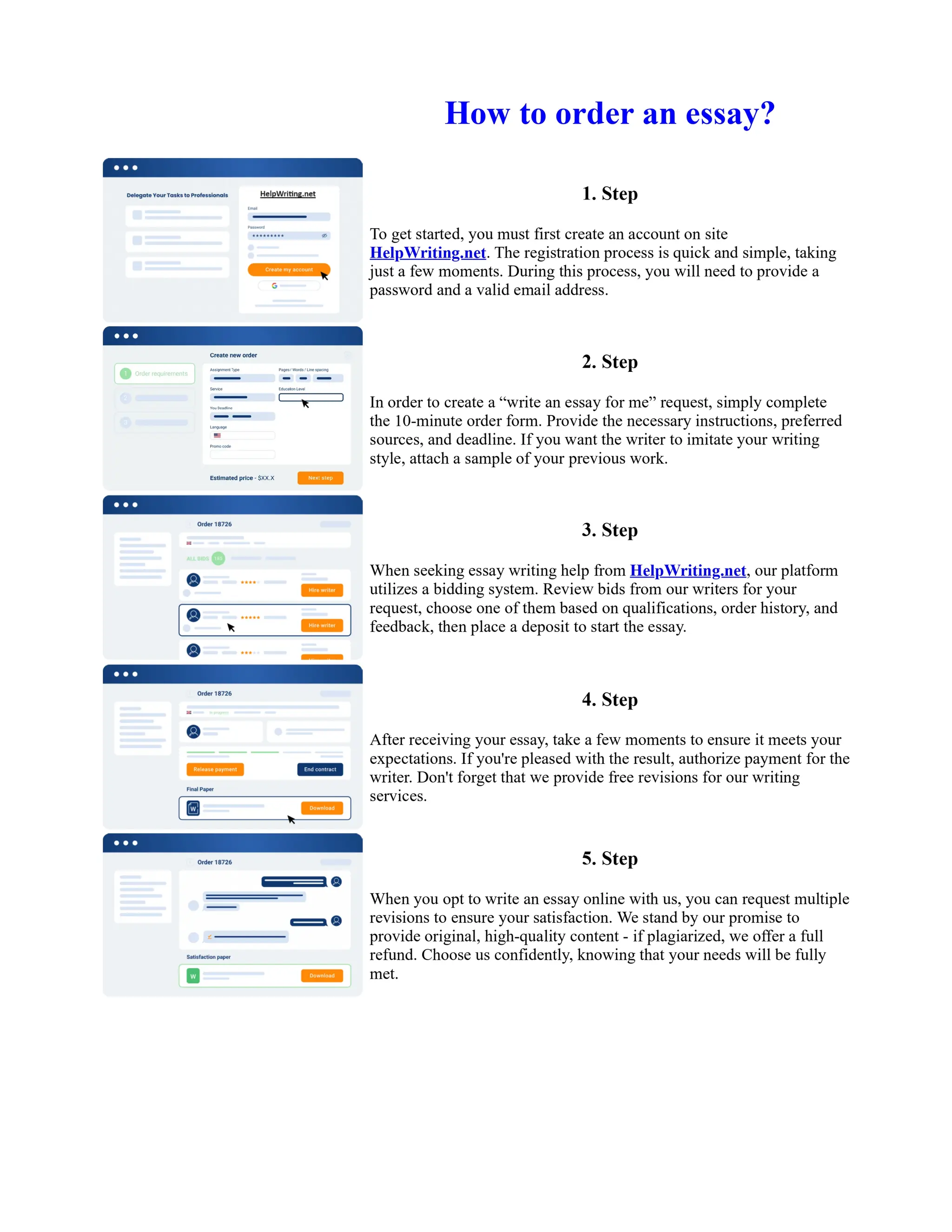
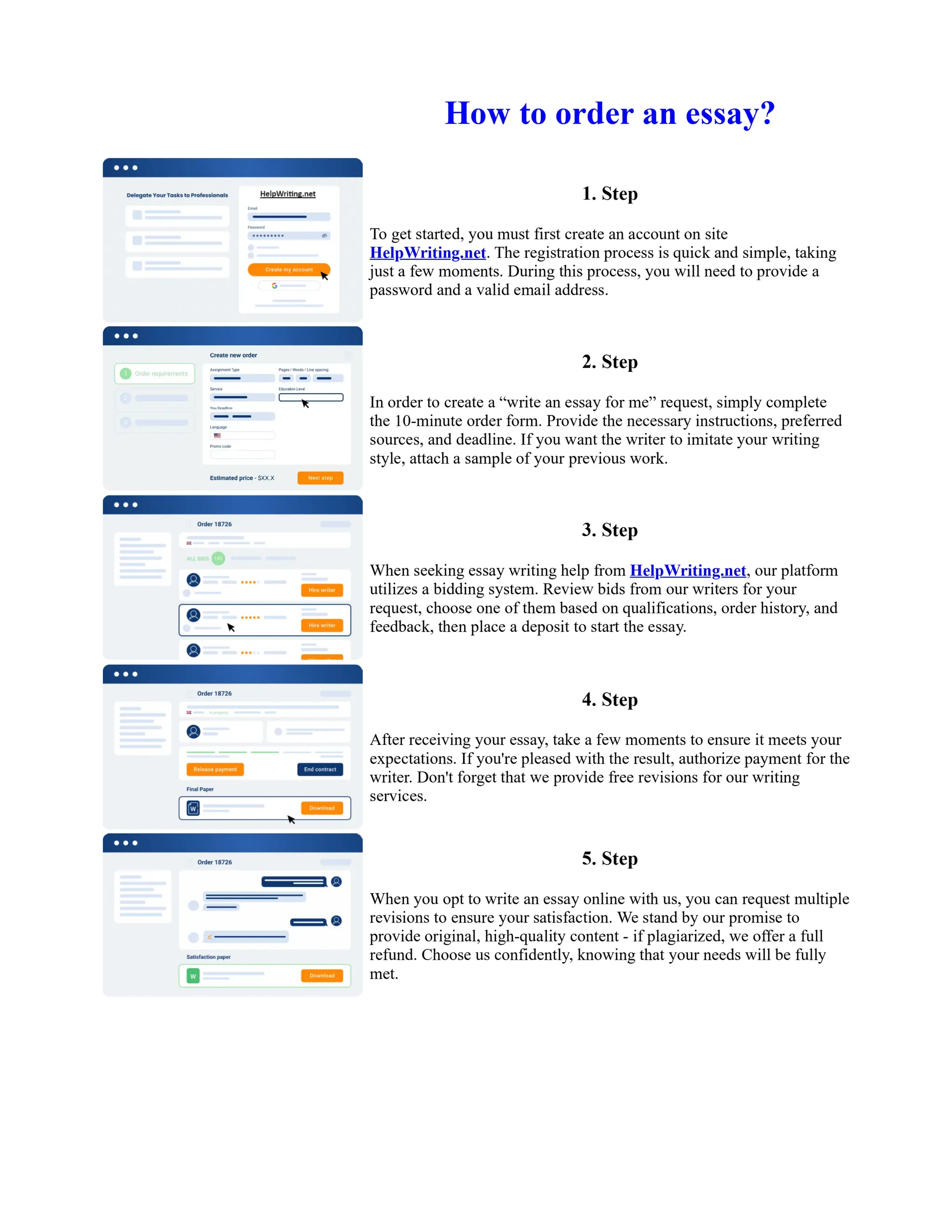
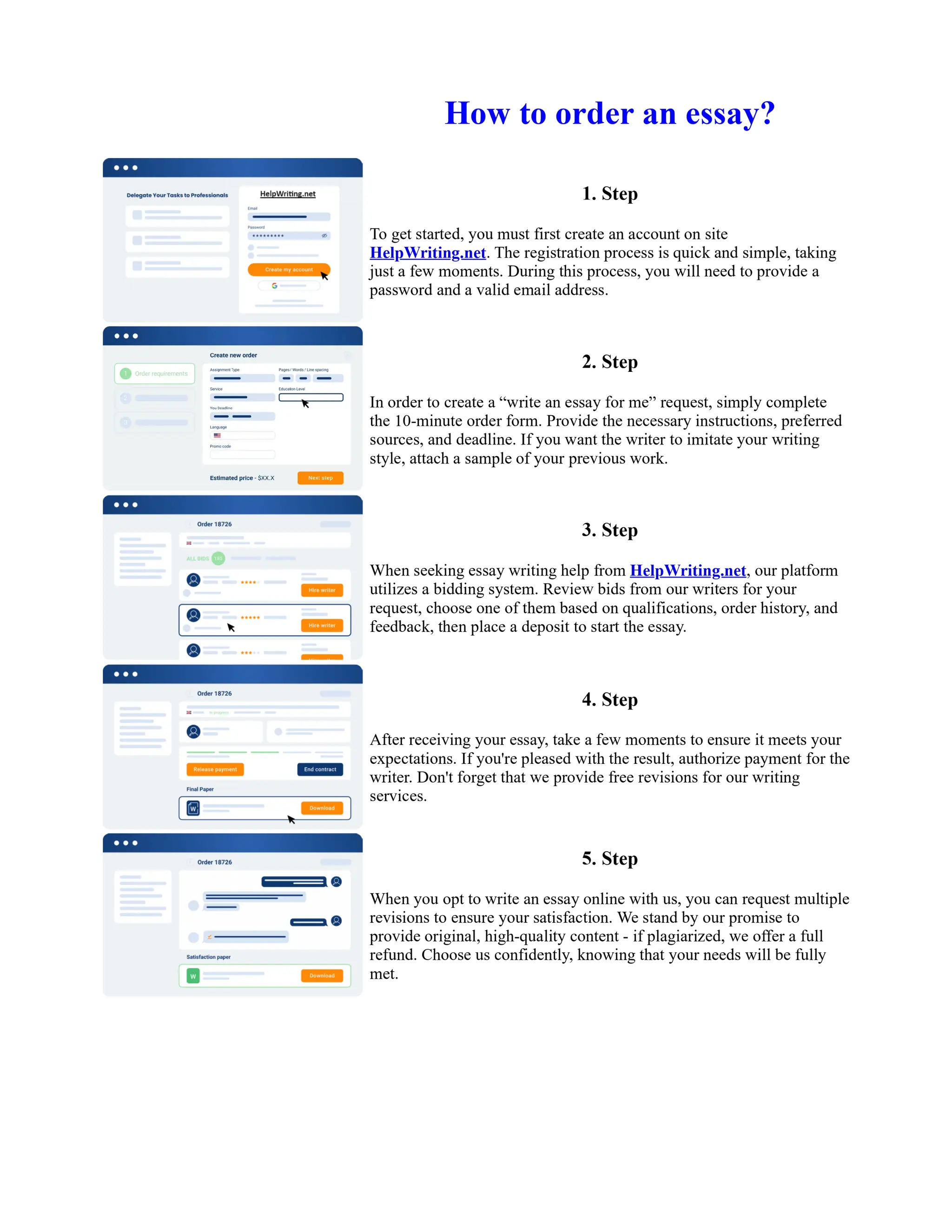
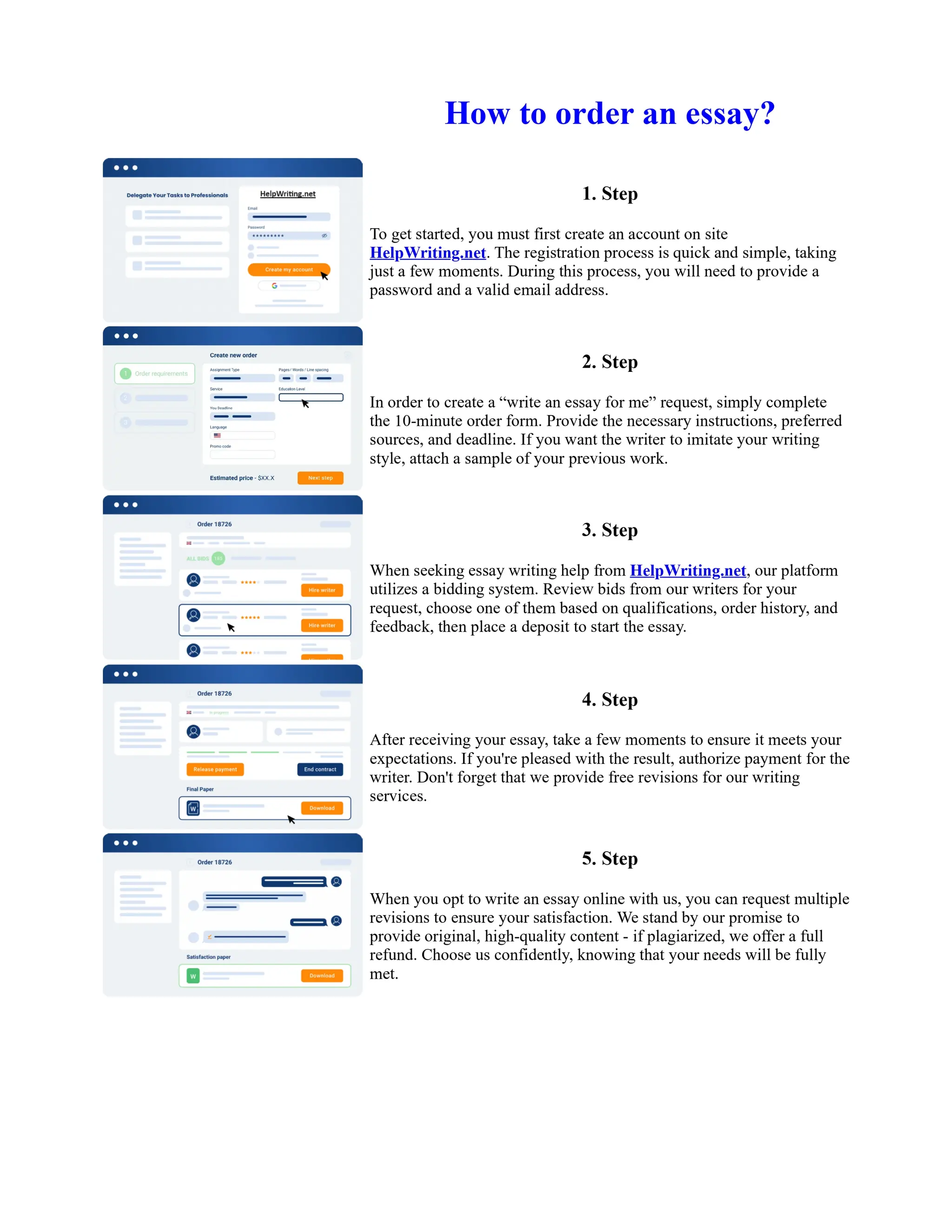
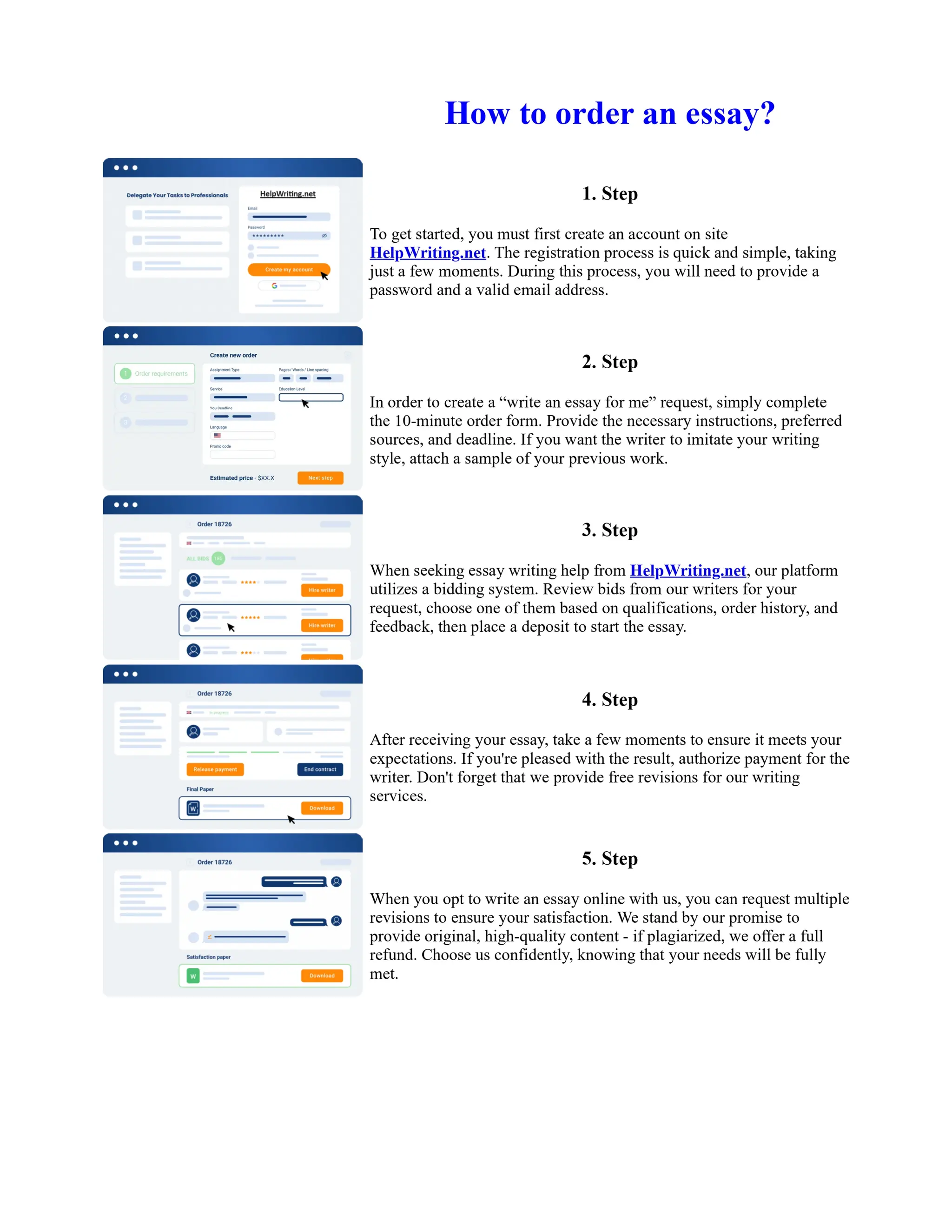
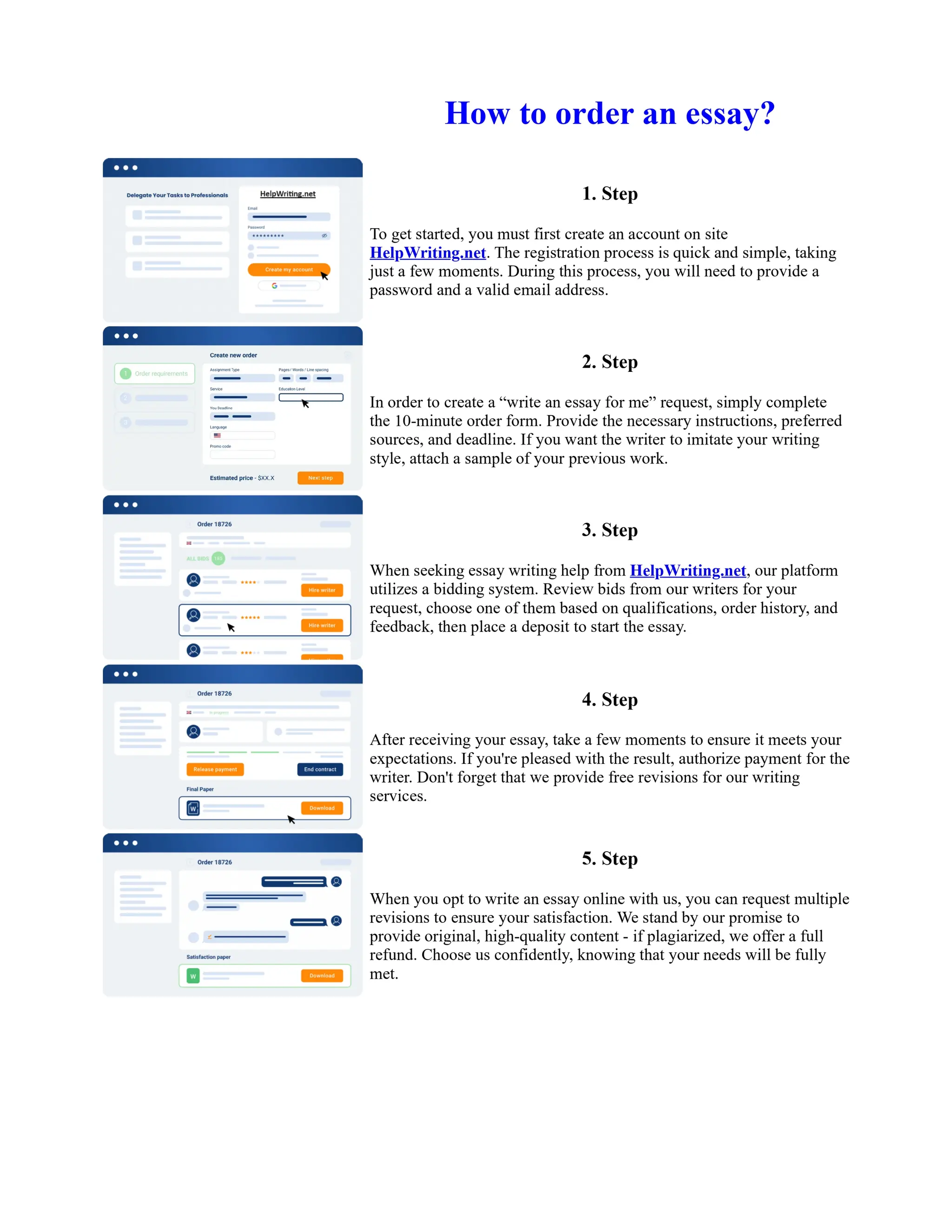
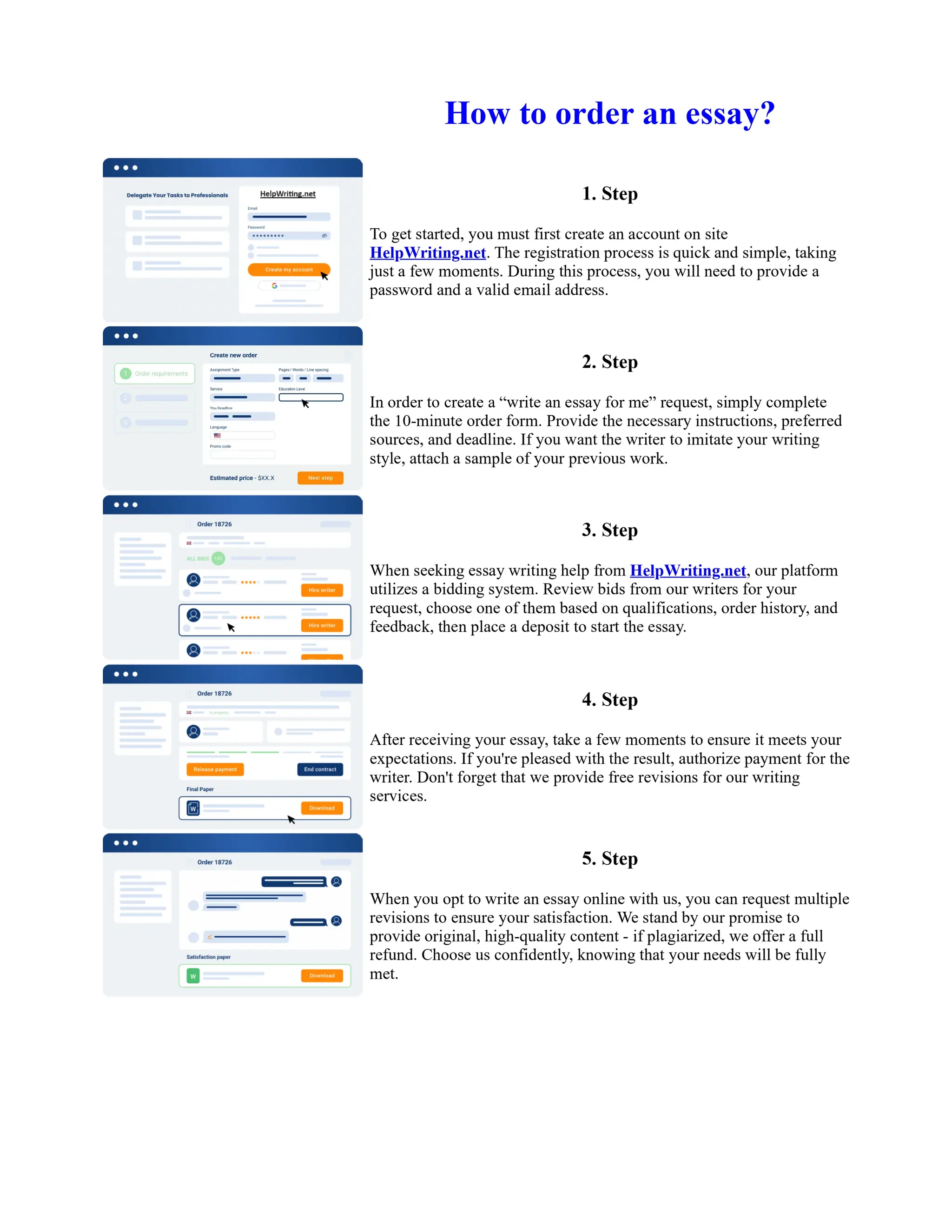
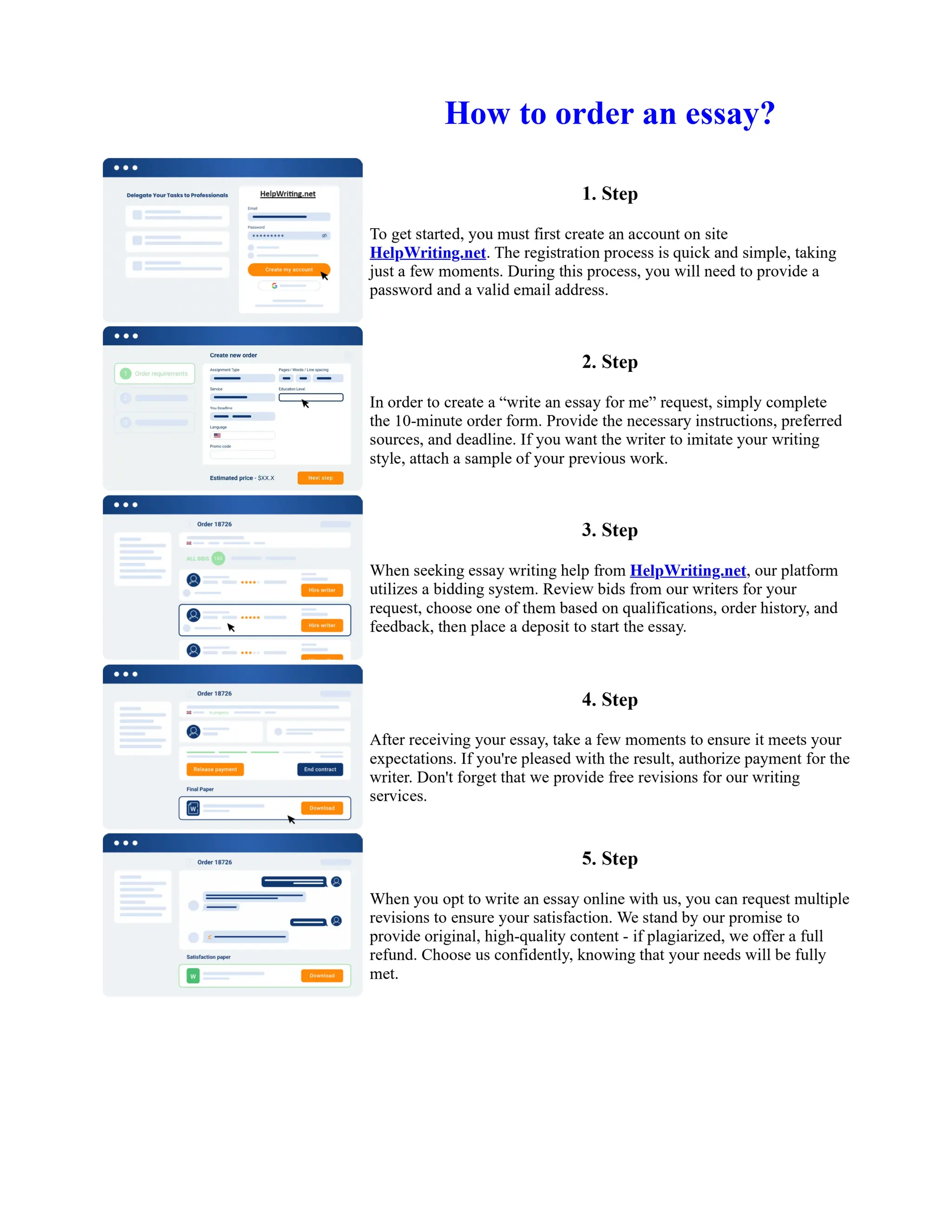
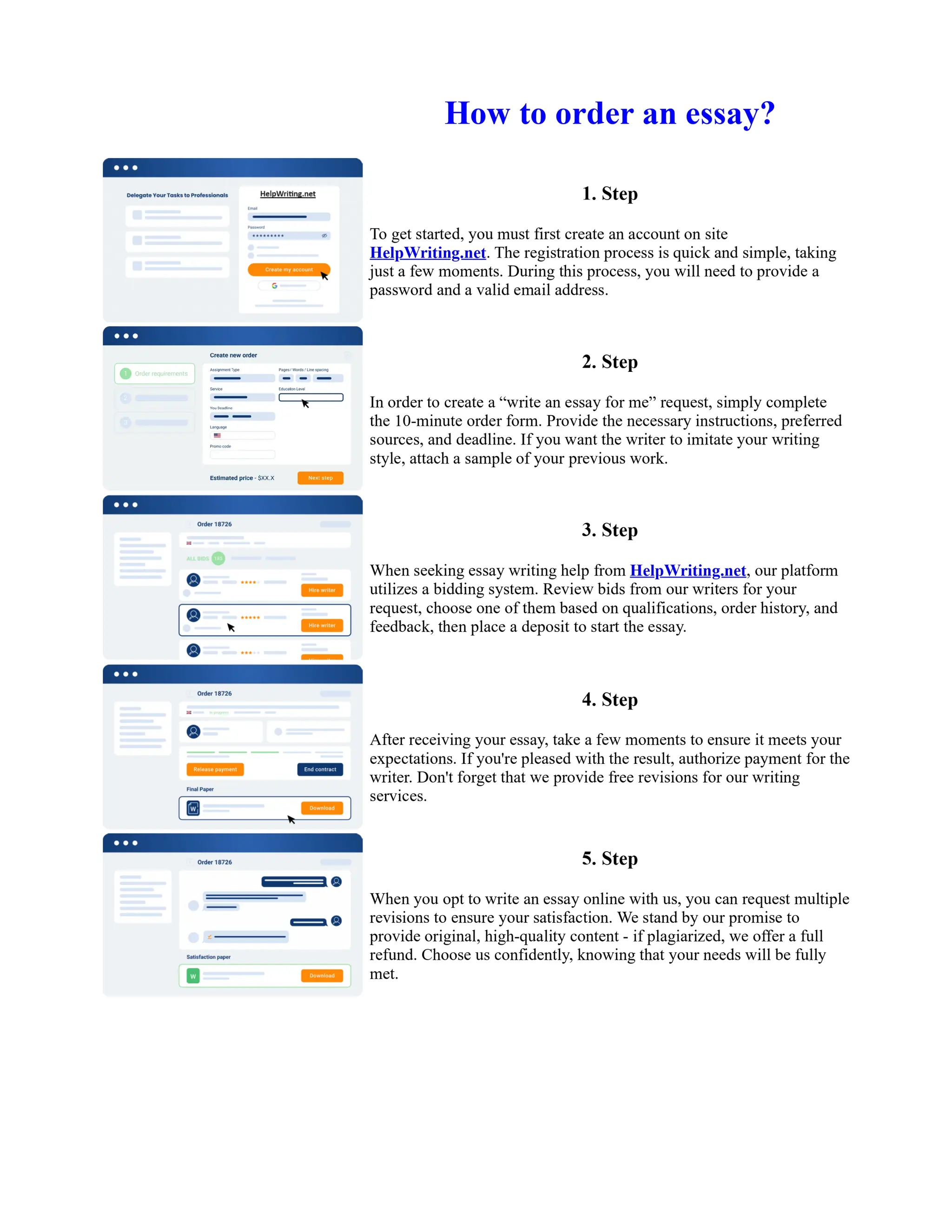
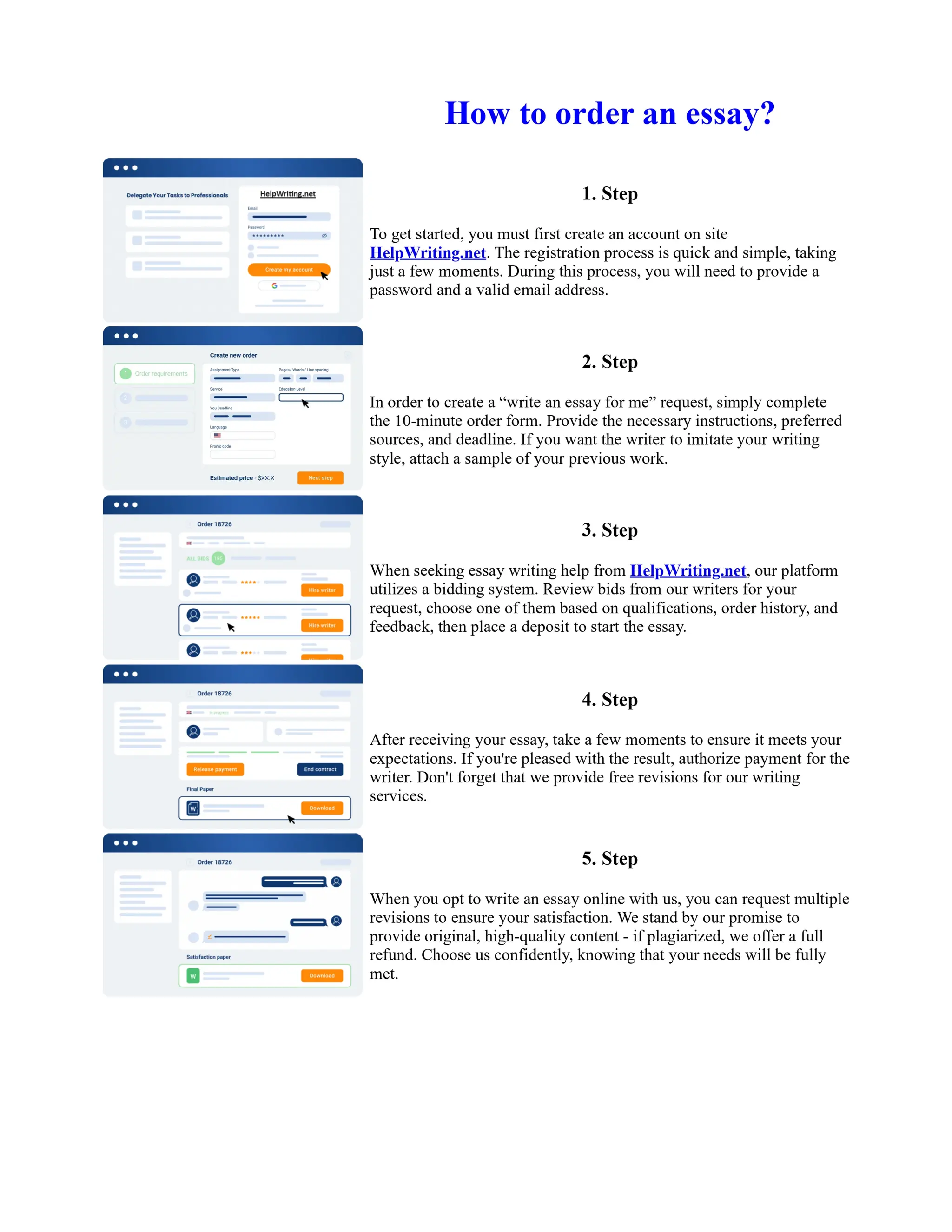
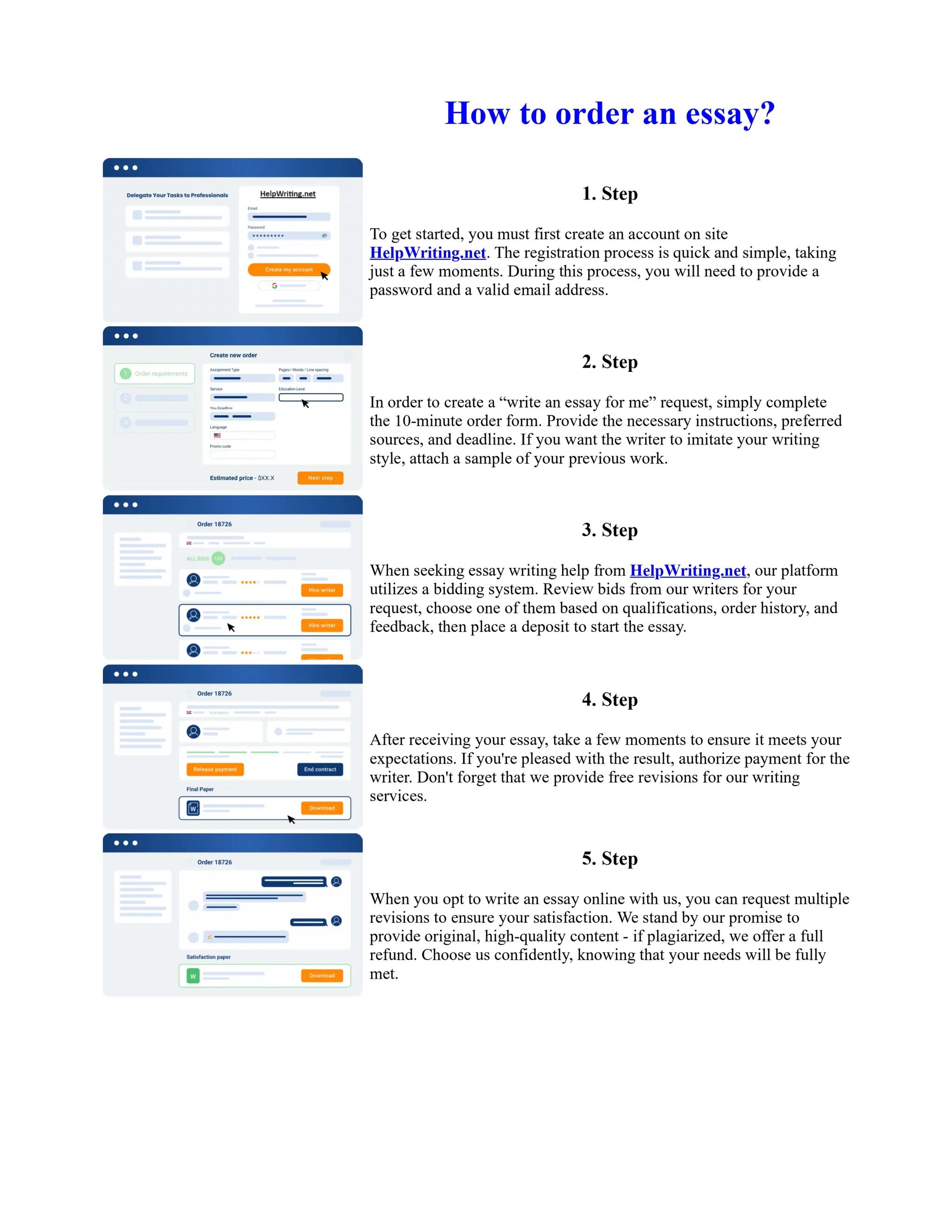
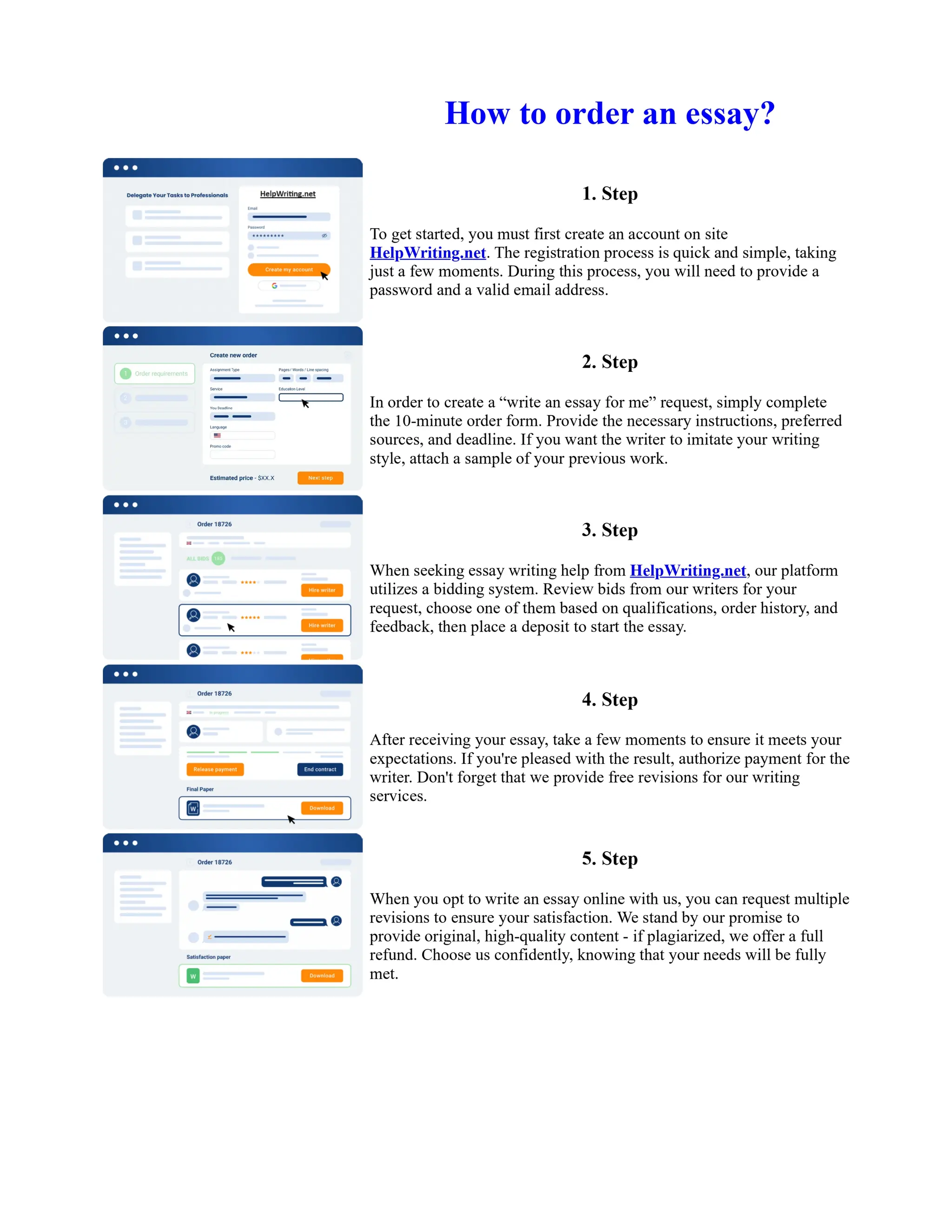
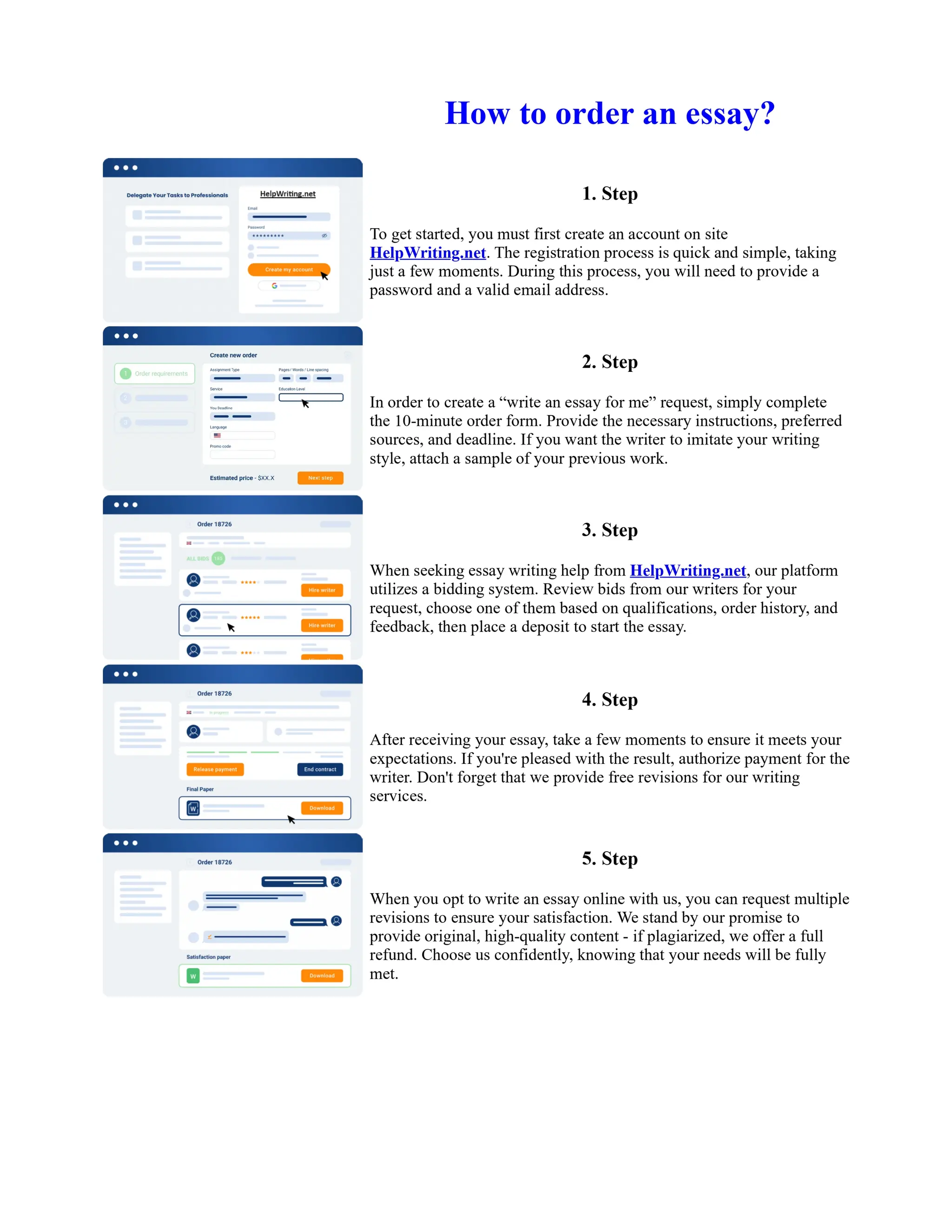
