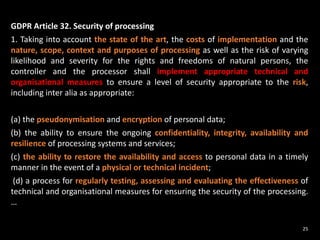
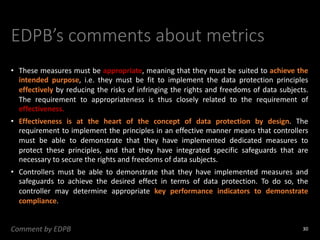
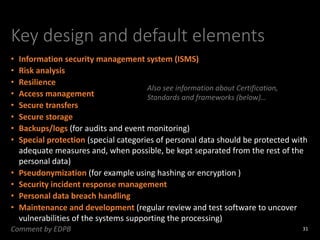
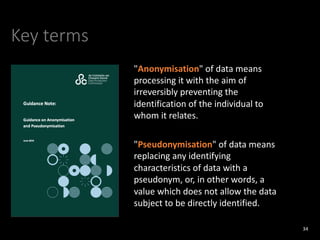
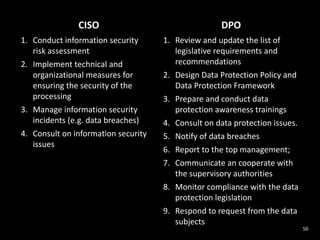
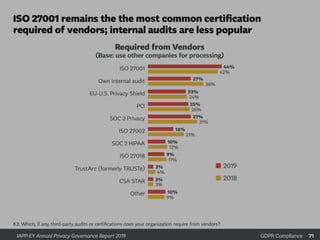
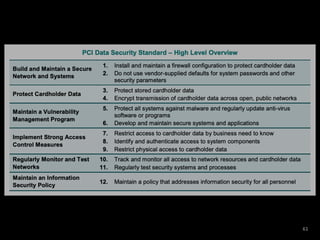
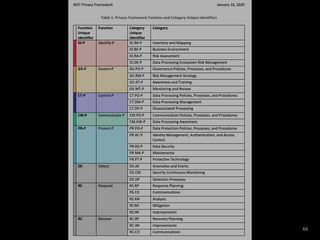
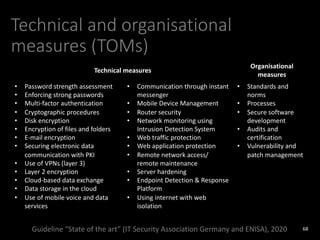
The document provides an overview of GDPR and information security issues. It highlights key topics such as appropriate security, data protection by design and by default, security of processing, personal data breaches, and the differences between DPO and CISO roles. The document contains recommendations for technical and organizational security measures organizations should implement to comply with GDPR principles and ensure an appropriate level of data security. These include implementing privacy by design principles, conducting risk assessments, access management, encryption, backups, and incident response processes.