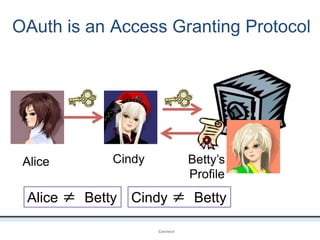
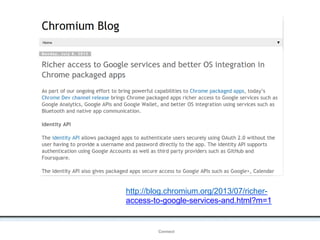
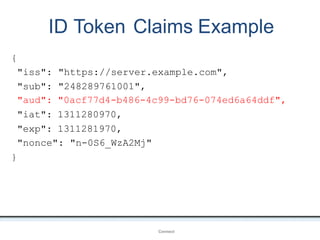
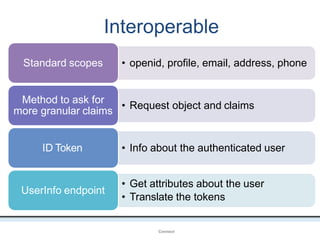
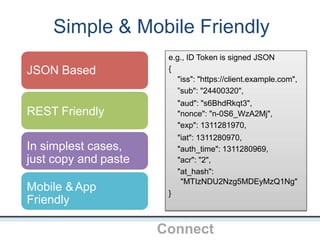
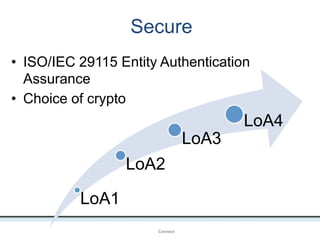
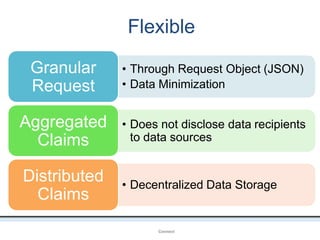
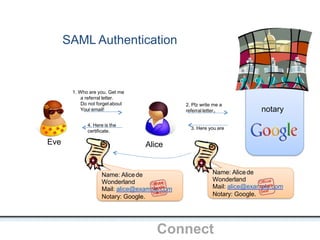
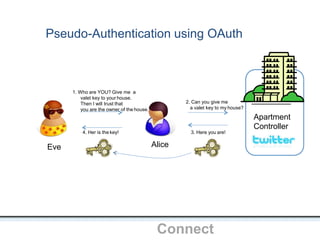
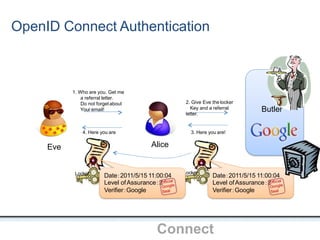
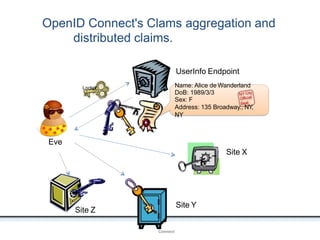
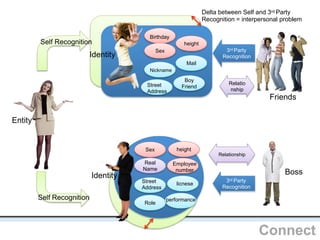
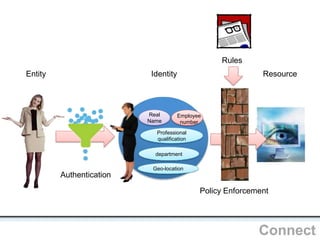
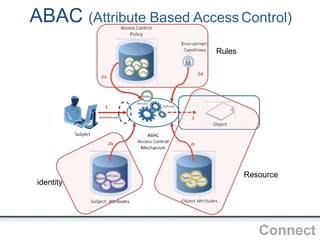
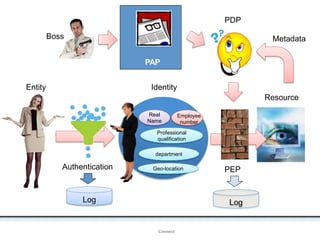
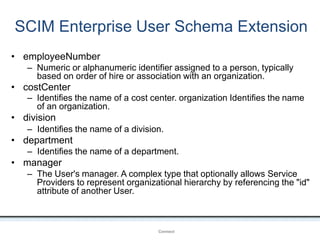
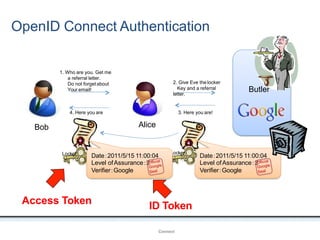
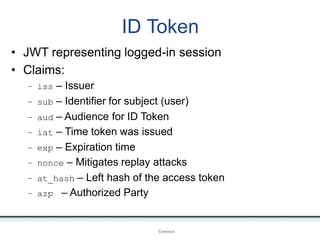
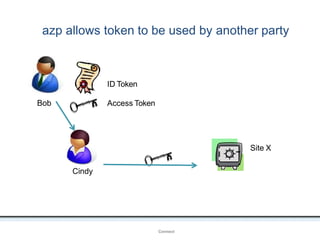
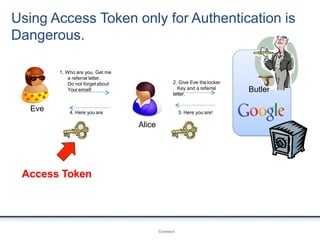
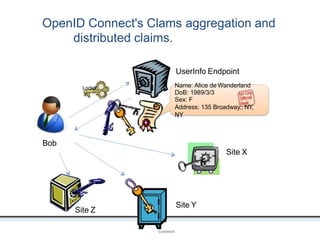
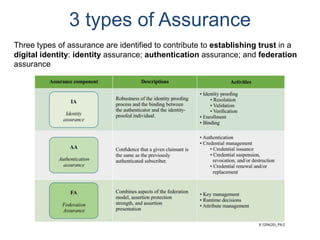
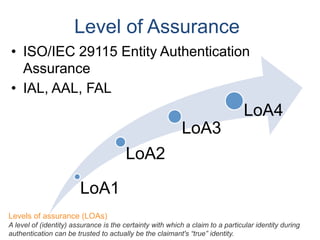
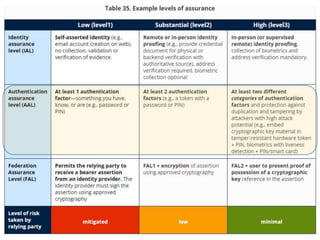
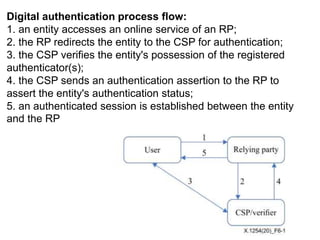
The document outlines an agenda covering various topics related to digital identity and authentication. It discusses entity identity, assurance frameworks, the digital authentication process flow, threats/risks/controls, strong authentication methods, token and credential management standards like JWT, OAuth 2.0, OpenID Connect, FAPI, and how they relate to identity in areas like banking and payments. It provides definitions for key terms and compares authentication flows using standards like SAML, OAuth and OpenID Connect.