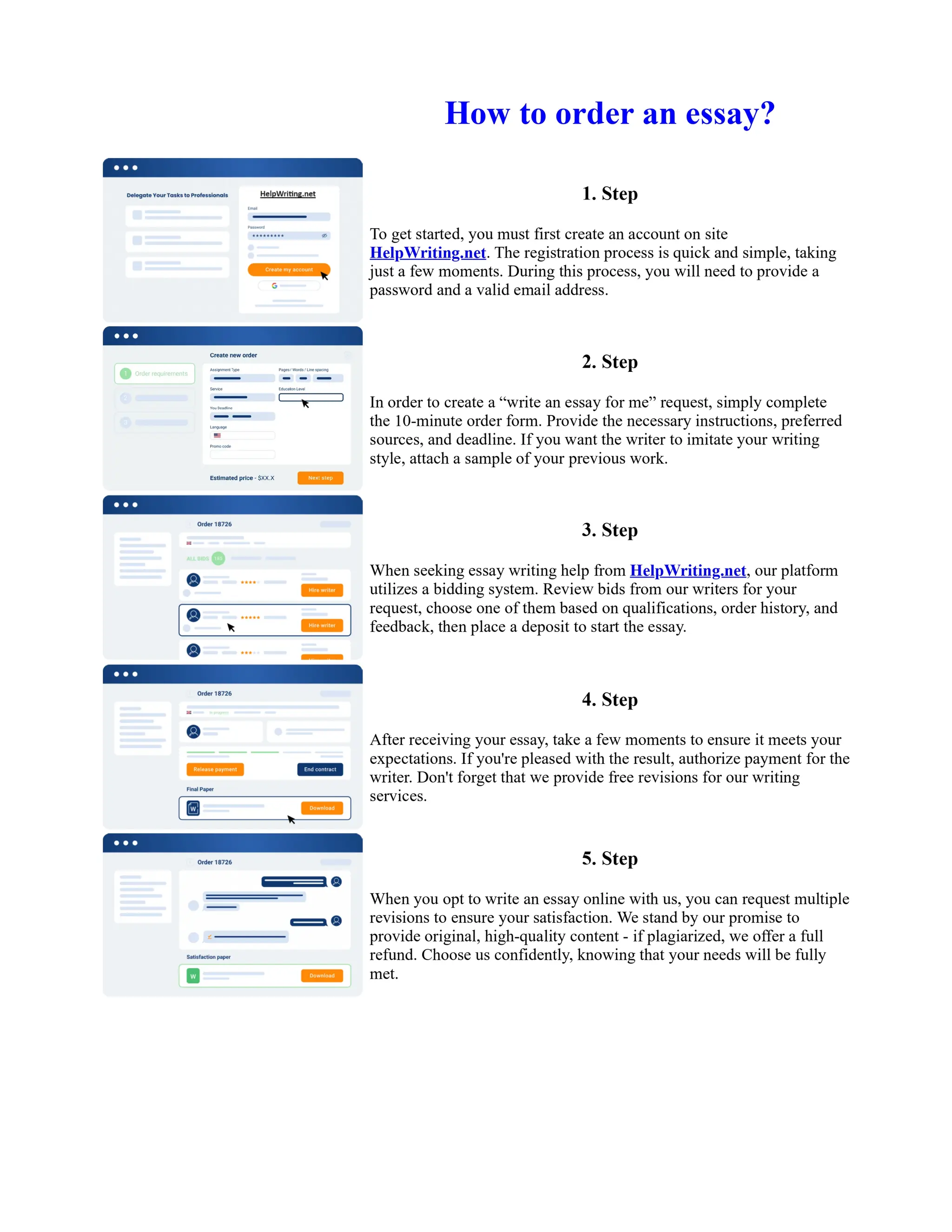
This document discusses human and technological aspects of cyber threats facing universities. It notes that while increased data and connectivity enable opportunities, they also present cybersecurity risks that could threaten an organization's existence. The challenges for IT security leaders are to balance security awareness with business needs. Recent attacks have shown blending of new and old techniques, resulting in highly evasive threats. The document also describes the four key steps in security authentication: