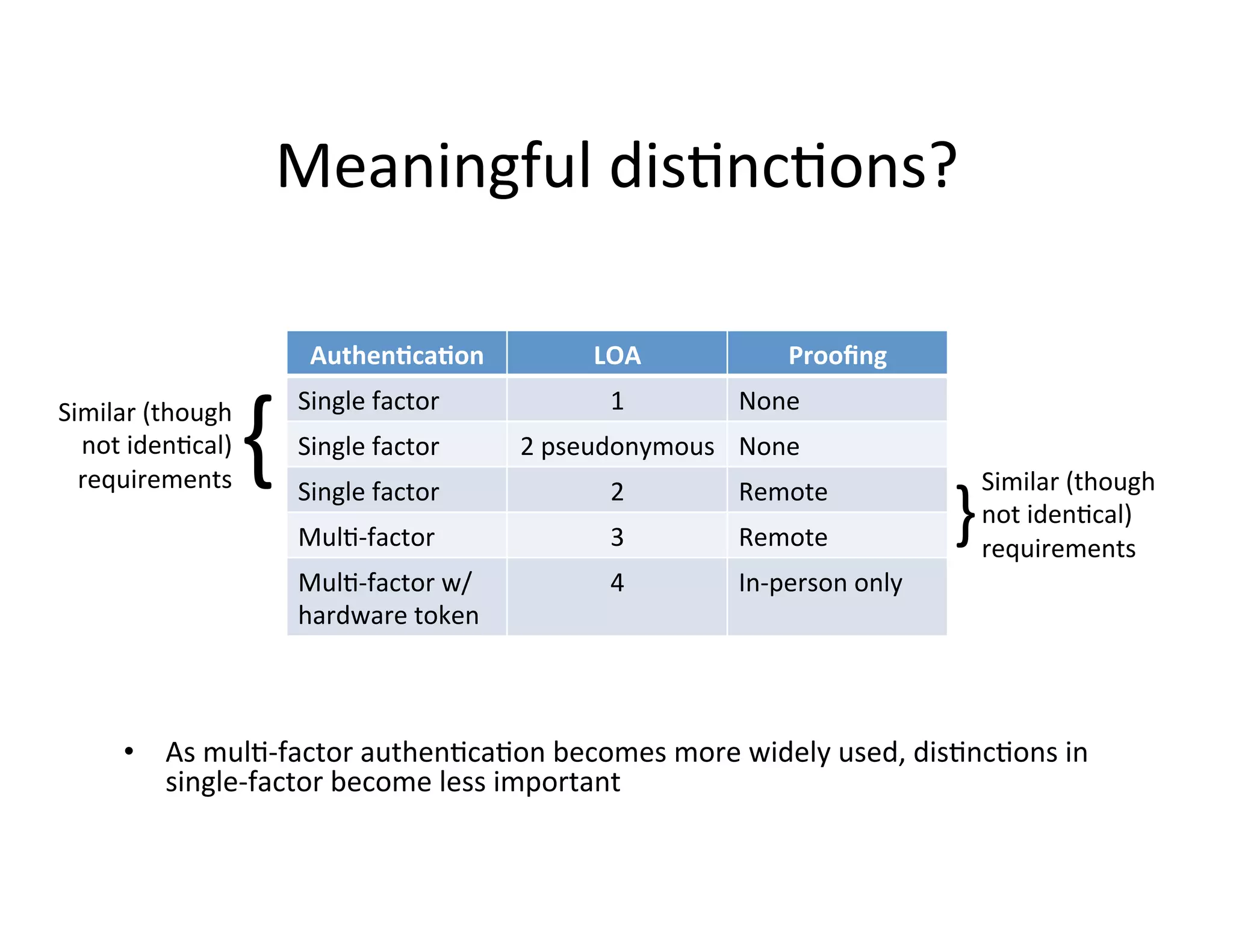
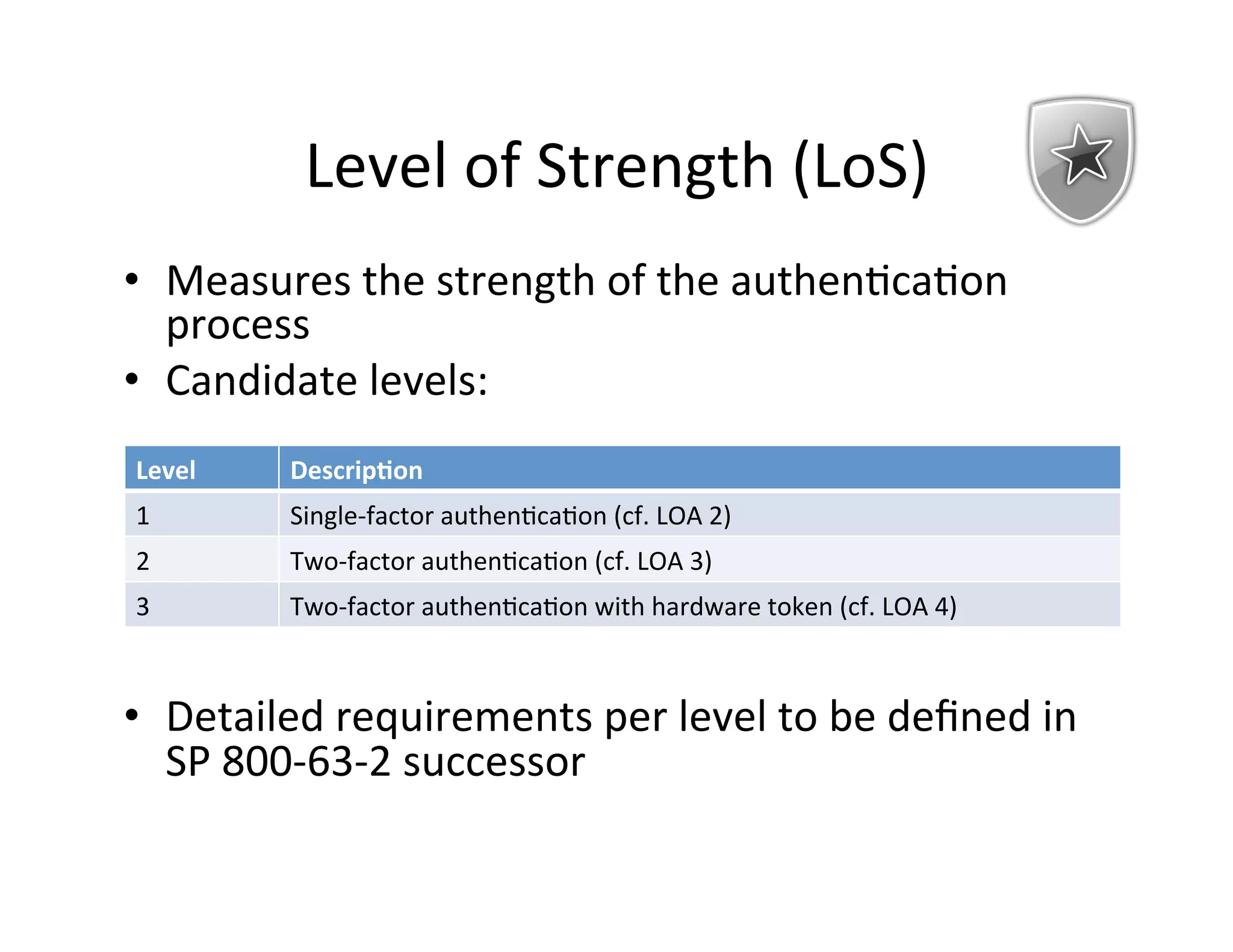
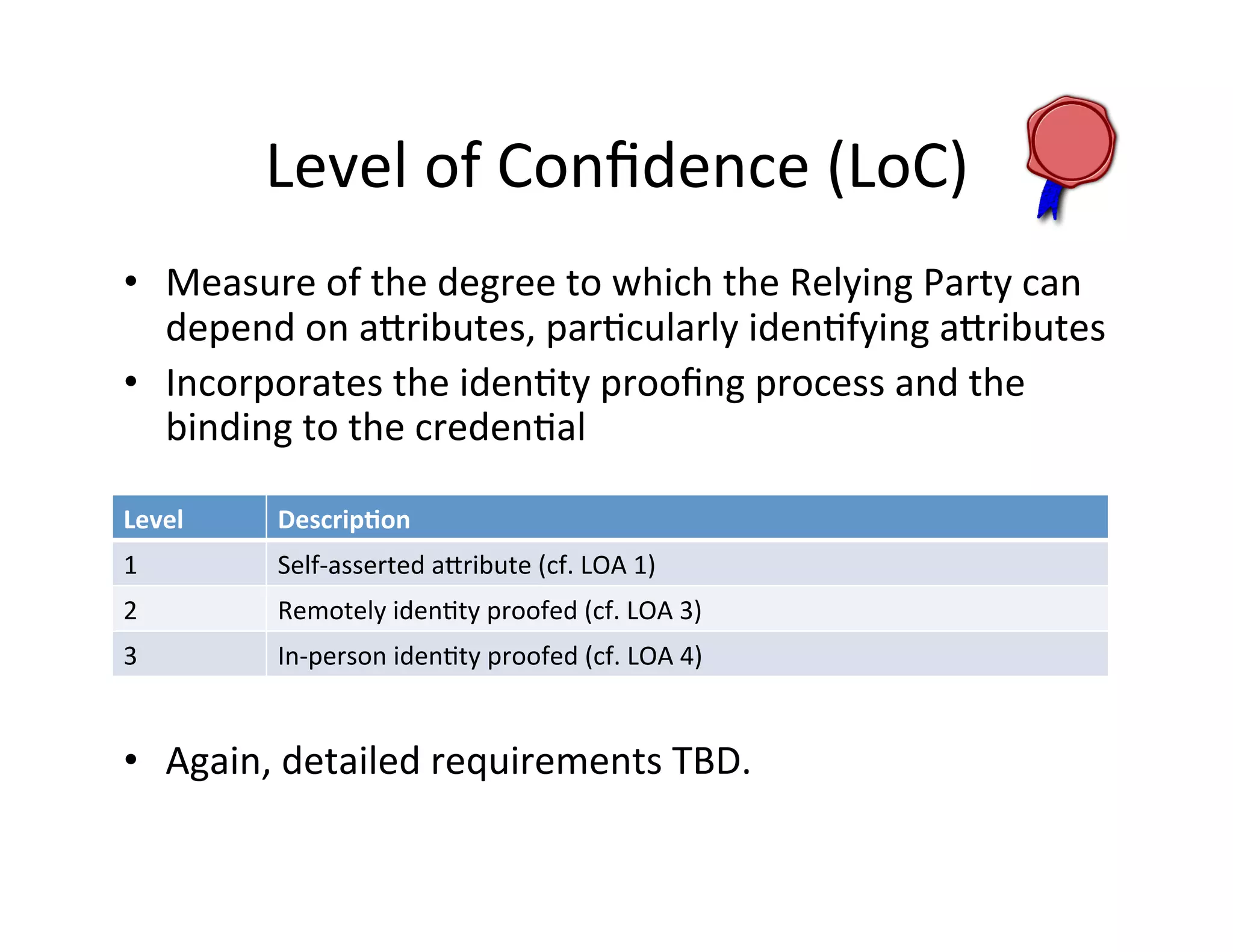
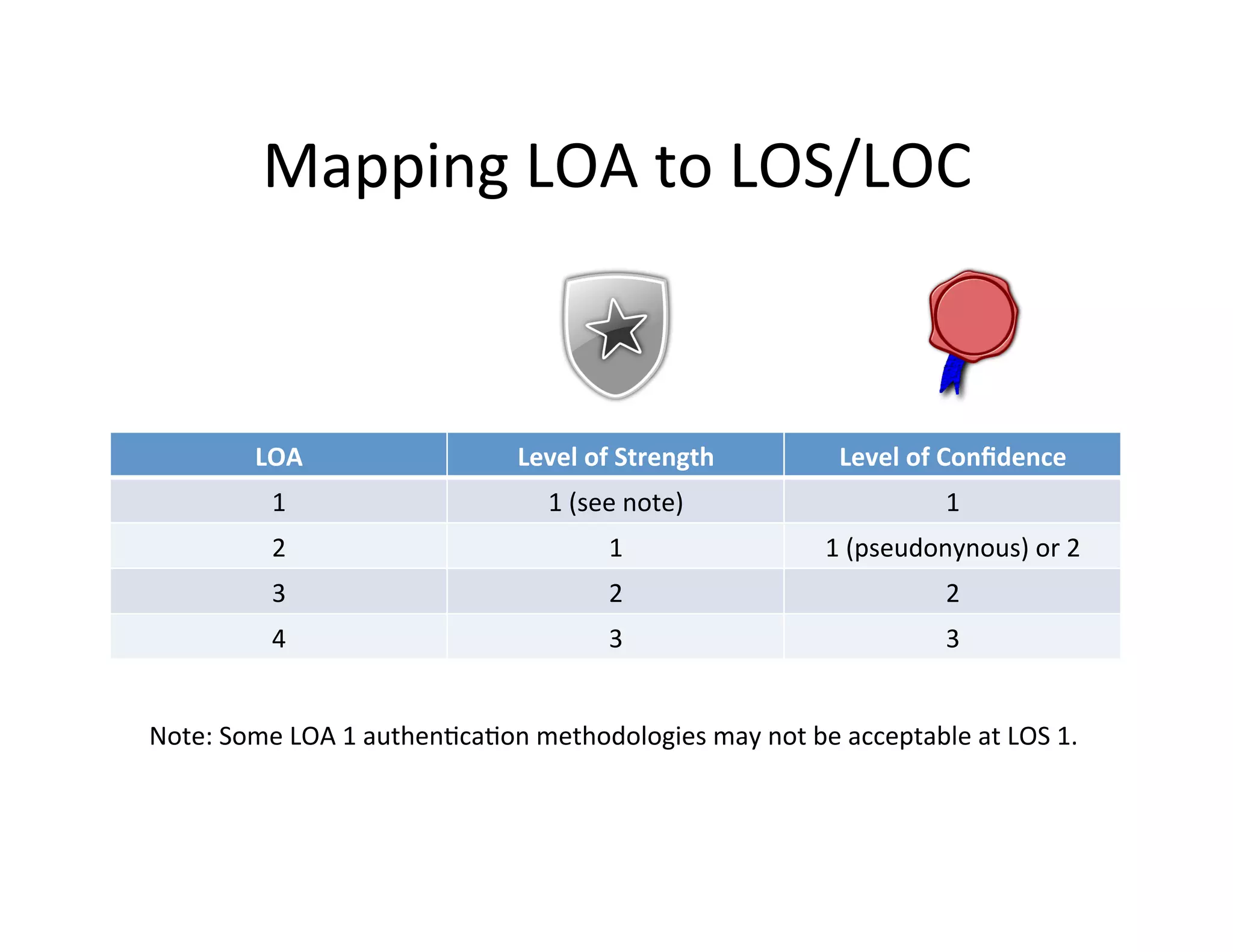