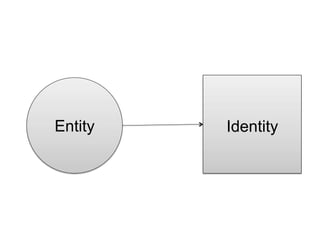
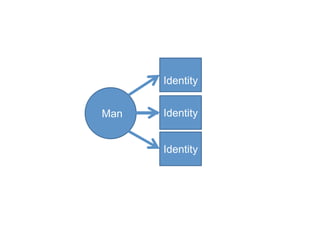
![Identity = set of attributes
related to an entity [iso 29115]](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-3-320.jpg)




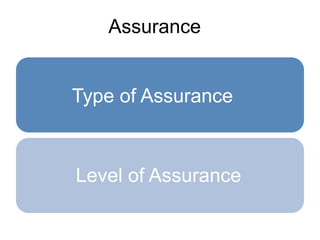
![Assurance = a statement that something will certainly be
true or will certainly happen, particularly when there has
been doubt about it [oxford dictionary]](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-15-320.jpg)
![authentication [b-ISO/IEC 18014-2]: Provision of
assurance of the claimed identity of an entity](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-16-320.jpg)
![Claimed Identity = An applicant’s declaration of
unvalidated and unverified personal attributes
[NIST SP 800-63-3]
{
"sub": "1234567890",
"name": "John Doe",
"admin": true
}
JSON Web Token Claims
JSON web tokens (JWTs) claims are pieces of information asserted about a](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-17-320.jpg)



![authentication [b-ISO/IEC 18014-2]: Provision of
assurance of the claimed identity of an entity](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-25-320.jpg)

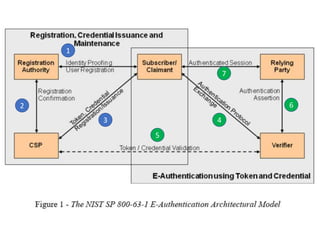
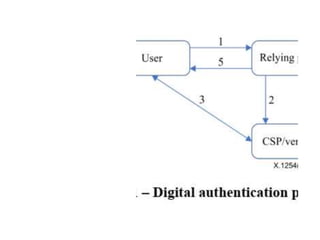
![• assertion [b-ITU-T X.1252]: A statement made by an entity without accompanying
evidence of its validity
• authentication factor [b-ISO/IEC 19790]: Piece of information and/or process used to
authenticate or verify the identity of an entity
• authentication protocol [b-ISO/IEC 29115]: Defined sequence of messages between
an entity and a verifier that enables the verifier to perform authentication of an entity
• credential [b-ITU-T X.1252]: A set of data presented as evidence of a claimed identity
and/or entitlements
• identity proofing [b-ISO/IEC 29115]: Process by which the registration authority (RA)
captures and verifies sufficient information to identify an entity to a specified or
understood level of assurance
• multifactor authentication [b-ISO/IEC 19790]: Authentication with at least two
independent authentication factors
• mutual authentication [b-ISO/IEC 29115]: Authentication of identities of entities which
provides both entities with assurance of each other's identity
• verification [b-ISO/IEC 29115]: Process of checking information by comparing the
provided information with previously corroborated information
• credential service provider (CSP): A trusted actor that issues or manages credentials
• identity service provider (ISP): responsible for identity proofing an entity's claimed
identity and ensuring that this claimed identity is associated with the credential used by
the entity
• identifier: One or more attributes that uniquely characterize an entity in a specific
context
• relying party (RP): Actor that relies on an identity assertion or claim
Terms and Definitions](https://image.slidesharecdn.com/api-security-jan23-240327090755-e481c79b/85/api-security-Jan23-pptxsdfffffffffffffffffffffffffffff-30-320.jpg)