identification, authentication, authorization, and accountability. It stresses integrating these steps is vital for securing networks against various attacks.


![Trusted Computing Group Analysis
Is one of Trusted Computing Group (TCG) specifications to measure, store and report hardware and
software integrity through a hardware root–of–trust. MTM is a security factor in mobile devices
checks all software and applications each time the underlying platform starts. MTM has very
constraints such as circuit area, as well as available power. Therefore, a MTM needs the spatially–
optimized architecture and design method to guarantees the integrity of a mobile platform [29].
Bouzefrane et al. [30] proposed a security protocol to authenticate Cloudlets–based mobile
computing using a mobile feature called NFC (Near field communication) of wireless data.
Cloudlets are used to offload intensive computation for NFC platforms, when mobile ... Show more
content on Helpwriting.net ...
D. Single Sign On (SSO)
Most users have multiple accounts in various Service Providers with different usernames and
passwords which in turn leads to lost productivity and apply more overhead on administrators. So,
there is a need to use the SSO technique in which an authorized user uses only a single action of
authentication to access all related systems or applications of same trust domain [34]. In cloud based
SSO system the central authentication server hides a multiplicity of user's account information into a
single account to be sent to the needed server of the system or application whenever the user intends
to use it [35]. The concept of SSO can be deployed within an Intranet, Extranet or Internet using
Token or PKI–based SSO protocols for single credentials or set of other protocols for multiple
credentials as declared in the following Figure:
Binu et al. [34] Proposed a Cloud authentication model with Single Sign–on (SSO) functionality
that uses a password and mobile token stored within a mobile phone as the authentication factors.
This model uses a Secure Access Markup Language 'SAML' protocol running on the authentication
server to support access across multiple domains.
