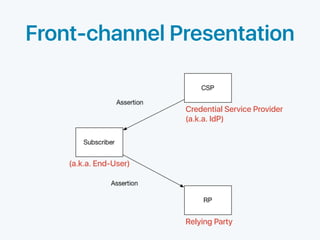
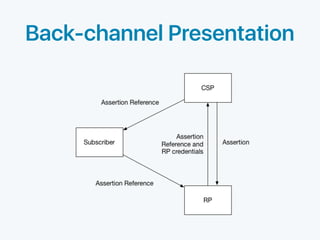
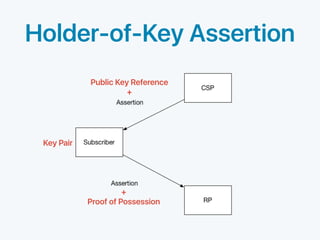
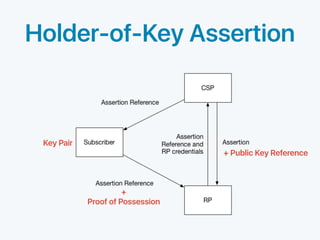
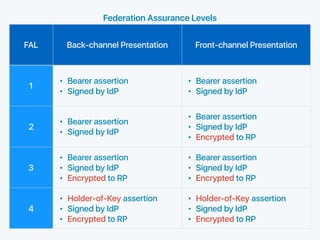
The document discusses standards for identity federation and assertions. It defines four levels of federation assurance (FAL) based on the type of assertion used and how it is presented. FAL1 uses front-channel or back-channel bearer assertions signed by the identity provider. FAL2 adds encryption of assertions to the relying party. FAL3 encrypts assertions to the relying party for both front and back-channel. FAL4 uses holder-of-key assertions, where the assertion contains a public key and proof of possession, signed and encrypted to the relying party. The document provides definitions and discusses security considerations for federation and assertions.