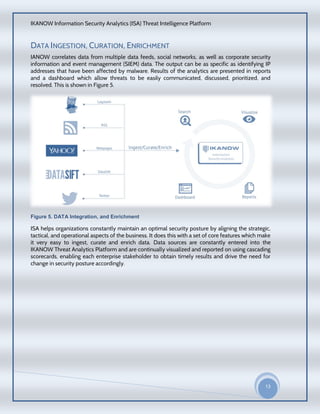
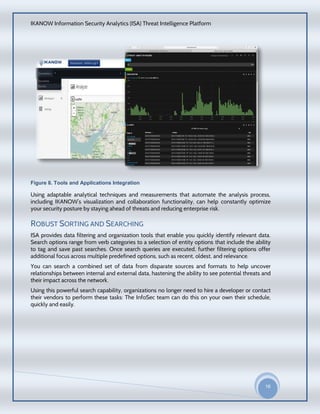
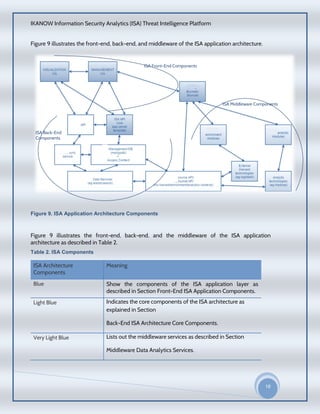
The document provides an overview of the IKANOW Information Security Analytics (ISA) Threat Intelligence Platform. It describes the platform's core features including three-step data ingestion, comprehensive visualizations and reports, integration with third-party tools, and robust searching. It discusses challenges around analyzing large amounts of security data from various sources and how the platform addresses these challenges through an open, flexible and scalable architecture that allows constant calibration of an organization's security posture.