2–Factor Authentication (2FA) is more suitable with principles of cloud authentication. A user sends
his username and password as the first factor to the cloud server for authentication. The cloud server
asks the user to send
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/nt2580finalprojectessayexamples-231104164549-43a94d79/75/Nt2580-Final-Project-Essay-Examples-4-2048.jpg)




























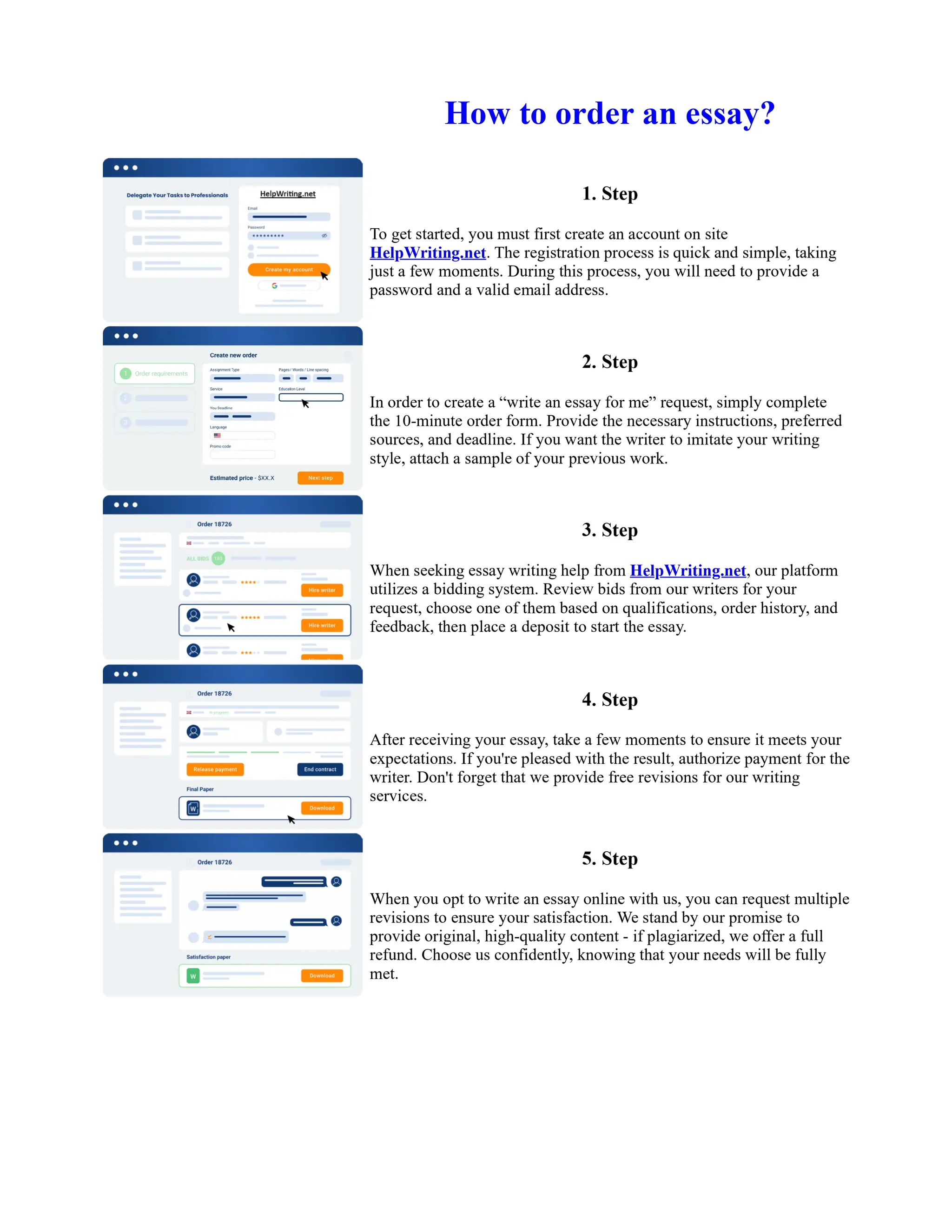
![Nt1330 Unit 2 Research Paper
SECTION TWO: METHODS AND NETWORK POLICES TO COUNTERMEASURE AND
MITIGATE THE RISK OF MV IN ENTERPRISE AND GOVERNMENT'S AGENCIES.
General recommendation and methods used to reduce the risk of MV:
The user authentication method has a crucial role to protect the MD and the data transferred through
the network either by using mobile's internal services provider like Verizon, Mobile, ATT or Wi–Fi
network providers in home or office. Many MD, nowadays Used two–way authentication methods
and OTP (one–time password) method which consists of generating string of varies of characters
and special characters to authenticate the user for one–time session. However, this method used for
many organizations and bank's system, still have its drawbacks when ... Show more content on
Helpwriting.net ...
While, the second method is building (Army App) store with fixed wireless distance and using a
special electronic equipment that suited for, the General Army Care and instructors [21]. On the
other hand, classified capability of Control MD like Secret Blackberry, secure iPad,
TIPSPIRAL(NSA) all equipped with information assurance certification and Accreditation process
provide real time access, reliable success decisions and remote scanning and special access key like
sensors, cards or fingerprint with independent multi–layer encryption, to prevent security preaches
[24].
All in all, the NIST published on July 10th, 2012 A special revision for managing and securing MD
against a variety of attacks for both personally–owned and organization–provided devices [39,38].
Stating the two approaches first, centralized management of the MD and alert massaging system to
worn server's management authority, both management methods contribute MD security policies
and restrictions provided by the enterprise security administrations to limit the use of application,
managing Wi–Fi network connections and constant monitoring system, in addition to third party
applications and providing encrypted data communication with intrusion detection and device
authentication control. Preventing installing of unauthorized software and prohibit the use rooted or
jailbroken
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/nt2580finalprojectessayexamples-231104164549-43a94d79/75/Nt2580-Final-Project-Essay-Examples-60-2048.jpg)
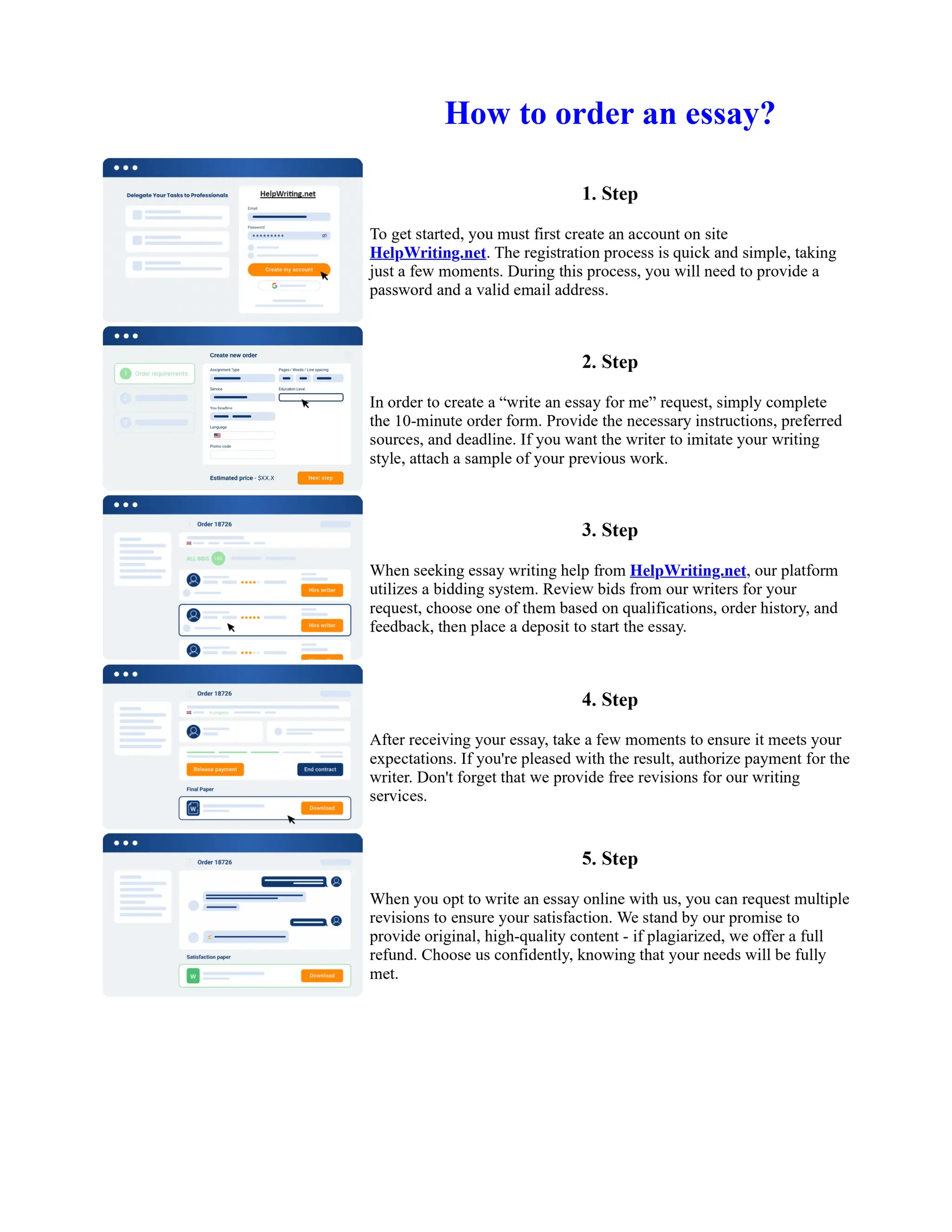
![Authentication Essay
I. INTRODUCTION Authentication is the only method which protects information or data of an
individual or organization from a second party to access. Based upon the confidentiality of that
particular data or information, the level of authentication depends. Now–a–days, all this data and
information what we are talking about is getting digitized all around the world. For this digitized
data or information to be secure, a proper authentication procedure must be set. This arise the need
for an authentication secret which belongs to the category "Something we know" to come into
picture. These secrets authenticate each secret holder as the authorized legitimate user to access their
particular account. Technology is ... Show more content on Helpwriting.net ...
