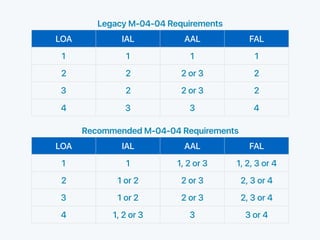
SP 800-63-3 is an update to NIST's digital identity guidelines. It introduces a new framework that separates assurance levels into three components: Identity Assurance Level (IAL), Authenticator Assurance Level (AAL), and Federation Assurance Level (FAL). This provides more flexibility and granularity over the previous version's single Level of Assurance (LOA). The document outlines the recommended requirements and mappings between the new IAL, AAL, FAL framework and the legacy LOA model from SP 800-63-2.