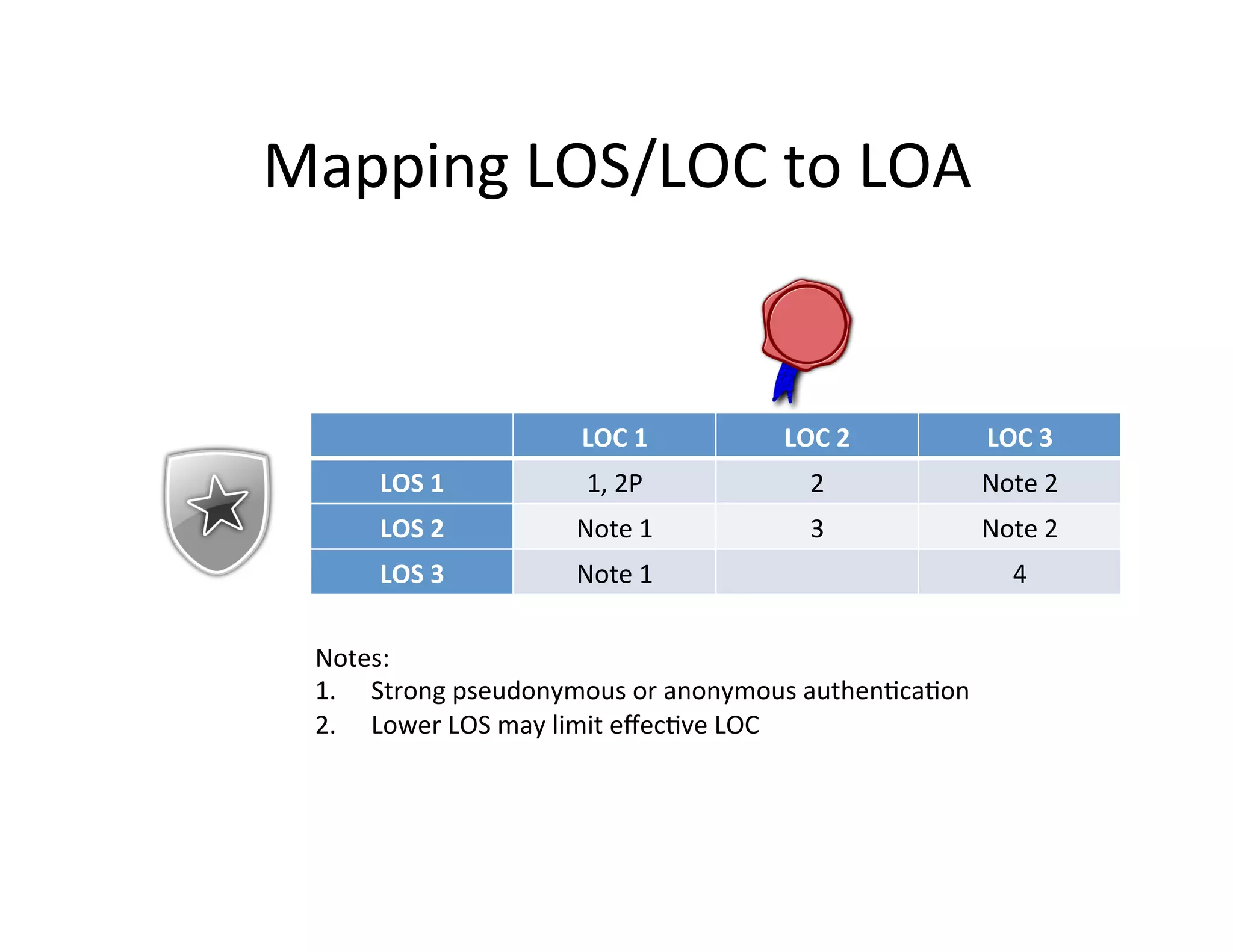
This document proposes a new model for Level of Assurance (LOA) that separates it into two parts: Level of Strength (LoS) of authentication and Level of Confidence (LoC) of attributes. LoS would measure the strength of the authentication process using levels like single-factor, two-factor, or two-factor with hardware token. LoC would measure the degree to which a relying party can depend on attributes based on the identity proofing process using levels like self-asserted, remotely verified, or in-person verified. This new model aims to avoid problems with the current LOA structure and emphasize meaningful distinctions between levels.