So, to convert location address into longitude and latitude coordinates, there is a number of ways to
accomplish this. You may have a GPS device which shows you these coordinates, and you could just
take a reading from the GPS while at the address and note down the coordinates. There are also a
number of software packages out there which provide this conversion, but you don't particularly
need to buy one of those geocoders unless you need to geocode a large number of addresses.
(Digital Maps API also provides geocoding of this sort, although it may not be as user–friendly to
those unfamiliar with programming, and the service limits you to a certain number of requests per
time period.)
About Mnemonics: Mnemonic devices are useful memory aids that can be applied to many different
aspects of daily life. There are always certain tidbits of information that people just can't seem to
remember in the form they are presented. People rely on mnemonics when they create some
association between that information they wish to remember and other concepts that they already
know, or find easier to remember. The use of mnemonics has also been shown to be of significant
value in the field of education. Manalo has shown that instruction using a specific type of
mnemonics known as "process mnemonics" produced improvements of mathematical ability in
students classified as learning disabled [3].Process mnemonics are used
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/nt2580finalprojectessayexamples-231104164549-43a94d79/75/Nt2580-Final-Project-Essay-Examples-62-2048.jpg)




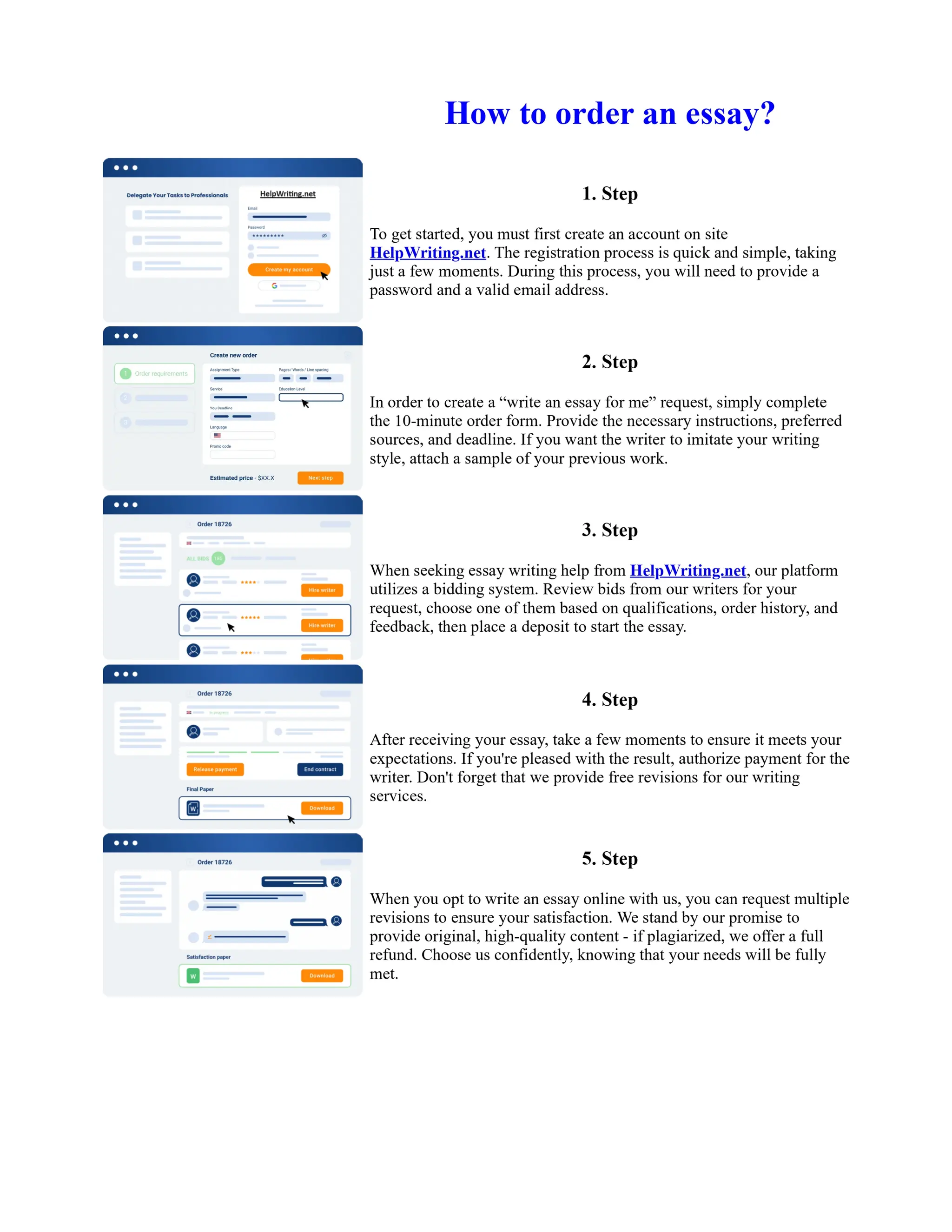
![Application Authentication And The Key Role For The User...
Introduction:
User Authentication plays the key role for the users to make use of the resources available in any
environment. With the advancements in technology, it has become quite easy for a person to find out
ways to access the data of the other person. It is very important to verify the true identity of the
person trying to access his/her data. The concerned organization or the business group has to make
sure that the person trying to access is the right user of the data and care must be taken in such a way
that the resources are not used for the wrong purposes. Making use of the correct resources by the
right person in a right way is the purpose behind the authentication. A customer is mainly concerned
about the security of his data ... Show more content on Helpwriting.net ...
Different authentication methods have their own user identification rates and the accuracy of an
authentication method depends on the environment being implemented. User authentication can be
performed by considering various physical human aspects like the typing biometric features,
gestures, lip features. Technologies like CBAT which is implemented in the server machine, Visual
authentication based on a single sign on token also are used for implementing the user
authentication methods. CBAT and Visual authentication methods need extra circuitry hardware to
be implemented and they make use of the software applications which are installed over them.
Section 2:
The authentication of users is done by taking in to account their physical features, as there are fewer
chances of different people having the same features. Physical aspects vary from individual to
individual. So the biometric features, Lip features, gestures can be used to solve the problems
associated with security, as they are unchangeable and are owned to a particular person. The
biometric used is the typing keystroke pattern features. The keystroke typing pattern varies from
person to person [6].The core concept of biometric methodology is that the input data from the user
is taken and the key stroke data is collected to calculate the key features. The calculated key features
are used in the creation of samples and compared against the classifiers which are
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/nt2580finalprojectessayexamples-231104164549-43a94d79/75/Nt2580-Final-Project-Essay-Examples-72-2048.jpg)


![Advantages And Disadvantages Of Textual Passwords
The system and information security is most important factor for security program and the major
security method for information and system security is authentication[1]. The authentication is
widely used for verifying the identity of a particular person. The most popular authentication
method is password authentication. In this, textual(alphanumeric) passwords are mostly used as
traditional method. These types of textual passwords are strings of letters and digits. But there are
several deficiencies in these textual passwords such as passwords used are short and simple which
are easy to remember[2].So textual passwords can be personal names of family members, dictionary
words, birth–date, pet name, phone number etc.and vulnerable to various attacks like dictionary
attack, easy to guess etc.[3][4]
Mostly users require the passwords for personal computers, social networks, email and more, and
for all these systems. For easy remembrance the users use the same password which reduces
security[5]. Hence if textual passwords are kept difficult then they are difficult to remember and if it
is easily kept then they are easy to guess. ... Show more content on Helpwriting.net ...
It is a click–based graphical password where a sequence of clicks on an image is used to derive a
password mainly for authentication purpose. As compared with other click–based graphical
passwords, images used in CaRP are Captcha challenges and every time new image is generated in
CaRP scheme.It is mainly related on the image–recognition Captcha. It offers protection against
dictionary attacks on passwords, which have been a major security problem for various online
services. It is widely spread and considered as a top cyber security
... Get more on HelpWriting.net ...](https://image.slidesharecdn.com/nt2580finalprojectessayexamples-231104164549-43a94d79/75/Nt2580-Final-Project-Essay-Examples-78-2048.jpg)