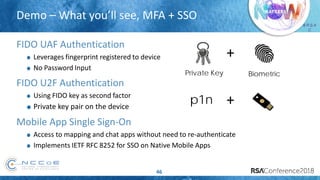
William Fisher presented on improving mobile authentication for public safety and first responders. He discussed challenges with password management and outlined requirements for an effective authentication solution, including being flexible, efficient, interoperable, and improving credential management. He then demonstrated a solution using standards-based multifactor authentication and single sign-on to provide benefits like reducing authentication time and the number of credentials needed. Finally, he highlighted new NIST guidance on implementing mobile single sign-on solutions.